Cryptography
Download as ppt, pdf1 like456 views
The document provides an overview of cryptography, detailing its history, definitions, and methods such as the Caesar cipher and permutation cipher. It discusses the significance of cryptography in secure communication, highlighting advancements from ancient techniques to modern applications in IT and cybersecurity. Additionally, it emphasizes the role of cryptography in strong authentication and wireless communication security.
1 of 50
Downloaded 14 times







































Ad
Recommended
▒╩░∙▒▓§▒▓į│┘▓╣│”Š▒├│▓į1
▒╩░∙▒▓§▒▓į│┘▓╣│”Š▒├│▓į1alvarooo10
╠²
This diagram shows the main components of a computer system including the microprocessor, chipset, memory slots, and expansion slots. The microprocessor connects to the chipset, which manages communication between the CPU and other components like memory and expansion cards. Random access memory can be installed in multiple slots to store and retrieve data for processing by the CPU.A TLS Story
A TLS Storyereddick
╠²
Transport Layer Security (TLS) is a cryptographic protocol that provides secure communication over the internet. It evolved from the Secure Sockets Layer (SSL) protocol. TLS allows for server authentication through X.509 certificates signed by a trusted certificate authority. It also enables optional client authentication and negotiation of encryption algorithms and cryptographic keys to establish an encrypted connection. This ensures confidentiality, integrity, and authentication of data transmitted over the insecure network.History of cryptography
History of cryptographyFarah Shaikh
╠²
The document provides a history of cryptography from ancient times to modern day. It describes early manual encryption techniques used by ancient Greeks and Romans. In the Middle Ages, Arabic scholar Al-Kindi developed frequency analysis to break ciphers. During the Renaissance period, the polyalphabetic cipher was introduced. In World War 1 and 2, mechanical encryption machines like the Enigma and SIGABA were widely used. Modern cryptography began with Claude Shannon's mathematical foundations and the introduction of the Data Encryption Standard (DES) in the 1970s. Public key cryptography was then introduced in the 1970s through Diffie-Hellman key exchange.The Engima Cipher
The Engima Cipherguestfaf89d
╠²
The document provides an overview of the Enigma cipher machine used by Germany in World War II to encrypt military communications. It describes the key components of the Enigma machine, including the plugboard, rotors, and reflector. It also discusses how codebreakers at Bletchley Park were able to decrypt Enigma messages by finding patterns and weaknesses in the German encryption methods.Security Systems for Digital Data - Paper
Security Systems for Digital Data - PaperBernhard Hofer
╠²
The document presents a detailed overview of cryptography, focusing on its history, terminology, and methods for securing digital data through encryption. It discusses both symmetric (private key) and asymmetric (public key) systems, their advantages and drawbacks, and emphasizes the importance of cryptography in ensuring privacy on the internet. The paper also touches on practical applications of encryption, challenges in password security, and future developments like quantum cryptography.Security Systems for Digital Data
Security Systems for Digital DataBernhard Hofer
╠²
The document discusses the evolution and current state of cryptography, detailing both symmetric and asymmetric key systems and their applications in securing digital data. It emphasizes the importance of cryptography for maintaining privacy over the internet and introduces quantum cryptography as a novel approach. The document also highlights the vulnerabilities of traditional systems, particularly concerning brute force attacks.Fundamentals of cryptography
Fundamentals of cryptographyHossain Md Shakhawat
╠²
The document provides an overview of cryptography, detailing its definition, historical development, and the processes of encryption and decryption. It explains key concepts including symmetric and asymmetric cryptography, the importance of confidentiality, integrity, authentication, and non-repudiation, as well as various cryptographic algorithms and attacks. The document emphasizes the role of cryptography in secure communication and its applications in modern technology.enigma cipher machine
enigma cipher machineAryan Raj
╠²
The document discusses the history and technology of the Enigma cipher machine. It describes how the Enigma machine worked using rotors to encrypt messages, giving it a very large number of possible encryption keys. It then discusses how the Enigma was adopted by German military in WWII and the efforts by Polish and British codebreakers to decrypt messages. Breaking the naval Enigma code in 1941 was a turning point in the Battle of the Atlantic. The decryption efforts involved thousands of people and early computers like the Bombe machine.Cryptography, Cryptology, Encryption and types
Cryptography, Cryptology, Encryption and typessowaibakhan3
╠²
The document discusses cryptography, its definitions, advantages, and historical context, emphasizing its role in securing information by encoding messages to ensure confidentiality, authentication, integrity, and non-repudiation. It covers types of ciphers such as the Caesar shift cipher and Vigen├©re cipher, detailing their encryption processes and weaknesses, alongside the concept of the one-time pad as a theoretically unbreakable encryption method. Additionally, it highlights key terminology and principles associated with cryptography and cryptosystems.Computer systems security 7-cryptography.ppt
Computer systems security 7-cryptography.pptstephen972973
╠²
The document discusses the key components of computer security communications, particularly focusing on the requirements for secure communication such as secrecy, authentication, and message integrity. It introduces various cryptographic techniques including symmetric and asymmetric encryption methods, their algorithms, and associated security features, along with the concept of key management and vulnerabilities such as man-in-the-middle attacks. Additionally, it covers authentication mechanisms and protocols used to validate identities and protect data integrity in communications.Cryptography & Steganography
Cryptography & SteganographyAnimesh Shaw
╠²
The document presents a comprehensive overview of cryptography and steganography, discussing its definition, history, key terminologies, types, and algorithms such as RSA and DES. It highlights the importance of cryptography in securing communications, ensuring data integrity, privacy, and authentication. Additionally, it contrasts symmetric and public-key cryptography while explaining key distribution challenges and types of encryption systems.Cryptography.pptxhis document provides an overview of cryptography. It define...
