CML's presentation with IORG
Download as pptx, pdf0 likes52 views
This document discusses information infiltration on social media through various means such as advertising, recommendation engines, public and private pages and groups, and messages. It emphasizes the need for transparency and restraint in communication behavior to address concerns around amplification, privacy, policy, and law. It also discusses defense strategies against disinformation attacks that manipulate social algorithms to influence collective online behavior and recommends approaches like detecting attack behavior, analyzing account credibility, and fact checking.
1 of 14
Download to read offline






Ad
Recommended
America Saves Week 2013 eXtension Social Media Project Final Report With Data...
America Saves Week 2013 eXtension Social Media Project Final Report With Data...Barbara O'Neill
?
104 Cooperative Extension educators participated in a social media outreach project for America Saves Week. They posted 100 tweets and Facebook messages each promoting savings tips. The project employed multiple evaluation methods including tracking hashtags, surveys, and click data. Survey results found the messages were helpful and 83% clicked on links. Participants' social media influence increased as measured by Klout and PeerIndex scores. The project was successful in promoting savings messages through social media.US Cyber Security Policy
US Cyber Security Policysuhlingse
?
The document outlines the timeline of key US cybersecurity policies and initiatives from 2003 to 2013, including the establishment of the Department of Homeland Security and the National Cyber Security Division. It discusses how power relationships within the US government have affected cybersecurity policy, and the effects of episodic, social, and system power circuits. Issues identified with US cybersecurity efficacy include a lack of clear leadership, competing priorities, an unurgent threat perception, and insufficient private sector support and resources. The document proposes improvements such as designated cybersecurity leadership, increased regulation and training, improved information sharing, and public-private partnerships.Cybersecurity: Increased Transparency and the Role of Civil Society
Cybersecurity: Increased Transparency and the Role of Civil SocietySarah Granger
?
The document discusses the evolving cybersecurity landscape, highlighting the rise of various cyber threats from state actors, mercenary hackers, and hactivists, as well as the increasing demand for government transparency in response to these threats. It emphasizes the importance of public-private partnerships and civil society in building resilient cybersecurity frameworks and suggests next steps for improving technology education and communication tools. Major hurdles include bureaucratic challenges and the rapid growth of technology, but there's progress in government openness and collaboration with civil society.Design and Prototyping of a Social Media Observatory
Design and Prototyping of a Social Media ObservatoryKarissa Rae McKelvey
?
This document discusses the design and prototyping of a social media observatory to collect and analyze large-scale social media data from Twitter. Some key points:
- It collects a random sample of Twitter data using the Streaming API dating back to August 2010, totaling over 5TB of compressed data related to US politics, social movements, and news.
- It aims to provide reliable, reproducible, and openly accessible social media data and analytics for non-profit uses through standardized data storage, reference models, and APIs/visualizations.
- Legal compliance with Twitter's terms of service is considered, limiting access to tweet text and derived aggregate data rather than individual tweets. The goal is to enable large-scaleMisinfosec frameworks Cansecwest 2019
Misinfosec frameworks Cansecwest 2019bodaceacat
?
The document discusses frameworks for analyzing misinformation from an information security perspective. It begins by describing the problem of misinformation and how it has evolved, then introduces a misinformation-focused version of the ATT&CK framework for mapping misinformation techniques. The framework is populated with real-world examples and analytical approaches. The goal is to establish common languages and methods for understanding, tracking, and responding to misinformation across different communities.Terp breuer misinfosecframeworks_cansecwest2019
Terp breuer misinfosecframeworks_cansecwest2019bodaceacat
?
The document discusses frameworks for analyzing misinformation from an information security perspective. It begins by describing the problem of misinformation and how it has evolved, then introduces a misinformation-focused version of the ATT&CK framework for mapping misinformation techniques. The framework is populated with historical misinformation examples and analytical approaches. The goal is to establish common languages and methods to better understand, track, and respond to misinformation operations.CansecWest2019: Infosec Frameworks for Misinformation
CansecWest2019: Infosec Frameworks for Misinformationbodaceacat
?
The document discusses the challenges of misinformation, particularly in the context of social engineering and influence operations by state and non-state actors. It introduces a framework, 'misinfosec,' which combines information security and misinformation, aiming to create a common language for understanding and combating misinformation online. The framework leverages existing models and analysis techniques to improve responses to misinformation campaigns and highlights the need for collaboration across various sectors.Facebook usato da Governi anche per fake news
Facebook usato da Governi anche per fake newsAndrea Spinosi Picotti
?
The document discusses the challenges and responsibilities Facebook faces in managing information operations on its platform, detailing the risks of disinformation and coordinated manipulation of public discourse. It explains various forms of information operations, including false news and false amplifiers, emphasizing the role of social media in facilitating these actions. Facebook commits to improving security and transparency by implementing measures to mitigate these risks while fostering an environment for authentic civic engagement.CSW2022_05_data collection.pptx.pdf
CSW2022_05_data collection.pptx.pdfSaraJayneTerp
?
