More Related Content Viewers also liked (7)
Internet of Things - Future & Opportunities * ž¦█ī┘垬ž▒┘垬 ž¦ž┤█īž¦žĪ - ┘üž▒žĄž¬┘枦█ī ┘Š█īž┤ ž▒┘ł Internet of Things - Future & Opportunities * ž¦█ī┘垬ž▒┘垬 ž¦ž┤█īž¦žĪ - ┘üž▒žĄž¬┘枦█ī ┘Š█īž┤ ž▒┘ł
Masoud Zamani ╠²
Internet of Things - Future & Opportunities
ž¦█ī┘垬ž▒┘垬 ž¦ž┤█īž¦žĪ ž©┘ć ž┤ž©┌®┘ćŌĆīž¦█ī ž¦ž▓ ž¦ž¼ž│ž¦┘ģ (ž¦ž┤█īž¦žĪ) ┘ü█īž▓█ī┌®█ī ž¦žĘ┘䞦┘é ┘ģ█īŌĆīž┤┘łž» ┌®┘ć ž©┘ć ┌®┘ģ┌® ┘éžĘž╣ž¦ž¬ ž¦┘ä┌®ž¬ž▒┘ł┘å█ī┌®█īžī ž│┘åž│┘łž▒┘枦 ┘ł ┘åž▒┘ģŌĆīž¦┘üž▓ž¦ž▒┘枦█ī ž»ž▒┘ł┘å ž«┘łž»ž┤ž¦┘åžī ž©ž¦ ┌»ž▒ž»žó┘łž▒█ī ┘ł ž¬žŁ┘ä█ī┘ä ž»ž¦ž»┘ćŌĆī┘枦█ī ┘ģž«ž¬┘ä┘üžī ┘ģ█īŌĆīž¬┘łž¦┘å┘åž» ž¦ž▒ž▓ž┤█ī ┘üž▒ž¦ž¬ž▒ ž¦ž▓ ┌®ž¦ž▒ž©ž▒█ī ┘ģž╣┘ģ┘ł┘ä ž«┘łž» ž▒ž¦ ž«┘ä┘é ┌®┘å┘åž». ž¦█ī┘å ž¦ž▒ž¦ž”┘ć ž¬┘䞦ž┤ ž»ž¦ž▒ž» ž¬ž¦ ž©ž¦ žóž┤┘垦ž│ž¦ž▓█ī ┘ģž«ž¦žĘž©ž¦┘å ž©ž¦ ž¦█ī┘垬ž▒┘垬 ž¦ž┤█īž¦žĪ ž▒┘ł┘åž»┘枦 ┘ł ┘üž▒žĄž¬ŌĆī┘枦█ī žóž¬█ī ž©ž¦ž▓ž¦ž▒ ž¦█ī┘å žŁ┘łž▓┘ć ž▒ž¦ ┘ģž┤ž«žĄ ž│ž¦ž▓ž».
-----
Videos:
Part 1: http://www.aparat.com/v/gGqhj
Part 2: http://www.aparat.com/v/EGe0f
Part 3: http://www.aparat.com/v/gAF0R
Similar to Cloud Computing (20) Presentation research method Presentation research method
amirhosseinshahed ╠²
Cloud Computing is a new concept that refers to a pool of virtual computer resources. The dynamic and scalable development of the Internet, which is often presented as a service, has made it a very interesting and significant topic.
Cloud Computing and Cloud Services Cloud Computing and Cloud Services
Saeid Bostandoust ╠²
What is Cloud Computing and Cloud Services?
What is Cloud Deployment Models?
What is IaaS, PaaS and SaaS?
Cloud Software and Cloud Providers
Cloud Computing Challenges
Cloud Encryption Mechanisms
Cloud Computing vs Server Virtualization
Cloud Computing Revenue
IPAM_IP address management_Ed: march2017 IPAM_IP address management_Ed: march2017
ali torabi ╠²
IPAM in persian language -IPAM enables you
to centrally manage DHCP and DNS servers.
whith this service You can use IP address tracking to search the IPAM database on the basis of IP address, MAC address, computer name, or user name.
┘ģ┘üž¦┘ć█ī┘ģ ž¦┘ł┘ä█ī┘ć ž»ž¦┌®ž▒ ┘ģ┘üž¦┘ć█ī┘ģ ž¦┘ł┘ä█ī┘ć ž»ž¦┌®ž▒
Ali Rasoulian ╠²
┘ł█ī┌ś┌»█īŌĆī┘枦█ī ž»ž¦┌®ž▒ ┌®┘ć ┘ģ█īž¬┘łž¦┘åž» ┘üž¦žĄ┘ä┘ć ž©█ī┘å ┘å┘łž┤ž¬┘å ž©ž▒┘垦┘ģ┘ć ž¬ž¦ ┘䞣žĖ┘ć ┘éž▒ž¦ž▒┌»█īž▒█ī ž©ž▒┘垦┘ģ┘ć ž»ž▒ ┘ģžŁ█īžĘ ž╣┘ģ┘ä█īž¦ž¬█ī ž▒ž¦ ž©┘ć ┘ģ█īž▓ž¦┘å ┘鞦ž©┘ä ž¬┘łž¼┘ć█ī ┌®ž¦┘ćž┤ ž»┘ćž» ┘ł ┘鞦ž©┘ä█īž¬ ž¬žŁ┘ł█ī┘ä ž│ž▒█īž╣ŌĆīž¬ž▒ ┘åž▒┘ģ ž¦┘üž▓ž¦ž▒ ž▒ž¦ ž©ž│█īž¦ž▒ ž¦┘üž▓ž¦█īž┤ ž»┘ćž».
