CIM Compliance.pptx
Download as pptx, pdf0 likes24 views
The document discusses common information modeling (CIM) which involves normalizing event data from different sources to a common standard. It describes the steps to implement CIM which include: defining events and fields, standardizing field names, validating for issues, setting up the CIM app, and rebuilding the data model. The goal of CIM is to allow faster searching across all event data regardless of source.
1 of 18
Download to read offline





Ad
Recommended
Splunk live! ninjas_break-out
Splunk live! ninjas_break-outSplunk
╠²
The document provides an overview of new features in Splunk Enterprise 6.1 including enhanced interactive analytics, embedding operational intelligence, and enabling the mission-critical enterprise. It discusses data models and pivot which allow analyzing data without search commands. Finally, it highlights five powerful search commands (eval, stats, eventstats, streamstats, transaction) that can solve most data analysis problems.Pragmatic Patterns (and Pitfalls) for Event Streaming in Brownfield Environme...
Pragmatic Patterns (and Pitfalls) for Event Streaming in Brownfield Environme...HostedbyConfluent
╠²
This document discusses using Apache Kafka for event streaming and summarizes some key challenges and solutions. It addresses how to get data into Kafka, ensure completeness of events from multiple data sources, handle asynchronous workflows, detect absence of expected events, and track complex workflows with a routing slip pattern.Data Onboarding Breakout Session
Data Onboarding Breakout SessionSplunk
╠²
This document discusses Splunk's data onboarding process, which provides a systematic way to ingest new data sources into Splunk. It ensures new data is instantly usable and valuable. The process involves several steps: pre-boarding to identify the data and required configurations; building index-time configurations; creating search-time configurations like extractions and lookups; developing data models; testing; and deploying the new data source. Following this process helps get new data onboarding right the first time and makes the data immediately useful.Using a Data Model to Bridge the Mainframe-Splunk Knowledge Gap
Using a Data Model to Bridge the Mainframe-Splunk Knowledge GapPrecisely
╠²
The document discusses the use of data models to simplify access to mainframe and complex log data for less technical users, presented by Ian Hartley. It highlights how data models bridge knowledge gaps by organizing data into user-friendly structures, enhancing search efficiency, and incorporating expert knowledge for improved insights. The benefits include broader audience access, reduced errors, and faster return on investment through clearer metrics and accelerated searches.Tech Talk SQL Server 2012 Business Intelligence
Tech Talk SQL Server 2012 Business IntelligenceRay Cochrane
╠²
This document provides an overview and update on Microsoft Business Intelligence tools in SQL Server 2012, including:
1) New features for Analysis Services like improved multidimensional model performance and new tabular project types.
2) Enhancements to Master Data Services and Data Quality Services for data governance and quality.
3) Updates to Reporting Services including new SharePoint integration and Office Open XML rendering extensions.
4) A introduction to Power View and its interactive data exploration and visualization capabilities integrated with PowerPivot.DataPreprocessing.ppt
DataPreprocessing.pptTesfahunAsmare1
╠²
Data preparation involves collecting, cleaning, integrating, and reducing data from multiple sources. Common data quality issues include missing or incorrect values, inconsistencies, and redundancy. Data must be cleaned by filling in missing values, resolving inconsistencies, removing outliers and noisy data. Integrating data from different sources requires resolving issues like different data formats, structures, and levels of detail. Dimensionality reduction and sampling techniques can reduce data volume for analysis while maintaining quality. Data transformation through normalization and discretization further prepares data for mining.Data preparation and processing chapter 2
Data preparation and processing chapter 2Mahmoud Alfarra
╠²
This document provides an overview of key aspects of data preparation and processing for data mining. It discusses the importance of domain expertise in understanding data. The goals of data preparation are identified as cleaning missing, noisy, and inconsistent data; integrating data from multiple sources; transforming data into appropriate formats; and reducing data through feature selection, sampling, and discretization. Common techniques for each step are outlined at a high level, such as binning, clustering, and regression for handling noisy data. The document emphasizes that data preparation is crucial and can require 70-80% of the effort for effective real-world data mining.MISTI Infosec 2010- SIEM Implementation
MISTI Infosec 2010- SIEM ImplementationMichael Nickle
