Contriber - Notifications Tutorial
0 likes336 views
View this presentation to learn about and the different types of Notifications that Contriber offers its users.
1 of 26
Download to read offline







Recommended
Collaboration in science



Collaboration in sciencecolwilliamson
╠²
This document discusses collaboration and cheating in science. It defines collaboration as working together, while cheating involves plagiarizing the work of others or violating rules. Four scenarios are presented where students could unintentionally engage in cheating: 1) copying a classmate's notes for a test correction, 2) using a lab partner's calculations without understanding, 3) copying data tables and graphs from a partner's lab report, 4) borrowing conclusions from a partner's lab report. The document advises verbally helping peers without showing work and making time to work with teachers rather than classmates to avoid accidental cheating.Lab3



Lab3AndersonBussing
╠²
This lab document covers measuring variability due to instruments and making box plots. It instructs students to bring their lab manual, print materials before class, and submit individual work. The point is that imprecise instruments like a yardstick marked every 6 inches can affect measurements, and randomizing orders reduces bias. Students should learn how instrument variability impacts results and how to calculate statistics like median, quartiles, standard deviation to make box plots from a data set.IT Group Silverstone Race Day 



IT Group Silverstone Race Day emilyvforrest
╠²
On Sunday 27th September, IT Group welcomed guests to watch the British Touring Car Championships and the MSA Formula Championships at Silverstone. 

Las tic Anamarisolderas
╠²
El documento describe las tecnolog├Łas de la informaci├│n y la comunicaci├│n (TIC), sus ventajas como el incremento de la producci├│n y los beneficios que brindan, as├Ł como sus desventajas como la falta de privacidad y el aislamiento. Explica que las TIC se utilizan en sectores como la educaci├│n, la salud y las empresas, y menciona algunos tipos de TIC como las redes, terminales y servicios, as├Ł como razones para usarlas como la alfabetizaci├│n digital y la innovaci├│n educativa.Develop Yourself and Become a Leader with 13 Recommendations from Boris Grun...



Develop Yourself and Become a Leader with 13 Recommendations from Boris Grun...Contriber
╠²
Listen to the full episode of Unlock PeopleŌĆÖs Potential with Boris Grundl: https://www.contriber.com/result-oriented-leadership-boris-grundl/
WeŌĆÖre all struggling to adopt the right mindset. How can you embrace your personal growth?
ItŌĆÖs not easy to find effective ways of developing yourself.
You might want to ask yourself:
What actions can I take to start achieving success in my life?
What can I do to become a better leader?
How can I overcome obstacles?
We interviewed a top leadership coach Boris Grundl. At the age 25, Boris Grundl had an accident that led him to become paralyzed. But despite all his condition, he became a successful marketing and sales director. Since then, he has written five books and shared his experiences in seminars and coaching sessions. Guerric de Ternay talked to Boris Grundl about finding oneŌĆÖs strengths, reaching full potential, and thinking like a leader.
Dig into the presentation to learn more from Boris GrundlŌĆÖs inspiring experience. Start implementing his advice to boost your personal growth and improve your leadership skills.
Listen to the full episode of Unlock PeopleŌĆÖs Potential with Boris Grundl: https://www.contriber.com/result-oriented-leadership-boris-grundl/ 

Trata de personas Anamarisolderas
╠²
La trata de personas es el comercio ilegal de personas con fines de esclavitud, explotaci├│n sexual u otros trabajos forzados. Involucra el reclutamiento, transporte o recepci├│n de personas a trav├®s de amenazas, coerci├│n o enga├▒o con el objetivo de explotarlas. Las v├Łctimas de trata de personas no pueden ser judicializadas por delitos cometidos debido a su experiencia y los estados deben proteger su privacidad e identidad.9 Positioning Tips from Marketing Guru Laura Ries That Will All Dramatically ...



9 Positioning Tips from Marketing Guru Laura Ries That Will All Dramatically ...Contriber
╠²
Listen to the full episode of Unlock PeopleŌĆÖs Potential with Laura Ries:
https://www.contriber.com/brand-positioning-laura-ries/
Companies often make positioning mistakes such as promoting too many benefits, lacking focus, or changing the focus too frequently and, therefore, losing the position they had in the customerŌĆÖs mind. This kind of setbacks can be avoided.
Have you ever wondered:
How should a brand build a position for a new product/service?
What to do when you have to compete with a leader in your market?
What is the main purpose advertising should be used for?
How you can use a Visual Hammer and a Battlecry to reinforce your position in a market?
We interviewed a leading brand strategist, Laura Ries, who is also a bestselling author, sought-after speaker, and popular television personality. Guerric de Ternay talked to Laura about brand positioning, marketing strategy, competing with a market leader, using Visual Hammer, and many other interesting marketing topics.
Dig into the presentation to learn from the 11 tips Laura Ries shared with us and start improving your brandŌĆÖs position today.
Listen to the full episode of Unlock PeopleŌĆÖs Potential with Laura Ries:
https://www.contriber.com/brand-positioning-laura-ries/ . Junk Email