ž│ž▒┘üžĄ┘ä ┘ģž©ž¦žŁž½:
- ┘ģž╣ž▒┘ü█ī ┘ģ┘ü┘ć┘ł┘ģ Container ┘ł Containerization
- ┘ģž╣ž▒┘ü█ī Docker - ┘ģž▓ž¦█īž¦ ┘ł ┘ģž╣ž¦█īž© Docker
- ┌垦┘äž┤ ┘枦 ┘ł ┘üž▒žĄž¬ ┘枦█ī ž¦ž│ž¬┘üž¦ž»┘ć ž¦ž▓ Docker
- ┘ģž╣ž▒┘ü█ī ž¦┘ł┘ä█ī┘ć ┘ģ┘ü┘ć┘ł┘ģ CI/CD
ž¦ž▒ž¦ž”┘ć┘ö DLP ž¦ž▒ž¦ž”┘ć┘ö DLP
ž¼ž┤┘å┘łž¦ž▒┘ć┘ö ž▒┘łž▓ žóž▓ž¦ž»█ī ┘åž▒┘ģŌĆīž¦┘üž▓ž¦ž▒ ž¬┘ćž▒ž¦┘å ╠²
ž¼ž¦ž©ž¼ž¦█ī█ī ž║█īž▒ ┘鞦┘å┘ł┘å█ī ž»ž¦ž»┘ć ┘枦 (┘åž┤ž¬ ž¦žĘ┘䞦ž╣ž¦ž¬ ) ž¬┘ćž»█īž»█ī ž¼ž»█ī ž©ž▒ž¦█ī ž│ž¦ž▓┘ģž¦┘å┘枦 ž¦ž│ž¬ . ┘ģžĘž¦┘äž╣┘ć ž¦ž«█īž▒ ž¦ž▓ 350ž┤ž▒┌®ž¬ ┘åž┤ž¦┘å ┘ģ█ī ž»┘ćž» ┌®┘ć ž©žĘ┘łž▒ ┘ģž¬┘łž│žĘ ┘ćž▓█ī┘å┘ć ┌®┘ä ž¦ž«┘䞦┘ä ž»ž¦ž»┘ć ┘枦 ž»ž▒ ž¦┘ģž▒█ī┌®ž¦ ž©ž▒ž¦ž©ž▒ 8/3 ┘ģ█ī┘ä█ī┘ł┘å ž»┘䞦ž▒ ž¦ž│ž¬ . ž©ž▒ž¦█ī ž¼┘ä┘ł┌»█īž▒█ī ž¦ž▓ ž¦█ī┘å ž¬┘ćž»█īž» žī ž┤ž▒┌®ž¬ŌĆī┘枦 ┘ģ┌®ž¦┘å█īž│┘ģ ┘ģžŁ█īžĘ ž¦┘ģ┘å█īž¬█ī ž«┘łž» ž▒ž¦ ┘ģž¦┘å┘åž» ┘üž¦█īž▒┘łž¦┘ä ž▒ž¦ ž©┘ć ┘ģ┘åžĖ┘łž▒ ž¼┘ä┘ł┌»█īž▒█ī ž¦ž▓ ž¼ž▒█īž¦┘å ┘垦ž«┘łž¦ž│ž¬┘ć ž»ž¦ž»┘ć ┘枦 ┌»ž│ž¬ž▒ž┤ ž»ž¦ž»┘ć ž¦┘åž»
Javan Cloud Security 950526 (oCCc63) Javan Cloud Security 950526 (oCCc63)
Morteza Javan ╠²
ž¦ž▒ž¦█ī┘ć ž¦┘ģ┘å█īž¬ ž»ž▒ ž▒ž¦█īž¦┘åž┤ ž¦ž©ž▒█ī ┘ł ┌®ž¦ž▒┌»ž¦┘ć ž╣┘ģ┘ä█ī ┘ģž»█īž▒█īž¬ ž▒█īž│┌® ž│ž▒┘ł█īž│ ┘枦█ī ž¦ž©ž▒█īžī ž¼┘äž│┘ć 63 ž¼ž¦┘ģž╣┘ć žóž▓ž¦ž» ž▒ž¦█īž¦┘åž┤ ž¦ž©ž▒█ī ž¦█īž▒ž¦┘å
Pdn tech-cloud management-softwares-ver2.0.1 Pdn tech-cloud management-softwares-ver2.0.1
pdnsoftco ╠²
┘ģž┤ž«žĄ┘ćŌĆī█ī ž¦žĄ┘ä█ī ž▒ž¦█īž¦┘åž┤ ž¦ž©ž▒█īžī ┘üž▒ž¦┘ć┘ģ ž│ž¦ž«ž¬┘å ž▓█īž▒ž│ž¦ž«ž¬ IT ┘ł ┌®ž¦ž▒ž©ž▒ž»┘枦█ī žó┘å ž©┘ć ž┤┌®┘ä █ī┌® ž│ž▒┘ł█īž│ ž©┘ć žĘž▒█ī┘é█ī ž¬┘łž│ž╣┘ćŌĆī┘Šž░█īž▒ ┘ģ█īŌĆīž©ž¦ž┤ž».ž¬ž¦┌®┘å┘ł┘å ┘åž▒┘ģŌĆīž¦┘üž▓ž¦ž▒┘枦█ī█ī ž©ž▒ž¦█ī ž¦█ī┘å ┘ģ┘åžĖ┘łž▒ žĘž▒ž¦žŁ█ī ┘ł ┘Š█īž¦ž»┘ćŌĆīž│ž¦ž▓█ī ž┤ž»┘ćŌĆīž¦┘åž». ž»ž▒ ž¦█ī┘å ┌»ž▓ž¦ž▒ž┤ ┘鞥ž» ž»ž¦ž▒█ī┘ģ ž│┘ć ┘ģ┘łž▒ž» ž¦ž▓ ž¦█ī┘å ┘åž▒┘ģŌĆīž¦┘üž▓ž¦ž▒┘枦 ž▒ž¦ ┘ģž╣ž▒┘ü█ī ┌®┘å█ī┘ģ ┘ł ┘ģžż┘ä┘ü┘ćŌĆī┘枦█ī ž│ž¦ž▓┘åž»┘ć ┘ł ┘ģž╣┘ģž¦ž▒█ī žó┘åŌĆī┘枦 ž▒ž¦ ┘ģ┘łž▒ž» ž©ž▒ž▒ž│█ī ┘éž▒ž¦ž▒ ž»┘ć█ī┘ģ.