Cryptography.pptxhis document provides an overview of cryptography. It define...researchcollabarator
╠²
The document provides an introduction to cryptography, defining it as a method for secure data storage and transmission. It discusses the history, techniques, and terminology relevant to cryptography, including different encryption methods like symmetric and asymmetric keys. Additionally, it highlights various applications of cryptography in everyday technology, such as e-commerce and electronic voting.Introduction to Cryptography
Introduction to CryptographyMd. Afif Al Mamun
╠²
Cryptography is the practice of securing communication and information by converting plaintext into ciphertext. The document provides an introduction to cryptography including its history from ancient times to the present. It discusses terminology like plaintext, encryption, ciphertext, decryption, and keys. Symmetric key cryptography uses a single key for encryption and decryption while asymmetric key cryptography uses two different keys. Examples of symmetric methods are DES, 3DES, AES, and RC4, while RSA is a common asymmetric method. Applications of cryptography include ATMs, email passwords, e-payments, e-commerce, electronic voting, defense services, securing data, and access control.Computer Security Chapter III.pdf
Computer Security Chapter III.pdfHarrisentertainment
╠²
This document provides an overview of cryptography and encryption techniques. It discusses the basic cryptographic terms and historical background of cryptography. It then describes different cipher techniques including transposition cipher and substitution cipher. It also discusses conventional encryption algorithms such as DES, AES, and RSA. Symmetric key cryptography and public key cryptography are explained. The document also covers digital signatures, cryptanalysis, and cryptographic systems in general.Cryptography and network security Nit701
Cryptography and network security Nit701Amit Pathak
╠²
The document provides an extensive overview of cryptography and network security, covering various types of cryptography, key algorithms, and their applications in securing communication. It discusses both symmetric and asymmetric cryptography, detailing their mechanisms, advantages, and drawbacks. Key concepts such as encryption, decryption, and cryptographic services like confidentiality, integrity, and authentication are also articulated, alongside various algorithms including RSA and DES.Information system security Unit 2.pptx
Information system security Unit 2.pptxDr. Pallawi Bulakh
╠²
The document provides a comprehensive overview of cryptography, detailing its definition, historical context, and importance in securing communication and protecting information. It describes various cryptographic techniques, including symmetric and asymmetric key cryptography, hash functions, and encryption methods such as stream and block ciphers. Additionally, it covers cryptanalysis, the study of breaking cryptographic systems, and the intricacies of different cipher techniques, including the Caesar cipher and Playfair cipher.Computer security communication networking cryptography .ppt
Computer security communication networking cryptography .ppttipurple7989
╠²
The document discusses the fundamentals of computer security, focusing on cryptography and secure communication requirements such as secrecy, authentication, and message integrity. It explains various encryption techniques, including symmetric and asymmetric encryption, and emphasizes the importance of algorithms like DES and RSA while detailing their strengths and vulnerabilities. Additionally, the document covers authentication mechanisms, highlighting the significance of protocols and message digests in verifying identities and ensuring data integrity.introduction to cryptography and its basic techniques
introduction to cryptography and its basic techniquesAneelSoomro1
╠²
The document outlines key concepts of computer security and cryptography, emphasizing the importance of secure communication, which includes secrecy, authentication, and message integrity. It discusses the basics of cryptography, including symmetric and asymmetric encryption methods, encryption algorithms like DES and RSA, and techniques for cryptanalysis. Moreover, it highlights authentication protocols such as message digests, password authentication, and the Kerberos system for establishing secure access.9-crypthvvy6u7btyjibuibuibryjijighhnm.ppt
9-crypthvvy6u7btyjibuibuibryjijighhnm.pptvikashbharati917
╠²
The document covers cryptography, detailing its importance in secure communications which require secrecy, authentication, and message integrity. It explains various encryption methods, including symmetric and asymmetric algorithms, their properties, strengths, limitations, and applications in securing communications like e-mails and data transmissions. Additionally, it discusses cryptanalysis and authentication techniques, highlighting the role of algorithms like RSA, DES, and specific protocols such as Kerberos in the field of computer security.Chaos based cryprography - encryption & hash function
Chaos based cryprography - encryption & hash functionssuser478d0e
╠²
The document discusses computer security focusing on secure communication, cryptography, and various encryption techniques. It outlines key concepts such as symmetric and asymmetric encryption, the importance of key size for security, methods of authentication, and cryptanalysis techniques. Additionally, it covers specific algorithms like DES, RSA, and discusses protocols used for secure data transmission, illustrating the significance of cryptographic methods in ensuring the secrecy and integrity of information.Symmetric Encryption Techniques
Symmetric Encryption Techniques Dr. Kapil Gupta
╠²
This document provides an overview of symmetric encryption techniques, including:
- Symmetric encryption uses a shared secret key for both encryption and decryption.
- Classical encryption algorithms like the Caesar cipher and monoalphabetic substitution ciphers can be broken through frequency analysis.
- The Playfair cipher improved security over monoalphabetic ciphers by encrypting digrams, but it can still be broken with enough ciphertext.
