Computer security risks
- 2. Computer Security Risks • A computer security risk is any event or • action that could cause a loss of or damage to • computer hardware, software, data, information, • or processing capability
- 3. Cybercrime Any illegal act involving a computer generally is referred to as a computer crime. The term cybercrime refers to online or Internet-based illegal acts. Software used by cybercriminals sometimes is called crimeware. Today, cybercrime is one of the FBI’s top three priorities.
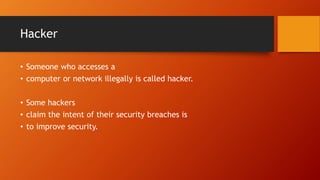
- 4. Hacker • Someone who accesses a • computer or network illegally is called hacker. • Some hackers • claim the intent of their security breaches is • to improve security.
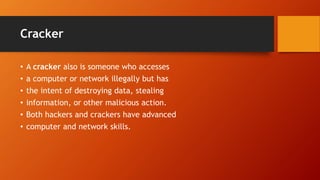
- 5. Cracker • A cracker also is someone who accesses • a computer or network illegally but has • the intent of destroying data, stealing • information, or other malicious action. • Both hackers and crackers have advanced • computer and network skills.
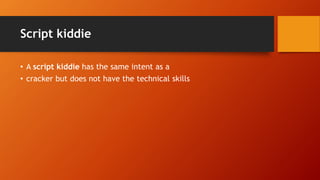
- 6. Script kiddie • A script kiddie has the same intent as a • cracker but does not have the technical skills
- 7. Cyberextortionist (CRIMINAL LAW obtaining something by illegal threats) A cyberextortionist is someone who uses e-mail as a vehicle for extortion. These perpetrators send an organization a threatening e-mail message indicating they will expose confidential information, exploit a security flaw, or launch an attack that will compromise the organization’s network — if they are not paid a sum of money.
- 8. Cyberterrorist • A cyberterrorist is someone who uses the • Internet or network to destroy or damage computers for political reasons. The • cyberterrorist might target the nation’s air • traffic control system, electricity-generating companies, or a telecommunications infrastructure. • The term, cyberwarfare, describes an attack whose goal ranges from disabling a government’s computer network to crippling • a country. Cyberterrorism and cyberwarfare usually require a team of highly skilled
- 9. Internet and Network Attacks • Information transmitted over networks has a • higher degree of security risk than information • kept on an organization’s premises. In an organization, • network administrators usually take • measures to protect a network from security • risks. On the Internet, where no central administrator • is present, the security risk is greater.
- 10. Security service • To determine if your computer is vulnerable • to an Internet or network attack, you • could use an online security service. An online • security service is a Web site that evaluates • your computer to check for Internet and e-mail • vulnera bilities
- 11. How virus can spread through Email Message
- 12. Safeguards against Computer Viruses and Other Malware • Methods that guarantee a computer or • network is safe from computer viruses and other • malware simply do not exist. Users can take several • precautions, however, to protect their home • and work computers and mobile devices from • these malicious infections
- 13. Precautions • Do not start a computer with removable media inserted in the drives or plugged in the ports. • For example, optical disc drives should be empty, and a USB port should not contain a USB flash • drive. During the startup process, a computer • may attempt to execute the boot sector on media • in certain drives and ports. Even if the attempt is • unsuccessful, a virus on the boot sector of removable • media can infect the computer’s hard disk. • If you must start the computer with media in a • drive or port, be certain the media are uninfected • or from a trusted source
- 14. Precautions • Never open an e-mail attachment unless you • are expecting the attachment and it is from a • trusted source. If the e-mail message is from an • unknown source or untrusted source, delete the • e-mail message immediately — without opening • or executing any attachments.
- 15. Precautions • Some viruses are hidden in macros, which • are instructions saved in software such as a word • processing or spreadsheet program. In programs • that allow users to write macros, you should set • the macro security level so that the application • software warns users that a document they are • attempting to open contains a macro
- 16. Precautions • Users should install an antivirus program and • update it frequently. • An antivirus program protects a computer against • viruses by identifying and removing any computer • viruses found in memory, on storage media, • or on incoming files.
- 17. Precautions • One technique that antivirus programs use to • identify a virus is to look for virus signatures. A • virus signature, also called a virus definition, is • a known specific pattern of virus code. Computer • users should update their antivirus program’s • signature files regularly