Junk Emailfosterstac
╠²
This document provides a training course on using Outlook 2003's junk email filter. The course includes two lessons: 1) Getting familiar with the junk email filter and how it works, and 2) Learning how to guard your privacy to avoid receiving more junk email. It discusses features like the junk email folder, safe and blocked senders lists, and options to control automatic download of images in emails. The document contains sample test questions to check understanding.Junk Email



Junk Emailfosterstac
╠²
This document summarizes an Outlook 2003 training course on using the junk email filter. The course covers how the filter works, managing safe and blocked sender lists, and privacy settings regarding blocked images. It includes sample questions to test understanding and suggests practicing with Outlook 2003. The goal is to help users make full use of the junk email filter to reduce spam in their inbox.Email spamming



Email spamminguno Assignment Help
╠²
Spam mail is unsolicited commercial email. It is sometimes used to spread computer viruses that can cause recipients to lose computer data. When classifying an email as spam, a mail service examines the email headers which contain information about the origination, routing, and receipt of the message. The most reliable header is "Received" as it lists the servers through which the message traveled to reach the recipient. Reading the headers from bottom to top shows where the email originated.A review of spam filtering and measures of antispam



A review of spam filtering and measures of antispamAlexander Decker
╠²
This document discusses spam filtering and measures to reduce spam. It begins by defining spam as unsolicited email messages. It then discusses the problems caused by increasing spam volumes, such as becoming a security issue for businesses. Various types of spam are described, like text spam, image spam, and content-based spam. Methods for filtering spam are outlined, including collecting spam/anti-spam data, preprocessing to reduce noise, identifying bad senders, applying classification tools to specified content types, and storing results. Techniques for anti-spam filtering mentioned include white lists, rule-based filtering, content-based filtering, and pattern detection.Online Safety Data Privacy and Email Basics Digital Literacy Fundamentals.pptx



Online Safety Data Privacy and Email Basics Digital Literacy Fundamentals.pptxExcellence Foundation for South Sudan
╠²
Online Safety Data Privacy and Email Basics Digital Literacy Fundamentals a presentation by Ulak Matthew Thomas, a lecturer at Starford International University in Juba South Sudan Slack tips



Slack tipsCarolina Cornish
╠²
All of our Tonto HR clients get sick of us singing the praises of SLACK and how it can have a positive impact on team culture irrespective of your organisational size.
One of our favourite clients DoseMe rolled out Slack a few months back and they LOVE IT.
Have a look at a 27 tips one of their devs wrote to make the most of this this super cheap, super effective communication and team-building tool.
Carolina
Introduction to121connections



Introduction to121connectionsDonald Scheske
╠²
This document provides an overview of how to use the 121 Connectors email response system. It summarizes the key areas of the system:
1. Logging in and exploring the different tabs on the home page such as forums, resources, and FAQs.
2. The different sections under "My Tools" including messages, queues, and inquirers that allow managing conversations.
3. How to access and respond to new inquirer assignments using template responses for different inquirer statuses and questions.
4. An overview of the message inbox and folders for storing conversations.
5. Alert indicators for new messages and how to access inquirer profiles from the messages section.Beginner Android Training



Beginner Android TrainingDennis Crouse
╠²
This a short presentation on cell phones and some tablets running the Android operating system.
You will benefit from this slideshow if you currently know little to nothing about Android phones/tablets.7 module web based email



7 module web based emailConnectYourCommunity
╠²
The document provides an overview of email including what it is, how it compares to regular mail, advantages and disadvantages, what is needed to set up an email account, how to avoid spam, and email etiquette and safety tips. It explains that email allows quick electronic communication by sending messages over the internet from one computer to another. While free and convenient, email also carries risks like spam and scams that users need to be aware of. The document provides instructions for creating a Gmail email account, including choosing a username and password.7 module web based email



7 module web based emailRozell Sneede
╠²
The document provides an overview of email including what it is, how it compares to regular mail, advantages and disadvantages, what is needed to set up an email account, how to avoid spam, and email etiquette and safety tips. It explains that email allows quick electronic communication by sending messages from one computer to another over the internet. To have an email account, a user needs a computer, internet connection, and can sign up through many free providers like Gmail which provides a username, password, and email address. The document provides guidance on email best practices.7 module web based email



7 module web based emailConnectYourCommunity
╠²
The document provides an overview of email including what it is, how it compares to regular mail, advantages and disadvantages, what is needed to set up an email account, how to avoid spam, and email etiquette and safety tips. It explains that email allows quick electronic communication by sending messages from one computer to another over the internet. To have an email account, a user needs a computer, internet connection, and can sign up through many free providers like Gmail which provides a username, password, and email address. The document provides guidance on email best practices.Inbox Zero & Task Management