- Polyalphabetic ciphers like the Vigen├©re cipher further increase security by using multiple cipher alphabets selected by a keyword.the art of the fking dum crypto_basic.ppt
the art of the fking dum crypto_basic.pptjamkhan10
╠²
This document discusses computer security and cryptography. It covers the basics of cryptography including the needs for secure communication, encryption algorithms, symmetric and asymmetric encryption, encryption standards like DES and AES, cryptanalysis techniques, and authentication methods. It provides an overview of the key concepts and techniques in cryptography and computer security.7-cryptography.ppt
7-cryptography.pptakamkhalidmohammed
╠²
This document discusses computer security and cryptography. It covers the basics of cryptography including the needs for secure communication, encryption algorithms, symmetric and asymmetric encryption, encryption standards like DES and AES, cryptanalysis techniques, and authentication methods. It provides an overview of the key concepts and techniques in cryptography and computer security.Introduction to Cryptography and its Basic Fundamentals
Introduction to Cryptography and its Basic FundamentalsChinfeliprada1
╠²
The document outlines the foundations of computer security, emphasizing the needs for secure communication, which include secrecy, authentication, and message integrity. It discusses various cryptographic methods, including symmetric and asymmetric encryption, detailing algorithms such as DES, RSA, and techniques like message digests and passwords. Additionally, it highlights the importance of key management and the vulnerabilities associated with cryptographic systems.This is the presentation ofcryptography.ppt
This is the presentation ofcryptography.pptvimalguptaofficial
╠²
The document discusses the principles and methodologies of computer security through cryptography, emphasizing secure communication requirements like secrecy, authentication, and message integrity. It outlines various encryption techniques, including symmetric and asymmetric encryption, block and stream ciphers, and key agreement algorithms, while also highlighting their strengths and weaknesses. Additionally, it addresses authentication methods such as message digests, digital signatures, and password protocols, with a focus on maintaining the integrity and confidentiality of communications.Crytography CertCourse Module 1 & 2.ppt
Crytography CertCourse Module 1 & 2.pptMuhammadShajid1
╠²
The document discusses computer security and cryptography. It provides an overview of the basic needs for secure communication including secrecy, authentication, and message integrity. It then describes the basics of cryptography including encryption, decryption, symmetric and asymmetric algorithms. Specific algorithms discussed include DES, Triple DES, RSA and El Gamal. It also covers cryptanalysis techniques for breaking encryption codes.K12 Tableau User Group virtual event June 18, 2025
K12 Tableau User Group virtual event June 18, 2025dogden2
╠²
National K12 Tableau User Group: June 2025 meeting slidesMore Related Content
Similar to Cryptography (20)
Cryptography, Cryptology, Encryption and types
Cryptography, Cryptology, Encryption and typessowaibakhan3
╠²
The document discusses cryptography, its definitions, advantages, and historical context, emphasizing its role in securing information by encoding messages to ensure confidentiality, authentication, integrity, and non-repudiation. It covers types of ciphers such as the Caesar shift cipher and Vigen├©re cipher, detailing their encryption processes and weaknesses, alongside the concept of the one-time pad as a theoretically unbreakable encryption method. Additionally, it highlights key terminology and principles associated with cryptography and cryptosystems.Computer systems security 7-cryptography.ppt
Computer systems security 7-cryptography.pptstephen972973
╠²
The document discusses the key components of computer security communications, particularly focusing on the requirements for secure communication such as secrecy, authentication, and message integrity. It introduces various cryptographic techniques including symmetric and asymmetric encryption methods, their algorithms, and associated security features, along with the concept of key management and vulnerabilities such as man-in-the-middle attacks. Additionally, it covers authentication mechanisms and protocols used to validate identities and protect data integrity in communications.Cryptography & Steganography
Cryptography & SteganographyAnimesh Shaw
╠²
The document presents a comprehensive overview of cryptography and steganography, discussing its definition, history, key terminologies, types, and algorithms such as RSA and DES. It highlights the importance of cryptography in securing communications, ensuring data integrity, privacy, and authentication. Additionally, it contrasts symmetric and public-key cryptography while explaining key distribution challenges and types of encryption systems.Cryptography.pptxhis document provides an overview of cryptography. It define...
Cryptography.pptxhis document provides an overview of cryptography. It define...researchcollabarator
╠²
The document provides an introduction to cryptography, defining it as a method for secure data storage and transmission. It discusses the history, techniques, and terminology relevant to cryptography, including different encryption methods like symmetric and asymmetric keys. Additionally, it highlights various applications of cryptography in everyday technology, such as e-commerce and electronic voting.Introduction to Cryptography
Introduction to CryptographyMd. Afif Al Mamun
╠²
Cryptography is the practice of securing communication and information by converting plaintext into ciphertext. The document provides an introduction to cryptography including its history from ancient times to the present. It discusses terminology like plaintext, encryption, ciphertext, decryption, and keys. Symmetric key cryptography uses a single key for encryption and decryption while asymmetric key cryptography uses two different keys. Examples of symmetric methods are DES, 3DES, AES, and RC4, while RSA is a common asymmetric method. Applications of cryptography include ATMs, email passwords, e-payments, e-commerce, electronic voting, defense services, securing data, and access control.Computer Security Chapter III.pdf
Computer Security Chapter III.pdfHarrisentertainment
╠²
This document provides an overview of cryptography and encryption techniques. It discusses the basic cryptographic terms and historical background of cryptography. It then describes different cipher techniques including transposition cipher and substitution cipher. It also discusses conventional encryption algorithms such as DES, AES, and RSA. Symmetric key cryptography and public key cryptography are explained. The document also covers digital signatures, cryptanalysis, and cryptographic systems in general.Cryptography and network security Nit701
Cryptography and network security Nit701Amit Pathak
╠²
