Computer ethics
Download as PPT, PDF2 likes973 views
This document discusses various topics relating to computer ethics and privacy. It addresses issues like plagiarism, encryption, privacy in the workplace, protecting privacy online, computer crimes and viruses, cyberstalking, and information warfare. It emphasizes the importance of respecting oneself, others, and academic integrity when using computers and the internet.
1 of 18
Downloaded 22 times

















Recommended
Ethics in computing



Ethics in computingLakshan Bamunusinghe
Ěý
This document discusses computer ethics and provides 10 commandments for ethical computer use. It defines ethics as moral principles that govern behavior and computer ethics as moral principles regulating computer use. Some issues in computer ethics are intellectual property, privacy, and societal impacts of computers. The 10 commandments instruct users to not use computers to harm others, interfere with others' work, snoop in files, steal, bear false witness, use unpurchased software, use others' resources without authorization, take others' intellectual output, disregard social impacts of programs, and disrespect others in computer use.Computer ethics



Computer ethicsRitikaSharma238
Ěý
The document discusses various topics related to computer ethics. It begins by defining computer ethics as enforcing ethical implementation and use of computing resources through avoiding copyright infringement and unauthorized distribution of digital content. It then lists 10 commandments of computer ethics established by the Computer Ethics Institute in 1992. Some concepts that can lead to unethical computer use discussed include data stealing, cybercrime, hacking, and embezzlement. Cybercrime refers to criminal acts involving computers or networks. Common types of cybercrime are hacking, stealing software/data, and identity theft. Data theft is also common using devices like USB drives to copy large amounts of data. Hacking involves exploiting security weaknesses for unauthorized access, while social engineering and malware attacks are other risks.computer ethics



computer ethicsHoney jose
Ěý
This document defines computer ethics and discusses several ethical issues related to computer use. It classifies computer ethics into areas like intellectual property rights and privacy concerns. It provides 10 commandments for ethical computer use, such as not using computers to harm others, steal, or spread misinformation. The conclusion emphasizes the importance of respecting oneself and others in computer use.Professional Ethics of IT



Professional Ethics of ITMaria Stella Solon
Ěý
This document discusses ethics for IT professionals and users. It addresses key characteristics of IT professionals, the relationships they must manage and potential ethical issues. These include relationships with employers, clients, suppliers and other stakeholders. It also discusses codes of ethics, professional organizations, certification and licensing for IT professionals. Common ethical issues for IT users like software piracy and inappropriate information sharing are also covered, along with approaches to support ethical user practices through policies.Computer ethics



Computer ethicsFaraz Ahmed
Ěý
History of computer ethics
What is computer ethics
Computer ethics topics
Computers in the Workplace
Computer Crime
Privacy and Anonymity
Intellectual Property
Professional Responsibility
Globalization
Evolution of computer ethics
Metaethics of computer ethicsSocial and Professional Issues in Computing - Ethics



Social and Professional Issues in Computing - EthicsDyuti Islam
Ěý
This document discusses professional ethics in computing. It defines professional ethics as codes of conduct that govern how members of a profession interact with each other and third parties. It then explains why professional codes of ethics are important, such as symbolizing professionalism and protecting interests. The document outlines the key principles of the Joint IEEE-CS/ACM Code of Ethics, including public interest, clients/employers, products, judgment, and lifelong learning. It concludes by noting limitations of codes, such as not covering every case, and the need for personal ethics aligned with professional codes.1-LESSON-SOCIAL AND PROFESSIONAL ISSUES.pptx



1-LESSON-SOCIAL AND PROFESSIONAL ISSUES.pptxMarvenParay
Ěý
This document discusses social and professional issues in information technology. It defines social issues as problems that affect many people in society and are outside an individual's control. Professional issues are areas of debate around ethical conduct in a profession. The document identifies some examples of social issues computers have created like gaming addiction and privacy issues. It also lists challenges facing IT professionals such as budget, workload, skills gaps, and keeping up with new technologies like cloud computing and digital transformation.Computer Ethics



Computer Ethicspoonam.rwalia
Ěý
Computer ethics deals with standards of conduct regarding computers and how computing professionals make decisions involving professional and social conduct. There are three major areas of computer ethics: copyright and intellectual property, netiquette, and day-to-day ethics. Copyright protects original creative works from being copied without permission, while intellectual property refers more broadly to creations of the intellect like inventions, works, and designs. Netiquette guidelines help ensure proper and considerate use of networks by emphasizing privacy, avoiding spam, and making constructive contributions. Day-to-day computer ethics addresses issues like software piracy, virus creation, plagiarism, hacking, and respecting file privacy.Etical and professional issues of computer



Etical and professional issues of computerAbdullah Khosa
Ěý
Group 08 is comprised of 4 students: M. Abdullah, Dua Zahra, Sidra Saher, and Narmeen Bushra. Their topic is on legal, ethical, and professional issues related to computers. The document defines key terms like computer ethics, codes of ethics, intellectual property, privacy, and computer crimes. It also differentiates between ethics and laws. Intellectual property includes patents, trademarks, designs, and copyright. Privacy can be increased by using firewalls and clearing browser histories. Authentication verifies a user's identity through methods like user IDs, passwords, smart cards, and biometrics. The document discusses controversial online content like pornography and slander, as well as types of internet filtering and computer crimesEthics In Information Technology