╠²
The document discusses the implementation of Security Information and Event Management (SIEM) systems, highlighting key points related to the development of business and technical requirements, vendor selection criteria, and the value of SIEM in managing compliance and risk. It emphasizes the importance of understanding organizational needs, defining success metrics, and addressing post-implementation challenges, such as complexity and ownership issues. A case study is provided to illustrate successful SIEM implementation, along with strategies for effective integration and ongoing support.fundamentalsofeventdrivenmicroservices11728489736099.pdf
fundamentalsofeventdrivenmicroservices11728489736099.pdfSmarak Pani
╠²
The document provides a comprehensive overview of event-driven microservices, focusing on communication structures, service modeling, and event modeling. It discusses the challenges of modern architectures, including data management and scaling with synchronous services, while emphasizing the importance of event streams as a single source of truth. The content is structured in three parts: foundational concepts, event modeling techniques, and practical service modeling examples to guide effective implementation of microservices.Data processing
Data processingakanshagoyal1989
╠²
This document discusses various techniques for data processing including data cleaning, integration, transformation, reduction, and similarity/dissimilarity measures. It describes common types of dirty or incomplete data like missing values, noisy data, and inconsistent data. It also discusses techniques for handling different types of dirty data, such as filling in missing values, smoothing noisy data, and resolving inconsistencies. Major tasks in data processing include data cleaning, integration, transformation, and reduction. Specific techniques discussed include binning, clustering, regression, normalization, aggregation, and dimensionality reduction. The document also provides details on various similarity and dissimilarity measures that can be used to calculate the proximity between data objects.Cyber Threat Ranking using READ
Cyber Threat Ranking using READZachary S. Brown
╠²
This document describes a proposed approach to rank cyber threat indicators of compromise (IOCs) matched in enterprise data based on reconstruction error from principal component analysis (PCA). The approach involves extracting IOCs from threat feeds, matching them to features engineered from proxy log and other data, decomposing the matched features with PCA, calculating a reconstruction error score to rank matches, and supplementing top ranked matches with contextual details to aid investigation. Future work may include adding an autoencoder model, incorporating analyst feedback, and using additional data sources.Sql Server 2012
Sql Server 2012Performics.Convonix
╠²
The document outlines the enhancements and features of SQL Server 2012 relevant to business intelligence, including improvements in availability, scalability, performance, manageability, and security. It emphasizes the importance of data quality and introduces management strategies through data quality services (DQS) and master data services (MDS) for maintaining accurate and consistent data. Additionally, it highlights new analytical features such as Power View and integration capabilities for better data visualization and insights.Mitigating One Million Security Threats With Kafka and Spark With Arun Janart...
Mitigating One Million Security Threats With Kafka and Spark With Arun Janart...HostedbyConfluent
╠²
Citrix has developed a comprehensive security analytics architecture to mitigate over 1 million security threats for its clients, including Fortune 500 companies. The platform utilizes sophisticated data ingestion, telemetry, and custom risk indicators to detect unusual activity, reduce false positives, and initiate security actions swiftly. With a focus on hybrid work, CitrixŌĆÖs analytics supports various products to provide secure access and enhanced protection against insider threats, malware, and compromised devices.Apache Spark for Cyber Security in an Enterprise Company
Apache Spark for Cyber Security in an Enterprise CompanyDatabricks
╠²
The document outlines a presentation by Josef Niedermeier from HPE discussing the use of Apache Spark for enhancing cybersecurity in enterprise environments. It addresses challenges in processing large volumes of data, particularly in the context of Security Information and Event Management (SIEM), and how Spark can offload tasks and improve performance, including the integration of machine learning for detection capabilities. Additionally, it highlights lessons learned, challenges faced in machine learning applications, and the importance of having solid use cases for implementation.Data Science presentation for explanation of numpy and pandas
Data Science presentation for explanation of numpy and pandasspmf313
╠²
It tells what is numpy and panda which is a python library.Apply big data and data lake for processing security data collections