The document provides an extensive overview of cryptography and network security, covering various types of cryptography, key algorithms, and their applications in securing communication. It discusses both symmetric and asymmetric cryptography, detailing their mechanisms, advantages, and drawbacks. Key concepts such as encryption, decryption, and cryptographic services like confidentiality, integrity, and authentication are also articulated, alongside various algorithms including RSA and DES.Information system security Unit 2.pptx
Information system security Unit 2.pptxDr. Pallawi Bulakh
╠²
The document provides a comprehensive overview of cryptography, detailing its definition, historical context, and importance in securing communication and protecting information. It describes various cryptographic techniques, including symmetric and asymmetric key cryptography, hash functions, and encryption methods such as stream and block ciphers. Additionally, it covers cryptanalysis, the study of breaking cryptographic systems, and the intricacies of different cipher techniques, including the Caesar cipher and Playfair cipher.Computer security communication networking cryptography .ppt
Computer security communication networking cryptography .ppttipurple7989
╠²
The document discusses the fundamentals of computer security, focusing on cryptography and secure communication requirements such as secrecy, authentication, and message integrity. It explains various encryption techniques, including symmetric and asymmetric encryption, and emphasizes the importance of algorithms like DES and RSA while detailing their strengths and vulnerabilities. Additionally, the document covers authentication mechanisms, highlighting the significance of protocols and message digests in verifying identities and ensuring data integrity.introduction to cryptography and its basic techniques
introduction to cryptography and its basic techniquesAneelSoomro1
╠²
The document outlines key concepts of computer security and cryptography, emphasizing the importance of secure communication, which includes secrecy, authentication, and message integrity. It discusses the basics of cryptography, including symmetric and asymmetric encryption methods, encryption algorithms like DES and RSA, and techniques for cryptanalysis. Moreover, it highlights authentication protocols such as message digests, password authentication, and the Kerberos system for establishing secure access.9-crypthvvy6u7btyjibuibuibryjijighhnm.ppt
9-crypthvvy6u7btyjibuibuibryjijighhnm.pptvikashbharati917
╠²
The document covers cryptography, detailing its importance in secure communications which require secrecy, authentication, and message integrity. It explains various encryption methods, including symmetric and asymmetric algorithms, their properties, strengths, limitations, and applications in securing communications like e-mails and data transmissions. Additionally, it discusses cryptanalysis and authentication techniques, highlighting the role of algorithms like RSA, DES, and specific protocols such as Kerberos in the field of computer security.Chaos based cryprography - encryption & hash function
Chaos based cryprography - encryption & hash functionssuser478d0e
╠²
The document discusses computer security focusing on secure communication, cryptography, and various encryption techniques. It outlines key concepts such as symmetric and asymmetric encryption, the importance of key size for security, methods of authentication, and cryptanalysis techniques. Additionally, it covers specific algorithms like DES, RSA, and discusses protocols used for secure data transmission, illustrating the significance of cryptographic methods in ensuring the secrecy and integrity of information.Symmetric Encryption Techniques
Symmetric Encryption Techniques Dr. Kapil Gupta
╠²
This document provides an overview of symmetric encryption techniques, including:
- Symmetric encryption uses a shared secret key for both encryption and decryption.
- Classical encryption algorithms like the Caesar cipher and monoalphabetic substitution ciphers can be broken through frequency analysis.
- The Playfair cipher improved security over monoalphabetic ciphers by encrypting digrams, but it can still be broken with enough ciphertext.
- Polyalphabetic ciphers like the Vigen├©re cipher further increase security by using multiple cipher alphabets selected by a keyword.the art of the fking dum crypto_basic.ppt
the art of the fking dum crypto_basic.pptjamkhan10
╠²
This document discusses computer security and cryptography. It covers the basics of cryptography including the needs for secure communication, encryption algorithms, symmetric and asymmetric encryption, encryption standards like DES and AES, cryptanalysis techniques, and authentication methods. It provides an overview of the key concepts and techniques in cryptography and computer security.7-cryptography.ppt
7-cryptography.pptakamkhalidmohammed
╠²
This document discusses computer security and cryptography. It covers the basics of cryptography including the needs for secure communication, encryption algorithms, symmetric and asymmetric encryption, encryption standards like DES and AES, cryptanalysis techniques, and authentication methods. It provides an overview of the key concepts and techniques in cryptography and computer security.Introduction to Cryptography and its Basic Fundamentals
Introduction to Cryptography and its Basic FundamentalsChinfeliprada1
╠²
The document outlines the foundations of computer security, emphasizing the needs for secure communication, which include secrecy, authentication, and message integrity. It discusses various cryptographic methods, including symmetric and asymmetric encryption, detailing algorithms such as DES, RSA, and techniques like message digests and passwords. Additionally, it highlights the importance of key management and the vulnerabilities associated with cryptographic systems.This is the presentation ofcryptography.ppt
This is the presentation ofcryptography.pptvimalguptaofficial
╠²
The document discusses the principles and methodologies of computer security through cryptography, emphasizing secure communication requirements like secrecy, authentication, and message integrity. It outlines various encryption techniques, including symmetric and asymmetric encryption, block and stream ciphers, and key agreement algorithms, while also highlighting their strengths and weaknesses. Additionally, it addresses authentication methods such as message digests, digital signatures, and password protocols, with a focus on maintaining the integrity and confidentiality of communications.Crytography CertCourse Module 1 & 2.ppt
Crytography CertCourse Module 1 & 2.pptMuhammadShajid1
╠²
The document discusses computer security and cryptography. It provides an overview of the basic needs for secure communication including secrecy, authentication, and message integrity. It then describes the basics of cryptography including encryption, decryption, symmetric and asymmetric algorithms. Specific algorithms discussed include DES, Triple DES, RSA and El Gamal. It also covers cryptanalysis techniques for breaking encryption codes.Cryptography.pptxhis document provides an overview of cryptography. It define...