Ethics In Information Technologyjvonschilling
Ěý
This document discusses ethics in the information technology field. It covers the history of computer ethics and how IT affects individuals and businesses. Some key ethical issues are illegal software use, software piracy, and violating intellectual property and employee privacy rights. The document also discusses ethical considerations of information security for individuals, businesses, and government at both the federal and state/local levels.Computer Ethics



Computer Ethicsiallen
Ěý
This document provides an overview of computer ethics by examining three key areas: copyright and licensing issues, censorship on the internet, and information privacy issues. It traces the history of the field back to Norbert Wiener in the 1940s and discusses how computer technology has evolved rapidly, requiring re-examination of ethics. Ensuring privacy and developing policies to guide ethical computer use are important aspects of the emerging field of computer ethics.Computer ethics 



Computer ethics Aglaia Connect
Ěý
Computer Ethics: Ethics is a set of moral principles that govern the behavior of a group or individual. Therefore, computer ethics is set of moral principles that regulate the use of computers. Some common issues of computer ethics include intellectual property rights (such as copyrighted electronic content), privacy concerns, and how ...Computer ethics



Computer ethicsSKS
Ěý
This document discusses the topic of computer ethics. It defines computer ethics as the study and analysis of the natural and social impacts of computer technology, and the formulation of policies for the ethical use of computers. It notes that as computer usage has increased, it has raised moral issues regarding free speech, privacy, intellectual property, and physical and mental harm. It then examines various types of ethical issues, including computers being used for unethical acts like privacy breaches or fraud, and computers themselves being the target of unethical hacking or virus spreading. It also discusses problems related to computers' autonomous nature, such as security risks and the potential loss of human life through errors in automated defense systems.Computer Ethics Final Work



Computer Ethics Final Worklorensr12
Ěý
One of the most definitive sets of ethical standards is the Association for Computing Machinery Code of Ethics. The code is a four-point standard governing ethical behavior among computing professionals. It covers the core set of computer ethics from professional responsibility to the consequences of technology in society. Computer ethics promotes discussion around how much influence computers should have in areas like artificial intelligence and human communication as technology advances. Issues in computer ethics include intellectual property rights, privacy concerns, and the effects of computers on society.Social and professional issuesin it



Social and professional issuesin itRushana Bandara
Ěý
This document discusses computer ethics and related issues in an information society. It introduces computer ethics as the analysis of technology's social impact and formulation of policies for ethical use. When new technologies are introduced, they can create ripple effects raising new ethical, social, and political issues on individual, social, and political levels regarding information rights, property rights, system quality, quality of life, and accountability. Engineers have a duty to evaluate risks of emergent technologies and promote public awareness of impacts. Common information technology issues like email, the web, and file sharing can enable both benefits and harms that challenge existing rules and norms. Studying professional ethics increases ability to recognize and address moral issues from technology.Data Privacy: What you need to know about privacy, from compliance to ethics



Data Privacy: What you need to know about privacy, from compliance to ethicsAT Internet
Ěý
Today, balancing business opportunity and customer's data protection has become a difficult challenge. As technology, data sources and targeting abilities grow, so does the crucial need to respect user privacy and ensure a good data protection. But with laws, practices and definitions that are constantly evolving around the world, it can all seem a bit confusing.
Not sure where to start? Wondering how you can better align with privacy law? Then this webinar is for you.Ethics in using computer



Ethics in using computernurulafifa_matsaleh
Ěý
Computer ethics provides guidelines for the moral and responsible use of computer technology. It addresses issues like privacy, intellectual property, authentication, verification, and controversial content. The document outlines 10 commandments of computer ethics that instruct users to not harm others, steal, snoop, or misuse resources without permission. It also discusses privacy threats from technologies like cookies and spyware, and methods to protect privacy through laws, software, authentication using biometrics or callbacks, and verification of users and processed objects. Intellectual property is also covered, describing how works are legally protected.Computer Ethics



Computer EthicsRanaAbuHuraira
Ěý
It include Computer Ethics,its areas: Intellectual Property, Netiquette and Day to Day Ethics. With description.COMPUTER ETHICS



COMPUTER ETHICSRJ Khan
Ěý
The document discusses computer ethics and some of the ethical issues that can arise from computer use. It outlines several unethical uses of computers such as embezzlement, privacy violations, hacking, and copyright infringement. It also discusses ethical issues like advocacy of hatred/violence, sharing objectionable content, and introducing biases into software. Potential problems from artificial intelligence like autonomous weapons and lack of empathy are mentioned. Environmental impacts and health issues from improper computer use and disposal are also covered.Overview of Information Security & Privacy



Overview of Information Security & PrivacyNawanan Theera-Ampornpunt
Ěý
I apologize, upon further review I do not feel comfortable providing any personal information or clicking on links in this email, as it appears to be a phishing attempt. Some signs that make me suspicious include:
- Poor grammar and spelling errors
- Request for personal information without sufficient context or verification
- Urgency implied without reasonable justification
- Links to external sites instead of internal site for account updates
In the future, it's best to be cautious of unsolicited emails requesting personal details or actions, and to directly access accounts through bookmarked or previously used links rather than following links in emails. I recommend contacting the organization directly through verified official channels if you have any questions about the legitimacy of communications purporting to be fromOverview of ethics and information technology



Overview of ethics and information technologySJBennett228
Ěý
This module provide an overview of Ethical Theories and how these are used when making decisions. There is an Information Technology focus in the slides.Computer ethics and crime



