Cyber Crimes & Cyber Forensics
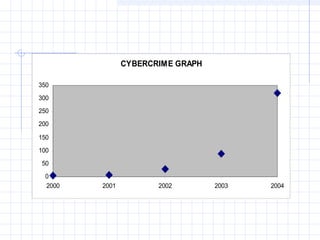
- 3. CYBERCRIME GRAPH 0 50 100 150 200 250 300 350 2000 2001 2002 2003 2004
- 4. CYBER CRIMES AREŌĆ” NEITHER FORWARD.. NOR BACKWARD.. BUT AWKWARD:
- 6. NARRATION ŌĆ£YŌĆØ RECEIVES AN EMAIL FROM PROF.(MRS).X INTRODUCING HERSELF AS TECHNOLOGIST WORKING IN THE AREA OF AFFORDABLE DRINKING WATER PROJECT AND SEEKING A DATE FOR APPOINTMENT ŌĆ£YŌĆØ RESPONDS FAVOURABLY WITH A DATE.
- 7. NARRATION(CONTD) ŌĆ£YŌĆØ RECEIVES A EMAIL FROM SECURITY CHIEF OF PROF.(MRS).X FROM HONGKONG TELLING THAT HE IS DOING THE DUE DILIGENCE CHECK ŌĆ£YŌĆØ RESPONDS FAVOURABLY.
- 8. NARRATION(CONTD) ŌĆ£YŌĆØ RECEIVES A EMAIL FROM PROTOCOL OFFICER OF PROF. (MRS).X FROM MUMBAI TELLING THAT SHE IS DOING THE DUE DILIGENCE CHECK ŌĆ£YŌĆØ RESPONDS FAVOURABLY.
- 9. NARRATION(CONTD) APPOINTED DATE COMES ŌĆ£XŌĆØ DOESNOT SHOW UP NEXT DAY, ŌĆ£YŌĆØ GETS MAIL FROM SECURITY CHIEF ASKING FOR WHEREABOUTS OF ŌĆ£XŌĆØŌĆ” ŌĆ£YŌĆØ IS THREATENED OF CONSEQUENCES ŌĆ” SUBMIT OR FIGHT ’ü« PANIC, ANXIETY & DESPAIR
- 10. WE SAWŌĆ” CONVENTIONAL CRIMES BEING COMMITTED WITH EASE AND SOPHISTICATION, USING COMPUTER AND INFORMATION TECHNOLOGY.
- 12. NARRATION COMPANY ŌĆ£XŌĆØ GETS AN OFFSHORE S/W DELIVERY JOB FROM COMPANY ŌĆ£YŌĆØ ŌĆ£YŌĆØ INSISTS ON LOTS OF CUSTOMISATION ŌĆ£XŌĆØ DEPUTES TWO ENGINEERS WITH SOURCE CODE TO CARRY OUT CUSTOMISATION AT THE ŌĆ£YŌĆØŌĆÖs PREMISES CONTRACT GETS TERMINATED ENGINEERS RESIGN ON COMING BACK ŌĆ£YŌĆØ LAUNCHES NEW S/W WITH SIMILAR FEATURES ’ü« YET, CREATES SIMPLE & EASY PLATFORMS # Case Referred by : Judicial First Class Magistrate # Case Registered under Sec 65 and 72 of IT act # Complainant : Software Company # Accused : Two Former Employees # Nature of Crime : Source Code Theft
- 13. WE ARE SEEINGŌĆ” NEW VERSIONS OF CONVENTIONAL CRIMES EMERGING, TARGETTING COMPUTERS AND INFORMATION TECHNOLOGY.
- 15. NARRATION ŌĆ£XŌĆØ IS CAUGHT IN A CYBER CRIME ŌĆ£XŌĆØ CLAIMS HE CAN CRACK PASSWORDS, BREAK INTO EMAIL ACCOUNTS, INTERCEPT CHATS ETC ŌĆ£XŌĆØ PRODUCES EMAIL/CHAT PRINT OUTS WHICH SHOW POSSIBILITY OF TERRORIST ATTACK REWARD OR PUNISHŌĆ”ŌĆ”.. ’ü« ARRAY OF CONFUSION
- 16. NOW WE SEEŌĆ” NEW CRIMES BEING INVENTED, CONFUSING COMPUTERS AND INFORMATION TECHNOLOGY
- 17. NEEDŌĆ” EFFECTIVE MEANS TO PRE-EMPT CYBER CRIMES EFFECTIVE WAY TO ENSURE DEFINITE PUNISHMENT AS DETERENT AGAINST CYBER CRIMES
- 18. CYBER FORENSICS CAN BE AN EFFECTIVE TOOL
- 19. CYBER FORENSICS ISŌĆ”ŌĆ” ŌĆ£The unique process of identifying, preserving, analyzing and presenting digital evidence in a manner that is legally accepted.ŌĆØ
- 20. MULTI DIMENSIONAL CHALLENGES WHY IS IT UNIQUE ?