Inbox Zero & Task ManagementMatteo Talmassons
╠²
This document discusses strategies for achieving Inbox Zero and effective task management. It recommends reading all emails at once and taking action by responding, delegating, deferring, or deleting. Deferred tasks should be recorded in a to-do list or calendar. Effective communication, both virtual and in-person, is key to delegating and involving others. All tasks and actions should be tracked and closed out once completed to maintain Inbox Zero. Daily notes and a to-do list help prioritize and manage tasks over time.OBHT electronic comm



OBHT electronic commpascastpt
╠²
This document discusses various electronic communication methods used in organizations. It covers email which over 70% of organizational communication is done through due to its efficiency. However, email messages can often be misinterpreted without body language cues. Instant messaging and text messaging allow for real-time short messages. Social networking software like MySpace and Facebook connect people globally but require caution about privacy. Blogs and video conferencing are also electronic methods being used more for business communication.MS Outlook MCQ Important Questions and Answers



MS Outlook MCQ Important Questions and AnswersSONU HEETSON
╠²
MS outlook MCQ Questions and answers. Microsoft outlook MCQs PDF for competitive exams.Send Your First Text Message



Send Your First Text MessageLisa Lindsay
╠²
This document provides instructions for sending and receiving text messages, including:
- The basics of text messaging and why it's useful to learn
- How much text messages typically cost and how to avoid excess charges
- How to send a text message by entering a phone number or contact name and composing a message
- How to read and reply to received text messages
- Tips for safe texting practices like not sharing your number widely or texting while driving
- An invitation to practice texting skills by sending messages to a library reference number.Important point to write business e-mail



Important point to write business e-mailsayuri tanaka
╠²
This document provides tips and guidelines for writing effective business emails. It advises including a clear and descriptive subject line to help recipients identify the email's contents. Short promotional messages in the subject line may be flagged as spam. The email should use a casual but professional tone and include contact information. Good email etiquette, such as quoting responses, should be followed. Overall, the document stresses the importance of business emails being clear, concise and standing out from the large volume of emails people receive daily.Cyber security and emails presentation



Cyber security and emails presentationWan Solo
╠²
Cyber security is important to protect sensitive information from unauthorized access. The document discusses why cyber security is important, common cyber security terms, how email clients work, why email attachments can be dangerous, steps to protect yourself and others from email threats, benefits of blind carbon copy (BCC) emails, reducing spam emails, general cyber security tips, and notes that absolute security is impossible to achieve.How to use Email Effectively at workplace



How to use Email Effectively at workplacedeineshd
╠²
Sharing my workplace presentation that will help you use email effectively at your workplace. Even useful when you communicate with the clients.Using Your Phone



Using Your Phonejlpeirce
╠²
This presentation will show you how to hook-up and use your classroom telephone as well as use Communicator to make calls with it.Integrity e-commerce Trends FinTech 2025



Integrity e-commerce Trends FinTech 2025Ed Morrissey
╠²
A brief presentation given during StL TechWeek's 2025 Fintech Summit on the lasting impact of the Covid pandemic on shopper behavior.More Related Content
Similar to Contriber - Notifications Tutorial (20)
Junk Email



Junk Emailfosterstac
╠²
This document provides a training course on using Outlook 2003's junk email filter. The course includes two lessons: 1) Getting familiar with the junk email filter and how it works, and 2) Learning how to guard your privacy to avoid receiving more junk email. It discusses features like the junk email folder, safe and blocked senders lists, and options to control automatic download of images in emails. The document contains sample test questions to check understanding.Junk Email



Junk Emailfosterstac
╠²
This document summarizes an Outlook 2003 training course on using the junk email filter. The course covers how the filter works, managing safe and blocked sender lists, and privacy settings regarding blocked images. It includes sample questions to test understanding and suggests practicing with Outlook 2003. The goal is to help users make full use of the junk email filter to reduce spam in their inbox.Email spamming



Email spamminguno Assignment Help
╠²
Spam mail is unsolicited commercial email. It is sometimes used to spread computer viruses that can cause recipients to lose computer data. When classifying an email as spam, a mail service examines the email headers which contain information about the origination, routing, and receipt of the message. The most reliable header is "Received" as it lists the servers through which the message traveled to reach the recipient. Reading the headers from bottom to top shows where the email originated.A review of spam filtering and measures of antispam



A review of spam filtering and measures of antispamAlexander Decker
╠²
This document discusses spam filtering and measures to reduce spam. It begins by defining spam as unsolicited email messages. It then discusses the problems caused by increasing spam volumes, such as becoming a security issue for businesses. Various types of spam are described, like text spam, image spam, and content-based spam. Methods for filtering spam are outlined, including collecting spam/anti-spam data, preprocessing to reduce noise, identifying bad senders, applying classification tools to specified content types, and storing results. Techniques for anti-spam filtering mentioned include white lists, rule-based filtering, content-based filtering, and pattern detection.Online Safety Data Privacy and Email Basics Digital Literacy Fundamentals.pptx