This document provides guidance on data collection for analyzing disinformation and malign influence. It discusses supported analysis including threat intelligence, intelligence analysis, open-source intelligence (OSINT), and data science. It describes tactical tasks like credibility verification, network detection, and activity analysis. Toolsets are presented for data gathering from social media and the web, data storage and sharing, information sharing, and response. Methods of automated data collection using APIs and scrapers as well as manual data collection through OSINT techniques are covered. Formats for structured data like JSON, XML, and CSV are demonstrated.DIGITAL HYDRA: SECURITY IMPLICATIONS OF FALSE INFORMATION ONLINE
DIGITAL HYDRA: SECURITY IMPLICATIONS OF FALSE INFORMATION ONLINEAlireza Ghahrood
?
The document titled 'Digital Hydra: Security Implications of False Information Online' discusses the threats posed by misinformation and disinformation on social media, examining how these phenomena affect societal security and the integrity of public discourse. It highlights the evolution of disinformation tactics, particularly in a post-truth environment, and evaluates the challenges faced by social media platforms in countering such narratives. The study also provides actionable knowledge and recommendations for addressing the malicious use of information, emphasizing the importance of understanding cognitive biases that enable the spread of false information.Threaths and risks
Threaths and risksHHSome
?
Social media allows users to share information publicly, but it also exposes them to various online threats. Once information is posted, it can be used to conduct attacks against both the user and their contacts. Attack methods mentioned in the document include baiting, clickjacking, cross-site scripting, doxing, elicitation, pharming, phreaking, scams, spoofing, and phishing. These attacks aim to secretly install malware, steal personal information, or trick users into revealing private details. The document advises being cautious about what information is shared online and checking URLs and email senders to avoid falling victim to such threats.Threaths and risks
Threaths and risksHHSome
?
Social media allows users to share information publicly, but this exposes them to various online threats. Once information is posted, it cannot be fully retracted and can be used for attacks against the user or their contacts. Personal details shared on social media could enable baiting, clickjacking, cross-site scripting, doxing, elicitation, pharming, phreaking, scams, spoofing and phishing attacks that aim to steal sensitive data without directly interacting with social media sites. Users should be aware of these risks and avoid oversharing to stay protected from malicious actors online.IRJET- Competitive Analysis of Attacks on Social Media
IRJET- Competitive Analysis of Attacks on Social MediaIRJET Journal
?
The document discusses deceptions on social media and proposes a machine learning model to detect fake accounts. It first introduces that social media brings both benefits and disadvantages, with deceptions causing problems. It then describes a machine learning pipeline with three parts: (1) a Cluster Builder that groups accounts into real and fake clusters, (2) a Profile Featurizer that extracts features from account profiles to represent clusters, and (3) an Account Scorer that trains models on cluster features and scores new clusters to detect fake accounts. The goal is to use machine learning to help address challenges of deceptions on social media.Introduction to Mining Social Media Data
Introduction to Mining Social Media DataMiriam Fernandez
?
The document provides an introduction to mining social media data. It discusses understanding social media and the most used platforms. It then discusses how social media data can be mined for various purposes like studying social phenomena, businesses monitoring customer communities, and education. Specific examples are given around categorizing social media accounts, policing, energy, disaster management, and addressing challenges like biases and ethics.Social engineering
Social engineeringn|u - The Open Security Community
?
This document discusses social engineering and identity theft. It begins with an introduction to Gaurav Singh and his interests in social engineering attacks and network penetration testing. It then defines social engineering as the art of stealing information from humans through deception rather than technical attacks. The document outlines common social engineering techniques including impersonation, phishing, and using social media to gather information about targets. It also discusses vulnerabilities that enable social engineering like trust, ignorance, and greed. The document explains the risks of social networking in corporate networks and the process of identity theft. It concludes with recommendations for social engineering countermeasures like strong passwords, access control, and monitoring social media activities.Data Breaches and Social Media: yugg.cloud
Data Breaches and Social Media: yugg.cloudNavya kumari
?
This document discusses the increasing concern of data breaches, particularly related to social media, highlighting the types, causes, and impacts of such breaches on individuals and businesses. It emphasizes the importance of strong security measures, careful privacy management, and staying informed about potential threats to mitigate risks. Strategies for protection include using secure passwords, adjusting privacy settings, and maintaining data awareness.Types-of-Social-Engineering-Attacks.pdf in
Types-of-Social-Engineering-Attacks.pdf inrg3935
?
The document discusses various types of social engineering attacks that exploit human psychology to gain access to sensitive information, including phishing, pretexting, baiting, and quid pro quo attacks. It emphasizes the importance of security awareness training, robust password policies, and verification procedures to defend against these threats. Real-world examples illustrate the impact of such attacks, highlighting the need for proactive measures to mitigate risks.Social Media Analytics Strategies And Governance Hamid Jahankhani
Social Media Analytics Strategies And Governance Hamid Jahankhaniparlohanikva
?
Social Media Analytics Strategies And Governance Hamid Jahankhani
Social Media Analytics Strategies And Governance Hamid Jahankhani
Social Media Analytics Strategies And Governance Hamid JahankhaniCognitive security: all the other things
Cognitive security: all the other thingsSara-Jayne Terp
?
