Cloud computing
- 2. ïWhat is Cloud Computing? ïVarious forms of Cloud Computing ïBenefits of Cloud computing ïWhy we need cloud security? ï Cloud Security Concerns ï Cloud Security Threats ï Cloud Security Mechanisms
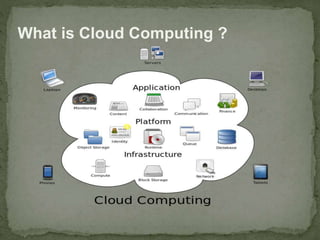
- 3. What is Cloud Computing ?
- 4. What is Cloud Computing ? Cloud computing is a type of computing that relies on sharing computing resources rather than having local servers or personal devices to handle applications .
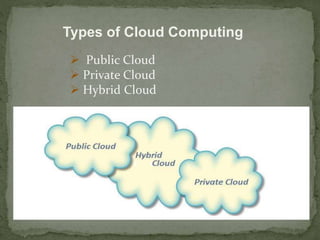
- 5. Types of Cloud Computing ï Public Cloud ï Private Cloud ï Hybrid Cloud
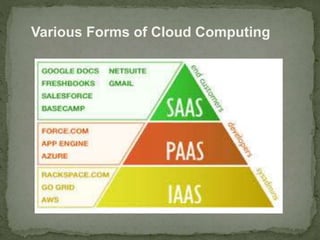
- 6. Various Forms of Cloud Computing ï Cloud Computing is some kind of hosted service Cloud Computing models down into : ï Infrastructure as a Service ï Platform as a Service ï Software as a Service
- 7. Various Forms of Cloud Computing
- 8. Benefits of Cloud Computing ï Cost (Pay as You Go) ïMulti-tenancy ïAccessibility ïElasticity ïEasily upgraded
- 9. Is my data secure on cloud? Why we need Cloud security? Can others access my confidential data? What if an hacker brings down my app hosted on cloud?
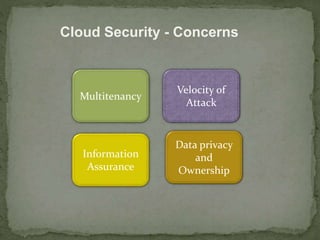
- 10. Cloud Security - Concerns Multitenancy Velocity of Attack Information Assurance Data privacy and Ownership
- 11. Security Concern - Multitenancy ïķ Multitenancy is a key security concern in cloud o For Cloud Clients ï Co-location of multiple VMs in single server and sharing the same resources increases the attack surface o For CSPs ï Enforcing uniform security controls and measures is difficult ïķ Mutual client isolation is key measure against multitenancy - related concerns
- 12. Security Concern â Velocity of Attack ïķ Security threats amplify and spread quickly in a Cloud â Known as âVelocity â of â Attackâ (VOA) factor ï Cloud infrastructure is comparatively larger ï Similarity in the platforms/components employed by a CSP increases the speed at which an attack can spread ïķ Effects of high VOA ïPotential loss due to an attack is comparatively higher ïIt is comparatively difficult to mitigate the spread of the attack
- 13. Security Concern â Information Assurance and Data Ownership âĒ Information assurance concern s for Cloud user involve ïCIA ïAuthenticity ïAuthorized use âĒ Data ownership concerns for Cloud Clients ïIn Cloud, Data belonging to client is maintained by a CSP who has access to the data but is not the legitimate owner of it ïData should be protected using encryption and access control mechanism
- 14. Security Concern â Data Privacy âĒ Private data may include ï Individual identity of client ï Details of services requested by client ï Proprietary data of client âĒ A CSP needs to ensure that private data of its client is protected from unauthorized user ï A CSP needs to deploy data privacy mechanism, which are compliant with the regional legal regulations
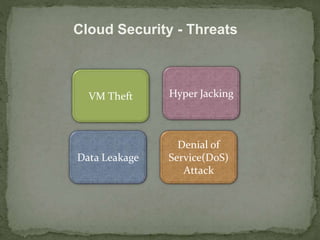
- 15. Cloud Security - Threats VM Theft Hyper Jacking Data Leakage Denial of Service(DoS) Attack
- 16. Security Threat â VM Theft âĒ What is VM Theft ? ï A Vulnerability that enables an attacker to copy or move VM in an unauthorized manner âĒ Result of inadequate controls on VM files allowing unauthorized copy or move operations
- 17. Security Threat â Hyper Jacking âĒ What is Hyper Jacking ? ïIt enables an attacker to install a rogue hypervisor or Virtual Machine Monitor that can take control of the underlying server resources. âĒ An attacker can run unauthorized application on a guest OS without the OS realizing it âĒ An attacker could control the interaction between the VMs and underlying servers âĒ Regular security measures are ineffective against hyper jacking
- 18. Security Threat â Data Leakage âĒ Confidential data stored on third party Cloud is Potentially vulnerable to unauthorized access or manipulation ïAttacks on service providerâs control system( for example password lists) could make all the client sâ data vulnerable âĒ Side Channel Attacks (SCA) can be used for data leakage in Cloud ïAn SCA extracts information by monitoring indirect actives; for example cache data
- 19. Security Threat â Denial of Service Attacks âĒ What is DoS attack? ïIt is an attempt to prevent legitimate user from accessing a resource or service âĒ Dos attack might affect software application and network component âĒ DoS involves ï Exhausting resources ïExploiting weakness in communication protocols
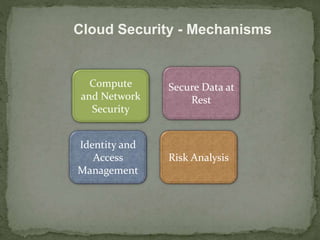
- 20. Cloud Security - Mechanisms Compute and Network Security Secure Data at Rest Identity and Access Management Risk Analysis
- 21. Security at Compute Level âĒ Securing a compute system includes ï Securing physical server ï Securing hypervisor ïSecurity at guest OS level ï§ Guest OS Hardening ï Security at application level
- 22. Securing Data-at -Rest âĒ Data-at-rest ï Data which is not being transferred over a network âĒ Encryption of Data-at-rest ï provides confidentiality ïProvides integrity services âĒ Full disk encryption is a key method to encrypt data-at-rest residing on a disk
- 23. Identity Management (IM) in Cloud âĒ One-time password ï Every new access request requires new password ï A measure against âpassword compromisesâ âĒ Federated Identity Management is provided as a service on cloud ïIn it user identities across different organization can be managed together to enable collaboration on Cloud
- 24. Risk Analysis âĒ Risk refers to the effect of uncertainty on business objectives âĒRisk management is a coordinated activity that direct and control an organization Risk Assessment âĒ Aim to identify potential risks while operating in a Cloud environment ïShould be performed before moving to cloud ïUsed to determine the actual scope for Cloud adoption