Online Safety Data Privacy and Email Basics Digital Literacy Fundamentals.pptxExcellence Foundation for South Sudan
╠²
Online Safety Data Privacy and Email Basics Digital Literacy Fundamentals a presentation by Ulak Matthew Thomas, a lecturer at Starford International University in Juba South Sudan Slack tips



Slack tipsCarolina Cornish
╠²
All of our Tonto HR clients get sick of us singing the praises of SLACK and how it can have a positive impact on team culture irrespective of your organisational size.
One of our favourite clients DoseMe rolled out Slack a few months back and they LOVE IT.
Have a look at a 27 tips one of their devs wrote to make the most of this this super cheap, super effective communication and team-building tool.
Carolina
Introduction to121connections



Introduction to121connectionsDonald Scheske
╠²
This document provides an overview of how to use the 121 Connectors email response system. It summarizes the key areas of the system:
1. Logging in and exploring the different tabs on the home page such as forums, resources, and FAQs.
2. The different sections under "My Tools" including messages, queues, and inquirers that allow managing conversations.
3. How to access and respond to new inquirer assignments using template responses for different inquirer statuses and questions.
4. An overview of the message inbox and folders for storing conversations.
5. Alert indicators for new messages and how to access inquirer profiles from the messages section.Beginner Android Training



Beginner Android TrainingDennis Crouse
╠²
This a short presentation on cell phones and some tablets running the Android operating system.
You will benefit from this slideshow if you currently know little to nothing about Android phones/tablets.7 module web based email



7 module web based emailConnectYourCommunity
╠²
The document provides an overview of email including what it is, how it compares to regular mail, advantages and disadvantages, what is needed to set up an email account, how to avoid spam, and email etiquette and safety tips. It explains that email allows quick electronic communication by sending messages over the internet from one computer to another. While free and convenient, email also carries risks like spam and scams that users need to be aware of. The document provides instructions for creating a Gmail email account, including choosing a username and password.7 module web based email



7 module web based emailRozell Sneede
╠²
The document provides an overview of email including what it is, how it compares to regular mail, advantages and disadvantages, what is needed to set up an email account, how to avoid spam, and email etiquette and safety tips. It explains that email allows quick electronic communication by sending messages from one computer to another over the internet. To have an email account, a user needs a computer, internet connection, and can sign up through many free providers like Gmail which provides a username, password, and email address. The document provides guidance on email best practices.7 module web based email



7 module web based emailConnectYourCommunity
╠²
The document provides an overview of email including what it is, how it compares to regular mail, advantages and disadvantages, what is needed to set up an email account, how to avoid spam, and email etiquette and safety tips. It explains that email allows quick electronic communication by sending messages from one computer to another over the internet. To have an email account, a user needs a computer, internet connection, and can sign up through many free providers like Gmail which provides a username, password, and email address. The document provides guidance on email best practices.Inbox Zero & Task Management



Inbox Zero & Task ManagementMatteo Talmassons
╠²
This document discusses strategies for achieving Inbox Zero and effective task management. It recommends reading all emails at once and taking action by responding, delegating, deferring, or deleting. Deferred tasks should be recorded in a to-do list or calendar. Effective communication, both virtual and in-person, is key to delegating and involving others. All tasks and actions should be tracked and closed out once completed to maintain Inbox Zero. Daily notes and a to-do list help prioritize and manage tasks over time.OBHT electronic comm



OBHT electronic commpascastpt
╠²
This document discusses various electronic communication methods used in organizations. It covers email which over 70% of organizational communication is done through due to its efficiency. However, email messages can often be misinterpreted without body language cues. Instant messaging and text messaging allow for real-time short messages. Social networking software like MySpace and Facebook connect people globally but require caution about privacy. Blogs and video conferencing are also electronic methods being used more for business communication.MS Outlook MCQ Important Questions and Answers



MS Outlook MCQ Important Questions and AnswersSONU HEETSON
╠²
MS outlook MCQ Questions and answers. Microsoft outlook MCQs PDF for competitive exams.Send Your First Text Message



Send Your First Text MessageLisa Lindsay
╠²
This document provides instructions for sending and receiving text messages, including:
- The basics of text messaging and why it's useful to learn
- How much text messages typically cost and how to avoid excess charges
- How to send a text message by entering a phone number or contact name and composing a message
- How to read and reply to received text messages
- Tips for safe texting practices like not sharing your number widely or texting while driving
- An invitation to practice texting skills by sending messages to a library reference number.Important point to write business e-mail



Important point to write business e-mailsayuri tanaka
╠²
This document provides tips and guidelines for writing effective business emails. It advises including a clear and descriptive subject line to help recipients identify the email's contents. Short promotional messages in the subject line may be flagged as spam. The email should use a casual but professional tone and include contact information. Good email etiquette, such as quoting responses, should be followed. Overall, the document stresses the importance of business emails being clear, concise and standing out from the large volume of emails people receive daily.Cyber security and emails presentation