More from Mohammad Amin Amjadi (17)
Image Cryptography and Steganography Image Cryptography and Steganography
Mohammad Amin Amjadi ╠²
1) EIRDH-P combines public key cryptography and steganography by encrypting images and embedding secret messages within the encrypted images.
2) It involves an Image Provider who encrypts a cover image using public key encryption. A Data Hider then embeds a secret message within the encrypted image.
3) The receiver decrypts the stego-image to extract the secret message and recover the original cover image using their private key.
memetic algorithm memetic algorithm
Mohammad Amin Amjadi ╠²
The document discusses using genetic algorithms and memetic algorithms to optimize wireless sensor network design parameters for energy efficiency while meeting application requirements. It proposes encoding sensor network characteristics and applying genetic operators to minimize energy use and maximize sensing uniformity over time. A memetic algorithm hybridizes this genetic algorithm with local searches that change sensor operating modes based on battery thresholds to further improve energy conservation. Evaluation shows the memetic algorithm enhances network lifetime compared to the genetic algorithm alone.
rivercode.PDF rivercode.PDF
Mohammad Amin Amjadi ╠²
This document contains assembly code macros and variables for a game involving planes, ships, and helicopters on different levels. It defines macros for drawing graphics, handling input, random number generation, and dynamic movement of objects. Variables track positions, speeds, and statuses of objects and the level parameters. The code implements game logic and object behavior through calls to the macros.