This document discusses cognitive security, which involves defending against attempts to intentionally or unintentionally manipulate cognition and sensemaking at scale. It covers various topics related to cognitive security including actors, channels, influencers, groups, messaging, and tools used in disinformation campaigns. Frameworks are presented for analyzing disinformation incidents, adapting concepts from information security like the cyber kill chain. Response strategies are discussed, drawing from fields like information operations, crisis management, and risk management. The need for a common language and ongoing monitoring and evaluation is emphasized.Social Media Challenges in the Digital Age: Mental Health, Misinformation, an...
Social Media Challenges in the Digital Age: Mental Health, Misinformation, an...Azmeen Gadit
?
Explore the top challenges of using social media in today’s digital age—ranging from mental health issues and information overload to misinformation and online privacy risks. This presentation offers practical, research-backed strategies to manage screen time, combat fake news, and protect your digital identity. Ideal for marketers, educators, students, and everyday users seeking to build a healthier, safer, and more intentional online presence. Learn how to balance personal and professional identities, strengthen your digital well-being, and navigate the evolving world of social networks with confidence.disinformation risk management: leveraging cyber security best practices to s...
disinformation risk management: leveraging cyber security best practices to s...Sara-Jayne Terp
?
This document discusses leveraging cybersecurity best practices to support cognitive security goals related to disinformation and misinformation. It outlines three layers of security - physical, cyber, and cognitive security. It then provides examples of cognitive security risk assessment and mapping the risk landscape. Next, it discusses working together to mitigate and respond to risks through proposed cognitive security operations centers. Finally, it provides a hypothetical example of conducting a country-level risk assessment and designing a response strategy. The document advocates adapting frameworks and standards from cybersecurity to help conceptualize and coordinate cognitive security challenges and responses.sabhira khadgi MYP Presentation for students.pptx
sabhira khadgi MYP Presentation for students.pptxsudeshaschool2041
?
The document is a PowerPoint presentation titled 'Safety on Social Media' by Sabhira Khadgi for grade 4, explaining what social media is and the importance of safety while using these platforms. It highlights strategies for online safety, such as using strong passwords, adjusting privacy settings, and recognizing risks like identity theft and cyberbullying. Additionally, it provides best practices for sharing information online and outlines steps to report suspicious activity.How tech titans and rogue nations threaten global stability.
How tech titans and rogue nations threaten global stability.MvdzMloncrypto
?
The document discusses the threats posed by AI-driven misinformation, emphasizing its role in destabilizing democracies, undermining public trust, and promoting disinformation for political gain by influential figures and authoritarian regimes. It highlights the need for comprehensive actions by policymakers and tech companies to address these challenges, including enforcing regulations, promoting digital literacy, and fostering ethical AI development. The global consequences of unchecked AI power and disinformation threaten economies, societies, and international stability.CCU Talk at 2022/01/03
CCU Talk at 2022/01/03Tunghai University
?
This document provides background information on an expert in computational data and offline real world events. It includes the expert's personal information, education history, work experience, research interests, certifications, and an outline of the topics to be covered. The expert's name is Chun-Ming Lai and they are an Assistant Professor in the Department of Information Engineering at Tunghai University. When Online Computational Data Meets
Offline Real World Events
When Online Computational Data Meets
Offline Real World EventsTunghai University
?
The document presents a comprehensive analysis of crisis informatics during the COVID-19 pandemic in Taiwan, including user behaviors related to the use of a face masks map (FMM) and its correlation with public health announcements. Key findings highlight the predictive power of social media sentiments and reactions in forecasting COVID-19 case numbers. Additionally, the research explores state-sponsored propaganda techniques on social media, focusing particularly on a dataset of posts from the People's Republic of China.Mimic iv
Mimic iv Tunghai University
?
惭滨惭滨颁-滨痴是对惭滨惭滨颁-滨滨滨的更新版本,提供了约40000位重症病患的去识别化医疗数据,旨在支持临床研究与机器学习应用。文档详述了数据库的获取流程,包括注册和伦理审查的步骤,以及各个模块的数据结构和信息。通过数据挖掘和分析,该数据库有助于改善医疗服务并确保病患隐私。Pydata Taipei 2020
Pydata Taipei 2020Tunghai University
?
The document discusses the correlation between Twitter users' locations and their opinions on COVID-19, presenting methodologies for data acquisition from Twitter, data pre-processing, and sentiment analysis. It highlights the top five countries (US, India, UK, China, Australia) that tweeted about COVID-19 from February to May, along with sentiment polarity and subjectivity over time. It also briefly contrasts data collection from Twitter and Facebook and mentions tools for sentiment analysis.CML's Presentation at FengChia University
CML's Presentation at FengChia UniversityTunghai University
?
The document discusses social media security challenges related to cognition, cross-platform issues, and push algorithms. It covers topics like abuse targeting internal or external victims, security issues on social media, and the life cycle and influence of social media posts. Detection of multiple accounts and geolocation identification on social media are also summarized.NDU Present
NDU PresentTunghai University
?