Cyber security and emails presentationWan Solo
╠²
Cyber security is important to protect sensitive information from unauthorized access. The document discusses why cyber security is important, common cyber security terms, how email clients work, why email attachments can be dangerous, steps to protect yourself and others from email threats, benefits of blind carbon copy (BCC) emails, reducing spam emails, general cyber security tips, and notes that absolute security is impossible to achieve.How to use Email Effectively at workplace



How to use Email Effectively at workplacedeineshd
╠²
Sharing my workplace presentation that will help you use email effectively at your workplace. Even useful when you communicate with the clients.Using Your Phone



Using Your Phonejlpeirce
╠²
This presentation will show you how to hook-up and use your classroom telephone as well as use Communicator to make calls with it.Online Safety Data Privacy and Email Basics Digital Literacy Fundamentals.pptx



Online Safety Data Privacy and Email Basics Digital Literacy Fundamentals.pptxExcellence Foundation for South Sudan
╠²
Recently uploaded (20)
Integrity e-commerce Trends FinTech 2025



Integrity e-commerce Trends FinTech 2025Ed Morrissey
╠²
A brief presentation given during StL TechWeek's 2025 Fintech Summit on the lasting impact of the Covid pandemic on shopper behavior.Tran Quoc Bao Named Top Voice in Healthcare and Vietnam LinkedIn Community by...



Tran Quoc Bao Named Top Voice in Healthcare and Vietnam LinkedIn Community by...Ignite Capital
╠²
In a significant recognition, Tran Quoc Bao has been named the Top Voice in Healthcare and the Healthcare Community in Vietnam on LinkedIn by Favikon. This prestigious accolade highlights Bao's influential role in shaping the digital health landscape, particularly through his impactful presence on the LinkedIn platform.
As a leading figure in the tech and healthcare sectors, Tran Quoc Bao has leveraged social media to drive important conversations, foster innovation, and connect with a global audience. His expertise and insights have resonated with professionals across various industries, making him a key thought leader in the ever-evolving world of digital healthcare.
By harnessing the power of technology and digital platforms, Bao continues to inspire and engage with healthcare professionals, entrepreneurs, and innovators, positioning himself as a trailblazer in both tech and health. This recognition is a testament to his vision and dedication to advancing the intersection of healthcare and technology in Vietnam and beyond.Vision Streategies for Pharmaceutical industries in Entrepreneurship manageme...



Vision Streategies for Pharmaceutical industries in Entrepreneurship manageme...sahilranawade9297
╠²
Information and ways of Vision strategies for Entrepreneurship management
Related to M pharm Industrial pharmacy syllabus
The Rising Influence of Decentralized Energy Networks.docx



The Rising Influence of Decentralized Energy Networks.docxInsolation Energy
╠²
The localized power generation movement revolutionizes how communities produce, access, and utilize electricity. Rather than exclusively depending on conventional grids, private citizens and companies opt for alternative options that provide reliability, efficiency, and affordability.
Advanced SystemCare Pro Crack Download 2025



Advanced SystemCare Pro Crack Download 2025bhutbhijan
╠²
Direct Link Below¤ÄüŌ£ö¤æć
https://upcommunity.net/dl/ŌśØŌśØŌ£ģ¤æē
Note: >> Please copy the link and paste it into Google New Tab now Download link And Enjoy ¤śŹ
Advanced SystemCare Pro is an all-in-one PC optimization utility designed for simplicity and efficiency T-shirt Printing Business New Business Idea



T-shirt Printing Business New Business IdeaSujeetPrajapati16
╠²
Department Of Commerce And Management Indira Gandhi National Tribal University Amarkantak Madhya Pradesh ( IGNTU) (New Business Idea) Course B.com/M.com & B.ba/M.ba Create And making By Sujeet Prajapati B.com 6th Semester And Final Year , Last Year WorldŌĆÖs Most Influential Leaders Transforming the Future, 2025



WorldŌĆÖs Most Influential Leaders Transforming the Future, 2025Worlds Leaders Magazine
╠²
Protais Muhirwa, Founder of ARMIA (Active Refugee & Migrant Integration in Australia), graced the cover of WorldŌĆÖs Leaders Magazine as one of the Worlds Most Influential Leaders Transforming the Future, 2025The Role of Data Analytics in Shaping Leadership Trends_ARL_27 March 2025.pptx



The Role of Data Analytics in Shaping Leadership Trends_ARL_27 March 2025.pptxCharles Cotter, PhD
╠²
The Role of Data Analytics in Shaping Leadership Trends by Dr Charles Cotter at the Africa Rising Leadership Summit and Awards on 27 March 2025. In this keynote presentation Dr Charles highlights three (3) research-based correlations between data analytics and leadership trends (2025 - 2030), namely:
ŌĆó #1. The emergence and conceptualization of Evidence-based Management (EBM) thinking and -practices in transforming x4 organizational pillars into High Performing Organization (HIPO) sub-cultures
ŌĆó #2. The power and value of harnessing data analytics in fuelling Data-driven Leadership best practices
ŌĆó #3. The Future Fit Leadership Code - the four (4) most important currencies that future-fit business leaders trade in, in the context of the Collaborative Intelligence Economy (of the future).
Hinduja Brothers - Pioneers of Global Business and Philanthropy