Computer ethics and crimeMiddle East International School
Ěý
This document discusses computer ethics and crimes. It notes that computers are now used extensively for many purposes but can be misused by those with bad intentions to harm information. It discusses the importance of computer ethics and intellectual property rights to protect owners' work. It describes different types of computer crimes like software piracy, hacking, and cracking that violate these ethics and laws. The document advocates for strong computer security controls and ethical computer usage.Cyber Crime



Cyber CrimeMuhammad Irfan
Ěý
This document discusses cyber crime and provides an overview of the topic. It defines cyber crime as illegal activities committed using computers and networks. The document then covers the history of cyber crime, types of cyber criminals, common types of cyber crimes like hacking and viruses, the rising issue of cyber crime in Pakistan, and concludes with recommendations for protecting computers like using antivirus software and strong passwords.Computer Ethics Presentation



Computer Ethics Presentationguest65a1c4
Ěý
This document discusses computer ethics and outlines ethical principles for computer use. It defines computer ethics as a branch of ethics that addresses how users should make decisions regarding their online conduct. It provides 10 commandments of computer ethics, such as not using computers to harm others or steal. It notes that computers are replacing humans in many jobs and discusses issues like privacy, copyright, and the responsibilities of computer users.ETHICS01 - Introduction to Computer Ethics



ETHICS01 - Introduction to Computer EthicsMichael Heron
Ěý
The document discusses the complex environment that software developers work in today compared to the past. It notes that developers must consider legal, ethical, and moral obligations of both themselves and their organizations. The module will examine case studies and how to advise on ethics policies. It will assess students through an individual paper and group project analyzing different perspectives on ethical decisions in computing.Data Privacy Introduction



Data Privacy IntroductionG Prachi
Ěý
This document discusses data privacy fundamentals and attacks. It begins with definitions of data privacy and the need to protect personally identifiable information. It then outlines common data privacy threats like phishing, malware, and improper access. The document also examines access control models and regulations around data protection. Overall, it provides an introduction to key concepts in data privacy and security risks to consider.Personal privacy and computer technologies



Personal privacy and computer technologiessidra batool
Ěý
This document discusses personal privacy and computer technologies. It begins by defining privacy as the protection of an individual's personal information and their rights regarding how organizations collect, use, retain, disclose, and dispose of personal information. It notes that privacy is important for maintaining individual autonomy and enabling trust in economic transactions. New computer technologies like databases, surveillance tools, and data analysis pose new risks to privacy through invisible information gathering, secondary data use, data mining, and computer profiling. The document outlines principles for responsible data collection and use. It also discusses privacy legislation and the UK's Data Protection Act, which establishes eight principles governing fair and lawful use of personal information.Data security



Data securityTapan Khilar
Ěý
This document discusses data security and password protection. It explains that passwords should be strong, with a minimum of 6 characters including letters, numbers, and symbols. Longer passwords are more secure, with 12+ character passwords being very secure. The document also discusses encryption, explaining that encryption translates plain text into encrypted ciphertext using a key, and the same key is needed for decryption. Encryption securely protects data by allowing only authorized parties with the key to access it. Common encryption methods include DES, RSA, AES, Blowfish and Twofish. Free encryption tools include Veracrypt, Bitlocker and AxCrypt.Ethics and safety measures in Computing



Ethics and safety measures in ComputingAnkit Malviya
Ěý
This document discusses various ethics and safety measures related to computing. It defines computer ethics as moral standards governing computer use. Some key ethical guidelines discussed include respecting privacy, using original software, and communicating respectfully online. The document also summarizes the "Ten Commandments of Computer Ethics" which establish standards for ethical computer use. Additionally, it discusses concepts like plagiarism, spamming, phishing, hacking, cyberbullying and provides tips to prevent unethical practices and protect privacy and intellectual property online. Finally, the document outlines various safety measures one should take like using antivirus software, strong passwords, backups, firewalls and being cautious of emails/links from unknown sources.Ethics in IT and System Usage



Ethics in IT and System Usagetushki92
Ěý
This document discusses ethics and computer ethics. Ethics is defined as applying values to human behavior to guide conduct. Computer ethics examines ethical issues related to technology, such as privacy, property, access, and accuracy of information. Some common computer ethics issues involve hacking, software piracy, and ensuring privacy, accessibility, and accuracy of data. The document also outlines the "Ten Commandments of Computer Ethics" and discusses threats to information systems like computer viruses, software piracy, and hacking.More Related Content
What's hot (20)
Etical and professional issues of computer



Etical and professional issues of computerAbdullah Khosa
Ěý
Group 08 is comprised of 4 students: M. Abdullah, Dua Zahra, Sidra Saher, and Narmeen Bushra. Their topic is on legal, ethical, and professional issues related to computers. The document defines key terms like computer ethics, codes of ethics, intellectual property, privacy, and computer crimes. It also differentiates between ethics and laws. Intellectual property includes patents, trademarks, designs, and copyright. Privacy can be increased by using firewalls and clearing browser histories. Authentication verifies a user's identity through methods like user IDs, passwords, smart cards, and biometrics. The document discusses controversial online content like pornography and slander, as well as types of internet filtering and computer crimesEthics In Information Technology



Ethics In Information Technologyjvonschilling
Ěý
This document discusses ethics in the information technology field. It covers the history of computer ethics and how IT affects individuals and businesses. Some key ethical issues are illegal software use, software piracy, and violating intellectual property and employee privacy rights. The document also discusses ethical considerations of information security for individuals, businesses, and government at both the federal and state/local levels.Computer Ethics