Cryptography.pptxhis document provides an overview of cryptography. It define...researchcollabarator
╠²
Recently uploaded (20)
K12 Tableau User Group virtual event June 18, 2025
K12 Tableau User Group virtual event June 18, 2025dogden2
╠²
National K12 Tableau User Group: June 2025 meeting slidesUniversity of Ghana Cracks Down on Misconduct: Over 100 Students Sanctioned
University of Ghana Cracks Down on Misconduct: Over 100 Students SanctionedKweku Zurek
╠²
University of Ghana Cracks Down on Misconduct: Over 100 Students Sanctioned
Pests of Maize: An comprehensive overview.pptx
Pests of Maize: An comprehensive overview.pptxArshad Shaikh
╠²
Maize is susceptible to various pests that can significantly impact yields. Key pests include the fall armyworm, stem borers, cob earworms, shoot fly. These pests can cause extensive damage, from leaf feeding and stalk tunneling to grain destruction. Effective management strategies, such as integrated pest management (IPM), resistant varieties, biological control, and judicious use of chemicals, are essential to mitigate losses and ensure sustainable maize production.A Visual Introduction to the Prophet Jeremiah
A Visual Introduction to the Prophet JeremiahSteve Thomason
╠²
These images will give you a visual guide to both the context and the flow of the story of the prophet Jeremiah. Feel free to use these in your study, preaching, and teaching.LDMMIA Shop & Student News Summer Solstice 25
LDMMIA Shop & Student News Summer Solstice 25LDM & Mia eStudios
╠²
6/18/25
Shop, Upcoming: Final Notes to Review as we Close Level One. Make sure to review the orientation and videos as well. ThereŌĆÖs more to come and material to cover in Levels 2-3. The content will be a combination of Reiki and Yoga. Also energy topics of our spiritual collective.
Thanks again all future Practitioner Level Students. Our Levels so far are: Guest, Grad, and Practitioner. We have had over 5k Spring Views.
https://ldm-mia.creator-spring.comIntellectual Property Right (Jurisprudence).pptx
Intellectual Property Right (Jurisprudence).pptxVishal Chanalia
╠²
Intellectual property corresponds to ideas owned by a person or a firm and thus subjected to legal protection under the law.
The main purpose of intellectual property is to give encouragement to the innovators of new concepts by giving them the opportunity to make sufficient profits from their inventions and recover their manufacturing costs and efforts. Paper 108 | ThoreauŌĆÖs Influence on Gandhi: The Evolution of Civil Disobedience
Paper 108 | ThoreauŌĆÖs Influence on Gandhi: The Evolution of Civil DisobedienceRajdeep Bavaliya
╠²
Dive into the powerful journey from ThoreauŌĆÖs 19thŌĆæcentury essay to GandhiŌĆÖs mass movement, and discover how one manŌĆÖs moral stand became the backbone of nonviolent resistance worldwide. Learn how conscience met strategy to spark revolutions, and why their legacy still inspires todayŌĆÖs social justice warriors. Uncover the evolution of civil disobedience. DonŌĆÖt forget to like, share, and follow for more deep dives into the ideas that changed the world.
M.A. Sem - 2 | Presentation
Presentation Season - 2
Paper - 108: The American Literature
Submitted Date: April 2, 2025
Paper Name: The American Literature
Topic: ThoreauŌĆÖs Influence on Gandhi: The Evolution of Civil Disobedience
[Please copy the link and paste it into any web browser to access the content.]
Video Link: https://youtu.be/HXeq6utg7iQ
For a more in-depth discussion of this presentation, please visit the full blog post at the following link: https://rajdeepbavaliya2.blogspot.com/2025/04/thoreau-s-influence-on-gandhi-the-evolution-of-civil-disobedience.html
Please visit this blog to explore additional presentations from this season:
Hashtags:
#CivilDisobedience #ThoreauToGandhi #NonviolentResistance #Satyagraha #Transcendentalism #SocialJustice #HistoryUncovered #GandhiLegacy #ThoreauInfluence #PeacefulProtest
Keyword Tags:
civil disobedience, Thoreau, Gandhi, Satyagraha, nonviolent protest, transcendentalism, moral resistance, Gandhi Thoreau connection, social change, political philosophyLAZY SUNDAY QUIZ "A GENERAL QUIZ" JUNE 2025 SMC QUIZ CLUB, SILCHAR MEDICAL CO...
LAZY SUNDAY QUIZ "A GENERAL QUIZ" JUNE 2025 SMC QUIZ CLUB, SILCHAR MEDICAL CO...Ultimatewinner0342
╠²
¤¦Ā Lazy Sunday Quiz | General Knowledge Trivia by SMC Quiz Club ŌĆō Silchar Medical College
Presenting the Lazy Sunday Quiz, a fun and thought-provoking general knowledge quiz created by the SMC Quiz Club of Silchar Medical College & Hospital (SMCH). This quiz is designed for casual learners, quiz enthusiasts, and competitive teams looking for a diverse, engaging set of questions with clean visuals and smart clues.
¤Ä» What is the Lazy Sunday Quiz?
The Lazy Sunday Quiz is a light-hearted yet intellectually rewarding quiz session held under the SMC Quiz Club banner. ItŌĆÖs a general quiz covering a mix of current affairs, pop culture, history, India, sports, medicine, science, and more.
Whether youŌĆÖre hosting a quiz event, preparing a session for students, or just looking for quality trivia to enjoy with friends, this PowerPoint deck is perfect for you.
¤ōŗ Quiz Format & Structure
Total Questions: ~50
Types: MCQs, one-liners, image-based, visual connects, lateral thinking
Rounds: Warm-up, Main Quiz, Visual Round, Connects (optional bonus)
Design: Simple, clear slides with answer explanations included
Tools Needed: Just a projector or screen ŌĆō ready to use!