Hinduja Brothers - Pioneers of Global Business and Philanthropyshiveshmani09
╠²
The Hinduja Brothers are a prominent Indian-born British family who lead the Hinduja Group, a diversified global conglomerate. The four brothers are Gopichand, Prakash, Ashok, and the late Srichand Hinduja. Philanthropy is central to the Hinduja family's values. The Hinduja Foundation supports healthcare and education initiatives in India and the UK. Their philanthropic work includes building hospitals, supporting schools, and providing aid during crises. The Hinduja Brothers have built a legacy of business success and philanthropy, making significant contributions to both the global economy and society.Top 10 Software Development Companies in USA 2025



Top 10 Software Development Companies in USA 2025SoluLab1231
╠²
In todayŌĆÖs business world, a top software development company plays an essential role since it serves as the foundation for innovation and technological advancement. These companies are largely responsible for creating one-of-a-kind solutions that meet specific company needs. Custom software development companies in America provide global firms with several benefits, including increased productivity, gaining a competitive advantage in their respective sectors, optimizing operations, and more.
HRD Support Program in Semiconductor & Advanced Electronics Industries



HRD Support Program in Semiconductor & Advanced Electronics IndustriesThailand Board of Investment North America
╠²
Presented by Mr. Thitidej Tularak, Minister-Counsellor, Office of Higher Education, Science, Research and Innovation, Royal Thai Embassy, Washington DC on April 2, 2025Bitcoin's Future Bitcoin's Future: Michael Saylor Predicts $500 Trillion Market



Bitcoin's Future Bitcoin's Future: Michael Saylor Predicts $500 Trillion Marketmohammadasim74
╠²
Bitcoin is on track to become the world's ultimate store of value, surpassing gold, real estate, and other long-term financial assets. According to MicroStrategy Executive Chairman Michael Saylor, BitcoinŌĆÖsŌĆØ market"capitalization will eventually reach $500 trillion. His forecast is based on increasing capital inflows into the cryptocurrency, signaling a monumental shift from legacy financial systems to a digital money network.Tran Quoc Bao: Asian Healthcare Leader and Top 10 Most Influential Hospital C...



Tran Quoc Bao: Asian Healthcare Leader and Top 10 Most Influential Hospital C...Ignite Capital
╠²
Hospital Planning in Public-Private Partnerships: A Financial Framework for Success
By Dr. Tran Quoc Bao, Healthcare Industry Expert
In the rapidly evolving world of hospital Public-Private Partnerships (PPPs), understanding the underlying financial assumptions is crucial for successful project execution. Dr. Tran Quoc Bao, one of Vietnam's most influential healthcare leaders, emphasizes the importance of a detailed financial model when planning hospital infrastructure through PPPs. This approach helps sponsors, particularly in greenfield projects, estimate capital and operational needs with greater precision.
A key component of this model is the breakdown of construction costs, which are typically estimated at $2,000 per square meter. The model suggests varying space requirements per bed depending on the region: 120m┬▓ in Emerging Markets, 170m┬▓ in Western Europe, and a significantly larger 360m┬▓ in the U.S. These differences reflect regional healthcare standards, and understanding these variations is critical for accurate cost forecasting.
Ongoing capital expenditures (capex) are also a significant consideration. This includes 2.5% for building maintenance and 15% for equipment costs, ensuring that the financial model aligns with real-world expectations. Operating costs per bed typically range from $120,000 to $160,000 annually. This financial framework also includes assumptions about debt-equity ratios (70/30) and a base loan interest rate of 12%, offering insight into project financing.
A vital component of the model is the expected return on equity (ROE), which ranges between 16-18%. This figure provides valuable guidance for investors in understanding the long-term financial sustainability of hospital PPP projects. Moreover, Dr. Bao highlights that upfront capital expenditure subsidies can substantially reduce annual PPP payments, providing governments and sponsors with greater flexibility in structuring agreements.
This comprehensive financial framework offers crucial clarity for hospital PPPs, allowing investors and sponsors to make smarter, more informed decisions about healthcare infrastructure development. By embracing these financial principles, stakeholders can enhance the predictability of costs, optimize resource allocation, and ultimately ensure the success of hospital PPP projects across various markets.Company Profile & SWOT Analysis List.pdf



