CHAPTER 1 MALWARE ANALYSIS PRIMER.ppt
Download as ppt, pdf0 likes45 views
This chapter provides an overview of malware analysis. It outlines the goals of malware analysis as determining what happened during a network intrusion and ensuring all infected machines and files are located. It describes static and dynamic analysis techniques, from basic to advanced. It also defines common types of malware like backdoors, botnets, downloaders, and more. Finally, it provides general rules for malware analysis, like focusing on key features and using different tools/approaches when stuck.
1 of 11
Download to read offline










Ad
Recommended
CHAPTER 1 MALWARE ANALYSIS PRIMER.pdf



CHAPTER 1 MALWARE ANALYSIS PRIMER.pdfManjuAppukuttan2
╠²
This document provides an overview of malware analysis. It discusses the goals of malware analysis as determining what happened on a network and ensuring all infected files are found. It also describes static and dynamic analysis techniques, from basic approaches like examining file contents up to advanced methods like reverse engineering code. The document outlines common types of malware like backdoors, botnets, and information stealing malware. Finally, it provides some general rules for malware analysis like focusing on key features and using different analysis approaches when getting stuck.Chapter 1 malware analysis primer



Chapter 1 malware analysis primerManjuA8
╠²
The document provides an overview of malware analysis, including its goals, common techniques, types of malware, and general rules. The goals of analysis are to understand what happened during an infection, locate all affected systems and files, and determine a malware's capabilities to facilitate detection and remediation. Techniques include static analysis of files without execution and dynamic analysis by running malware in a controlled environment. Types of malware include backdoors, botnets, downloaders, info-stealers, and more. General rules advise focusing on key features, using multiple tools and approaches, and recognizing that malware aims to evade analysis.Introduction To Malware Analysis.pptx



Introduction To Malware Analysis.pptxTrngTun36
╠²
Malware analysis involves studying malicious software to understand its capabilities and how it infects systems. There are several types of malware like trojans, ransomware, and remote access tools. Malware analysis examines samples through static, dynamic, code, and behavioral analysis to determine the malware's functions, how the infection occurred, and how to prevent similar attacks. The process provides details about the malware's registry entries, files, and network activity to generate detection signatures.Introduction To Malware Analysis.pptx



Introduction To Malware Analysis.pptxdatasun
╠²
Malware analysis involves studying malicious software to understand its capabilities and how it infects systems. There are several types of malware like trojans, ransomware, and remote access tools. Malware analysis examines samples through static, dynamic, code, and behavioral analysis to determine the malware's functions, how the infection occurred, and how to prevent similar attacks. The process provides details on the malware's communications, files, and registry entries to generate detection signatures.Unveiling the Shadows: A Comprehensive Guide to Malware Analysis for Ensuring...



Unveiling the Shadows: A Comprehensive Guide to Malware Analysis for Ensuring...CyberPro Magazine
╠²
Malicious software, or malware, is a constant concern in the networked world of digital landscapes. Cybercriminals are always improving their strategies, which makes malware more complex and difficult to identify. To combat this, protecting computer systems requires an understanding of and application of malware analysis. What Are The Types of Malware? Must Read



What Are The Types of Malware? Must ReadBytecode Security
╠²
If you want to make your career in ethical hacking, Bytecode Security offers the best malware analysis course online offline with job placement assistance. Read more: https://www.bytec0de.com/malware-analysis-course-training-certification/Malware forensic



Malware forensicSumeraHangi
╠²
This document discusses malware forensics. It defines malware as malicious software programs and describes what malware can do. The document outlines different types of malware and explains how malware analysis has become a forensic discipline. It describes malware forensics as investigating malware properties to identify culprits and reasons for attacks. This includes analyzing malicious code, entry points, propagation methods, and system impacts. The document contrasts static and dynamic malware analysis approaches.CH1- Introduction to malware analysis-v2.pdf



CH1- Introduction to malware analysis-v2.pdfWajdiElhamzi3
╠²
This document outlines a course on advanced malware reverse engineering. It begins with an introduction to malware types like viruses, worms, trojans, and ransomware. It then covers basic analysis techniques like viewing malware behavior and signatures. More advanced topics include static analysis using disassembly and dynamic analysis using debuggers. The goals of analysis are understanding malware functionality and enabling incident response. Analysis requires both static and dynamic methods to fully comprehend advanced threats.Basic survey on malware analysis, tools and techniques



Basic survey on malware analysis, tools and techniquesijcsa
╠²
The term malware stands for malicious software. It is a program installed on a system without the
knowledge of owner of the system. It is basically installed by the third party with the intention to steal some
private data from the system or simply just to play pranks. This in turn threatens the computerŌĆÖs security,
wherein computer are used by oneŌĆÖs in day-to-day life as to deal with various necessities like education,
communication, hospitals, banking, entertainment etc. Different traditional techniques are used to detect
and defend these malwares like Antivirus Scanner (AVS), firewalls, etc. But today malware writers are one
step forward towards then Malware detectors. Day-by-day they write new malwares, which become a great
challenge for malware detectors. This paper focuses on basis study of malwares and various detection
techniques which can be used to detect malwares.Introduction to Malware analysis 



Introduction to Malware analysis HusseinMuhaisen
╠²
Hey Guys , In This ║▌║▌▀Ż I'll be Directing you guys to the stepping stones of getting into malware analysis. Just Make Sure to focus on the slides and you are ready to go A FRAMEWORK FOR ANALYSIS AND COMPARISON OF DYNAMIC MALWARE ANALYSIS TOOLS