¤¦Ā Who Is It For?
College quiz clubs
School or medical students
Teachers or faculty for classroom engagement
Event organizers needing quiz content
Quizzers preparing for competitions
Freelancers building quiz portfolios
¤ÆĪ Why Use This Quiz?
Ready-made, high-quality content
Curated with lateral thinking and storytelling in mind
Covers both academic and pop culture topics
Designed by a quizzer with real event experience
Usable in inter-college fests, informal quizzes, or Sunday brain workouts
¤ōÜ About the Creators
This quiz has been created by Rana Mayank Pratap, an MBBS student and quizmaster at SMC Quiz Club, Silchar Medical College. The club aims to promote a culture of curiosity and smart thinking through weekly and monthly quiz events.
¤öŹ SEO Tags:
quiz, general knowledge quiz, trivia quiz, ║▌║▌▀ŻShare quiz, college quiz, fun quiz, medical college quiz, India quiz, pop culture quiz, visual quiz, MCQ quiz, connect quiz, science quiz, current affairs quiz, SMC Quiz Club, Silchar Medical College
¤ōŻ Reuse & Credit
YouŌĆÖre free to use or adapt this quiz for your own events or sessions with credit to:
SMC Quiz Club ŌĆō Silchar Medical College & Hospital
Curated by: Rana Mayank PratapChalukyas of Gujrat, Solanki Dynasty NEP.pptx
Chalukyas of Gujrat, Solanki Dynasty NEP.pptxDr. Ravi Shankar Arya Mahila P. G. College, Banaras Hindu University, Varanasi, India.
╠²
This presentation has been made keeping in mind the students of undergraduate and postgraduate level. In this slide try to present the brief history of Chaulukyas of Gujrat up to Kumarpala To keep the facts in a natural form and to display the material in more detail, the help of various books, websites and online medium has been taken. Whatever medium the material or facts have been taken from, an attempt has been made by the presenter to give their reference at the end.
Chaulukya or Solanki was one of the Rajputs born from Agnikul. In the Vadnagar inscription, the origin of this dynasty is told from Brahma's Chauluk or Kamandalu. They ruled in Gujarat from the latter half of the tenth century to the beginning of the thirteenth century. Their capital was in Anahilwad. It is not certain whether it had any relation with the Chalukya dynasty of the south or not. It is worth mentioning that the name of the dynasty of the south was 'Chaluky' while the dynasty of Gujarat has been called 'Chaulukya'. The rulers of this dynasty were the supporters and patrons of Jainism.Tanja Vujicic - PISA for Schools contact Info
Tanja Vujicic - PISA for Schools contact InfoEduSkills OECD
╠²
Tanja Vujicic, Senior Analyst and PISA for SchoolŌĆÖs Project Manager at the OECD spoke at the OECD webinar 'Turning insights into impact: What do early case studies reveal about the power of PISA for Schools?' on 20 June 2025
PISA for Schools is an OECD assessment that evaluates 15-year-old performance on reading, mathematics, and science. It also gathers insights into studentsŌĆÖ learning environment, engagement and well-being, offering schools valuable data that help them benchmark performance internationally and improve education outcomes. A central ambition, and ongoing challenge, has been translating these insights into meaningful actions that drives lasting school improvement. Sustainable Innovation with Immersive Learning
Sustainable Innovation with Immersive LearningLeonel Morgado
╠²
Prof. Leonel and Prof. Dennis approached educational uses, practices, and strategies of using immersion as a lens to interpret, design, and planning educational activities in a sustainable way. Rather than one-off gimmicks, the intent is to enable instructors (and institutions) to be able to include them in their regular activities, including the ability to evaluate and redesign them.
Immersion as a phenomenon enables interpreting pedagogical activities in a learning-agnostic way: you take a stance on the learning theory to follow, and leverage immersion to envision and guide your practice.How to use search fetch method in Odoo 18
How to use search fetch method in Odoo 18Celine George
╠²
The search_fetch is a powerful ORM method used in Odoo for some specific addons to combine the functionality of search and read for more efficient data fetching. It might be used to search for records and fetch specific fields in a single call. It stores the result in the cache memory.Romanticism in Love and Sacrifice An Analysis of Oscar WildeŌĆÖs The Nightingal...
Romanticism in Love and Sacrifice An Analysis of Oscar WildeŌĆÖs The Nightingal...KaryanaTantri21
╠²
The story revolves around a college student who despairs not having a red rose as a condition for dancing with the girl he loves. The nightingale hears his complaint and offers to create the red rose at the cost of his life. He sang a love song all night with his chest stuck to the thorns of the rose tree. Finally, the red rose grew, but his sacrifice was in vain. The girl rejected the flower because it didnŌĆÖt match her outfit and preferred a jewellery gift. The student threw the flower on the street and returned to studying philosophyGreat Governors' Send-Off Quiz 2025 Prelims IIT KGP
Great Governors' Send-Off Quiz 2025 Prelims IIT KGPIIT Kharagpur Quiz Club
╠²
Prelims of the Great Governors' Send-Off Quiz 2025 hosted by the outgoing governors.
QMs: Aarushi, Aatir, Aditya, ArnavList View Components in Odoo 18 - Odoo ║▌║▌▀Żs
List View Components in Odoo 18 - Odoo ║▌║▌▀ŻsCeline George
╠²
In Odoo, there are many types of views possible like List view, Kanban view, Calendar view, Pivot view, Search view, etc.