The document discusses security challenges in online social media. It begins by introducing the speaker, Chun-Ming Tim Lai, and his background and research interests. It then provides an overview of social media and how it has significantly impacted mass communication compared to traditional media. The document outlines some key security threats in social media like phishing, malware, spam, fake news, and crowdturfing. It proposes using lifecycle analysis of posts, detecting multiple accounts, identifying geolocations, and analyzing personal words to help address these security issues. More Related Content
Similar to CML's presentation with IORG (16)
CSW2022_05_data collection.pptx.pdf
CSW2022_05_data collection.pptx.pdfSaraJayneTerp
?
This document provides guidance on data collection for analyzing disinformation and malign influence. It discusses supported analysis including threat intelligence, intelligence analysis, open-source intelligence (OSINT), and data science. It describes tactical tasks like credibility verification, network detection, and activity analysis. Toolsets are presented for data gathering from social media and the web, data storage and sharing, information sharing, and response. Methods of automated data collection using APIs and scrapers as well as manual data collection through OSINT techniques are covered. Formats for structured data like JSON, XML, and CSV are demonstrated.DIGITAL HYDRA: SECURITY IMPLICATIONS OF FALSE INFORMATION ONLINE
DIGITAL HYDRA: SECURITY IMPLICATIONS OF FALSE INFORMATION ONLINEAlireza Ghahrood
?
The document titled 'Digital Hydra: Security Implications of False Information Online' discusses the threats posed by misinformation and disinformation on social media, examining how these phenomena affect societal security and the integrity of public discourse. It highlights the evolution of disinformation tactics, particularly in a post-truth environment, and evaluates the challenges faced by social media platforms in countering such narratives. The study also provides actionable knowledge and recommendations for addressing the malicious use of information, emphasizing the importance of understanding cognitive biases that enable the spread of false information.Threaths and risks
Threaths and risksHHSome
?
Social media allows users to share information publicly, but it also exposes them to various online threats. Once information is posted, it can be used to conduct attacks against both the user and their contacts. Attack methods mentioned in the document include baiting, clickjacking, cross-site scripting, doxing, elicitation, pharming, phreaking, scams, spoofing, and phishing. These attacks aim to secretly install malware, steal personal information, or trick users into revealing private details. The document advises being cautious about what information is shared online and checking URLs and email senders to avoid falling victim to such threats.Threaths and risks
Threaths and risksHHSome
?
Social media allows users to share information publicly, but this exposes them to various online threats. Once information is posted, it cannot be fully retracted and can be used for attacks against the user or their contacts. Personal details shared on social media could enable baiting, clickjacking, cross-site scripting, doxing, elicitation, pharming, phreaking, scams, spoofing and phishing attacks that aim to steal sensitive data without directly interacting with social media sites. Users should be aware of these risks and avoid oversharing to stay protected from malicious actors online.IRJET- Competitive Analysis of Attacks on Social Media
IRJET- Competitive Analysis of Attacks on Social MediaIRJET Journal
?
The document discusses deceptions on social media and proposes a machine learning model to detect fake accounts. It first introduces that social media brings both benefits and disadvantages, with deceptions causing problems. It then describes a machine learning pipeline with three parts: (1) a Cluster Builder that groups accounts into real and fake clusters, (2) a Profile Featurizer that extracts features from account profiles to represent clusters, and (3) an Account Scorer that trains models on cluster features and scores new clusters to detect fake accounts. The goal is to use machine learning to help address challenges of deceptions on social media.Introduction to Mining Social Media Data
Introduction to Mining Social Media DataMiriam Fernandez
?
The document provides an introduction to mining social media data. It discusses understanding social media and the most used platforms. It then discusses how social media data can be mined for various purposes like studying social phenomena, businesses monitoring customer communities, and education. Specific examples are given around categorizing social media accounts, policing, energy, disaster management, and addressing challenges like biases and ethics.Social engineering
Social engineeringn|u - The Open Security Community
?
This document discusses social engineering and identity theft. It begins with an introduction to Gaurav Singh and his interests in social engineering attacks and network penetration testing. It then defines social engineering as the art of stealing information from humans through deception rather than technical attacks. The document outlines common social engineering techniques including impersonation, phishing, and using social media to gather information about targets. It also discusses vulnerabilities that enable social engineering like trust, ignorance, and greed. The document explains the risks of social networking in corporate networks and the process of identity theft. It concludes with recommendations for social engineering countermeasures like strong passwords, access control, and monitoring social media activities.Data Breaches and Social Media: yugg.cloud
Data Breaches and Social Media: yugg.cloudNavya kumari
?
This document discusses the increasing concern of data breaches, particularly related to social media, highlighting the types, causes, and impacts of such breaches on individuals and businesses. It emphasizes the importance of strong security measures, careful privacy management, and staying informed about potential threats to mitigate risks. Strategies for protection include using secure passwords, adjusting privacy settings, and maintaining data awareness.Types-of-Social-Engineering-Attacks.pdf in
Types-of-Social-Engineering-Attacks.pdf inrg3935
?