A FRAMEWORK FOR ANALYSIS AND COMPARISON OF DYNAMIC MALWARE ANALYSIS TOOLSIJNSA Journal
╠²
Malware writers have employed various obfuscation and polymorphism techniques to thwart static analysis approaches and bypassing antivirus tools. Dynamic analysis techniques, however, have essentially overcome these deceits by observing the actual behaviour of the code execution. In this regard, various methods, techniques and tools have been proposed. However, because of the diverse concepts and strategies used in the implementation of these methods and tools, security researchers and malware analysts find it difficult to select the required optimum tool to investigate the behaviour of a malware and to contain the associated risk for their study. Focusing on two dynamic analysis techniques: Function Call monitoring and Information Flow Tracking, this paper presents a comparison framework for dynamic malware analysis tools. The framework will assist the researchers and analysts to recognize the toolŌĆÖs implementation strategy, analysis approach, system-wide analysis support and its overall handling of binaries, helping them to select a suitable and effective one for their study and analysis.CNIT 126 Ch 0: Malware Analysis Primer & 1: Basic Static Techniques



CNIT 126 Ch 0: Malware Analysis Primer & 1: Basic Static TechniquesSam Bowne
╠²
║▌║▌▀Żs for a college course at City College San Francisco. Based on "Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software", by Michael Sikorski and Andrew Honig; ISBN-10: 1593272901.
Instructor: Sam Bowne
Class website: https://samsclass.info/126/126_S17.shtml
Ch0 1



Ch0 1TylerDerdun
╠²
This document provides an overview of basic static malware analysis techniques. It discusses using antivirus scanners, hashing files, and analyzing strings to identify malware without executing it. It also covers examining the Portable Executable (PE) file format used in Windows executables, including analyzing the PE header, imported and exported functions, linked libraries, and important sections like .text and .rsrc. Detecting packed files and analyzing the PE dynamically at runtime is also mentioned. The goal is to gain an initial understanding of unknown files through static inspection before dynamic analysis.Practical Malware Analysis: Ch 0: Malware Analysis Primer & 1: Basic Static T...



Practical Malware Analysis: Ch 0: Malware Analysis Primer & 1: Basic Static T...Sam Bowne
╠²
This document provides an overview of basic static malware analysis techniques. It discusses using antivirus scanners, hashing files, and finding strings to identify malware without executing it. It also covers analyzing the Portable Executable (PE) file format used in Windows executables, including examining the PE header, imported and exported functions, linked libraries, and sections like .text and .rsrc. The document demonstrates various tools for these static analysis tasks like HashCalc, strings, PEview, Dependency Walker, and Resource Hacker.Cyber Defense Forensic Analyst - Real World Hands-on Examples



Cyber Defense Forensic Analyst - Real World Hands-on ExamplesSandeep Kumar Seeram
╠²
The document discusses analyzing malware using static and dynamic analysis techniques. Static analysis involves examining a malware file's code and structure without executing it, using tools like disassemblers and string extractors. Dynamic analysis executes malware in a controlled environment to observe its behaviors and any changes it makes. The document then demonstrates analyzing the "Netflix Account Generator" malware using an isolated cloud sandbox, where it is observed starting child processes and making outbound network connections, suggesting it is a remote access trojan.Type of Malware and its different analysis and its types !



Type of Malware and its different analysis and its types !Mohammed Jaseem Tp
╠²
This document discusses different types of malware and methods for analyzing malware. It defines malware as malicious software designed to damage computers without consent. The document outlines 10 main types of malware: viruses, worms, Trojans, spyware, adware, ransomware, rootkits, keyloggers, botnets, and bugs. It also describes 3 methods of malware analysis: static analysis, which examines code without executing it; dynamic analysis, which observes behavior by running malware; and threat analysis, which identifies malware families and tracks criminal infrastructure over time.Malware Detection Using Data Mining Techniques 



Malware Detection Using Data Mining Techniques Akash Karwande
╠²
This document discusses techniques for malware detection using data mining. It begins by defining the problem of malware as one of the most serious issues faced on the internet. It then discusses types of malware like viruses, worms, trojans, and rootkits. It describes how rootkits can hide themselves and their activities. The document outlines static and dynamic analysis methods for malware detection and describes signature-based and behavior-based detection techniques. It shows results from using the Weka tool achieving over 97% success in rootkit detection. Advanced techniques discussed include n-grams and analyzing API/system calls.Cyber Security Threats Unveilded



Cyber Security Threats UnveildedElewayte
╠²
This document provides an overview of malware analysis. It defines malware and lists common types. It describes two main techniques for analyzing malware: static and dynamic analysis. Static analysis involves examining malware code and structure without executing it, while dynamic analysis observes malware behavior by executing it in a controlled environment. The goal of malware analysis is to understand malware functionality, behavior, and impact in order to better defend against threats. Host- and network-based intrusion detection systems use malware signatures to detect unauthorized or malicious activities on individual systems and network traffic.Malware analysis



Malware analysisPrakashchand Suthar
╠²
- Malware analysis involves both static and dynamic analysis techniques to understand malware behavior and assess potential damage. Static analysis involves disassembling and reviewing malware code and structure without executing it. Dynamic analysis observes malware behavior when executed in an isolated virtual environment.
- Tools for static analysis include file hashing, string extraction, and PE header examination. Dynamic analysis tools monitor the registry, file system, processes, and network traffic created by malware runtime behavior. These include Process Monitor, Wireshark, Process Explorer, and network sniffers.
- To safely conduct malware analysis, one should create an isolated virtual lab separated from production networks, and install behavioral monitoring and code analysis tools like OllyDbg, Process Monitor, and WireshMission Impossible - Malware Analysis.pdf