Company Profile & SWOT Analysis List.pdfRobertPhillips265023
╠²
Product list and brochure of company profile and SWOT analysis reports available on Platform Executive.
Each report is available for purchase online and includes the following sections:
1. Introduction
2. Aims and objectives
3. Scope of the report
4. Target audiences
5. Table of contents
6. Executive summary
7. Overview
8. Key facts
9. Concise history
10. Company description
11. The business model
11.1. Business model canvas
11.2. Value proposition
11.3. Target markets
11.4. Key success factors
12. Industries
13. Key people
14. Management capabilities
15. Key stakeholders
16. The regulatory environment
17. Risk analysis
18. Corporate Social Responsibility (CSR)
19. Ethical considerations
20. Key performance indicators
21. Future market trends
22. Potential synergies
23. Supply chain analysis
24. Financial data
25. Products and/or services
25.1. Customers and cohorts
25.2. Business units
25.3. Major products and services
25.4. Competitive advantages
25.5. Potential new products and innovations
26. Latest Patents
27. Technology as a change agent
28. Innovation score
29. The competitive landscape
30. Competitive Profile Matrix (CPM)
31. Brand strength
32. Sentiment score
33. 7Ps marketing analysis
34. CATWOE analysis
35. MOST analysis
36. PESTLE analysis
37. PorterŌĆÖs Five Forces
38. SWOT analysis
39. 5C analysis
40. ESG analysis
41. Appendices
The SWOT analysis reports are designed for investors, stakeholders, industry analysts, and business executives seeking a deeper understanding of the companyŌĆÖs operations, strategy, financial health, and competitive advantage. They include a wide array of sections that provide a holistic view of the business.Futureproof ondernemen college over impact waardering bij RUG



Futureproof ondernemen college over impact waardering bij RUGErik-Jan Kreuze
╠²
Futureproof businesses and valuation of impact PROFILE FOR FREIGHT FORWARDING INTERNATIONAL BUSINESS IMPORT EXPORT



PROFILE FOR FREIGHT FORWARDING INTERNATIONAL BUSINESS IMPORT EXPORTILHAM GROUP INTERNATIONAL
╠²
ILHAM GROUP INTERNATIONAL
FREIGHT FORWARDING PROFILE Bradley_Jamelia_BSEB_PB1_2025-03 Personal Brand Identity Kit



Bradley_Jamelia_BSEB_PB1_2025-03 Personal Brand Identity KitJABradley1
╠²
Bradley_Jamelia_BSEB_PB1_2025-03 Personal Brand Identity KitHRD Support Program in Semiconductor & Advanced Electronics Industries