Apply big data and data lake for processing security data collectionsGregory Shlyuger
╠²
The document discusses the application of big data and data lakes in enhancing cybersecurity through Security Information and Event Management (SIEM) systems. It outlines the challenges of SIEM implementation, the integration of data lakes for better processing and analysis of security data, and presents a use case involving the addition of squid proxy logs to the Apache Metron platform for real-time security monitoring. The document emphasizes the need for efficient data handling and integration strategies to improve the resilience of modern enterprises against cybersecurity threats.1Chapter_ Two_ 2 Data Preparation lecture note.pptx
1Chapter_ Two_ 2 Data Preparation lecture note.pptxfikadumeuedu
╠²
The document discusses the critical steps and challenges involved in data mining, focusing on data collection, quality, preprocessing, and integration. It emphasizes the importance of data cleansing, reduction, and transformation to ensure good quality data for effective analysis. Additionally, the document outlines various data mining tasks such as predictive and descriptive modeling, along with basic algorithms like classification, clustering, and association rule discovery.Intro to Data warehousing lecture 10
Intro to Data warehousing lecture 10AnwarrChaudary
╠²
The document discusses the details of data extraction, transformation, and loading (ETL) processes, focusing on change data capture (CDC) in both modern and legacy systems. It highlights the advantages and challenges of identifying modified data, the necessity of data cleansing, and common anomalies that arise. Additionally, it outlines various data transformation types and methods to address data quality issues.SplunkLive! Presentation - Data Onboarding with Splunk
SplunkLive! Presentation - Data Onboarding with SplunkSplunk
╠²
- The data onboarding process involves systematically bringing new data sources into Splunk to make the data instantly usable and valuable for users
- The process includes pre-boarding activities like identifying the data, mapping fields, and building index-time and search-time configurations
- It also involves deploying any necessary infrastructure, deploying the configurations, testing and validating the data, and getting user approval before the process is complete3-DataPreprocessing a complete guide.pdf
3-DataPreprocessing a complete guide.pdfshobyscms
╠²
The document discusses data preprocessing and its importance in data mining, emphasizing the need for data cleaning, integration, transformation, and reduction to improve data quality. It highlights common data quality issues such as noise, missing values, and inconsistencies, and outlines techniques for handling these problems. Overall, effective data preprocessing enhances both the quality of mined results and the efficiency of the mining process.Understanding event data
Understanding event datayalisassoon
╠²
This document discusses event data and the Snowplow data pipeline. It notes that 3 years ago, analyzing user behavior and engagement using tools like Google Analytics was difficult. The Snowplow data pipeline was created to collect and analyze event-level data at scale using open source big data technologies. The pipeline has expanded to encompass different types of digital event data by developing a schema for structured JSON events and a versioning system. A real-time version of the pipeline is also being built to feed event data into applications in addition to batch processing. Developing a semantic model and standard framework for describing events is discussed as being important for enabling downstream applications to consume structured event data.ServiceNow CIS-ITSM Exam Dumps & Questions [2024]
ServiceNow CIS-ITSM Exam Dumps & Questions [2024]SkillCertProExams
╠²
The document provides information about the ServiceNow CIS-ITSM Washington exam dumps and practice tests for 2024, containing over 530 questions to help candidates prepare effectively for the exam. Skillcertpro offers detailed explanations for each question, updates the exam content bi-weekly, and guarantees a 100% pass on the first attempt with lifetime access and free updates. Additionally, it includes sample questions with explanations related to IT service management concepts and processes.Real-Time Streaming: Move IMS Data to Your Cloud Data Warehouse
Real-Time Streaming: Move IMS Data to Your Cloud Data WarehousePrecisely
╠²
The document discusses the importance and challenges of moving IMS data to cloud data warehouses (CDWs), highlighting best practices for effective integration. It addresses the significant role of IMS within major corporations, particularly in relation to transaction data, while outlining common issues and strategies for improving data transfer processes. Additionally, it emphasizes the need for a structured and incremental approach to minimize data overload and maximize efficiency in streaming performance.Data Preprocessing