Mission Impossible - Malware Analysis.pdfnull - The Open Security Community
╠²
Mission Impossible - Malware Analysis by Mohammed Danish AmberBasic Dynamic Analysis of Malware



Basic Dynamic Analysis of MalwareNatraj G
╠²
This document provides an overview of basic dynamic malware analysis techniques. It explains that dynamic analysis examines how malware behaves when executed by monitoring changes to the system, unusual processes, network traffic, and other behaviors. A number of tools are described that can be used for dynamic analysis, including sandboxes, process monitors, registry snapshots, network service emulators, and packet sniffers. Caution is advised to perform analysis safely in a isolated lab environment.Malware Classification and Analysis



Malware Classification and AnalysisPrashant Chopra
╠²
The document discusses malware analysis using machine learning. It proposes collecting malware binaries from online sources and using Cuckoo Sandbox to analyze their behavior dynamically. Features would be extracted from the analysis reports and used to classify the malware into families using machine learning algorithms. The goal is to develop an automated malware classification system that can identify both known and unknown malware types.A SURVEY ON MALWARE DETECTION AND ANALYSIS TOOLS



A SURVEY ON MALWARE DETECTION AND ANALYSIS TOOLSIJNSA Journal
╠²
This document summarizes a survey paper on malware detection and analysis tools. It provides an overview of different types of malware like viruses, worms, Trojans, rootkits, spyware and keyloggers. It describes techniques for malware analysis, including static analysis which examines code without execution, and dynamic analysis which analyzes behavior during execution. It also lists some limitations of static analysis and the need for dynamic analysis. Finally, it discusses various tools available for malware detection, analysis, reverse engineering and debugging.Survey on Malware Detection Techniques



Survey on Malware Detection TechniquesEditor IJMTER
╠²
Malware is a worldwide pandemic. It is designed to damage computer systems without
the knowledge of the owner using the system. SoftwareŌƤs from reputable vendors also contain
malicious code that affects the system or leaks informationŌƤs to remote servers. MalwareŌƤs includes
computer viruses, spyware, dishonest ad-ware, rootkits, Trojans, dialers etc. Malware detectors are
the primary tools in defense against malware. The quality of such a detector is determined by the
techniques it uses. It is therefore imperative that we study malware detection techniques and
understand their strengths and limitations. This survey examines different types of Malware and
malware detection methods.Malware detection



Malware detectionssuser1eca7d
╠²
WhatŌĆÖs spyware and malware detection? How to carry out malware detection? How to tell if you are infected by malware? How to survive from malware attacks?Fundamental of malware analysis



Fundamental of malware analysisSumedt Jitpukdebodin
╠²
This document discusses the fundamentals of malware analysis. It outlines the objectives of malware analysis as understanding a file's statistics, behaviors, and effects on the operating system and network. It also describes methods of malware analysis including static analysis of a file's code and structure, dynamic analysis of its behaviors when run, and automatic analysis using online sandboxes. The document concludes that a malware analysis report should outline the malware's statistics, spreading mechanisms, persistence, network usage, and recommended defenses.More Related Content
Similar to CHAPTER 1 MALWARE ANALYSIS PRIMER.ppt (20)
Basic survey on malware analysis, tools and techniques



Basic survey on malware analysis, tools and techniquesijcsa
╠²
The term malware stands for malicious software. It is a program installed on a system without the
knowledge of owner of the system. It is basically installed by the third party with the intention to steal some
private data from the system or simply just to play pranks. This in turn threatens the computerŌĆÖs security,
wherein computer are used by oneŌĆÖs in day-to-day life as to deal with various necessities like education,
communication, hospitals, banking, entertainment etc. Different traditional techniques are used to detect
and defend these malwares like Antivirus Scanner (AVS), firewalls, etc. But today malware writers are one
step forward towards then Malware detectors. Day-by-day they write new malwares, which become a great
challenge for malware detectors. This paper focuses on basis study of malwares and various detection
techniques which can be used to detect malwares.Introduction to Malware analysis 



Introduction to Malware analysis HusseinMuhaisen
╠²
Hey Guys , In This ║▌║▌▀Ż I'll be Directing you guys to the stepping stones of getting into malware analysis. Just Make Sure to focus on the slides and you are ready to go A FRAMEWORK FOR ANALYSIS AND COMPARISON OF DYNAMIC MALWARE ANALYSIS TOOLS



A FRAMEWORK FOR ANALYSIS AND COMPARISON OF DYNAMIC MALWARE ANALYSIS TOOLSIJNSA Journal
╠²
Malware writers have employed various obfuscation and polymorphism techniques to thwart static analysis approaches and bypassing antivirus tools. Dynamic analysis techniques, however, have essentially overcome these deceits by observing the actual behaviour of the code execution. In this regard, various methods, techniques and tools have been proposed. However, because of the diverse concepts and strategies used in the implementation of these methods and tools, security researchers and malware analysts find it difficult to select the required optimum tool to investigate the behaviour of a malware and to contain the associated risk for their study. Focusing on two dynamic analysis techniques: Function Call monitoring and Information Flow Tracking, this paper presents a comparison framework for dynamic malware analysis tools. The framework will assist the researchers and analysts to recognize the toolŌĆÖs implementation strategy, analysis approach, system-wide analysis support and its overall handling of binaries, helping them to select a suitable and effective one for their study and analysis.CNIT 126 Ch 0: Malware Analysis Primer & 1: Basic Static Techniques