HRD Support Program in Semiconductor & Advanced Electronics IndustriesThailand Board of Investment North America
╠²
Contriber - Notifications Tutorial
- 2. There are three different types of notifications in Contriber. You can use all of them at once OR none of them at all. Workspace Notifications ...starts at slide 3 These types of notifications appear on your workspace and indicate how many messages have been left in various flows. Desktop Notifications ...starts at slide 14 These types of notifications display on your desktop. These are helpful in situations when you are not currently viewing your workspace, but want to know immediately when new activity takes place. Email Notifications ...starts at slide 21 These types of notifications are sent to your email. You have the option of receiving email notifications instantly or daily.
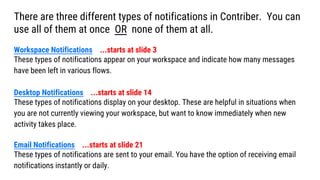
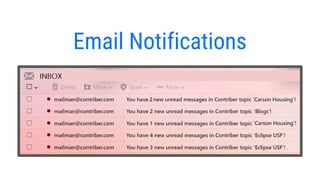
- 4. Blue Notification This notification indicates that there is 1 unread message in the ŌĆśWater TestsŌĆÖ flow.
- 5. Red Notification This notification indicates that there are 3 messages in the ŌĆśGround TestsŌĆÖ flow. At least one of the messages has your name included.
- 6. @Red Notification This notification indicates that there are 2 messages in the ŌĆśDesign 1ŌĆÖ flow. At least one of the messages has been addressed to you with an elevated priority.
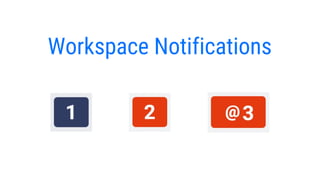
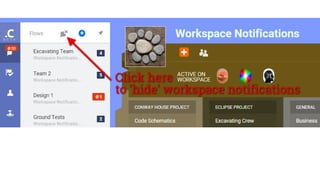
- 7. A workspace showing the 3 different types of notifications.
- 8. **Useful tip** You can ŌĆśhideŌĆÖ Workspace notifications if they are distracting to you. Then...
- 10. And presto! Workspace notifications are ŌĆśhiddenŌĆÖ
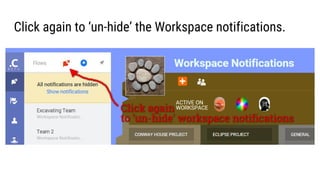
- 11. Click again to ŌĆśun-hideŌĆÖ the Workspace notifications.
- 12. The user can see the workspace notifications again!
- 13. Detailed look at Workspace notifications If a user leaves a message in a flow, all persons using that flow will receive a notification. It will either be Blue, Red, or @Red Blue If a message is left in a flow, all persons using that flow will receive a blue notification. Red If you type a person(s) name in the message, those person(s) will receive a red notification and everyone else using the flow will receive a blue notification. For example: WeŌĆÖre meeting with Mike and Lisa tomorrow at 9am. In this example, Mike and Lisa will receive red notifications and everyone else using the flow will receive blue notifications. This type of tagging can be used to indicate that a message is important, but not mission critical. @Red If you type the @ symbol before a person(s) name in a message, those person(s) will receive an @Red notification and everyone else using the flow will receive a blue notification. For example: @Mike and @Lisa, please meet with us tomorrow at 9am. In this example, Mike and Lisa will receive @red notifications and everyone else using the flow will receive blue notifications. This type of tagging is useful when the message is very urgent for a particular person(s) to read.
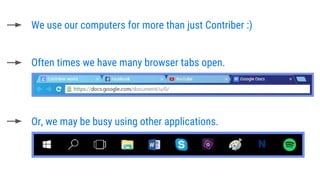
- 15. We use our computers for more than just Contriber :) Often times we have many browser tabs open. Or, we may be busy using other applications.
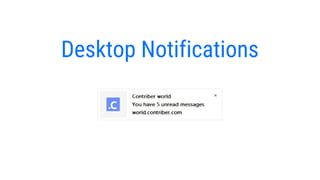
- 16. If you have opened Contriber, but are not currently viewing your workspace (perhaps you are watching a YouTube video), you can choose to be notified immediately when new activity occurs on your workspace(s) using ŌĆśdesktop notificationsŌĆÖ.
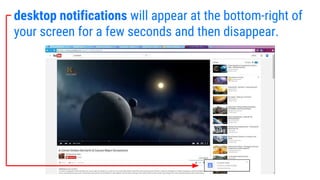
- 17. desktop notifications will appear at the bottom-right of your screen for a few seconds and then disappear.
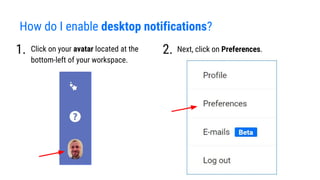
- 18. How do I enable desktop notifications? Click on your avatar located at the bottom-left of your workspace. 1. 2. Next, click on Preferences.
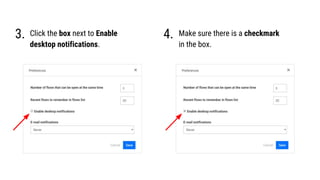
- 19. Click the box next to Enable desktop notifications. 4.3. Make sure there is a checkmark in the box.
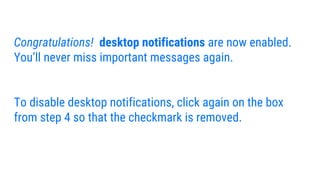
- 20. Congratulations! desktop notifications are now enabled. YouŌĆÖll never miss important messages again. To disable desktop notifications, click again on the box from step 4 so that the checkmark is removed.
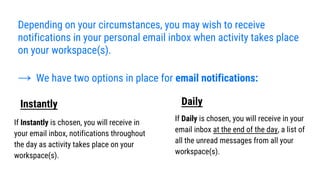
- 22. Depending on your circumstances, you may wish to receive notifications in your personal email inbox when activity takes place on your workspace(s). ŌåÆ We have two options in place for email notifications: If Instantly is chosen, you will receive in your email inbox, notifications throughout the day as activity takes place on your workspace(s). If Daily is chosen, you will receive in your email inbox at the end of the day, a list of all the unread messages from all your workspace(s). Instantly Daily
- 23. How do I enable email notifications? Click on your avatar located at the bottom-left of your workspace. 1. 2. Next, click on Preferences.
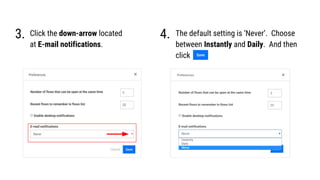
- 24. Click the down-arrow located at E-mail notifications. 4.3. The default setting is ŌĆśNeverŌĆÖ. Choose between Instantly and Daily. And then click
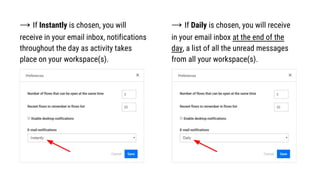
- 25. ŌåÆ If Instantly is chosen, you will receive in your email inbox, notifications throughout the day as activity takes place on your workspace(s). ŌåÆ If Daily is chosen, you will receive in your email inbox at the end of the day, a list of all the unread messages from all your workspace(s).
- 26. Congratulations! Regardless of the option you chose (Instantly or Daily), you are now set up to receive email notifications. Remember, you can always revert back to not receiving email notifications by choosing ŌĆśNeverŌĆÖ in the email notifications box.