The major change that introduced in the Odoo 18 technical part in creating views is the tag <tree> got replaced with the <list> for creating list views. Vitamin and Nutritional Deficiencies.pptx
Vitamin and Nutritional Deficiencies.pptxVishal Chanalia
╠²
Vitamin and nutritional deficiency occurs when the body does not receive enough essential nutrients, such as vitamins and minerals, needed for proper functioning. This can lead to various health problems, including weakened immunity, stunted growth, fatigue, poor wound healing, cognitive issues, and increased susceptibility to infections and diseases. Long-term deficiencies can cause serious and sometimes irreversible health complications.LAZY SUNDAY QUIZ "A GENERAL QUIZ" JUNE 2025 SMC QUIZ CLUB, SILCHAR MEDICAL CO...
LAZY SUNDAY QUIZ "A GENERAL QUIZ" JUNE 2025 SMC QUIZ CLUB, SILCHAR MEDICAL CO...Ultimatewinner0342
╠²
Chalukyas of Gujrat, Solanki Dynasty NEP.pptx
Chalukyas of Gujrat, Solanki Dynasty NEP.pptxDr. Ravi Shankar Arya Mahila P. G. College, Banaras Hindu University, Varanasi, India.
╠²
Ad
Cryptography
- 1. C r y p t o g r a p h y Presented byŌĆ” Saumil Patel Divyarajsinh Vaghela Richa Raval Milan Patel
- 3. C R Y P T O G R A P H Y An art of making and solving codesŌĆ” What is Cryptography?
- 4. C R Y P T O G R A P H Y What was the need to invent Cryptography? For Secure CommunicationŌĆ”
- 5. C R Y P T O G R A P H Y Hacker
- 6. C R Y P T O G R A P H Y Key Words ’ā© Plain Text :- It is the simple text. ’ā© Cipher Text :- It is the coded text. ’ā© Encryption :- Converting plain text into Cipher text. ’ā© Decryption :- Converting back from Cipher text into Plain text. (Ex. Hello) (Ex. lkjne)
- 7. C R Y P T O G R A P H Y Defination ’ā©It is the practice and study of techniques for secure communication of data. This system is called Cryptosystem.
- 8. of
- 9. Ancient History Pioneer of Cryptography :- Julius Caesar Birth :- 100 BC Country :- Rome Invention :- Shift Cipher method
- 10. Ancient History ’ā© Started in Egypt in 3000 B.C. ’ā© They found it very complicate due to insufficient knowledge of Mathematics & Cryptography. ’ā© Finally they had to stop itŌĆ”
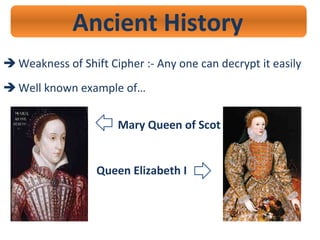
- 11. Ancient History ’ā© Weakness of Shift Cipher :- Any one can decrypt it easily ’ā© Well known example ofŌĆ” Mary Queen of Scot Queen Elizabeth I c c
- 12. Modern History (ZimmermannŌĆÖs Telegram) ’ā©Sent by Arthur Zimmermann, the foreign secretary of Germany on 11/01/1917. ’ā©United States entered into World War - I ’ā©It was intercepted and decoded by British Intelligence.
- 13. In 20th CenturyŌĆ” ’ā©Invented by Arthur Scherbius at the end of World War I. ’ā©Intention:- To Encode and decode of Ciphers. ’ā© Adopted by Military and Govt. ’ā©First broken by Polish Cipher Bureau in Dec.1932 by using Theoretical Mathematics and Reverse Engineering. Enigma Machine
- 14. In 21th CenturyŌĆ” After the end of World War II, the Encryption and Decryption has shifted from ŌĆ”.
- 15. In 21th CenturyŌĆ” Parallel to the development ofŌĆ” ŌĆ”advance methods in Cryptography were developed. Shift Cipher DES Cipher RSA Cipher Permutation Cipher DH Secret key exchange method
- 16. Ceasar Cipher/ Shift Cipher Method -Saumil Patel
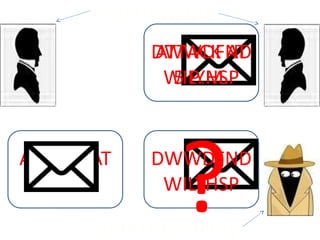
- 17. Indian Army Pakistan Army ATTACK AT 5 P.M. DWWDFND WILYHSP DWWDFND WILYHSP ATTACK AT 5 P.M. ?
- 18. How did they do itŌĆ”??? They use a method calledŌĆ” CEASAR CIPHER
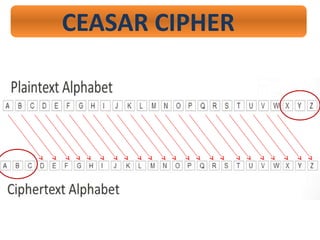
- 19. CEASAR CIPHER ’ā© One of the simplest and widely known encryption technique. ’ā© Named after Julius Caesar. ’ā© He used it in his private communication. ’ā© This method is also known as Shift Cipher or CeaserŌĆÖs Code.
- 20. CEASAR CIPHER
- 21. CEASAR CIPHER How to convert a text into Cipher Code? Step -1 :- Remove space, comma(,) , dot(.), ŌĆ£ ŌĆ£, etc. and write a simple sentence. Step -2 :- Replace numbers by alphabets. ex. 5 ’ā© FIVE Step -3 :-Replace each alphabet by a definite shift.
