CXC CSEC Information Technology Multiple Choice Questions
- 1. CXC Multiple Choice Questions 1. Which of the following devices is used to perform input into the computer (a) Monitor (b) Mouse (c)External hard drive (d) USB flash drive 2. Which of the following is NOT part of a diskette? (a) Track (b) sector (c)Cylinder (d)Cluster 3. A diskette is divided into a number of concentric circles called (a) sectors (b) cylinders (c) tracks (d) clusters 4. Which of the following devices is NOT used in a point of sale terminal? (a) Printer (b) Plotter (c)Bar code reader (d) Electronic cash register 5. Resolution determines the clarity of the image displayed on a monitor. The term resolution refers to the number of pixels (a) present horizontally on the screen (b) present vertically on the screen (c)present in a unit area of the screen (d) that make up the colour 6. Identify the list that is arranged starting from the BEST to WORST print quality. (a) Laser, Dot matrix, Inkjet (b) Inkjet, Dot matrix, Laser (c) Laser, Inkjet, Dot matrix (d) Dot matrix, Inkjet, Laser 7. Which of the following is NOT an audio output? (a) Microphone (b) Earphone (c)Headphone (d) Speakers
- 2. 8. The oneŌĆÖs complement of 01010011 is (a) 11010011 (b) 01011111 (c) 10101100 (d) 11111111 9. In modern personal computers, the CPU speed is measured in (a) nanoseconds (b) milliseconds (c) MHz (d) GHz 10. The storage capacity of a floppy disk is (a) 1.44 MB (b) 1.44 GB (c)1440 KB (d) 1440 MB 11. The process of preparing a floppy disk to store data from a computer is called (a) deleting (b) easing (c)formatting (d) archiving 12. An example of a point and draw device is a (a) keyboard (b) joystick (c)mouse (d) scanner 13. An application in which scanners are commonly used is (a) publishing (b) billing (c)printing reports (d) cheque processing 14. Which of the following does NOT serial access? (a) Reel to reel tape (b) Microfilm (c)Microfiche (d) Cartridge tape 15. Which of the following provides transmission of data in BOTH directions at the SAME time? (a) Half Duplex (b) Full Duplex (c) Null Duplex (d) Simplex
- 3. 16. In the URL http://www.shoes.com, ŌĆśshoes.comŌĆÖ stands for the (a) extension (b) company name (c) domain name (d) internet company 17. Google is an example of (a) the Internet Explorer (b) a Web browser (c)a search engine (d) the World Wide Web 18. A new employee at a financial company has been asked to set a password on her computer. She has tried setting the password on several occasions but gets an error message which says ŌĆ£password not effectiveŌĆØ. The problem can be corrected by entering a password that is (a) made up of several numbers (b) a relativeŌĆÖs name (c) composed of at least six upper case characters (d) a mixture of mixed case and alphanumeric characters 19. Transferring data from a remote computer to your computer is referred to as (a) uploading (b) browsing (c)downloading (d) data mining 20. Scrambling of messages at the sending end and unscrambling them at the receiving end is called (a) espionage (b) encryption (c) coding (d) eavesdropping 21. The acronym ŌĆśHTTPŌĆÖ stands for (a) Hyper Text Transfer Protocol (b) Hyper Text Transmission Protocol (c) Higher Text Transmission Protocol (d) Higher Text Transfer Protocol 22. E-mail is the transmission of messages and files via a computer network. E-mail is short for (a) encrypted mail (b) emerging mail (c) entertainment mail (d) electronic mail
- 4. Item 23 refers to the icon below. 23. In an e-mail program the icon above is used to (a) send a file (b) forward a file (c) create a file (d) attach a file 24. Which of the following is NEITHER a validation NOR a verification check? (a) storage media check (b) Inconsistency check (c) Data-type check (d) Range check 25. Advantages of information processing include (a) retraining of staff (b) less human intervention (c) increasing the amount of equipment needed (d) reduction of face-to-face interaction 26. Which of the following statements is true of a transaction file? (a) It is the most complete and up-to-date data file (b) It is used as a back-up copy (c) It is used for real time processing (d) It is used to update the master file 27. Which type of processing systemwill use sequential file organization? (a) Real-time processing (b) Batch processing (c) Transaction processing (d) Online processing 28. Data verification is checking for (a) particular data types (b) data in a specific range
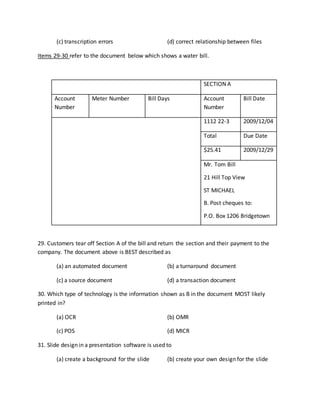
- 5. (c) transcription errors (d) correct relationship between files Items 29-30 refer to the document below which shows a water bill. SECTION A Account Number Meter Number Bill Days Account Number Bill Date 1112 22-3 2009/12/04 Total Due Date $25.41 2009/12/29 Mr. Tom Bill 21 Hill Top View ST MICHAEL B. Post cheques to: P.O. Box 1206 Bridgetown 29. Customers tear off Section A of the bill and return the section and their payment to the company. The document above is BEST described as (a) an automated document (b) a turnaround document (c) a source document (d) a transaction document 30. Which type of technology is the information shown as B in the document MOST likely printed in? (a) OCR (b) OMR (c) POS (d) MICR 31. ║▌║▌▀Ż design in a presentation software is used to (a) create a background for the slide (b) create your own design for the slide
- 6. (c) create a layout for the slide (d) create a style for the slide 32. Which of the following are uses of a typical presentation software? I. To enhance public speaking II. To store records in a structural fashion III. To create graphs of sales IV. To deliver lectures (a) I and II only (b) I and IV only (c) I, II and IV only (d) I, II, III and IV Items 33- 34 refer to the diagram below which shows a section of the standard Toolbar of a word processing package 33. The name of the icon labeled ŌĆś1ŌĆÖ is (a) undo (b) repeat (c) word wrap (d) text alignment 1 2
- 7. 34. The purpose of the icon labeled ŌĆś2ŌĆÖ is to (a) align text on the left and right margin (b) increase the indentation of the selected paragraphs (c) increase the columns in documents (d) display the grid to select columns and rows Item 35 refers to the diagram shown below 35. The diagram above is called the (a) page setup dialog box (b) paragraph dialog box (c) clipboard task pane (d) format dialog box 36. The term used to describe text in a spreadsheet that is aligned towards the left by default is (a) value formulae (b) headings (c) labels (d) values 37. Which of the following is the default justification of numbers in spreadsheets?