8. 8
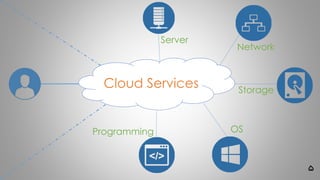
Cloud
ŌĆ½┘ģžŁž¦ž│ž©ž¦ž¬█īŌĆ¼ ŌĆ½┘łžĖž¦█ī┘üŌĆ¼ ŌĆ½ž¦┘åž¼ž¦┘ģŌĆ¼
ŌĆ½┘枦ŌĆ¼ ŌĆ½ž©ž▒┘垦┘ģ┘ćŌĆ¼ ŌĆ½ž¦ž¼ž▒ž¦█īŌĆ¼
ŌĆ½ž¦žĘž¦┘äž╣ž¦ž¬ŌĆ¼ ŌĆ½ž│ž¦ž▓█īŌĆ¼ ŌĆ½ž░ž«█īž▒┘ćŌĆ¼
Services
ŌĆ½ž¦ž│┘Ćž¬┘Ć┘ü┘Ć┘Ć┘Ćž¦ž»┘ćŌĆ¼
ŌĆ½ž©ž¦ž¦┘䞬ž▒ŌĆ¼ ŌĆ½ž│ž▒ž╣ž¬█īŌĆ¼ ŌĆ½ž©ž¦ŌĆ¼
ŌĆ½ž│█īž│ž¬┘ģŌĆ¼ ŌĆ½ž▒┘ł█īŌĆ¼ ŌĆ½┘åžĄž©ŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½┘å█īž¦ž▓ŌĆ¼ ŌĆ½ž©ž»┘ł┘åŌĆ¼ žī ŌĆ½žŁ┘ģ┘äŌĆ¼ ŌĆ½┘鞦ž©┘ä█īž¬ŌĆ¼
ŌĆ½┘éž»ž▒ž¬┘ģ┘åž»ŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼ ŌĆ½ž│ž«ž¬ŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½┘å█īž¦ž▓ŌĆ¼ ŌĆ½ž╣ž»┘ģŌĆ¼
ŌĆ½žŁ┘ģ┘äŌĆ¼ ŌĆ½┘鞦ž©┘ä█īž¬ŌĆ¼
14. 14
Cloud
Computing
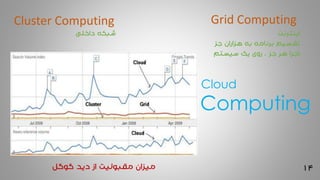
Cluster Computing Grid Computing
ŌĆ½ž»ž¦ž«┘ä█īŌĆ¼ ŌĆ½ž┤ž©┌®┘ćŌĆ¼ ŌĆ½ž¦█ī┘垬ž▒┘垬ŌĆ¼
ŌĆ½ž¼ž▓ŌĆ¼ ŌĆ½┘ćž▓ž¦ž▒ž¦┘åŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½ž©ž▒┘垦┘ģ┘ćŌĆ¼ ŌĆ½ž¬┘éž│█ī┘ģŌĆ¼
ŌĆ½ž│█īž│ž¬┘ģŌĆ¼ ŌĆ½█ī┌®ŌĆ¼ ŌĆ½ž▒┘ł█īŌĆ¼ žī ŌĆ½ž¼ž▓ŌĆ¼ ŌĆ½┘ćž▒ŌĆ¼ ŌĆ½ž¦ž¼ž▒ž¦ŌĆ¼
ŌĆ½┌»┘ł┌»┘äŌĆ¼ ŌĆ½ž»█īž»ŌĆ¼ ŌĆ½ž¦ž▓ŌĆ¼ ŌĆ½┘ģ┘éž©┘ł┘ä█īž¬ŌĆ¼ ŌĆ½┘ģ█īž▓ž¦┘åŌĆ¼
15. 15
ŌĆ½┘ć┘Ćž¦ŌĆ¼ ŌĆ½┘ł█ī┘Ć┘Ć┘Ć┌ś┌»┘Ć┘Ć█īŌĆ¼
oŌĆ½ž│┘üž¦ž▒ž┤ŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½ž©┘垦ŌĆ¼(ŌĆ½ž│ž▒┘ł█īž│ŌĆ¼ ŌĆ½ž│┘ä┘üŌĆ¼)
ŌĆ½┌®ž¦ž▒ž©ž▒ŌĆ¼ ŌĆ½┘å█īž¦ž▓ŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½ž¬┘łž¼┘ćŌĆ¼ ŌĆ½ž©ž¦ŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼ ŌĆ½ž│ž«ž¬ŌĆ¼ ŌĆ½┘ģž┤ž«žĄž¦ž¬ŌĆ¼
oŌĆ½ž┤ž©┌®┘ćŌĆ¼ ŌĆ½┘üž▒ž¦┌»█īž▒ŌĆ¼ ŌĆ½ž»ž│ž¬ž▒ž│█īŌĆ¼
ŌĆ½┘Š┘䞬┘üž▒┘ģŌĆ¼ ŌĆ½ž¦ž▓ŌĆ¼ ŌĆ½┘ģž│ž¬┘é┘äŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž»ž│ž¬ž▒ž│ŌĆ¼ ŌĆ½ž»ž▒ŌĆ¼ ŌĆ½ž¼ž¦ŌĆ¼ ŌĆ½┘ć┘ģ┘ćŌĆ¼