CNIT 126 Ch 0: Malware Analysis Primer & 1: Basic Static TechniquesSam Bowne
╠²
║▌║▌▀Żs for a college course at City College San Francisco. Based on "Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software", by Michael Sikorski and Andrew Honig; ISBN-10: 1593272901.
Instructor: Sam Bowne
Class website: https://samsclass.info/126/126_S17.shtml
Ch0 1



Ch0 1TylerDerdun
╠²
This document provides an overview of basic static malware analysis techniques. It discusses using antivirus scanners, hashing files, and analyzing strings to identify malware without executing it. It also covers examining the Portable Executable (PE) file format used in Windows executables, including analyzing the PE header, imported and exported functions, linked libraries, and important sections like .text and .rsrc. Detecting packed files and analyzing the PE dynamically at runtime is also mentioned. The goal is to gain an initial understanding of unknown files through static inspection before dynamic analysis.Practical Malware Analysis: Ch 0: Malware Analysis Primer & 1: Basic Static T...



Practical Malware Analysis: Ch 0: Malware Analysis Primer & 1: Basic Static T...Sam Bowne
╠²
This document provides an overview of basic static malware analysis techniques. It discusses using antivirus scanners, hashing files, and finding strings to identify malware without executing it. It also covers analyzing the Portable Executable (PE) file format used in Windows executables, including examining the PE header, imported and exported functions, linked libraries, and sections like .text and .rsrc. The document demonstrates various tools for these static analysis tasks like HashCalc, strings, PEview, Dependency Walker, and Resource Hacker.Cyber Defense Forensic Analyst - Real World Hands-on Examples



Cyber Defense Forensic Analyst - Real World Hands-on ExamplesSandeep Kumar Seeram
╠²
The document discusses analyzing malware using static and dynamic analysis techniques. Static analysis involves examining a malware file's code and structure without executing it, using tools like disassemblers and string extractors. Dynamic analysis executes malware in a controlled environment to observe its behaviors and any changes it makes. The document then demonstrates analyzing the "Netflix Account Generator" malware using an isolated cloud sandbox, where it is observed starting child processes and making outbound network connections, suggesting it is a remote access trojan.Type of Malware and its different analysis and its types !



Type of Malware and its different analysis and its types !Mohammed Jaseem Tp
╠²
This document discusses different types of malware and methods for analyzing malware. It defines malware as malicious software designed to damage computers without consent. The document outlines 10 main types of malware: viruses, worms, Trojans, spyware, adware, ransomware, rootkits, keyloggers, botnets, and bugs. It also describes 3 methods of malware analysis: static analysis, which examines code without executing it; dynamic analysis, which observes behavior by running malware; and threat analysis, which identifies malware families and tracks criminal infrastructure over time.Malware Detection Using Data Mining Techniques 



Malware Detection Using Data Mining Techniques Akash Karwande
╠²
This document discusses techniques for malware detection using data mining. It begins by defining the problem of malware as one of the most serious issues faced on the internet. It then discusses types of malware like viruses, worms, trojans, and rootkits. It describes how rootkits can hide themselves and their activities. The document outlines static and dynamic analysis methods for malware detection and describes signature-based and behavior-based detection techniques. It shows results from using the Weka tool achieving over 97% success in rootkit detection. Advanced techniques discussed include n-grams and analyzing API/system calls.Cyber Security Threats Unveilded



Cyber Security Threats UnveildedElewayte
╠²
This document provides an overview of malware analysis. It defines malware and lists common types. It describes two main techniques for analyzing malware: static and dynamic analysis. Static analysis involves examining malware code and structure without executing it, while dynamic analysis observes malware behavior by executing it in a controlled environment. The goal of malware analysis is to understand malware functionality, behavior, and impact in order to better defend against threats. Host- and network-based intrusion detection systems use malware signatures to detect unauthorized or malicious activities on individual systems and network traffic.Malware analysis



Malware analysisPrakashchand Suthar
╠²
- Malware analysis involves both static and dynamic analysis techniques to understand malware behavior and assess potential damage. Static analysis involves disassembling and reviewing malware code and structure without executing it. Dynamic analysis observes malware behavior when executed in an isolated virtual environment.
- Tools for static analysis include file hashing, string extraction, and PE header examination. Dynamic analysis tools monitor the registry, file system, processes, and network traffic created by malware runtime behavior. These include Process Monitor, Wireshark, Process Explorer, and network sniffers.
- To safely conduct malware analysis, one should create an isolated virtual lab separated from production networks, and install behavioral monitoring and code analysis tools like OllyDbg, Process Monitor, and WireshMission Impossible - Malware Analysis.pdf



Mission Impossible - Malware Analysis.pdfnull - The Open Security Community
╠²
Mission Impossible - Malware Analysis by Mohammed Danish AmberBasic Dynamic Analysis of Malware



Basic Dynamic Analysis of MalwareNatraj G
╠²
This document provides an overview of basic dynamic malware analysis techniques. It explains that dynamic analysis examines how malware behaves when executed by monitoring changes to the system, unusual processes, network traffic, and other behaviors. A number of tools are described that can be used for dynamic analysis, including sandboxes, process monitors, registry snapshots, network service emulators, and packet sniffers. Caution is advised to perform analysis safely in a isolated lab environment.Malware Classification and Analysis