The document discusses various types of social engineering attacks that exploit human psychology to gain access to sensitive information, including phishing, pretexting, baiting, and quid pro quo attacks. It emphasizes the importance of security awareness training, robust password policies, and verification procedures to defend against these threats. Real-world examples illustrate the impact of such attacks, highlighting the need for proactive measures to mitigate risks.Social Media Analytics Strategies And Governance Hamid Jahankhani
Social Media Analytics Strategies And Governance Hamid Jahankhaniparlohanikva
?
Social Media Analytics Strategies And Governance Hamid Jahankhani
Social Media Analytics Strategies And Governance Hamid Jahankhani
Social Media Analytics Strategies And Governance Hamid JahankhaniCognitive security: all the other things
Cognitive security: all the other thingsSara-Jayne Terp
?
This document discusses cognitive security, which involves defending against attempts to intentionally or unintentionally manipulate cognition and sensemaking at scale. It covers various topics related to cognitive security including actors, channels, influencers, groups, messaging, and tools used in disinformation campaigns. Frameworks are presented for analyzing disinformation incidents, adapting concepts from information security like the cyber kill chain. Response strategies are discussed, drawing from fields like information operations, crisis management, and risk management. The need for a common language and ongoing monitoring and evaluation is emphasized.Social Media Challenges in the Digital Age: Mental Health, Misinformation, an...
Social Media Challenges in the Digital Age: Mental Health, Misinformation, an...Azmeen Gadit
?
Explore the top challenges of using social media in today’s digital age—ranging from mental health issues and information overload to misinformation and online privacy risks. This presentation offers practical, research-backed strategies to manage screen time, combat fake news, and protect your digital identity. Ideal for marketers, educators, students, and everyday users seeking to build a healthier, safer, and more intentional online presence. Learn how to balance personal and professional identities, strengthen your digital well-being, and navigate the evolving world of social networks with confidence.disinformation risk management: leveraging cyber security best practices to s...
disinformation risk management: leveraging cyber security best practices to s...Sara-Jayne Terp
?
This document discusses leveraging cybersecurity best practices to support cognitive security goals related to disinformation and misinformation. It outlines three layers of security - physical, cyber, and cognitive security. It then provides examples of cognitive security risk assessment and mapping the risk landscape. Next, it discusses working together to mitigate and respond to risks through proposed cognitive security operations centers. Finally, it provides a hypothetical example of conducting a country-level risk assessment and designing a response strategy. The document advocates adapting frameworks and standards from cybersecurity to help conceptualize and coordinate cognitive security challenges and responses.sabhira khadgi MYP Presentation for students.pptx
sabhira khadgi MYP Presentation for students.pptxsudeshaschool2041
?
The document is a PowerPoint presentation titled 'Safety on Social Media' by Sabhira Khadgi for grade 4, explaining what social media is and the importance of safety while using these platforms. It highlights strategies for online safety, such as using strong passwords, adjusting privacy settings, and recognizing risks like identity theft and cyberbullying. Additionally, it provides best practices for sharing information online and outlines steps to report suspicious activity.How tech titans and rogue nations threaten global stability.
How tech titans and rogue nations threaten global stability.MvdzMloncrypto
?
The document discusses the threats posed by AI-driven misinformation, emphasizing its role in destabilizing democracies, undermining public trust, and promoting disinformation for political gain by influential figures and authoritarian regimes. It highlights the need for comprehensive actions by policymakers and tech companies to address these challenges, including enforcing regulations, promoting digital literacy, and fostering ethical AI development. The global consequences of unchecked AI power and disinformation threaten economies, societies, and international stability.More from Tunghai University (8)
CCU Talk at 2022/01/03
CCU Talk at 2022/01/03Tunghai University
?
This document provides background information on an expert in computational data and offline real world events. It includes the expert's personal information, education history, work experience, research interests, certifications, and an outline of the topics to be covered. The expert's name is Chun-Ming Lai and they are an Assistant Professor in the Department of Information Engineering at Tunghai University. When Online Computational Data Meets
Offline Real World Events
When Online Computational Data Meets
Offline Real World EventsTunghai University
?
The document presents a comprehensive analysis of crisis informatics during the COVID-19 pandemic in Taiwan, including user behaviors related to the use of a face masks map (FMM) and its correlation with public health announcements. Key findings highlight the predictive power of social media sentiments and reactions in forecasting COVID-19 case numbers. Additionally, the research explores state-sponsored propaganda techniques on social media, focusing particularly on a dataset of posts from the People's Republic of China.Mimic iv
Mimic iv Tunghai University
?
惭滨惭滨颁-滨痴是对惭滨惭滨颁-滨滨滨的更新版本,提供了约40000位重症病患的去识别化医疗数据,旨在支持临床研究与机器学习应用。文档详述了数据库的获取流程,包括注册和伦理审查的步骤,以及各个模块的数据结构和信息。通过数据挖掘和分析,该数据库有助于改善医疗服务并确保病患隐私。Pydata Taipei 2020
Pydata Taipei 2020Tunghai University
?