oŌĆ½ž│ž¦ž▓█īŌĆ¼ ŌĆ½┘ć┘ģ┌»ž¦┘ģŌĆ¼
ŌĆ½┘ćž│ž¬┘åž»ŌĆ¼ ŌĆ½ž©ž▒┘łž▓ŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½█ī┌®ž│ž¦┘åŌĆ¼ ŌĆ½ž¼ž¦ŌĆ¼ ŌĆ½┘ć┘ģ┘ćŌĆ¼ ŌĆ½ž¦žĘž¦┘äž╣ž¦ž¬ŌĆ¼
oŌĆ½ž»ž▒ž¼ž¦ŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž│ž▒█īž╣ŌĆ¼ ŌĆ½┘Šž░█īž▒█īŌĆ¼ ŌĆ½ž¦┘åž╣žĘž¦┘üŌĆ¼(ŌĆ½┘ģ┘é█īž¦ž│ŌĆ¼)
ŌĆ½ž¦ž│ž¬ŌĆ¼ ŌĆ½┘Šž░█īž▒ŌĆ¼ ŌĆ½ž¦┘ģ┌®ž¦┘åŌĆ¼ ŌĆ½┘䞣žĖ┘ćŌĆ¼ ŌĆ½┘ćž▒ŌĆ¼ ŌĆ½ž»ž▒ŌĆ¼ ŌĆ½ž│█īž│ž¬┘ģŌĆ¼ ŌĆ½┘Š█ī┌®ž▒ž©┘åž»█īŌĆ¼
oŌĆ½ž│█īž│ž¬┘ģŌĆ¼ ŌĆ½ž¦ž¬┘ł┘ģž¦ž¬█ī┌®ŌĆ¼ ŌĆ½ž│ž¦ž▓█īŌĆ¼ ŌĆ½ž©┘ć█ī┘å┘ćŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½┌®┘垬ž▒┘äŌĆ¼
ŌĆ½ž¦ž│ž¬ŌĆ¼ ŌĆ½┘ģž┤ž«žĄŌĆ¼ ŌĆ½┘ģ┘垦ž©ž╣ŌĆ¼ ŌĆ½ž¦ž▓ŌĆ¼ ŌĆ½ž¦ž│ž¬┘üž¦ž»┘ćŌĆ¼ ŌĆ½┘ģ█īž▓ž¦┘åŌĆ¼
oŌĆ½ž¦ž│ž¬┘üž¦ž»┘ćŌĆ¼ ŌĆ½┘ģ█īž▓ž¦┘åŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž«ž»┘ģž¦ž¬ŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½ž©ž│ž¬┘ćŌĆ¼ ŌĆ½┘Šž▒ž»ž¦ž«ž¬ŌĆ¼
ŌĆ½┘üž▒┌®ž¦┘åž│ŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½┘Šž▒ž»ž¦ž▓┘åž»┘ćŌĆ¼ ŌĆ½ž¬ž╣ž»ž¦ž»ŌĆ¼ žī ŌĆ½ž¼ž¦┘åž©█īŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž¦žĄ┘ä█īŌĆ¼ ŌĆ½žŁž¦┘üžĖ┘ćŌĆ¼ ŌĆ½┘ģ█īž▓ž¦┘åŌĆ¼ ŌĆ½┘ć┘ģ┌å┘ł┘åŌĆ¼
oŌĆ½┘éž»ž▒ž¬┘ģ┘åž»ŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼ ŌĆ½ž│ž«ž¬ŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½┘å█īž¦ž▓ŌĆ¼ ŌĆ½ž╣ž»┘ģŌĆ¼
ŌĆ½ž¦ž│ž¬ŌĆ¼ ŌĆ½┘ģ┘ć┘ģŌĆ¼ ŌĆ½┘ģž▒┘łž▒┌»ž▒ŌĆ¼ ŌĆ½┘ģ┘垦ž│ž©ŌĆ¼ ŌĆ½ž¦ž¼ž▒ž¦ŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž┤ž©┌®┘ćŌĆ¼ ŌĆ½ž©█īž┤ž¬ž▒ŌĆ¼
oŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼ ŌĆ½┘åž▒┘ģŌĆ¼ ŌĆ½žóž│ž¦┘åŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž│ž▒█īž╣ŌĆ¼ ŌĆ½ž▒ž│ž¦┘å█īŌĆ¼ ŌĆ½ž©ž▒┘łž▓ŌĆ¼
ŌĆ½ž«ž¦žĄ█īŌĆ¼ ŌĆ½┌®ž¦ž▒ŌĆ¼ ŌĆ½ž¦┘åž¼ž¦┘ģŌĆ¼ ŌĆ½█īž¦ŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž▓┘ģž¦┘åŌĆ¼ ŌĆ½žĄž▒┘üŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½┘å█īž¦ž▓ŌĆ¼ ŌĆ½ž©ž»┘ł┘åŌĆ¼