Malware Classification and AnalysisPrashant Chopra
╠²
The document discusses malware analysis using machine learning. It proposes collecting malware binaries from online sources and using Cuckoo Sandbox to analyze their behavior dynamically. Features would be extracted from the analysis reports and used to classify the malware into families using machine learning algorithms. The goal is to develop an automated malware classification system that can identify both known and unknown malware types.A SURVEY ON MALWARE DETECTION AND ANALYSIS TOOLS



A SURVEY ON MALWARE DETECTION AND ANALYSIS TOOLSIJNSA Journal
╠²
This document summarizes a survey paper on malware detection and analysis tools. It provides an overview of different types of malware like viruses, worms, Trojans, rootkits, spyware and keyloggers. It describes techniques for malware analysis, including static analysis which examines code without execution, and dynamic analysis which analyzes behavior during execution. It also lists some limitations of static analysis and the need for dynamic analysis. Finally, it discusses various tools available for malware detection, analysis, reverse engineering and debugging.Survey on Malware Detection Techniques



Survey on Malware Detection TechniquesEditor IJMTER
╠²
Malware is a worldwide pandemic. It is designed to damage computer systems without
the knowledge of the owner using the system. SoftwareŌƤs from reputable vendors also contain
malicious code that affects the system or leaks informationŌƤs to remote servers. MalwareŌƤs includes
computer viruses, spyware, dishonest ad-ware, rootkits, Trojans, dialers etc. Malware detectors are
the primary tools in defense against malware. The quality of such a detector is determined by the
techniques it uses. It is therefore imperative that we study malware detection techniques and
understand their strengths and limitations. This survey examines different types of Malware and
malware detection methods.Malware detection



Malware detectionssuser1eca7d
╠²
WhatŌĆÖs spyware and malware detection? How to carry out malware detection? How to tell if you are infected by malware? How to survive from malware attacks?Fundamental of malware analysis



Fundamental of malware analysisSumedt Jitpukdebodin
╠²
This document discusses the fundamentals of malware analysis. It outlines the objectives of malware analysis as understanding a file's statistics, behaviors, and effects on the operating system and network. It also describes methods of malware analysis including static analysis of a file's code and structure, dynamic analysis of its behaviors when run, and automatic analysis using online sandboxes. The document concludes that a malware analysis report should outline the malware's statistics, spreading mechanisms, persistence, network usage, and recommended defenses.More from ManjuAppukuttan2 (17)
CHAPTER 3 BASIC DYNAMIC ANALYSIS.ppt



CHAPTER 3 BASIC DYNAMIC ANALYSIS.pptManjuAppukuttan2
╠²
This document discusses various tools and techniques for performing basic dynamic malware analysis, including sandboxes, Process Monitor, Process Explorer, and Regshot. It explains how sandboxes like GFI Sandbox can provide initial analysis of malware but have limitations. Process Monitor and Process Explorer allow monitoring processes, registry changes, and other activity in real-time. Regshot facilitates comparing registry snapshots before and after malware is run.CHAPTER 2 BASIC ANALYSIS.ppt



CHAPTER 2 BASIC ANALYSIS.pptManjuAppukuttan2
╠²
The document discusses various techniques for analyzing potential malware through static analysis. It covers hashing files to generate unique identifiers, searching for strings, examining import/export functions and the portable executable file format, and using tools like PEview and Resource Hacker. The goal of static analysis is to understand a file's functionality and attributes without executing it.UNIT 3.1 INTRODUCTON TO IDA.ppt



UNIT 3.1 INTRODUCTON TO IDA.pptManjuAppukuttan2
╠²
The document discusses disassembly theory, including first, second, and third generation languages. It then discusses the why and how of disassembly, including uses for malware analysis, vulnerability analysis, software interoperability, compiler validation, and debugging displays. It describes the basic process of disassembly and two common algorithms: linear sweep and recursive descent. Finally, it outlines some common reversing and disassembly tools like file, PE Tools, PEiD, nm, ldd, objdump, otool, and strings.UNIT 3.2 GETTING STARTED WITH IDA.ppt



UNIT 3.2 GETTING STARTED WITH IDA.pptManjuAppukuttan2
╠²
This document provides an overview of getting started with IDA and navigating disassemblies:
- Launching IDA involves choosing a file to analyze which loads the file and displays it. The history allows reopening recent files.
- The initial analysis populates various windows like Functions and disassembles the code. Data displays include graph, text, hex, and named views.
- Navigation uses double-clicks, addresses, and the stack frame. Searches find text or binary patterns.
- Common tasks involve naming locations and variables, transforming code/data, and recognizing data structures.SA UNIT III STORM.pdf



SA UNIT III STORM.pdfManjuAppukuttan2
╠²
The document defines key concepts in Storm including:
1. A Storm topology defines a graph of computation and is composed of spouts, streams, and bolts.
2. Spouts are sources that read/listen to external data and emit tuples to streams.
3. Streams are sequences of tuples that flow between topology components and can be processed in parallel by bolts.SA UNIT II KAFKA.pdf



SA UNIT II KAFKA.pdfManjuAppukuttan2
╠²
Kafka uses a publish-subscribe messaging model with topics that can be partitioned across multiple servers. Messages are organized into topics which are distributed and stored across partitions. Producers write data to topics in the form of messages which are consumed by subscribers. The messages are distributed to partitions in a partitioned topic for scalability and fault tolerance.SA UNIT I STREAMING ANALYTICS.pdf