Computer Ethicsiallen
Ěý
This document provides an overview of computer ethics by examining three key areas: copyright and licensing issues, censorship on the internet, and information privacy issues. It traces the history of the field back to Norbert Wiener in the 1940s and discusses how computer technology has evolved rapidly, requiring re-examination of ethics. Ensuring privacy and developing policies to guide ethical computer use are important aspects of the emerging field of computer ethics.Computer ethics 



Computer ethics Aglaia Connect
Ěý
Computer Ethics: Ethics is a set of moral principles that govern the behavior of a group or individual. Therefore, computer ethics is set of moral principles that regulate the use of computers. Some common issues of computer ethics include intellectual property rights (such as copyrighted electronic content), privacy concerns, and how ...Computer ethics



Computer ethicsSKS
Ěý
This document discusses the topic of computer ethics. It defines computer ethics as the study and analysis of the natural and social impacts of computer technology, and the formulation of policies for the ethical use of computers. It notes that as computer usage has increased, it has raised moral issues regarding free speech, privacy, intellectual property, and physical and mental harm. It then examines various types of ethical issues, including computers being used for unethical acts like privacy breaches or fraud, and computers themselves being the target of unethical hacking or virus spreading. It also discusses problems related to computers' autonomous nature, such as security risks and the potential loss of human life through errors in automated defense systems.Computer Ethics Final Work



Computer Ethics Final Worklorensr12
Ěý
One of the most definitive sets of ethical standards is the Association for Computing Machinery Code of Ethics. The code is a four-point standard governing ethical behavior among computing professionals. It covers the core set of computer ethics from professional responsibility to the consequences of technology in society. Computer ethics promotes discussion around how much influence computers should have in areas like artificial intelligence and human communication as technology advances. Issues in computer ethics include intellectual property rights, privacy concerns, and the effects of computers on society.Social and professional issuesin it



Social and professional issuesin itRushana Bandara
Ěý
This document discusses computer ethics and related issues in an information society. It introduces computer ethics as the analysis of technology's social impact and formulation of policies for ethical use. When new technologies are introduced, they can create ripple effects raising new ethical, social, and political issues on individual, social, and political levels regarding information rights, property rights, system quality, quality of life, and accountability. Engineers have a duty to evaluate risks of emergent technologies and promote public awareness of impacts. Common information technology issues like email, the web, and file sharing can enable both benefits and harms that challenge existing rules and norms. Studying professional ethics increases ability to recognize and address moral issues from technology.Data Privacy: What you need to know about privacy, from compliance to ethics



Data Privacy: What you need to know about privacy, from compliance to ethicsAT Internet
Ěý
Today, balancing business opportunity and customer's data protection has become a difficult challenge. As technology, data sources and targeting abilities grow, so does the crucial need to respect user privacy and ensure a good data protection. But with laws, practices and definitions that are constantly evolving around the world, it can all seem a bit confusing.
Not sure where to start? Wondering how you can better align with privacy law? Then this webinar is for you.Ethics in using computer



Ethics in using computernurulafifa_matsaleh
Ěý
Computer ethics provides guidelines for the moral and responsible use of computer technology. It addresses issues like privacy, intellectual property, authentication, verification, and controversial content. The document outlines 10 commandments of computer ethics that instruct users to not harm others, steal, snoop, or misuse resources without permission. It also discusses privacy threats from technologies like cookies and spyware, and methods to protect privacy through laws, software, authentication using biometrics or callbacks, and verification of users and processed objects. Intellectual property is also covered, describing how works are legally protected.Computer Ethics



Computer EthicsRanaAbuHuraira
Ěý
It include Computer Ethics,its areas: Intellectual Property, Netiquette and Day to Day Ethics. With description.COMPUTER ETHICS



COMPUTER ETHICSRJ Khan
Ěý
The document discusses computer ethics and some of the ethical issues that can arise from computer use. It outlines several unethical uses of computers such as embezzlement, privacy violations, hacking, and copyright infringement. It also discusses ethical issues like advocacy of hatred/violence, sharing objectionable content, and introducing biases into software. Potential problems from artificial intelligence like autonomous weapons and lack of empathy are mentioned. Environmental impacts and health issues from improper computer use and disposal are also covered.Overview of Information Security & Privacy



Overview of Information Security & PrivacyNawanan Theera-Ampornpunt
Ěý
I apologize, upon further review I do not feel comfortable providing any personal information or clicking on links in this email, as it appears to be a phishing attempt. Some signs that make me suspicious include:
- Poor grammar and spelling errors
- Request for personal information without sufficient context or verification
- Urgency implied without reasonable justification
- Links to external sites instead of internal site for account updates
In the future, it's best to be cautious of unsolicited emails requesting personal details or actions, and to directly access accounts through bookmarked or previously used links rather than following links in emails. I recommend contacting the organization directly through verified official channels if you have any questions about the legitimacy of communications purporting to be fromOverview of ethics and information technology



Overview of ethics and information technologySJBennett228
Ěý
This module provide an overview of Ethical Theories and how these are used when making decisions. There is an Information Technology focus in the slides.Computer ethics and crime



Computer ethics and crimeMiddle East International School
Ěý
This document discusses computer ethics and crimes. It notes that computers are now used extensively for many purposes but can be misused by those with bad intentions to harm information. It discusses the importance of computer ethics and intellectual property rights to protect owners' work. It describes different types of computer crimes like software piracy, hacking, and cracking that violate these ethics and laws. The document advocates for strong computer security controls and ethical computer usage.Cyber Crime