Data PreprocessingT Kavitha
╠²
Data preprocessing involves cleaning, transforming, and reducing raw data to improve its quality and prepare it for analysis. It addresses issues like missing values, noise, inconsistencies, and redundancies. The document outlines various techniques for data cleaning (e.g. handling missing values, smoothing noisy data), integration (e.g. schema matching), and reduction (e.g. dimensionality reduction, numerosity reduction). The goal of preprocessing is to produce quality data that leads to more accurate and efficient data mining and decision making.Chapter 2 Cond (1).ppt
Chapter 2 Cond (1).pptkannaradhas
╠²
The document discusses data preprocessing concepts from Chapter 3 of the book "Data Mining: Concepts and Techniques". It covers topics like data quality, major tasks in preprocessing including data cleaning, integration and reduction. Data cleaning involves handling incomplete, noisy and inconsistent data using techniques such as imputation of missing values, smoothing of noisy data, and resolving inconsistencies. Data integration combines data from multiple sources which requires tasks like schema integration and entity identification. Data reduction techniques include dimensionality reduction and data compression.Data Management Workshop - ETOT 2016
Data Management Workshop - ETOT 2016DataGenic Ltd
╠²
The document discusses a workshop focused on adapting IT department strategies to data and analytics, highlighting trends and best practices in data management across various industries. It covers topics such as data collection, categorization, validation, and the use of technologies like cloud services and open-source databases. Additionally, it emphasizes the importance of quality management and methods for handling high volumes of data.Salesforce Summer '25 Release Frenchgathering.pptx.pdf
Salesforce Summer '25 Release Frenchgathering.pptx.pdfyosra Saidani
╠²
Salesforce Summer '25 Release Frenchgathering.pptx.pdfA Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash
╠²
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and PrivacyMore Related Content
Similar to CIM Compliance.pptx (20)
fundamentalsofeventdrivenmicroservices11728489736099.pdf
fundamentalsofeventdrivenmicroservices11728489736099.pdfSmarak Pani
╠²
The document provides a comprehensive overview of event-driven microservices, focusing on communication structures, service modeling, and event modeling. It discusses the challenges of modern architectures, including data management and scaling with synchronous services, while emphasizing the importance of event streams as a single source of truth. The content is structured in three parts: foundational concepts, event modeling techniques, and practical service modeling examples to guide effective implementation of microservices.Data processing
Data processingakanshagoyal1989
╠²
This document discusses various techniques for data processing including data cleaning, integration, transformation, reduction, and similarity/dissimilarity measures. It describes common types of dirty or incomplete data like missing values, noisy data, and inconsistent data. It also discusses techniques for handling different types of dirty data, such as filling in missing values, smoothing noisy data, and resolving inconsistencies. Major tasks in data processing include data cleaning, integration, transformation, and reduction. Specific techniques discussed include binning, clustering, regression, normalization, aggregation, and dimensionality reduction. The document also provides details on various similarity and dissimilarity measures that can be used to calculate the proximity between data objects.Cyber Threat Ranking using READ
Cyber Threat Ranking using READZachary S. Brown
╠²
This document describes a proposed approach to rank cyber threat indicators of compromise (IOCs) matched in enterprise data based on reconstruction error from principal component analysis (PCA). The approach involves extracting IOCs from threat feeds, matching them to features engineered from proxy log and other data, decomposing the matched features with PCA, calculating a reconstruction error score to rank matches, and supplementing top ranked matches with contextual details to aid investigation. Future work may include adding an autoencoder model, incorporating analyst feedback, and using additional data sources.Sql Server 2012
Sql Server 2012Performics.Convonix
╠²
The document outlines the enhancements and features of SQL Server 2012 relevant to business intelligence, including improvements in availability, scalability, performance, manageability, and security. It emphasizes the importance of data quality and introduces management strategies through data quality services (DQS) and master data services (MDS) for maintaining accurate and consistent data. Additionally, it highlights new analytical features such as Power View and integration capabilities for better data visualization and insights.Mitigating One Million Security Threats With Kafka and Spark With Arun Janart...