SA UNIT I STREAMING ANALYTICS.pdfManjuAppukuttan2
╠²
The document discusses stream processing models. It describes the key components as data sources, stream processing pipelines, and data sinks. Data sources refer to the inputs of streaming data, pipelines are the processing applied to the streaming data, and sinks are the outputs where the results are stored or sent. Stateful stream processing requires ensuring state is preserved over time and data consistency even during failures. Frameworks like Apache Spark use sources and sinks to connect to streaming data sources like Kafka and send results to other systems, acting as pipelines between different distributed systems.CHAPTER 2 BASIC ANALYSIS.pdf



CHAPTER 2 BASIC ANALYSIS.pdfManjuAppukuttan2
╠²
The document discusses analyzing potential malware using static analysis techniques. It describes examining a file's Portable Executable (PE) header, which contains metadata about the code, libraries and functions. It also summarizes analyzing imported and exported functions, which can provide clues about the program's functionality. Static analysis tools like PEview, Dependency Walker, Strings and Resource Hacker are used to extract further information from files.Ad
Recently uploaded (20)
Electrical and Electronics Engineering: An International Journal (ELELIJ)



Electrical and Electronics Engineering: An International Journal (ELELIJ)elelijjournal653
╠²
Call For Papers...!!!
Electrical and Electronics Engineering: An International Journal (ELELIJ)
Web page link: https://wireilla.com/engg/eeeij/index.html
Submission Deadline: June 08, 2025
Submission link: elelijjournal@wireilla.com
Contact Us: wirelinux@wireilla.org
May 2025: Top 10 Cited Articles in Software Engineering & Applications Intern...



May 2025: Top 10 Cited Articles in Software Engineering & Applications Intern...sebastianku31
╠²
The International Journal of Software Engineering & Applications (IJSEA) is a bi-monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the Software Engineering & Applications. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern software engineering concepts & establishing new collaborations in these areas.
ISO 4020-6.1- Filter Cleanliness Test Rig Catalogue.pdf



ISO 4020-6.1- Filter Cleanliness Test Rig Catalogue.pdf FILTRATION ENGINEERING & CUNSULTANT
╠²
ISO 4020-6.1 ŌĆō Filter Cleanliness Test Rig: Precision Testing for Fuel Filter Integrity
Explore the design, functionality, and standards compliance of our advanced Filter Cleanliness Test Rig developed according to ISO 4020-6.1. This rig is engineered to evaluate fuel filter cleanliness levels with high accuracy and repeatabilityŌĆöcritical for ensuring the performance and durability of fuel systems.
¤ö¼ Inside This Presentation:
Overview of ISO 4020-6.1 testing protocols
Rig components and schematic layout
Test methodology and data acquisition
Applications in automotive and industrial filtration
Key benefits: accuracy, reliability, compliance
Perfect for R&D engineers, quality assurance teams, and lab technicians focused on filtration performance and standard compliance.
¤øĀ’ĖÅ Ensure Filter Cleanliness ŌĆö Validate with Confidence."The Enigmas of the Riemann Hypothesis" by Julio Chai



"The Enigmas of the Riemann Hypothesis" by Julio ChaiJulio Chai
╠²
In the vast tapestry of the history of mathematics, where the brightest minds have woven with threads of logical reasoning and flash-es of intuition, the Riemann Hypothesis emerges as a mystery that chal-lenges the limits of human understanding. To grasp its origin and signif-icance, it is necessary to return to the dawn of a discipline that, like an incomplete map, sought to decipher the hidden patterns in numbers. This journey, comparable to an exploration into the unknown, takes us to a time when mathematicians were just beginning to glimpse order in the apparent chaos of prime numbers.
Centuries ago, when the ancient Greeks contemplated the stars and sought answers to the deepest questions in the sky, they also turned their attention to the mysteries of numbers. Pythagoras and his followers revered numbers as if they were divine entities, bearers of a universal harmony. Among them, prime numbers stood out as the cornerstones of an infinite cathedralŌĆöindivisible and enigmaticŌĆöhiding their ar-rangement beneath a veil of apparent randomness. Yet, their importance in building the edifice of number theory was already evident.
The Middle Ages, a period in which the light of knowledge flick-ered in rhythm with the storms of history, did not significantly advance this quest. It was the Renaissance that restored lost splendor to mathe-matical thought. In this context, great thinkers like Pierre de Fermat and Leonhard Euler took up the torch, illuminating the path toward a deeper understanding of prime numbers. Fermat, with his sharp intuition and ability to find patterns where others saw disorder, and Euler, whose overflowing genius connected number theory with other branches of mathematics, were the architects of a new era of exploration. Like build-ers designing a bridge over an unknown abyss, their contributions laid the groundwork for later discoveries.
Utilizing Biomedical Waste for Sustainable Brick Manufacturing: A Novel Appro...



Utilizing Biomedical Waste for Sustainable Brick Manufacturing: A Novel Appro...IRJET Journal
╠²
https://www.irjet.net/archives/V11/i2/IRJET-V11I209.pdfStructural Health and Factors affecting.pptx



Structural Health and Factors affecting.pptxgunjalsachin
╠²
Structural Health- Factors affecting Health of Structures,
Causes of deterioration in RC structures-Permeability of concrete, capillary porosity, air voids, Micro cracks and macro cracks, corrosion of reinforcing bars, sulphate attack, alkali silica reaction
Causes of deterioration in Steel Structures: corrosion, Uniform deterioration, pitting, crevice, galvanic, laminar, Erosion, cavitations, fretting, Exfoliation, Stress, causes of defects in connection
Maintenance and inspection of structures.Proposed EPA Municipal Waste Combustor Rule



Proposed EPA Municipal Waste Combustor RuleAlvaroLinero2
╠²
Florida Section AWMA Presentation on Proposed EPA Municipal Waste Combustor Rule. Reviews EPA procedures to set standards and pitfalls.Digital Crime ŌĆō Substantive Criminal Law ŌĆō General Conditions ŌĆō Offenses ŌĆō In...