- 22. CEASAR CIPHER Ex. ATTACK AT 5 P.M. Step -1 :- Remove space, comma(,) , dot(.), ŌĆ£ ŌĆ£, etc. and write a simple sentence. ’ā© ATTACKAT5PM
- 23. CEASAR CIPHER Ex. ATTACK AT 5 P.M. ’ā© ATTACKAT5PM Step -2 :- Replace numbers by alphabets. ’ā© ATTACKATFIVEPM
- 24. CEASAR CIPHER Ex. ATTACK AT 5 P.M. Step -3 :-Replace each alphabet by a definite shift. Plain Text :A T T A C K A T F I V E P M Cipher Text :D W W D F N D W I L Y H S P
- 25. CEASAR CIPHER Ex. ATTACK AT 5 P.M. Cipher Text: DWWDFNDWILYHSP
- 26. Cipher Disk & Permutation Method -Divyarajsinh Vaghela
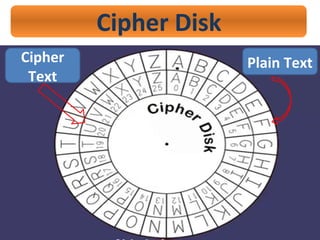
- 27. Cipher Disk ’ā© Enciphering & Deciphering tool. ’ā© Developed by Italian Architect Leon Battista Alberti in 1470. ’ā© It Consist of two concentric disk. 1) Large :- Stationary 2) Small :- Movable
- 29. Cipher Disk ’ā© How Cipher Disk is Useful ? ’ā©Disadvantage of Shift Cipher method is that there are only 25 different possibilities for each alphabet. ’ā©Cipher Disk is useful to decrypt the Cipher code very quickly.
- 30. Permutation Cipher ’ā© It is one of the most advance methods used now a days. What is the advantage to use Permutation Cipher? ’ā© It is next to impossible to decrypt the code encrypted by Permutation Cipher.
- 31. Permutation Cipher * Method to create Permutation Cipher Code:- Step-1 :- Write all the alphabets in a row for the plain text. Step-2 :- Randomly choose any of the 26 alphabets for each alphabet of the plain text. Ex. For A choose N, For B choose W, etcŌĆ”
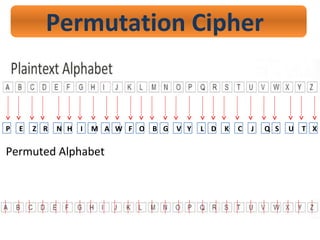
- 32. Permutation Cipher P E Z R N H I M A W F O B G V Y L D K C J Q S U T X Permuted Alphabet
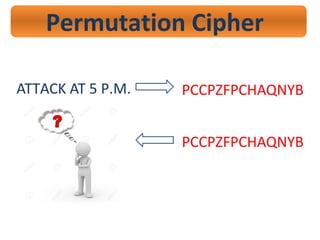
- 33. Permutation Cipher Ex. ATTACK AT 5 P.M. ’ā© A T T A C K A T F I V E P M P PCC Z F P CHAQ N Y B
- 34. Permutation Cipher ATTACK AT 5 P.M. PCCPZFPCHAQNYB PCCPZFPCHAQNYB
- 35. Applications & Importance of Cryptography - Milan Patel
- 36. ’ā© Cryptography plays an important role in many IT applications ! HOW..??? LetŌĆÖs see an overviewŌĆ”
- 37. Strong Authentication ’ā© Cryptography plays an important role in Identity Management. There are many methods fromŌĆ” to
- 38. Strong Authentication OTP tokens ( One Time Password Generating tokens) - Popular solution for securing authentication. - Widely used in Banks. - Manufactured by RSA, VASCO, Codes, etc.
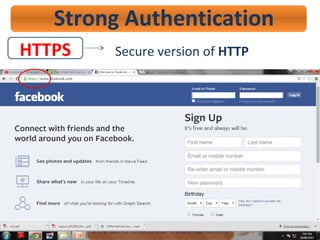
- 39. HTTPS Strong Authentication Secure version of HTTP
- 40. HTTPS Strong Authentication Secure version of HTTP
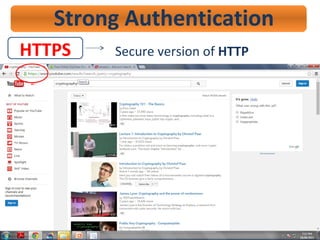
- 41. HTTPS Strong Authentication Secure version of HTTP
- 42. HTTPS Strong Authentication Secure version of HTTP
- 43. HTTPS Strong Authentication Secure version of HTTP
- 44. HTTPS Strong Authentication Secure version of HTTP ’ā© To access e-banking site. ’ā© To secure online credit card transaction. ’ā© For secure email messaging. ’ā© File sharing.
- 45. TLS protocol Strong Authentication (Transport Layer Security) - Most widely used protocol. - Ex. Certificate for server authentication.
- 46. Wireless Communication Why use Cryptography for Wireless Communication ? BecauseŌĆ” -It is very easy for any one to hack any wireless communication than an wired communication. -All that required are only laptop and an antenna..!
- 47. Wireless Communication ’ā© It is the most widely used standard for wireless networking today. ’ā© Cryptography plays an important role in Wi-fi in two waysŌĆ” 1) Securing data transmission 2) End point authentication
- 48. Wireless Communication ’ā© It is designed to enable wireless data exchange over short distance. ’ā© Cryptography plays an important role in Bluetooth in two aspect :- 1) Confidentially 2) Authentication (called pairing)
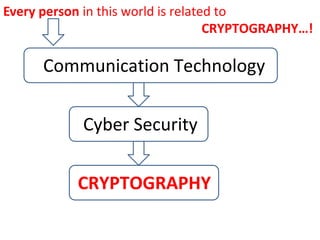
- 49. Every person in this world is related to CRYPTOGRAPHYŌĆ”! Communication Technology Cyber Security CRYPTOGRAPHY