Mitigating One Million Security Threats With Kafka and Spark With Arun Janart...HostedbyConfluent
╠²
Citrix has developed a comprehensive security analytics architecture to mitigate over 1 million security threats for its clients, including Fortune 500 companies. The platform utilizes sophisticated data ingestion, telemetry, and custom risk indicators to detect unusual activity, reduce false positives, and initiate security actions swiftly. With a focus on hybrid work, CitrixŌĆÖs analytics supports various products to provide secure access and enhanced protection against insider threats, malware, and compromised devices.Apache Spark for Cyber Security in an Enterprise Company
Apache Spark for Cyber Security in an Enterprise CompanyDatabricks
╠²
The document outlines a presentation by Josef Niedermeier from HPE discussing the use of Apache Spark for enhancing cybersecurity in enterprise environments. It addresses challenges in processing large volumes of data, particularly in the context of Security Information and Event Management (SIEM), and how Spark can offload tasks and improve performance, including the integration of machine learning for detection capabilities. Additionally, it highlights lessons learned, challenges faced in machine learning applications, and the importance of having solid use cases for implementation.Data Science presentation for explanation of numpy and pandas
Data Science presentation for explanation of numpy and pandasspmf313
╠²
It tells what is numpy and panda which is a python library.Apply big data and data lake for processing security data collections
Apply big data and data lake for processing security data collectionsGregory Shlyuger
╠²
The document discusses the application of big data and data lakes in enhancing cybersecurity through Security Information and Event Management (SIEM) systems. It outlines the challenges of SIEM implementation, the integration of data lakes for better processing and analysis of security data, and presents a use case involving the addition of squid proxy logs to the Apache Metron platform for real-time security monitoring. The document emphasizes the need for efficient data handling and integration strategies to improve the resilience of modern enterprises against cybersecurity threats.1Chapter_ Two_ 2 Data Preparation lecture note.pptx
1Chapter_ Two_ 2 Data Preparation lecture note.pptxfikadumeuedu
╠²
The document discusses the critical steps and challenges involved in data mining, focusing on data collection, quality, preprocessing, and integration. It emphasizes the importance of data cleansing, reduction, and transformation to ensure good quality data for effective analysis. Additionally, the document outlines various data mining tasks such as predictive and descriptive modeling, along with basic algorithms like classification, clustering, and association rule discovery.Intro to Data warehousing lecture 10
Intro to Data warehousing lecture 10AnwarrChaudary
╠²
The document discusses the details of data extraction, transformation, and loading (ETL) processes, focusing on change data capture (CDC) in both modern and legacy systems. It highlights the advantages and challenges of identifying modified data, the necessity of data cleansing, and common anomalies that arise. Additionally, it outlines various data transformation types and methods to address data quality issues.SplunkLive! Presentation - Data Onboarding with Splunk
SplunkLive! Presentation - Data Onboarding with SplunkSplunk
╠²
- The data onboarding process involves systematically bringing new data sources into Splunk to make the data instantly usable and valuable for users
- The process includes pre-boarding activities like identifying the data, mapping fields, and building index-time and search-time configurations
- It also involves deploying any necessary infrastructure, deploying the configurations, testing and validating the data, and getting user approval before the process is complete3-DataPreprocessing a complete guide.pdf
3-DataPreprocessing a complete guide.pdfshobyscms
╠²
The document discusses data preprocessing and its importance in data mining, emphasizing the need for data cleaning, integration, transformation, and reduction to improve data quality. It highlights common data quality issues such as noise, missing values, and inconsistencies, and outlines techniques for handling these problems. Overall, effective data preprocessing enhances both the quality of mined results and the efficiency of the mining process.Understanding event data
Understanding event datayalisassoon
╠²
This document discusses event data and the Snowplow data pipeline. It notes that 3 years ago, analyzing user behavior and engagement using tools like Google Analytics was difficult. The Snowplow data pipeline was created to collect and analyze event-level data at scale using open source big data technologies. The pipeline has expanded to encompass different types of digital event data by developing a schema for structured JSON events and a versioning system. A real-time version of the pipeline is also being built to feed event data into applications in addition to batch processing. Developing a semantic model and standard framework for describing events is discussed as being important for enabling downstream applications to consume structured event data.ServiceNow CIS-ITSM Exam Dumps & Questions [2024]