Digital Crime ŌĆō Substantive Criminal Law ŌĆō General Conditions ŌĆō Offenses ŌĆō In...ManiMaran230751
╠²
Digital Crime ŌĆō Substantive Criminal Law ŌĆō General Conditions ŌĆō Offenses ŌĆō Investigation Methods for
Collecting Digital Evidence ŌĆō International Cooperation to Collect Digital Evidence.9aeb2aae-3b85-47a5-9776-154883bbae57.pdf



9aeb2aae-3b85-47a5-9776-154883bbae57.pdfRishabhGupta578788
╠²
Certification of participation for the tata crucibal campus quiz 2024Direct Current circuitsDirect Current circuitsDirect Current circuitsDirect C...



Direct Current circuitsDirect Current circuitsDirect Current circuitsDirect C...BeHappy728244
╠²
Direct Current circuitsFresh concrete Workability Measurement



Fresh concrete Workability MeasurementSasiVarman5
╠²
Fresh concrete
Workability
Measurement of workability
Factor affecting workability
Hardened concrete
Strength stress strain characteristics
Segregation and bleeding
Creep durability of concrete
Water absorption permeability
Corrosion test acid resistance
Forensic Science ŌĆō Digital Forensics ŌĆō Digital Evidence ŌĆō The Digital Forensi...



Forensic Science ŌĆō Digital Forensics ŌĆō Digital Evidence ŌĆō The Digital Forensi...ManiMaran230751
╠²
Forensic Science ŌĆō Digital Forensics ŌĆō Digital Evidence ŌĆō The Digital Forensics Process ŌĆō Introduction ŌĆō The
Identification Phase ŌĆō The Collection Phase ŌĆō The Examination Phase ŌĆō The Analysis Phase ŌĆō The
Presentation Phase.ISO 4548-9 Oil Filter Anti Drain Catalogue.pdf



ISO 4548-9 Oil Filter Anti Drain Catalogue.pdf FILTRATION ENGINEERING & CUNSULTANT
╠²
This presentation showcases a detailed catalogue of testing solutions aligned with ISO 4548-9, the international standard for evaluating the anti-drain valve performance in full-flow lubricating oil filters used in internal combustion engines.
Topics covered include:[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)
![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)
![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)
![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)
[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)ĒĢśņØ┤Ēöīļ¤ŁņŖż / HIFLUX Co., Ltd.
╠²
Lok Fitting, VCR Fitting, Pipe FittingISO 4548-7 Filter Vibration Fatigue Test Rig Catalogue.pdf



ISO 4548-7 Filter Vibration Fatigue Test Rig Catalogue.pdf FILTRATION ENGINEERING & CUNSULTANT
╠²
This presentation provides a comprehensive overview of a specialized test rig designed in accordance with ISO 4548-7, the international standard for evaluating the vibration fatigue resistance of full-flow lubricating oil filters used in internal combustion engines.
Key features include:Application Security and Secure Software Development Lifecycle



Application Security and Secure Software Development LifecycleDrKavithaP1
╠²
It Explain about application security and software development life cycleMay 2025 - Top 10 Read Articles in Artificial Intelligence and Applications (...



May 2025 - Top 10 Read Articles in Artificial Intelligence and Applications (...gerogepatton
╠²
The International Journal of Artificial Intelligence & Applications (IJAIA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the Artificial Intelligence & Applications (IJAIA). It is an international journal intended for professionals and researchers in all fields of AI for researchers, programmers, and software and hardware manufacturers. The journal also aims to publish new attempts in the form of special issues on emerging areas in Artificial Intelligence and applications.Digital Crime ŌĆō Substantive Criminal Law ŌĆō General Conditions ŌĆō Offenses ŌĆō In...



Digital Crime ŌĆō Substantive Criminal Law ŌĆō General Conditions ŌĆō Offenses ŌĆō In...ManiMaran230751
╠²
Forensic Science ŌĆō Digital Forensics ŌĆō Digital Evidence ŌĆō The Digital Forensi...