Cloud
Services
16. 16
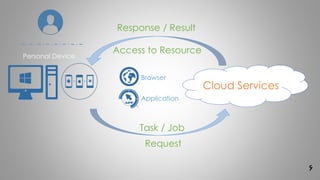
ŌĆ½┘ć┘Ć┘Ć┘Ćž¦ŌĆ¼ ŌĆ½┘ä┘Ć┘Ć┘Ć┘Ćž¦█ī┘Ć┘Ć┘Ć┘Ć┘Ć┘ćŌĆ¼
oŌĆ½┌®ž¦ž▒ž©ž▒ž»█īŌĆ¼ ŌĆ½ž¦┘ä█ī┘ćŌĆ¼(Client)
Mobile , Laptop , Pc
oŌĆ½┘åž▒┘ģŌĆ¼ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼(Application)
Google Apps , Microsoft Apps
oŌĆ½ž│┌®┘łŌĆ¼(Platform)
.Net , Java
oŌĆ½ž│ž¦ž«ž¬ŌĆ¼ ŌĆ½ž▓█īž▒ŌĆ¼(Infrastructure)
ŌĆ½┘ģžŁž¦ž│ž©ž¦ž¬ŌĆ¼ žī ŌĆ½ž│ž¦ž▓█īŌĆ¼ ŌĆ½ž░ž«█īž▒┘ćŌĆ¼ žī ŌĆ½ž¦ž▒ž¬ž©ž¦žĘž¦ž¬ŌĆ¼
oŌĆ½ž│ž▒┘łž▒ŌĆ¼(Server)
ŌĆ½ž¦ž©ž▒ŌĆ¼ ŌĆ½┘ü█īž▓█ī┌®█īŌĆ¼ ŌĆ½ž©ž«ž┤ŌĆ¼:ŌĆ½ž¦ž©ž▒█īŌĆ¼ ŌĆ½ž▒ž¦█īž¦┘åž┤ŌĆ¼ ŌĆ½ž«ž»┘ģž¦ž¬ŌĆ¼ ŌĆ½┘枦█īŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼ ŌĆ½┘åž▒┘ģŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒┘枦ŌĆ¼ ŌĆ½ž│ž«ž¬ŌĆ¼
Cloud
Services
17. 17
ŌĆ½ž¦ž▒ž¦ž”┘Ć┘ćŌĆ¼ ŌĆ½ž¦ž┤┘Ć┌®┘Ćž¦┘äŌĆ¼
oŌĆ½ž│ž▒┘ł█īž│ŌĆ¼ ŌĆ½ž╣┘å┘łž¦┘åŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½ž¦ž©ž▒█īŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼ ŌĆ½┘åž▒┘ģŌĆ¼(SaaS)
ŌĆ½ž»ž¦ž▒ž»ŌĆ¼ ŌĆ½ž»ž│ž¬ž▒ž│█īŌĆ¼ ŌĆ½┌®ž¦ž▒ž©ž▒█īŌĆ¼ ŌĆ½ž©ž▒┘垦┘ģ┘ćŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½┌®ž¦ž▒ž©ž▒ŌĆ¼
ŌĆ½ž¦ŌĆ¼ŌĆ½┘ģžŁž»┘łž»ŌĆ¼ ŌĆ½┘Š█ī┌®ž▒ž©┘åž»█īŌĆ¼ ŌĆ½┘ģ┌®ž¦┘åŌĆ¼
oŌĆ½ž│ž▒┘ł█īž│ŌĆ¼ ŌĆ½ž╣┘å┘łž¦┘åŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½ž¦ž©ž▒█īŌĆ¼ ŌĆ½ž©ž│ž¬ž▒ŌĆ¼(PaaS)
ŌĆ½ž»┘ćž»ŌĆ¼ ŌĆ½┘éž▒ž¦ž▒ŌĆ¼ ŌĆ½ž¦ž©ž▒ŌĆ¼ ŌĆ½ž▒┘ł█īŌĆ¼ ŌĆ½ž▒ž¦ŌĆ¼ ŌĆ½ž«┘łž»ŌĆ¼ ŌĆ½ž©ž▒┘垦┘ģ┘ćŌĆ¼ ŌĆ½ž¬┘łž¦┘åž»ŌĆ¼ ŌĆ½┘ģ█īŌĆ¼ ŌĆ½┌®ž¦ž▒ž©ž▒ŌĆ¼
ŌĆ½ž©ž▒┘垦┘ģ┘ćŌĆ¼ ŌĆ½┘枦ž│ž¬ŌĆ¼ ŌĆ½┘ģ█īž▓ž©ž¦┘å█īŌĆ¼ ŌĆ½┘ģžŁ█īžĘŌĆ¼ ŌĆ½┘Š█ī┌®ž▒ž©┘åž»█īŌĆ¼ ŌĆ½ž¦┘ģ┌®ž¦┘åŌĆ¼
oŌĆ½ž│ž▒┘ł█īž│ŌĆ¼ ŌĆ½ž╣┘å┘łž¦┘åŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½ž¦ž©ž▒█īŌĆ¼ ŌĆ½ž│ž¦ž«ž¬ŌĆ¼ ŌĆ½ž▓█īž▒ŌĆ¼(IaaS)