ServiceNow CIS-ITSM Exam Dumps & Questions [2024]SkillCertProExams
╠²
The document provides information about the ServiceNow CIS-ITSM Washington exam dumps and practice tests for 2024, containing over 530 questions to help candidates prepare effectively for the exam. Skillcertpro offers detailed explanations for each question, updates the exam content bi-weekly, and guarantees a 100% pass on the first attempt with lifetime access and free updates. Additionally, it includes sample questions with explanations related to IT service management concepts and processes.Real-Time Streaming: Move IMS Data to Your Cloud Data Warehouse
Real-Time Streaming: Move IMS Data to Your Cloud Data WarehousePrecisely
╠²
The document discusses the importance and challenges of moving IMS data to cloud data warehouses (CDWs), highlighting best practices for effective integration. It addresses the significant role of IMS within major corporations, particularly in relation to transaction data, while outlining common issues and strategies for improving data transfer processes. Additionally, it emphasizes the need for a structured and incremental approach to minimize data overload and maximize efficiency in streaming performance.Data Preprocessing
Data PreprocessingT Kavitha
╠²
Data preprocessing involves cleaning, transforming, and reducing raw data to improve its quality and prepare it for analysis. It addresses issues like missing values, noise, inconsistencies, and redundancies. The document outlines various techniques for data cleaning (e.g. handling missing values, smoothing noisy data), integration (e.g. schema matching), and reduction (e.g. dimensionality reduction, numerosity reduction). The goal of preprocessing is to produce quality data that leads to more accurate and efficient data mining and decision making.Chapter 2 Cond (1).ppt
Chapter 2 Cond (1).pptkannaradhas
╠²
The document discusses data preprocessing concepts from Chapter 3 of the book "Data Mining: Concepts and Techniques". It covers topics like data quality, major tasks in preprocessing including data cleaning, integration and reduction. Data cleaning involves handling incomplete, noisy and inconsistent data using techniques such as imputation of missing values, smoothing of noisy data, and resolving inconsistencies. Data integration combines data from multiple sources which requires tasks like schema integration and entity identification. Data reduction techniques include dimensionality reduction and data compression.Data Management Workshop - ETOT 2016
Data Management Workshop - ETOT 2016DataGenic Ltd
╠²
The document discusses a workshop focused on adapting IT department strategies to data and analytics, highlighting trends and best practices in data management across various industries. It covers topics such as data collection, categorization, validation, and the use of technologies like cloud services and open-source databases. Additionally, it emphasizes the importance of quality management and methods for handling high volumes of data.Recently uploaded (20)
Salesforce Summer '25 Release Frenchgathering.pptx.pdf
Salesforce Summer '25 Release Frenchgathering.pptx.pdfyosra Saidani
╠²
Salesforce Summer '25 Release Frenchgathering.pptx.pdfA Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash
╠²
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and PrivacyPyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc
╠²
AI VIDEO MAGAZINE - r/aivideo community newsletter ŌĆō Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash
╠²
Oh, the Possibilities - Balancing Innovation and Risk with Generative AIOpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM
╠²
penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Nowcnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2
╠²
ū×ū©ūøū¢ ūóūÖūæūĢūōūÖūØ ū¬ūóū®ūÖūÖū¬ūÖ ūæūóū£ 3/4/5 ū”ūÖū©ūÖūØ, ūóūō 22 ūöūŚū£ūżūĢū¬ ūøū£ūÖūØ ūóūØ ūøū£ ūÉūżū®ū©ūĢūÖūĢū¬ ūöūóūÖūæūĢūō ūöūōū©ūĢū®ūĢū¬.╠²ūæūóū£ ū®ūśūŚ ūóūæūĢūōūö ūÆūōūĢū£ ūĢū×ūŚū®ūæ ūĀūĢūŚ ūĢū¦ū£ ū£ūöūżūóū£ūö ūæū®ūżūö ūöūóūæū©ūÖū¬/ū©ūĢūĪūÖū¬/ūÉūĀūÆū£ūÖū¬/ūĪūżū©ūōūÖū¬/ūóū©ūæūÖū¬ ūĢūóūĢūō..
ū×ūĪūĢūÆū£ ū£ūæū”ūó ūżūóūĢū£ūĢū¬ ūóūÖūæūĢūō ū®ūĢūĀūĢū¬ ūöū×ū¬ūÉūÖū×ūĢū¬ ū£ūóūĀūżūÖūØ ū®ūĢūĀūÖūØ: ū¦ūÖūōūĢūŚ ūÉūĀūøūÖ, ūÉūĢūżū¦ūÖ, ūĀūÖūĪūĢū©, ūĢūøū©ūĪūĢūØ ūÉūĀūøūÖ.Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
╠²
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata
╠²
The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
¤æŗ Introducing Data Contracts: An agreement between data producers and consumers
¤ōØ Data Contracts key components: Understanding a contract and its purpose
¤¦æŌĆŹ¤Ä© Writing your first contract: How to create your own contracts in OpenMetadata
¤”Š An OpenMetadata MCP Server update!