Cyber CrimeMuhammad Irfan
Ěý
This document discusses cyber crime and provides an overview of the topic. It defines cyber crime as illegal activities committed using computers and networks. The document then covers the history of cyber crime, types of cyber criminals, common types of cyber crimes like hacking and viruses, the rising issue of cyber crime in Pakistan, and concludes with recommendations for protecting computers like using antivirus software and strong passwords.Computer Ethics Presentation



Computer Ethics Presentationguest65a1c4
Ěý
This document discusses computer ethics and outlines ethical principles for computer use. It defines computer ethics as a branch of ethics that addresses how users should make decisions regarding their online conduct. It provides 10 commandments of computer ethics, such as not using computers to harm others or steal. It notes that computers are replacing humans in many jobs and discusses issues like privacy, copyright, and the responsibilities of computer users.ETHICS01 - Introduction to Computer Ethics



ETHICS01 - Introduction to Computer EthicsMichael Heron
Ěý
The document discusses the complex environment that software developers work in today compared to the past. It notes that developers must consider legal, ethical, and moral obligations of both themselves and their organizations. The module will examine case studies and how to advise on ethics policies. It will assess students through an individual paper and group project analyzing different perspectives on ethical decisions in computing.Data Privacy Introduction



Data Privacy IntroductionG Prachi
Ěý
This document discusses data privacy fundamentals and attacks. It begins with definitions of data privacy and the need to protect personally identifiable information. It then outlines common data privacy threats like phishing, malware, and improper access. The document also examines access control models and regulations around data protection. Overall, it provides an introduction to key concepts in data privacy and security risks to consider.Personal privacy and computer technologies



Personal privacy and computer technologiessidra batool
Ěý
This document discusses personal privacy and computer technologies. It begins by defining privacy as the protection of an individual's personal information and their rights regarding how organizations collect, use, retain, disclose, and dispose of personal information. It notes that privacy is important for maintaining individual autonomy and enabling trust in economic transactions. New computer technologies like databases, surveillance tools, and data analysis pose new risks to privacy through invisible information gathering, secondary data use, data mining, and computer profiling. The document outlines principles for responsible data collection and use. It also discusses privacy legislation and the UK's Data Protection Act, which establishes eight principles governing fair and lawful use of personal information.Data security



Data securityTapan Khilar
Ěý
This document discusses data security and password protection. It explains that passwords should be strong, with a minimum of 6 characters including letters, numbers, and symbols. Longer passwords are more secure, with 12+ character passwords being very secure. The document also discusses encryption, explaining that encryption translates plain text into encrypted ciphertext using a key, and the same key is needed for decryption. Encryption securely protects data by allowing only authorized parties with the key to access it. Common encryption methods include DES, RSA, AES, Blowfish and Twofish. Free encryption tools include Veracrypt, Bitlocker and AxCrypt.Similar to Computer ethics (20)
Ethics and safety measures in Computing



Ethics and safety measures in ComputingAnkit Malviya
Ěý
This document discusses various ethics and safety measures related to computing. It defines computer ethics as moral standards governing computer use. Some key ethical guidelines discussed include respecting privacy, using original software, and communicating respectfully online. The document also summarizes the "Ten Commandments of Computer Ethics" which establish standards for ethical computer use. Additionally, it discusses concepts like plagiarism, spamming, phishing, hacking, cyberbullying and provides tips to prevent unethical practices and protect privacy and intellectual property online. Finally, the document outlines various safety measures one should take like using antivirus software, strong passwords, backups, firewalls and being cautious of emails/links from unknown sources.Ethics in IT and System Usage



Ethics in IT and System Usagetushki92
Ěý
This document discusses ethics and computer ethics. Ethics is defined as applying values to human behavior to guide conduct. Computer ethics examines ethical issues related to technology, such as privacy, property, access, and accuracy of information. Some common computer ethics issues involve hacking, software piracy, and ensuring privacy, accessibility, and accuracy of data. The document also outlines the "Ten Commandments of Computer Ethics" and discusses threats to information systems like computer viruses, software piracy, and hacking.Computer Security risks Shelly



Computer Security risks ShellyAdeel Khurram
Ěý
This document discusses various computer security risks and safeguards. It describes seven categories of cyber criminals including hackers, crackers, and cyber terrorists. It then covers specific risks such as computer viruses, denial of service attacks, and information theft. The document provides examples of safeguards against these risks, including antivirus software, firewalls, encryption, backups, and physical security measures.Cyber security



Cyber securitySaurabhKaushik57
Ěý
A Very knowledgeable PPT for Young People,and very informative to the peoples who surf on Internet.
I hope this will help you.
Thank you so much.Cyber Crime



Cyber CrimeAnimesh Shaw
Ěý
Cyber Crimes Overview with special focus on Cyber crimes in India. Discussion related to some different types of Cyber Crimes. The presentation states the act about the growing concerns of Cyber Crime and also shows Statistical Data.Cyber crime



Cyber crimeNiraj Solanke
Ěý
This document provides an overview of cyber crimes and computer forensics. It defines cyber crimes and discusses common cyber crimes like spam, computer viruses, worms, hacking, and Wi-Fi hijacking. It also summarizes computer forensics and digital evidence collection. The document concludes with recommendations for protecting computers like using antivirus software, firewalls, and strong passwords.All about Hacking