ŌĆ½┘枦ŌĆ¼ ŌĆ½ž©ž▒┘垦┘ģ┘ćŌĆ¼ žī ŌĆ½ž│ž¦ž▓█īŌĆ¼ ŌĆ½ž░ž«█īž▒┘ćŌĆ¼ ŌĆ½┘üžČž¦█īŌĆ¼ žī ŌĆ½ž╣ž¦┘ģ┘äŌĆ¼ ŌĆ½ž│█īž│ž¬┘ģŌĆ¼ ŌĆ½┘ģž»█īž▒█īž¬ŌĆ¼
Cloud
Services
Software as a Service
Platform as a Service
Infrastructure as a Service
18. 18
ŌĆ½┘ć┘Ć┘Ć┘Ćž¦ŌĆ¼ ŌĆ½┘ä┘Ć┘Ć┘Ć┘Ćž¦█ī┘Ć┘Ć┘Ć┘Ć┘Ć┘ćŌĆ¼
oŌĆ½┌®ž¦ž▒ž©ž▒ž»█īŌĆ¼ ŌĆ½ž¦┘ä█ī┘ćŌĆ¼(Client)
Mobile , Laptop , Pc
oŌĆ½┘åž▒┘ģŌĆ¼ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼(Software: )SaaS
Google Apps , Microsoft Apps
oŌĆ½ž│┌®┘łŌĆ¼(Platform: )PaaS
.Net , Java , Python
oŌĆ½ž│ž¦ž«ž¬ŌĆ¼ ŌĆ½ž▓█īž▒ŌĆ¼(Infrastructure: )IaaS
ŌĆ½┘ģžŁž¦ž│ž©ž¦ž¬ŌĆ¼ žī ŌĆ½ž│ž¦ž▓█īŌĆ¼ ŌĆ½ž░ž«█īž▒┘ćŌĆ¼ žī ŌĆ½ž¦ž▒ž¬ž©ž¦žĘž¦ž¬ŌĆ¼
oŌĆ½ž│ž▒┘łž▒ŌĆ¼(Server)
ŌĆ½ž¦ž©ž▒ŌĆ¼ ŌĆ½┘ü█īž▓█ī┌®█īŌĆ¼ ŌĆ½ž©ž«ž┤ŌĆ¼:ŌĆ½ž¦ž©ž▒█īŌĆ¼ ŌĆ½ž▒ž¦█īž¦┘åž┤ŌĆ¼ ŌĆ½ž«ž»┘ģž¦ž¬ŌĆ¼ ŌĆ½┘枦█īŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼ ŌĆ½┘åž▒┘ģŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒┘枦ŌĆ¼ ŌĆ½ž│ž«ž¬ŌĆ¼
Cloud
Services
ŌĆ½ž│žĘžŁŌĆ¼
ŌĆ½ž¬┘Ć┘ĆžČ┘Ć┘Ć┘Ć┘ģ┘Ć┘Ć█ī┘Ć┘Ć┘Ć┘åŌĆ¼
ŌĆ½ž¦ž▒ž¦ž”┘Ć┘ćŌĆ¼ ŌĆ½ž¦ž┤┘Ć┌®┘Ćž¦┘äŌĆ¼
20. 20
ŌĆ½ž¦ž┤┌®ž¦┘äŌĆ¼
ŌĆ½ž│┘Ćž¦ž▓█īŌĆ¼ ŌĆ½žó┘ģ┘Ćž¦ž»┘ćŌĆ¼
oŌĆ½ž«žĄ┘łžĄ█īŌĆ¼ ŌĆ½ž¦ž©ž▒ŌĆ¼(Private Cloud)
ŌĆ½┌®┘åž»ŌĆ¼ ŌĆ½┘ģ█īŌĆ¼ ŌĆ½┌®ž¦ž▒ŌĆ¼ ŌĆ½ž│ž¦ž▓┘ģž¦┘åŌĆ¼ ŌĆ½█ī┌®ŌĆ¼ ŌĆ½ž©ž▒ž¦█īŌĆ¼ ŌĆ½ž¦ž©ž▒█īŌĆ¼ ŌĆ½ž▓█īž▒ž│ž¦ž«ž¬ŌĆ¼
oŌĆ½ž¦ž©ž▒ŌĆ¼ŌĆ½┌»ž▒┘ł┘ć█īŌĆ¼(Commiunity Cloud)
ŌĆ½ž©ž▒ž¦█īŌĆ¼ ŌĆ½ž¦ž©ž▒█īŌĆ¼ ŌĆ½ž▓█īž▒ž│ž¦ž«ž¬ŌĆ¼ŌĆ½ž│ž¦ž▓┘ģž¦┘åŌĆ¼ ŌĆ½┌å┘åž»█ī┘åŌĆ¼ŌĆ½┌®┘åž»ŌĆ¼ ŌĆ½┘ģ█īŌĆ¼ ŌĆ½┌®ž¦ž▒ŌĆ¼
oŌĆ½ž¦ž©ž▒ŌĆ¼ŌĆ½ž╣┘ģ┘ł┘ģ█īŌĆ¼(Public Cloud)
ŌĆ½ž¦ž©ž▒█īŌĆ¼ ŌĆ½ž▓█īž▒ž│ž¦ž«ž¬ŌĆ¼ŌĆ½ž¦ž│ž¬ŌĆ¼ ŌĆ½ž╣┘ģ┘ł┘ģŌĆ¼ ŌĆ½ž¦ž«ž¬█īž¦ž▒ŌĆ¼ ŌĆ½ž»ž▒ŌĆ¼
oŌĆ½ž¦ž©ž▒ŌĆ¼ŌĆ½žó┘ģ█īž«ž¬┘ćŌĆ¼(Hybrid Cloud)
ŌĆ½ž¦ž©ž▒ŌĆ¼ ŌĆ½┌å┘åž»ŌĆ¼ ŌĆ½█īž¦ŌĆ¼ ŌĆ½ž»┘łŌĆ¼ ŌĆ½ž¦ž▓ŌĆ¼(ŌĆ½ž╣┘ģ┘ł┘ģ█īŌĆ¼ ŌĆ½█īž¦ŌĆ¼ ŌĆ½┌»ž▒┘ł┘ć█īŌĆ¼ žī ŌĆ½ž«žĄ┘łžĄ█īŌĆ¼)ŌĆ½ž┤ž»┘ćŌĆ¼ ŌĆ½ž¬ž┤┌®█ī┘äŌĆ¼