Ō×Ģ And More!UserCon Belgium: Honey, VMware increased my bill
UserCon Belgium: Honey, VMware increased my billstijn40
╠²
VMwareŌĆÖs pricing changes have forced organizations to rethink their datacenter cost management strategies. While FinOps is commonly associated with cloud environments, the FinOps Foundation has recently expanded its framework to include ScopesŌĆöand Datacenter is now officially part of the equation. In this session, weŌĆÖll map the FinOps Framework to a VMware-based datacenter, focusing on cost visibility, optimization, and automation. YouŌĆÖll learn how to track costs more effectively, rightsize workloads, optimize licensing, and drive efficiencyŌĆöall without migrating to the cloud. WeŌĆÖll also explore how to align IT teams, finance, and leadership around cost-aware decision-making for on-prem environments. If your VMware bill keeps increasing and you need a new approach to cost management, this session is for you!Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash
╠²
Lessons Learned from Developing Secure AI WorkflowsAI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software
╠²
In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software
╠²
Managing airport and airspace data is no small task, especially when youŌĆÖre expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts ŌĆō all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results ŌĆō streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FMEŌĆÖs AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too.AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.Ad
CIM Compliance.pptx
- 1. CIM compliance By Matt Feeley
- 2. Copyright ┬®2023 | guidepointsecurity.com How to see it Practice of normalizing fields to a common standard like, ŌĆó source_host, source_ip, source -> src ŌĆó vendor_action, measure, result -> action ŌĆó known_auth, etc.. -> signature across data sources like, ŌĆó Windows ŌĆó Linux ŌĆó Palo, etc.. within events of matching domains (23) ŌĆó Authentication ŌĆó Malware ŌĆó Intrusion detection, etc..
- 3. Copyright ┬®2023 | guidepointsecurity.com How do you say it? Toe┬Ęma┬Ętow Tuh┬Ęmay┬Ętow Tomato
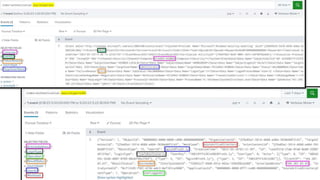
- 4. Copyright ┬®2023 | guidepointsecurity.com
- 5. Copyright ┬®2023 | guidepointsecurity.com
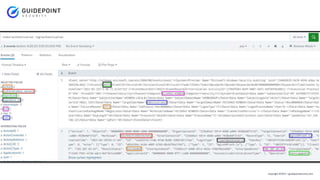
- 6. Copyright ┬®2023 | guidepointsecurity.com ŌĆó Searches Itself ŌĆó Syntax change datamodels, tstats, etc.. ŌĆó No (index=*) OR (index=win AND index=o365) ŌĆó Faster results (saved different on backend) ŌĆó Search returns all events per datamodel (regardless of data source) Why Do CIM?
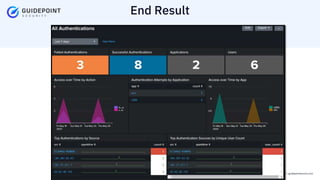
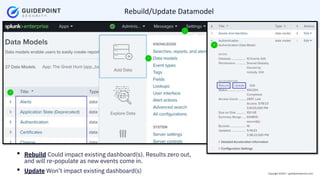
- 7. Copyright ┬®2023 | guidepointsecurity.com End Result
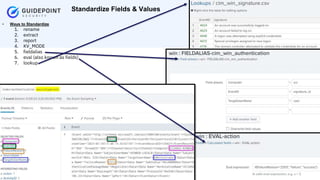
- 8. Copyright ┬®2023 | guidepointsecurity.com Steps Involved D E F I N I N G 1. Pre-requistes 1. Install CIM app 2. Identify & Define 1. Identify events to a domain 2. Define eventtypes & tags for event 3. Normalize 1. Review fields 2. Standardize the fields 4. Validate & Complete 1. Validate Check for adverse affects (like overwriting, existing fields) 2. Setup Common Information Model app 3. Rebuild/Update Datamodel
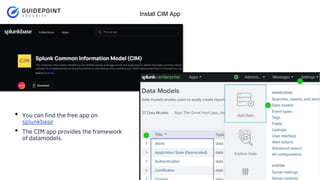
- 9. Copyright ┬®2023 | guidepointsecurity.com Install CIM App ŌĆó You can find the free app on splunkbase ŌĆó The CIM app provides the framework of datamodels.