The document discusses the correlation between Twitter users' locations and their opinions on COVID-19, presenting methodologies for data acquisition from Twitter, data pre-processing, and sentiment analysis. It highlights the top five countries (US, India, UK, China, Australia) that tweeted about COVID-19 from February to May, along with sentiment polarity and subjectivity over time. It also briefly contrasts data collection from Twitter and Facebook and mentions tools for sentiment analysis.CML's Presentation at FengChia University
CML's Presentation at FengChia UniversityTunghai University
?
The document discusses social media security challenges related to cognition, cross-platform issues, and push algorithms. It covers topics like abuse targeting internal or external victims, security issues on social media, and the life cycle and influence of social media posts. Detection of multiple accounts and geolocation identification on social media are also summarized.NDU Present
NDU PresentTunghai University
?
The document discusses security challenges in online social media. It begins by introducing the speaker, Chun-Ming Tim Lai, and his background and research interests. It then provides an overview of social media and how it has significantly impacted mass communication compared to traditional media. The document outlines some key security threats in social media like phishing, malware, spam, fake news, and crowdturfing. It proposes using lifecycle analysis of posts, detecting multiple accounts, identifying geolocations, and analyzing personal words to help address these security issues. Yuntech present
Yuntech presentTunghai University
?
The document discusses security challenges with online social media. It first outlines the author's background and research interests. It then provides an overview of key aspects of social media compared to traditional media, such as greater data size, user participation, and real-time interaction. The document outlines some major security threats on social media like phishing, malware, spam, fake news, and crowdturfing. It proposes examining suitable targets, lifecycle analysis, detecting multiple accounts, identifying geolocations, and analyzing personal words to address these threats. The outline suggests predicting suitable targets using temporal features and analyzing influence over time.Big data johnson_public
Big data johnson_publicTunghai University
?
The document discusses the establishment of the Tunghai Industry Smart-Transformation Center (TISC) by Tunghai University in collaboration with BlueTalk Asia and Amazon AWS to help Taiwanese industries undergo innovation transformation and industrial upgrading in response to disruptive innovation brought by smart technology. The main responsibilities of the center include assisting industries in digital transformation and innovative upgrading, advising industries on building smart innovation and digital transformation intelligent systems, and facilitating industry-academia collaboration and knowledge sharing.Ad
Recently uploaded (20)
cybercrime investigation and digital forensics
cybercrime investigation and digital forensicsgoverdhankumar137300
?
cybercrime investigation and digital forensics history of internet in nepal Class-8 (sparsha).pptx
history of internet in nepal Class-8 (sparsha).pptxSPARSH508080
?
It tells about the history of computers and internet. Explained breifly最新版美国特拉华大学毕业证(鲍顿别濒毕业证书)原版定制
最新版美国特拉华大学毕业证(鲍顿别濒毕业证书)原版定制taqyea
?
2025原版特拉华大学毕业证书pdf电子版【q薇1954292140】美国毕业证办理UDel特拉华大学毕业证书多少钱?【q薇1954292140】海外各大学Diploma版本,因为疫情学校推迟发放证书、证书原件丢失补办、没有正常毕业未能认证学历面临就业提供解决办法。当遭遇挂科、旷课导致无法修满学分,或者直接被学校退学,最后无法毕业拿不到毕业证。此时的你一定手足无措,因为留学一场,没有获得毕业证以及学历证明肯定是无法给自己和父母一个交代的。
【复刻特拉华大学成绩单信封,Buy University of Delaware Transcripts】
购买日韩成绩单、英国大学成绩单、美国大学成绩单、澳洲大学成绩单、加拿大大学成绩单(q微1954292140)新加坡大学成绩单、新西兰大学成绩单、爱尔兰成绩单、西班牙成绩单、德国成绩单。成绩单的意义主要体现在证明学习能力、评估学术背景、展示综合素质、提高录取率,以及是作为留信认证申请材料的一部分。
特拉华大学成绩单能够体现您的的学习能力,包括特拉华大学课程成绩、专业能力、研究能力。(q微1954292140)具体来说,成绩报告单通常包含学生的学习技能与习惯、各科成绩以及老师评语等部分,因此,成绩单不仅是学生学术能力的证明,也是评估学生是否适合某个教育项目的重要依据!
我们承诺采用的是学校原版纸张(原版纸质、底色、纹路)我们工厂拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有成品以及工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!
【主营项目】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理毕业证|办理文凭: 买大学毕业证|买大学文凭【q薇1954292140】特拉华大学学位证明书如何办理申请?
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理美国成绩单特拉华大学毕业证【q薇1954292140】国外大学毕业证, 文凭办理, 国外文凭办理, 留信网认证Make DDoS expensive for the threat actors
Make DDoS expensive for the threat actorsAPNIC
?
Awal Haolader, Network Analyst / Technical Trainer at APNIC, delivered a presentation titled 'Make DDoS expensive for the threat actors' at Phoenix Summit 2025 held in Dhaka, Bangladesh from 19 to 24 May 2025.Paper: The World Game (s) Great Redesign.pdf
Paper: The World Game (s) Great Redesign.pdfSteven McGee
?