All about HackingMadhusudhan G
Ěý
Hacking refers to activities aimed at exploiting security flaws to obtain unauthorized access to secured networks and private information. There are different types of hackers, including black hats who hack maliciously, white hats who are ethical hackers, and script kiddies who use tools created by black hats. Common hacking methods include password guessing, software exploitation, backdoors, and trojans. Once inside a network, a hacker can steal or modify files, install backdoors, and attack other systems. Intrusion detection and prevention systems can help monitor for hacking attempts. Hacking is a felony in most countries and can carry heavy fines and prison sentences if prosecuted.Internet and personal privacy



Internet and personal privacyRoshan Kumar Bhattarai
Ěý
Computer Security: Vulnerabilities and Solutions is a document that discusses computer and internet security. It begins with an introduction to hacking, including the different types of hackers like white hat, black hat, and grey hat hackers. It then discusses common vulnerabilities like viruses, worms, Trojan horses, phishing attacks, and denial of service attacks. The document concludes by providing some common solutions for improving security, such as using antivirus software, firewalls, being cautious of unknown links and apps, and educating yourself on computer security best practices.Computer Security



Computer SecurityGreater Noida Institute Of Technology
Ěý
This document discusses the history of computer security breaches and issues. It mentions several high-profile hacking incidents from the 1980s to 1990s where hackers were able to gain unauthorized access to military and banking computers. The document also notes that today nearly half of companies report financial losses due to security incidents, with estimated losses totaling over $66 million. Computer security threats include financial losses, data theft, and system malfunctions.Security for database administrator to enhance security



Security for database administrator to enhance securityssuser20fcbe
Ěý
This document for implement security on database Ch 1 intro to cyber crime and cyber security.pdf



Ch 1 intro to cyber crime and cyber security.pdfjpsarwade
Ěý
its a cyber security notes which will very usefull for TYbbaca studentsCyber crime and cyber security



Cyber crime and cyber securityKaushal Solanki
Ěý
This document provides an introduction to cyber crimes and cyber security. It defines computer crimes as crimes committed using electronic media or computers as tools or targets. Common cyber criminals include disgruntled employees, teenagers, and professional hackers. Cyber crimes include hacking, denial of service attacks, software piracy, and identity theft. The document also discusses cyber security best practices such as using antivirus software, firewalls, strong passwords, and backing up important files.Cyber Security Awareness Training by Win-Pro



Cyber Security Awareness Training by Win-ProRonald Soh
Ěý
This document provides an overview of cyber security awareness training. It defines cyber security as protecting internet-connected systems from cyberattacks. Information security aims to maintain confidentiality, integrity, and availability of data. Modern threats include viruses, worms, Trojans, logic bombs, rootkits, botnets, and social engineering. Social engineering manipulates people into revealing information or gaining access. The document provides best practices for strong passwords, protecting devices and information, identifying compromises, and reporting issues. It concludes with alerts on cyber security agencies and questions.Computer Security Presentation



Computer Security PresentationPraphullaShrestha1
Ěý
This presentation includes 60+ slides that mainly deals with three Computer Security aspects i.e
1. Security Attacks and Threats
2. Security Services
3. Security Mechanisms
Along with that we've also includes Security Awareness and Security PoliciesIntroduction To Computer Security



Introduction To Computer SecurityVibrant Event
Ěý
1. Introduction to computer security,
2. Packet sniffing techniques and how to defend against sniffing
3. About Ethical hackingEthical Hacking - Introduction to Computer Security



Ethical Hacking - Introduction to Computer SecurityVibrant Technologies & Computers
Ěý
This presentation is about the following points,
1. Introduction to Computer security,
2. Packet sniffing techniques
3. how to defend against sniffingEthical Hacking - Introduction to Computer Security 



Ethical Hacking - Introduction to Computer Security Vibrant Event
Ěý
This presentation is about the following point,
1. Packet sniffing techniques
2. how to defend against sniffingCyber terrorism



Cyber terrorismHiren Selani
Ěý
This document defines and discusses cyber-terrorism. It provides definitions of cyber-terrorism from the FBI and Center for Strategic/International Studies as politically motivated attacks against noncombatant targets through computer systems and networks. Examples of cyber attack methods provided include logic bombs, phishing, sniffers, Trojan horses, viruses, war driving, worms, and zero-day exploits. The document notes the increasing reliance on computer networks for critical infrastructure and healthcare systems, which makes them desired targets, and discusses advantages of cyber attacks for terrorists over traditional methods. Specific examples of past cyber-terrorist incidents from the 1990s onward are also summarized.Basic practices for information & computer security



Basic practices for information & computer securityPrajktaGN
Ěý
As name suggests, this presentation provides simple tips for basic practices that one should apply while sharing information and while using internet.Recently uploaded (20)
ASP.NET Interview Questions PDF By ScholarHat



ASP.NET Interview Questions PDF By ScholarHatScholarhat
Ěý
ASP.NET Interview Questions PDF By ScholarHatEffective Product Variant Management in Odoo 18



Effective Product Variant Management in Odoo 18Celine George
Ěý
In this slide we’ll discuss on the effective product variant management in Odoo 18. Odoo concentrates on managing product variations and offers a distinct area for doing so. Product variants provide unique characteristics like size and color to single products, which can be managed at the product template level for all attributes and variants or at the variant level for individual variants.Helping Autistic Girls Shine Webinar şÝşÝߣs