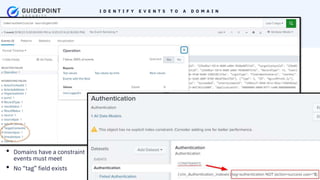
- 10. Copyright ┬®2023 | guidepointsecurity.com I D E N T I F Y E V E N T S T O A D O M A I N ŌĆó Domains have a constraint events must meet ŌĆó No ŌĆ£tagŌĆØ field exists
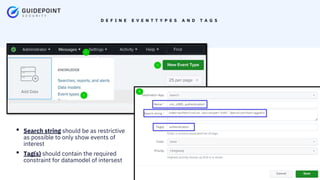
- 11. Copyright ┬®2023 | guidepointsecurity.com D E F I N E E V E N T T Y P E S A N D T A G S ŌĆó Search string should be as restrictive as possible to only show events of interest ŌĆó Tag(s) should contain the required constraint for datamodel of intersest
- 12. Copyright ┬®2023 | guidepointsecurity.com
- 13. Copyright ┬®2023 | guidepointsecurity.com Review Fields ŌĆó Use best judgement ŌĆó DonŌĆÖt be afraid to ask Admins of data source to validate ŌĆó Every field does NOT need to exist within an event ŌĆó Some events might just not contain a field
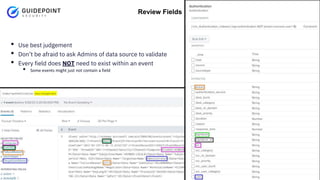
- 14. Copyright ┬®2023 | guidepointsecurity.com ŌĆó Ways to Standardize 1. rename 2. extract 3. report 4. KV_MODE 5. fieldalias 6. eval (also known as fields) 7. lookup Standardize Fields & Values
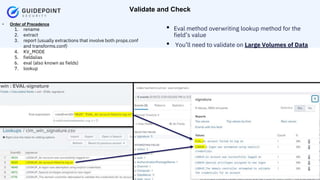
- 15. Copyright ┬®2023 | guidepointsecurity.com ŌĆó Order of Precedence 1. rename 2. extract 3. report (usually extractions that involve both props.conf and transforms.conf) 4. KV_MODE 5. fieldalias 6. eval (also known as fields) 7. lookup Validate and Check ŌĆó Eval method overwriting lookup method for the fieldŌĆÖs value ŌĆó YouŌĆÖll need to validate on Large Volumes of Data
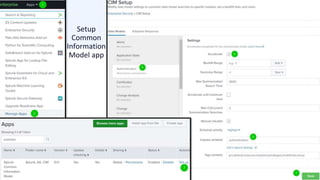
- 16. Copyright ┬®2023 | guidepointsecurity.com Setup Common Information Model app
- 17. Copyright ┬®2023 | guidepointsecurity.com Rebuild/Update Datamodel ŌĆó Rebuild Could impact existing dashboard(s). Results zero out, and will re-populate as new events come in. ŌĆó Update WonŌĆÖt impact existing dashboard(s)
- 18. Copyright ┬®2023 | guidepointsecurity.com Things to watch out for ŌĆó Set Global Permission on all Knowledge Objects ŌĆó Evals, Extractions, Eventtypes, Tags, etc.. ŌĆó Always validate pre-existing fields/events work as expected. ŌĆó Knowledge object order of precedence can over wright other knowledge objects. 1. rename 2. extract 3. report (usually extractions that involve both props.conf and transforms.conf) 4. KV_MODE 5. fieldalias 6. eval (also known as fields) 7. calculated 8. lookup PAY ATTENTION!!! ŌĆó Attempt to use add-ons from splunkbase. ŌĆó Potentially already CIM comply ŌĆó The better quality the add-on the less youŌĆÖll need to do thatŌĆÖs custom. ŌĆó You should always review and CIM even if add-on parses accurate ŌĆó Rebuild/Update datamodels at any point additional CIM compliance is done ŌĆó Every event will NOT contain every field to standardize ŌĆó Some fields require certain values for output