Cloud
Services
22. 22
ŌĆ½┘ģ┘Ć┘Ćž┤┘Ć┘Ć┘Ć┌®┘Ć┘Ć┘ä┘Ćž¦ž¬ŌĆ¼
oŌĆ½ž▓█īž¦ž»ŌĆ¼ ŌĆ½ž┤┌®ž│ž¬ŌĆ¼ ŌĆ½┘å┘鞦žĘŌĆ¼ ŌĆ½ž»ž¦ž▒ž¦█īŌĆ¼
ŌĆ½ž│ž¦┘ģž¦┘å┘ćŌĆ¼Amazonžī18ŌĆ½ž©┘łž»ŌĆ¼ ŌĆ½┘éžĘž╣ŌĆ¼ ŌĆ½┘ģž¬┘łž¦┘ä█īŌĆ¼ ŌĆ½ž│ž¦ž╣ž¬ŌĆ¼
oŌĆ½ž│ž¦┘ģž¦┘å┘ćŌĆ¼ ŌĆ½┘Šž┤ž¬ŌĆ¼ ŌĆ½ž┤ž▒┌®ž¬ŌĆ¼ ŌĆ½┘ģž┤┌®ž¦┘䞬ŌĆ¼
ŌĆ½ž┤ž▒┌®ž¬ŌĆ¼ ŌĆ½┘łž▒ž┤┌®ž│ž¬┌»█īŌĆ¼SteamLoadŌĆ½ž©┘ćŌĆ¼ ŌĆ½┘ćž▒┌»ž▓ŌĆ¼ ŌĆ½ž©ž▒ž«█īŌĆ¼ žī
ŌĆ½┘å┌®ž▒ž»┘åž»ŌĆ¼ ŌĆ½┘Š█īž»ž¦ŌĆ¼ ŌĆ½ž»ž│ž¬ž▒ž│█īŌĆ¼ ŌĆ½ž¦žĘž¦┘äž╣ž¦ž¬ž┤ž¦┘åŌĆ¼
oŌĆ½ž¦┘ģ┘å█īž¬█īŌĆ¼ ŌĆ½žČž╣┘üŌĆ¼
ŌĆ½žŁ┘üž¦žĖž¬█īŌĆ¼ ŌĆ½ž│ž¦┘ģž¦┘å┘ćŌĆ¼ ŌĆ½ž┤┌®ž│ž¬┘åŌĆ¼Gmail
oŌĆ½ž¦┘üž▓ž¦ž▒█īŌĆ¼ ŌĆ½┘åž▒┘ģŌĆ¼ ŌĆ½ž¦█īž▒ž¦ž»ž¦ž¬ŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½┘ģž┤┌®ž¦┘䞬ŌĆ¼
Google DocsŌĆ½ž»█ī┌»ž▒ž¦┘åŌĆ¼ ŌĆ½ž»ž│ž¬ž▒ž│ŌĆ¼ ŌĆ½ž»ž▒ŌĆ¼ ŌĆ½ž¦žĘž¦┘äž╣ž¦ž¬ŌĆ¼ žī
CloudComputing
24. 24
ŌĆ½žó█ī┘Ć┘Ć┘Ć┘Ć┘Ć┘Ć┘Ć┘Ć┘å┘Ć┘Ć┘Ć┘Ć┘Ć┘Ć┘Ć┘Ćž»┘ćŌĆ¼
oŌĆ½ž¼ž»█īž»ŌĆ¼ ŌĆ½žó┌®ž¦ž»┘ģ█ī┌®ŌĆ¼ ŌĆ½ž▒ž┤ž¬┘ćŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž┤ž║┘äŌĆ¼
oŌĆ½┌®ž¦ž▒ž©ž▒ž¦┘åŌĆ¼ ŌĆ½ž▒žČž¦█īž¬ŌĆ¼ ŌĆ½ž¼┘äž©ŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž¦ž╣ž¬┘ģž¦ž»ŌĆ¼ ŌĆ½ž¦┘üž▓ž¦█īž┤ŌĆ¼
oŌĆ½┌®ž¦ž▒ŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½┌®ž│ž©ŌĆ¼ ŌĆ½ž©ž¦ž▓ž¦ž▒ŌĆ¼ ŌĆ½ž¬┘łž│ž╣┘ćŌĆ¼
ŌĆ½┘ć┌®ž▒┘枦ŌĆ¼ ŌĆ½ž»ž│ž¬ŌĆ¼ ŌĆ½ž┤ž»┘åŌĆ¼ ŌĆ½ž©ž│ž¬┘ćŌĆ¼
oŌĆ½ž▒ž¦█ī┌»ž¦┘åŌĆ¼ ŌĆ½┘枦█īŌĆ¼ ŌĆ½ž╣ž¦┘ģ┘äŌĆ¼ ŌĆ½ž│█īž│ž¬┘ģŌĆ¼ ŌĆ½┌®ž¦ž▒┌»█īž▒█īŌĆ¼ ŌĆ½ž©┘ćŌĆ¼
oŌĆ½┌®┘ģŌĆ¼ ŌĆ½ž¦█ī┘垬ž▒┘垬ŌĆ¼ ŌĆ½ž©ž¦ŌĆ¼ ŌĆ½ž¦ž¬žĄž¦┘äŌĆ¼ ŌĆ½ž©ž▒ž¦█īŌĆ¼ ŌĆ½ž▒ž¦┘ć┌®ž¦ž▒┘枦ŌĆ¼ ŌĆ½ž¦ž▒ž¦ž”┘ćŌĆ¼
ŌĆ½žó┘üž¦┘ä█ī┘åŌĆ¼ ŌĆ½┘łŌĆ¼ ŌĆ½ž│ž▒ž╣ž¬ŌĆ¼
oŌĆ½┘éž»ž▒ž¬┘ģ┘åž»ŌĆ¼ ŌĆ½ž¦┘üž▓ž¦ž▒ŌĆ¼ ŌĆ½ž│ž«ž¬ŌĆ¼ ŌĆ½ž©┘ćŌĆ¼ ŌĆ½┘å█īž¦ž▓ŌĆ¼ ŌĆ½ž╣ž»┘ģŌĆ¼
oŌĆ½┘枦ŌĆ¼ ŌĆ½ž┤ž▒┌®ž¬ŌĆ¼ ŌĆ½ž¬┘łž│žĘŌĆ¼ ŌĆ½┘ģž┤ž¬ž▒█īž¦┘åŌĆ¼ ŌĆ½ž¬ž┤┘ł█ī┘éŌĆ¼
CloudComputing