Paper: The REAL QFS - DeFi Quantum Financial System structured data AI symbols exchange derived from Net Centric Warfare, Battlefield Digitization for the World Game (s) Great Reset - Redesign: "End state = "in the beginning state" "Start at end state & work backwards" FutureMan3 years of Quarkus in production, what have we learned - Devoxx Polen
3 years of Quarkus in production, what have we learned - Devoxx PolenJago de Vreede
?
Quarkus has grown in popularity in the last years, but what’s it really like to use it in large-scale, real-world business projects? In this session, we’ll move beyond the basics of "Hello World" to explore how to build enterprise-level applications with Quarkus efficiently.
In this talk we will set up a multi-module project, incorporating integration tests and addressing the challenges with build times, while maintaining a high development velocity. Next, we’ll tackle an upgrade scenario and splitting the application into multiple microservices. Along the way, we’ll share hard-earned lessons, including what to avoid.
At the end of the talk, you should have a good understanding of how to efficiently set up a “big” enterprise project with Quarkus and the confidence to get started.
原版澳洲斯文本科技大学毕业证(厂鲍罢毕业证书)如何办理
原版澳洲斯文本科技大学毕业证(厂鲍罢毕业证书)如何办理taqyed
?
2025年极速办斯文本科技大学毕业证【q薇1954292140】学历认证流程斯文本科技大学毕业证澳洲本科成绩单制作【q薇1954292140】海外各大学Diploma版本,因为疫情学校推迟发放证书、证书原件丢失补办、没有正常毕业未能认证学历面临就业提供解决办法。当遭遇挂科、旷课导致无法修满学分,或者直接被学校退学,最后无法毕业拿不到毕业证。此时的你一定手足无措,因为留学一场,没有获得毕业证以及学历证明肯定是无法给自己和父母一个交代的。
【复刻斯文本科技大学成绩单信封,Buy Swinburne University of Technology Transcripts】
购买日韩成绩单、英国大学成绩单、美国大学成绩单、澳洲大学成绩单、加拿大大学成绩单(q微1954292140)新加坡大学成绩单、新西兰大学成绩单、爱尔兰成绩单、西班牙成绩单、德国成绩单。成绩单的意义主要体现在证明学习能力、评估学术背景、展示综合素质、提高录取率,以及是作为留信认证申请材料的一部分。
斯文本科技大学成绩单能够体现您的的学习能力,包括斯文本科技大学课程成绩、专业能力、研究能力。(q微1954292140)具体来说,成绩报告单通常包含学生的学习技能与习惯、各科成绩以及老师评语等部分,因此,成绩单不仅是学生学术能力的证明,也是评估学生是否适合某个教育项目的重要依据!
我们承诺采用的是学校原版纸张(原版纸质、底色、纹路)我们工厂拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有成品以及工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!
【主营项目】
一.斯文本科技大学毕业证【q微1954292140】斯文本科技大学成绩单、留信认证、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理国外各大学文凭(一对一专业服务,可全程监控跟踪进度)DDoS in India, presented at INNOG 8 by Dave Phelan
DDoS in India, presented at INNOG 8 by Dave PhelanAPNIC
?
Dave Phelan, Senior Network Analyst & Technical Trainer at APNIC, presented on 'DDoS in India' at INNOG 8 held in conjunction with the 2nd India ISP Conclave held in Delhi, India from 23 to 28 May 2025.COMPUTER ETHICS AND CRIME.......................................................
COMPUTER ETHICS AND CRIME.......................................................FOOLKUMARI
?
DONT LOOK AT ME inside the internet - understanding the TCP/IP protocol
inside the internet - understanding the TCP/IP protocolshainweniton02
?
Key factors on TCP/IP protocol最新版美国威斯康星大学绿湾分校毕业证(鲍奥骋叠毕业证书)原版定制
最新版美国威斯康星大学绿湾分校毕业证(鲍奥骋叠毕业证书)原版定制Taqyea
?
鉴于此,定制威斯康星大学绿湾分校学位证书提升履历【q薇1954292140】原版高仿威斯康星大学绿湾分校毕业证(UWGB毕业证书)可先看成品样本【q薇1954292140】帮您解决在美国威斯康星大学绿湾分校未毕业难题,美国毕业证购买,美国文凭购买,【q微1954292140】美国文凭购买,美国文凭定制,美国文凭补办。专业在线定制美国大学文凭,定做美国本科文凭,【q微1954292140】复制美国University of Wisconsin-Green Bay completion letter。在线快速补办美国本科毕业证、硕士文凭证书,购买美国学位证、威斯康星大学绿湾分校Offer,美国大学文凭在线购买。
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
【复刻一套威斯康星大学绿湾分校毕业证成绩单信封等材料最强攻略,Buy University of Wisconsin-Green Bay Transcripts】
购买日韩成绩单、英国大学成绩单、美国大学成绩单、澳洲大学成绩单、加拿大大学成绩单(q微1954292140)新加坡大学成绩单、新西兰大学成绩单、爱尔兰成绩单、西班牙成绩单、德国成绩单。成绩单的意义主要体现在证明学习能力、评估学术背景、展示综合素质、提高录取率,以及是作为留信认证申请材料的一部分。
威斯康星大学绿湾分校成绩单能够体现您的的学习能力,包括威斯康星大学绿湾分校课程成绩、专业能力、研究能力。(q微1954292140)具体来说,成绩报告单通常包含学生的学习技能与习惯、各科成绩以及老师评语等部分,因此,成绩单不仅是学生学术能力的证明,也是评估学生是否适合某个教育项目的重要依据!最新版加拿大奎斯特大学毕业证(蚕鲍颁毕业证书)原版定制
最新版加拿大奎斯特大学毕业证(蚕鲍颁毕业证书)原版定制taqyed
?
