Cloud Security.pptx
- 2. Outline âĒ Introduction âĒ Defining Cloud Security âĒ Why Cloud Security - Top Threats âĒ Cloud Security Ownership Models âĒ Cloud Security Standards âĒ Cloud Security - Services by Cloud Services providers âĒ Managed Cloud Security
- 3. Why Cloud Security ? âĒ More and More Business are moving towards the Cloud âĒ Trust is the most important Concern before adopting cloud. âĒ Maintaining customerâs data security, privacy, and compliance with the related regulations. âĒ Global Cloud Security Market was valued at USD 3.43 billion in 2016 and is projected to reach USD 27.20 billion by 2025, growing at a CAGR of 25.86% from 2017 to 2025.
- 4. Defining Cloud Security âĒ In Cloud Security , basically we see the below scenarios :- ï Security OF the Cloud - Security OF the Cloud being how the cloud providers secure their environment themselves. ï Security IN the Cloud - Security IN the Cloud being those aspects of security that are the responsibility of the cloud consumer securing their own data and applications within the cloud. ï Managed Security Services over Cloud - Security Vendors are offering Security services over Cloud. Since Cloud Security policies and rules can be configured and managed in one place, administration overheads are reduced and IT teams empowered to focus on other areas of the business âĒ In Nutshell, Cloud security or cloud computing security, consists of a set of policies, controls, procedures and technologies that work together to protect cloud-based systems, data and infrastructure. These security measures are configured to protect data, support regulatory compliance and protect customers' privacy as well as setting authentication rules for individual users and devices .
- 5. Cloud Security - Top Threats As per the Research artifacts produced by Cloud Security Alliance (CSA) , the below are the top 12 threats in a Cloud deployment : -
- 6. Cloud Security â Responsibilities
- 7. Cloud Security Standards General IT security standards + Cloud Specific Standards AWS Complies to the following standards and certification bodies
- 8. Security Services provided by Cloud Service Providers
- 9. Cloud Service Providers - Security Services Security Services Infrastructure Security Identity and Access Management Data Protection DDoS Monitoring and Logging
- 10. AWS Infrastructure Security âĒ VPC â Virtual Private Cloud , lets user provision a logically isolated section of the Amazon Web Services (AWS) Cloud . Users have complete control over virtual networking environment, including selection of IP address range, creation of subnets, and configuration of route tables and network gateways âĒ Security groups and Network Access lists built into Amazon VPC provide control access to user instances AWS provides several security capabilities and services to increase privacy and control network access. These include:
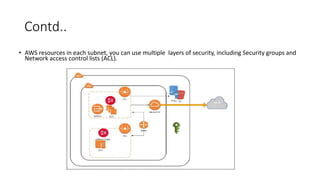
- 11. Contd.. âĒ AWS resources in each subnet, you can use multiple layers of security, including Security groups and Network access control lists (ACL).
- 12. âĒ Identity and access management ensures that only authorized and authenticated users are able to access the cloud resources. For example, AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. It is used to control who is authenticated (signed in) and authorized (has permissions) to use resources. CSPs define principals (that is, users, groups, services, and roles for creating account in Cloud) build out policies aligned with these principals, and implement strong credential management. âĒ Support of MFA (Multi Factor Authentication) Identity and Access Management
- 13. Data Protection and Encryption Data Protection and Encryption refers to the following :- âĒ Data classification âĒ Encryption âĒ Protecting data at rest âĒ Protecting data in transit
- 14. Contd.. âĒ Data classification - Data classification provides a way to categorize organizational data based on levels of sensitivity. For example, public-facing content is available for anyone to access, whereas important content is encrypted and stored in a protected manner that requires authorized access to a key for decrypting the content. ïž Amazon Macie is a security service that uses machine learning to automatically discover, classify, and protect sensitive data in AWS. ïž Macie recognizes sensitive data such as personally identifiable information (PII) or intellectual property. It provides you with dashboards and alerts that give visibility into how this data is being accessed or moved. âĒ Encryption - Encryption is a way of transforming content in a manner that makes it unreadable without a secret key necessary to decrypt the content back into plain text. AWS KMS helps to manage encryption keys and integrates with many AWS services. This service provides durable, secure, and redundant storage for master keys.
- 15. Contd..
- 16. Contd.. âĒ Data at rest represents any data that persists for any duration in the cloud. This includes block storage, object storage, databases, archives, and any other storage medium on which data is persisted. âĒ Amazon S3 is an object storage service that integrates with AWS KMS. âĒ Amazon EBS is a block storage service integrated with AWS KMS. âĒ Amazon Glacier is a secure, durable, and extremely low-cost storage service for data archiving and long-term backup that encrypts data at rest. âĒ Data in transit is any data that gets transmitted from one system to another - When protecting data in transit, selecting secure protocols that implement the latest in cryptography standards such as Transport Layer Security (TLS) is a common best practice.
- 17. AWS Shield and AWS WAF âĒ AWS Shield - It is a managed Distributed Denial of Service (DDoS) protection service that safeguards applications running on AWS. AWS Shield provides always-on detection and automatic inline mitigations that minimize application downtime and latency, so there is no need to engage AWS Support to benefit from DDoS protection. âĒ AWS WAF- It is a web application firewall that helps protect web applications from attacks by allowing you to configure rules that allow, block, or monitor (count) web requests based on conditions that you define. These conditions include IP addresses, HTTP headers, URI strings etc .
- 18. Monitoring and Logging - Cloud Trail and Cloud Watch âĒ Cloud Trail - CloudTrail is enabled on AWS account at the time of creation . When activity occurs in your AWS account, that activity is recorded in a CloudTrail event. ï The AWS API call history produced by CloudTrail enables security analysis, resource change tracking, and compliance auditing. The recorded information includes the identity of the API caller, the time of the API call, the source IP address of the API caller, the request parameters, and the response elements returned by the AWS service. âĒ Cloud Watch â CloudWatch provides system-wide visibility into resource utilization, application performance, and operational health. Programmatically retrieve your monitoring data, view graphs, and set alarms to help you troubleshoot, spot trends, and take automated action based on the state of your cloud environment.
- 19. Thank You
Editor's Notes
- #11: VPC [Virtual Private Cloud ] lets you provision a logically isolated section of the Amazon Web Services (AWS) Cloud where you can launch AWS resources in a virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways
- #14: For example, if you have S3 buckets that contain highly critical data or EC2 instances that process confidential data, they can be tagged with a âDataClassification=CRITICALâ tag. You can define levels of access to the AWS KMS encryption keys through key policies to ensure that appropriate services have access to the sensitive content through a secure mechanism.