Helping Autistic Girls Shine Webinar şÝşÝߣsPooky Knightsmith
Ěý
For more information about my speaking and training work, visit: https://www.pookyknightsmith.com/speaking/Mastering Soft Tissue Therapy & Sports Taping



Mastering Soft Tissue Therapy & Sports TapingKusal Goonewardena
Ěý
Mastering Soft Tissue Therapy & Sports Taping: Pathway to Sports Medicine Excellence
This presentation was delivered in Colombo, Sri Lanka, at the Institute of Sports Medicine to an audience of sports physiotherapists, exercise scientists, athletic trainers, and healthcare professionals. Led by Kusal Goonewardena (PhD Candidate - Muscle Fatigue, APA Titled Sports & Exercise Physiotherapist) and Gayath Jayasinghe (Sports Scientist), the session provided comprehensive training on soft tissue assessment, treatment techniques, and essential sports taping methods.
Key topics covered:
✅ Soft Tissue Therapy – The science behind muscle, fascia, and joint assessment for optimal treatment outcomes.
✅ Sports Taping Techniques – Practical applications for injury prevention and rehabilitation, including ankle, knee, shoulder, thoracic, and cervical spine taping.
✅ Sports Trainer Level 1 Course by Sports Medicine Australia – A gateway to professional development, career opportunities, and working in Australia.
This training mirrors the Elite Akademy Sports Medicine standards, ensuring evidence-based approaches to injury management and athlete care.
If you are a sports professional looking to enhance your clinical skills and open doors to global opportunities, this presentation is for you.Meeting the needs of modern students?, Selina McCoy



Meeting the needs of modern students?, Selina McCoyEconomic and Social Research Institute
Ěý
NAPD Annual Symposium
“Equity in our Schools: Does the system deliver for all young people?”AI and Academic Writing, Short Term Course in Academic Writing and Publicatio...



AI and Academic Writing, Short Term Course in Academic Writing and Publicatio...Prof. (Dr.) Vinod Kumar Kanvaria
Ěý
AI and Academic Writing, Short Term Course in Academic Writing and Publication, UGC-MMTTC, MANUU, 25/02/2025, Prof. (Dr.) Vinod Kumar Kanvaria, University of Delhi, vinodpr111@gmail.comOne Click RFQ Cancellation in Odoo 18 - Odoo şÝşÝߣs



One Click RFQ Cancellation in Odoo 18 - Odoo şÝşÝߣsCeline George
Ěý
In this slide, we’ll discuss the one click RFQ Cancellation in odoo 18. One-Click RFQ Cancellation in Odoo 18 is a feature that allows users to quickly and easily cancel Request for Quotations (RFQs) with a single click.Azure Administrator Interview Questions By ScholarHat



Azure Administrator Interview Questions By ScholarHatScholarhat
Ěý
Azure Administrator Interview Questions By ScholarHatFull-Stack .NET Developer Interview Questions PDF By ScholarHat



Full-Stack .NET Developer Interview Questions PDF By ScholarHatScholarhat
Ěý
Full-Stack .NET Developer Interview Questions PDF By ScholarHatInventory Reporting in Odoo 17 - Odoo 17 Inventory App



Inventory Reporting in Odoo 17 - Odoo 17 Inventory AppCeline George
Ěý
This slide will helps us to efficiently create detailed reports of different records defined in its modules, both analytical and quantitative, with Odoo 17 ERP.Blind spots in AI and Formulation Science, IFPAC 2025.pdf



Blind spots in AI and Formulation Science, IFPAC 2025.pdfAjaz Hussain
Ěý
The intersection of AI and pharmaceutical formulation science highlights significant blind spots—systemic gaps in pharmaceutical development, regulatory oversight, quality assurance, and the ethical use of AI—that could jeopardize patient safety and undermine public trust. To move forward effectively, we must address these normalized blind spots, which may arise from outdated assumptions, errors, gaps in previous knowledge, and biases in language or regulatory inertia. This is essential to ensure that AI and formulation science are developed as tools for patient-centered and ethical healthcare.Administrative bodies( D and C Act, 1940



Administrative bodies( D and C Act, 1940P.N.DESHMUKH
Ěý
These presentation include information about administrative bodies such as D.T.A.B
CDL AND DCC, etc.Odoo 18 Accounting Access Rights - Odoo 18 şÝşÝߣs



Odoo 18 Accounting Access Rights - Odoo 18 şÝşÝߣsCeline George
Ěý
In this slide, we’ll discuss on accounting access rights in odoo 18. To ensure data security and maintain confidentiality, Odoo provides a robust access rights system that allows administrators to control who can access and modify accounting data. Oral exam Kenneth Bech - What is the meaning of strategic fit?



Oral exam Kenneth Bech - What is the meaning of strategic fit?MIPLM
Ěý
Presentation of the CEIPI DU IPBA oral exam of Kenneth Bech - What is the meaning of strategic fit? Functional Muscle Testing of Facial Muscles.pdf



Functional Muscle Testing of Facial Muscles.pdfSamarHosni3
Ěý
Functional Muscle Testing of Facial Muscles.pdfAI and Academic Writing, Short Term Course in Academic Writing and Publicatio...