2025年极速办奎斯特大学毕业证【q薇1954292140】学历认证流程奎斯特大学毕业证加拿大本科成绩单制作【q薇1954292140】海外各大学Diploma版本,因为疫情学校推迟发放证书、证书原件丢失补办、没有正常毕业未能认证学历面临就业提供解决办法。当遭遇挂科、旷课导致无法修满学分,或者直接被学校退学,最后无法毕业拿不到毕业证。此时的你一定手足无措,因为留学一场,没有获得毕业证以及学历证明肯定是无法给自己和父母一个交代的。
【复刻奎斯特大学成绩单信封,Buy Quest University Canada Transcripts】
购买日韩成绩单、英国大学成绩单、美国大学成绩单、澳洲大学成绩单、加拿大大学成绩单(q微1954292140)新加坡大学成绩单、新西兰大学成绩单、爱尔兰成绩单、西班牙成绩单、德国成绩单。成绩单的意义主要体现在证明学习能力、评估学术背景、展示综合素质、提高录取率,以及是作为留信认证申请材料的一部分。
奎斯特大学成绩单能够体现您的的学习能力,包括奎斯特大学课程成绩、专业能力、研究能力。(q微1954292140)具体来说,成绩报告单通常包含学生的学习技能与习惯、各科成绩以及老师评语等部分,因此,成绩单不仅是学生学术能力的证明,也是评估学生是否适合某个教育项目的重要依据!
我们承诺采用的是学校原版纸张(原版纸质、底色、纹路)我们工厂拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有成品以及工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!
【主营项目】
一.奎斯特大学毕业证【q微1954292140】奎斯特大学成绩单、留信认证、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理国外各大学文凭(一对一专业服务,可全程监控跟踪进度)Ad
CML's presentation with IORG
- 1. Information Infiltration on Social Media Chun-Ming Lai <cmlai@thu.edu.tw>
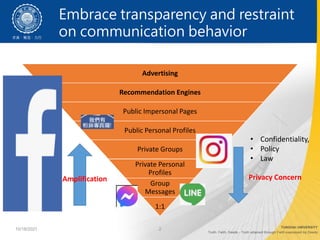
- 2. Advertising Recommendation Engines Public Impersonal Pages Public Personal Profiles Private Groups Private Personal Profiles Group Messages 1:1 10/18/2021 2 Embrace transparency and restraint on communication behavior Amplification Privacy Concern ? Confidentiality, ? Policy ? Law
- 3. Content Context Cognitive Collective Behavior Information Influence 2021/10/18 3 Defense Strategy
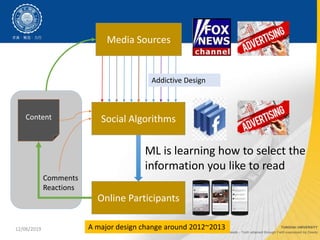
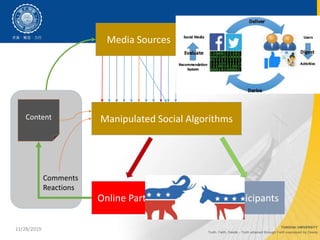
- 4. 12/06/2019 Media Sources Social Algorithms Online Participants Content Comments Reactions ML is learning how to select the information you like to read Addictive Design A major design change around 2012~2013
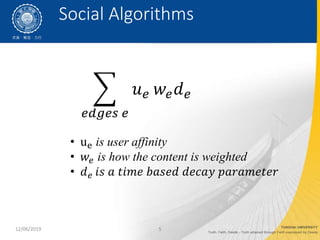
- 5. 12/06/2019 5 ????? ? ?? ???? ? ue is user affinity ? ?? is how the content is weighted ? ?? ?? ? ???? ????? ????? ????????? Social Algorithms
- 7. OUR ALGORITHM Attack Disinformation is ineffective without a successful manipulation of social algorithm Detect Attack behavior-OUR ALGORITHM
- 8. 11/28/2019 Media Sources Manipulated Social Algorithms Online Participants Content Comments Reactions Online Participants
- 9. 12/06/2019 9 Temporal/ Spatial Interaction Graph Accounts Credibility Fact Checker Research Directions
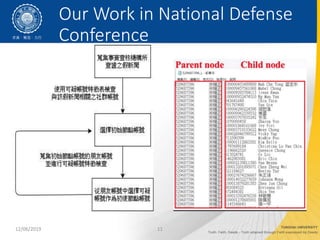
- 11. 12/06/2019 11 Our Work in National Defense Conference