Forensic Science ŌĆō Digital Forensics ŌĆō Digital Evidence ŌĆō The Digital Forensi...ManiMaran230751
╠²
Ad
CHAPTER 1 MALWARE ANALYSIS PRIMER.ppt
- 1. Chapter 1 Malware Analysis Primer Prepared by, Dr. A. Manju, M.E., Ph.D, Assistant Professor, SRM Institute of Science & Technology, Ramapuram Campus Michael Sikorski, Practical Malware Analysis ŌĆō The Hands-On Guide to Dissecting Malicious Software, Kindle Edition, No Starch Press; 1 edition (1 February 2012), ISBN: 1593272901
- 2. Outline ’Ƭ The Goals of Malware Analysis ’Ƭ Malware Analysis Techniques ’Ƭ Types of Malware ’Ƭ General Rules for Malware Analysis
- 3. The Goals of Malware Analysis ’éĘ The purpose of malware analysis is usually to provide the information you need to respond to a network intrusion. ’éĘ Your goals will typically be to determine exactly what happened, and to ensure that youŌĆÖve located all infected machines and files. ’éĘ When analyzing suspected malware, your goal will typically be to determine exactly what a particular suspect binary can do, how to detect it on your network, and how to measure and contain its damage. ’éĘ Once you identify which files require full analysis, itŌĆÖs time to develop signatures to detect malware infections on your network.
- 4. The Goals of Malware Analysis ’éĘ Host-based signatures, or indicators, are used to detect malicious code on victim computers. These indicators often identify files created or modified by the malware or specific changes that it makes to the registry. Unlike antivirus signatures, malware indicators focus on what the malware does to a system, not on the characteristics of the malware itself, which makes them more effective in detecting malware that changes form or that has been deleted from the hard disk. ’éĘ Network signatures are used to detect malicious code by monitoring network traffic. Network signatures can be created without malware analysis, but signatures created with the help of malware analysis are usually far more effective, offering a higher detection rate and fewer false positives.
- 5. Malware Analysis Techniques ’éĘ There are two fundamental approaches to malware analysis: o static and o dynamic. ’éĘ Static analysis involves examining the malware without running it. ’éĘ Dynamic analysis involves running the malware.
- 6. Malware Analysis Techniques ’éĘ Both techniques are further categorized as basic or advanced. ’éĘ Basic Static Analysis: o Examining the executable file without viewing the actual instructions. o Confirm whether a file is malicious, provide information about its functionality, and sometimes provide information that will allow you to produce simple network signatures. o Straightforward and can be quick, but itŌĆÖs largely ineffective against sophisticated malware, and it can miss important behaviors. ’éĘ Basic Dynamic Analysis: o Involve running the malware and observing its behavior on the system in order to remove the infection, produce effective signatures, or both. o However, before you can run malware safely, you must set up an environment that will allow you to study the running malware without risk of damage to your system or network. o Basic dynamic analysis techniques can be used by most people without deep programming knowledge, but they wonŌĆÖt be effective with all malware and can miss important functionality.
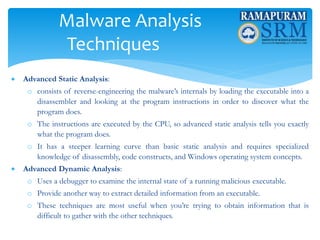
- 7. Malware Analysis Techniques ’éĘ Advanced Static Analysis: o consists of reverse-engineering the malwareŌĆÖs internals by loading the executable into a disassembler and looking at the program instructions in order to discover what the program does. o The instructions are executed by the CPU, so advanced static analysis tells you exactly what the program does. o It has a steeper learning curve than basic static analysis and requires specialized knowledge of disassembly, code constructs, and Windows operating system concepts. ’éĘ Advanced Dynamic Analysis: o Uses a debugger to examine the internal state of a running malicious executable. o Provide another way to extract detailed information from an executable. o These techniques are most useful when youŌĆÖre trying to obtain information that is difficult to gather with the other techniques.
- 8. Types of Malware ’Ƭ Backdoor: Malicious code that installs itself onto a computer to allow the attacker access. Backdoors usually let the attacker connect to the computer with little or no authentication and execute commands on the local system. ’Ƭ Botnet: Similar to a backdoor, in that it allows the attacker access to the system, but all computers infected with the same botnet receive the same instructions from a single command-and-control server. ’Ƭ Downloader: Malicious code that exists only to download other malicious code. Downloaders are commonly installed by attackers when they first gain access to a system. The downloader program will download and install additional malicious code.
- 9. Types of Malware ’Ƭ Information-stealing malware: Malware that collects information from a victimŌĆÖs computer and usually sends it to the attacker. Examples include sniffers, password hash grabbers, and keyloggers. This malware is typically used to gain access to online accounts such as email or online banking. ’Ƭ Launcher: Malicious program used to launch other malicious programs. Usually, launchers use non-traditional techniques to launch other malicious programs in order to ensure stealth or greater access to a system. ’Ƭ Rootkit: Malicious code designed to conceal the existence of other code. Rootkits are usually paired with other malware, such as a backdoor, to allow remote access to the attacker and make the code difficult for the victim to detect.
- 10. Types of Malware ’Ƭ Scareware: Malware designed to frighten an infected user into buying something. It usually has a user interface that makes it look like an antivirus or other security program. It informs users that there is malicious code on their system and that the only way to get rid of it is to buy their ŌĆ£software,ŌĆØ when in reality, the software itŌĆÖs selling does nothing more than remove the scareware. ’Ƭ Spam-sending malware: Malware that infects a userŌĆÖs machine and then uses that machine to send spam. This malware generates income for attackers by allowing them to sell spam- sending services. ’Ƭ Worm or virus: Malicious code that can copy itself and infect additional computers.
- 11. General Rules of Malware Analysis ’éĘ Most malware programs are large and complex, and you canŌĆÖt possibly understand every detail. First, focus on the key features. When you run into difficult and complex sections, try to get a general overview before you get stuck in the weeds. ’éĘ Second, remember that different tools and approaches are available for different jobs. There is no one approach. If you get stuck, donŌĆÖt spend too long on any one issue; move on to something else. Try analyzing the malware from a different angle, or just try a different approach. ’éĘ Finally, remember that malware analysis is like a cat-and-mouse game. As new malware analysis techniques are developed, malware authors respond with new techniques to thwart analysis. To succeed as a malware analyst, you must be able to recognize, understand, and defeat these techniques, and respond to changes in the art of malware analysis.












![[HIFLUX] High Pressure Tube Support Catalog 2025](https://cdn.slidesharecdn.com/ss_thumbnails/tubesupporten-250529073613-16c22974-thumbnail.jpg?width=560&fit=bounds)