AI and Academic Writing, Short Term Course in Academic Writing and Publicatio...Prof. (Dr.) Vinod Kumar Kanvaria
Ěý
Computer ethics
- 1. Doing the Right Thing Computer Ethics
- 3. Plagiarism • Downloading somebody else’s works as if it were your own. • Plagiarism is a serious offense. The more famous you get, the more you’re at risk. • In college writing, it’s fine to make use of someone else’s effort as long as you use your own words and give credit. • Plagiarizing copyrighted materials is called copyright infringement
- 4. Privacy & Encryption • Privacy – refers to an individual’s ability to restrict or eliminate the collection, use, and sale of confidential personal information. • Encryption – refers to a coding or scrambling process by which a message is rendered unreadable by anyone except the intended recipient. Coded Message
- 5. Cipher text • Refers to a coded message Decode the message below V YBIR LBH ORYC BRX WRR A B C D E F J H I J K L M N O P Q R S T U V W X Y Z
- 6. Global Unique Identifiers (GUID) • A unique identification number that is generated by a computer hardware component or a program.
- 7. Privacy at Work. (Things to Remember) • Except in the case of an emergency, never use your employer’s telephone system for professional calls. Make all such calls from a pay telephone. • Never use the e-mail account your employer gives you for professional purposes. Get your own account with an Internet Service Provider (ISP), and be sure to send and receive all personal mail from your home computer. • Assume that everything you do while you’re at work – whether it’s talking on the phone, using your computer, taking a break, or chatting with co-workers is being monitored and recorded.
- 8. Protecting your Privacy Online To safeguard your privacy on the internet do the following: • Browse anonymously by surfing from sites such as “The Anonymizer” or “The-cloak” • Disable cookies on your Web browser or use cookie management software, such as Junkbuster. • Use a “throw-away” e-mail address on a free Web-based service such as Hotmail. • Tell children not to divulge any personal information to strangers online without first asking permision. • Don’t fill out site registration form unless you see a privacy policy statement indicating that the information you supply will not be sold to third parties.
- 9. Computer Crime: Tools and Techniques • Password guessing • Shoulder surfing • Packet sniffers • Dumpster diving • Social Engineering • Superuser status
- 10. SALAMI SHAVING AND DATA • Salami Shaving – a programmer alters a program so that it subtracts a very small amount of money from each account. • Data Diddling- insiders modify data so that it’s difficult or impossible to tell that they’ve stolen fund or equipment.
- 11. COMPUTER VIRUSES • Computer Virus - a computer program that can copy itself and infect a computer without permission or knowledge of the user. • File infectors – attached themselves to a program file. • Boot sector virus – propagates by means of in infected program, but it installs itself at the beginning of a hard drive. • Macro Virus – Take advantage of the automatic command execution capabilities • Executable File- program that can run on a given computer Platform. • E-mail Attachment-a computer file that is included with an e-mail message. Plain Text – safe file
- 12. MORE ROGUE PROGRAMS • Time bombs- also called logic bombs, are designed to sit harmlessly on a system until a certain event or set of circumstance causes the program to become active. • Worm – resembles a computer virus in that it can spread from one computer to another. Can propagate over a computer network. • Trojan Horse – is disguised as a useful program, but it contains hidden instructions to perform a malicious task instead. Sometimes a trojan horse is disguised as a game or a utility program that users will find appealing.
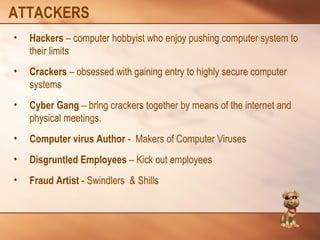
- 13. ATTACKERS • Hackers – computer hobbyist who enjoy pushing computer system to their limits • Crackers – obsessed with gaining entry to highly secure computer systems • Cyber Gang – bring crackers together by means of the internet and physical meetings. • Computer virus Author - Makers of Computer Viruses • Disgruntled Employees – Kick out employees • Fraud Artist - Swindlers & Shills
- 14. Cyberstalkers & Sexual Predators • Cyberstalking – define as the use of the internet e-mail, and other electronic communication media to harass or threaten a person repeatedly. • Cybersex - a virtual sex encounter in which two or more persons connected remotely via a computer network send one another sexually explicit messages describing a sexual experience. It is a form of role-playing in which the participants pretend they are having actual sexual relations
- 15. INFORMATION WARFARE • IW – the use of information technologies to corrupt or destroy an enemy’s information and industrial infrastructure. • Electronic Warfare – The use of electronic device to destroy or damage computer system. • Network Warfare – hacker-like attacks on the nation’s network infrastructure, including the electronic banking system. • Structural Sabotage – Attacks on information systems that support transportation, finance, energy and telecommunication.
- 16. Spotlight Ethics • Plagiarism – The presentation of Somebody else’s work as if it were your own. • At some colleges, plagiarism can get you thrown out of school on the first offense. • Copyright Infringement – Plagiarizing copyrighted material.
- 17. Ten Commandments for Computer Ethics 1. Thou shalt not use computer to harm other people. 2. Thou shalt not interfere with other people’s computer work. 3. Thou shalt not snoop around in other people’s files. 4. Thou shalt not use a computer to steal. 5. Thou shalt not use a computer to bear false witness. 6. Thou shalt not copy or use propriety software for which you have not paid. 7. Thou shalt not use other people’s computer resources without authorization or proper compensation. 8. Thou shalt not appropriate other people’s intellectual output. 9. Thou shalt think about the social consequences of the program you write or the system you design. 10. Thou shalt use a computer in ways that show consideration and respect for your fellow Humans.
- 18. Summary • Respecting yourself • Respecting Others • Respecting Academic Integrity