- 8. (a) left (b) Full (c)Centred (d) Right 38. When a cell from a spreadsheet is absolute referenced. (a) its value becomes constant (b) its cell address becomes constant (c)its label becomes constant (d) its cell value changes automatically 39. Spreadsheet formulae use (a) values, labels or cell addresses (b) values, mathematical operators or cell addresses (c)labels or cell addresses (d) values or cell addresses 40. Which of the following is NOT involved in extraction or filtering of records in spreadsheets? (a) Value range (b) Criteria range (c)List range (d) Copy to range 41. Which of the following characteristics must two database tables have in order for them to be linked? (a) At least one common attribute name (b) Composite keys (c)At least two tuples in the table (d) The same data in all tuples 42. The term used to describe an attribute that can function like a primary key is a (a) candidate key (b) secondary key (c)foreign key (d) composite key 43.Which of the following is/are true of secondary keys? I. They are used strictly for data retrieval purposes II. They are always in text form III. They do not contain null values
- 9. IV. They do the same function as a foreign key (a) I only (b) II and III only (c)III and IV only (d) I,II,III and IV 44. The object that is used to produce a list of records that meet a particular criterion is a (a) form (b) table (c) module (d) query 45.In a relational database, tables are also called (a) tuples (b) files (c) relational (d) entity 46. Consider the following algorithm A = 7 B= 9 A = B- A B = A+B Write A,B The output of this algorithm is (a) 2,9 (b) 2,16 (c) 7,9 (d) 7,11 47. Consider the following algorithm Sum ’ā¤ 0 Read a,b Sum ’ā¤ a+b Write Sum In the above algorithm, ŌĆśsum’ā¤0ŌĆÖ represents
- 10. (a) a declaration (b) a computation (c) an initialization (d) an assignment 48. In the programming language Pascal, which of the following is NOT a standard data type? (a) Floating point (b) Char (c) Boolean (d) Integer 49. Which of the following structures in most commonly used to implement a post ŌĆōtest loop in Pascal? (a) for ŌĆōdo (b) while-do (c) if-then (d) repeat ŌĆōuntil 50. Which of the following statements would be placed in the flow chart box shown below? (a) Read A (b) A >25 (c) Count ’ā¤ count +1 (d) Output C 51. The purpose of comments in program code is to I. allow persons to read it to follow the processes II. know the purpose of the program III. generate code (a) I and II only (b) I and III only (c) II and III only (d) I, II and III 52. Which of the following are true about the use of indentation in programming? I. To make the layout of the code attractive II. For compiler/interpreter to identify errors easily
- 11. III. For easy understanding of the order of code IV. For easy correction of syntax errors (a) I ,II and III only (b) I, III and IV only (c) II, III and IV only (d) I,II, III and IV only 53. Which of the following is NOT a third generation language? (a) Assembly (b) COBOL (c) C (d) PASCAL 54. The Pascal code var x,y would generate an error. The term used to describe this type of error is. (a) run time error (b) execution error (c) logical error (d) syntax error Item 55 referstothe followingpseudocode ReadA,B If A < 2 C ’ā¤ 2 Else C’ā¤ 6 Endif D ’ā¤C*B +2 Write D 55. What isprintedbythe pseudocode if the inputvalues are 5and 2 respectively? (a) 6 (b) 12 (c)14 (d) 24 56. A compilerissoftware thatconvertsthe (a) source code intoassemblycode
- 12. (b) source code intomachine code (c)programto output (d) program to objectcode one instructionata time 57. The resultof the expression3mod4 is (a) 0 (b) 1 (c)3 (d) 4 58. Whichof the followingsymbolsisusedtoperformassignmentsinthe programminglanguage Pascal? (a) = (b) ’ā¤ (c):= (d) = = 59. The variable total isassignedthe value 12.Which outputshowsthe CORRECT displaywhenthe Pascal code Writeln(ŌĆśtotal =ŌĆÖ);isexecuted? (a) total = (b) 12 (c) total =12 (d) ŌĆśtotal =ŌĆÖ 60. Whichof the followingidentifiersisavalidvariable name? (a) Begin (b) icount (c)Num1 (d) 5sum
- 13. This relates to question 43: A secondarykeyismade ona fieldthatyouwouldlike tobe indexedfor fastersearches! This relates to question 42: primary key:- The attribute or combination of attributes that uniquely identifies a row or record. Foreign Key:- an attribute or combination of attribute in a table whose value match a primary key in another table. Composite key:- A primary key that consistsof two or more attributes is known as composite key candidate key:- is a column in a table which has the ability to become a primary key. Alternate Key:- Any of the candidate keys that is not part of the primary key is called an alternate key.