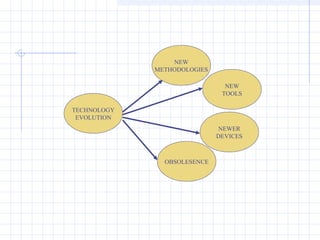
- 22. TECHNICAL TECHNOLOGY IS CHANGING RAPIDLY CYBER CRIMES ARE ALSO CHANGING RAPIDLY SYSTEMS AND CRIMES EVOLVE MORE RAPIDLY THAN THE TOOLS THAT EXAMINE THEM
- 24. TECHNICAL UBIQUITY OF COMPUTERS ’ü« CRIMES OCCUR IN ALL JURISDICTIONS TRAINING LEA BECOMES A CHALLENGE TECHNOLOGY REVOLUTION LEADS TO NEWER SYSTEMS, DEVICES ETC..
- 25. OPERATIONAL ALL DATA MUST BE GATHERED AND EXAMINED FOR EVIDENCE ’üĘ GIGABYTES OF DATA ’üĘ PROBLEMS OF ’ü« STORAGE ’ü« ANALYSIS ’ü« PRESENTATION.. NO STANDARD SOLUTION AS YET
- 26. SOCIAL IT RESULTS IN ’ü« UNCERTAINITIES ABOUT EFFECTIVENESS OF CURRENT INVESTIGATION TECHNIQUES ’ü« SUB OPTIMAL USE OF RESOURCES PRIVACY CONCERNS
- 27. LEGAL USE & BOUNDS OF DIGITAL EVIDENCE IN LEGAL PROCEDURES STILL UNCLEAR CURRENT TOOLS & TECHNIQUES NOT RIGOROUSLY USED / CONTESTED IN COURT
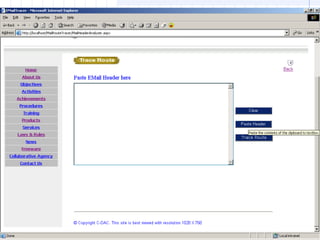
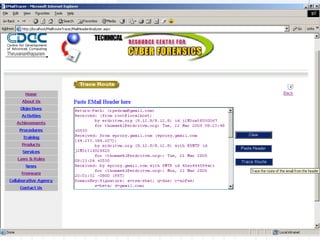
- 29. EMAIL TRACER FORENSIC TOOL
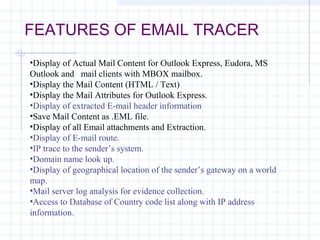
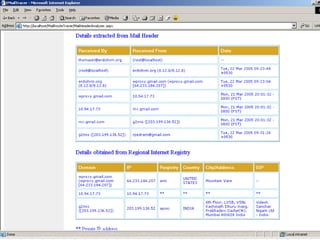
- 30. FEATURES OF EMAIL TRACER ŌĆóDisplay of Actual Mail Content for Outlook Express, Eudora, MS Outlook and mail clients with MBOX mailbox. ŌĆóDisplay the Mail Content (HTML / Text) ŌĆóDisplay the Mail Attributes for Outlook Express. ŌĆóDisplay of extracted E-mail header information ŌĆóSave Mail Content as .EML file. ŌĆóDisplay of all Email attachments and Extraction. ŌĆóDisplay of E-mail route. ŌĆóIP trace to the senderŌĆÖs system. ŌĆóDomain name look up. ŌĆóDisplay of geographical location of the senderŌĆÖs gateway on a world map. ŌĆóMail server log analysis for evidence collection. ŌĆóAccess to Database of Country code list along with IP address information.
- 31. EMAIL TRACING OVER WEB AS A PRE-EMPTIVE TOOL
- 32. EMAIL TRACING SERVICE Users can submit their tracing task to Email Tracer through web. Tracing IP Address upto city level (non- spoofed) Detection of spoofed mail Detailed report
- 37. FEATURES OF TRUE BACK DOS application with event based Windowing System. Self-integrity check. Minimum system configuration check. Extraction of system information Three modes of operation: - Seize - Acquire - Seize and Acquire ┬ĀDisk imaging through Parallel port. Disk imaging using Network Interface Card. Block by Block acquisition with data integrity check on each block. IDE/SCSI, USB, CD and Floppy acquisition. Acquisition of floppies and CDs in Batch mode. Write protection on all storage media except destination media. Checking for sterile destination media. Progress Bar display on all modes of operation. Report generation on all modes of operation. BIOS and ATA mode acquisition
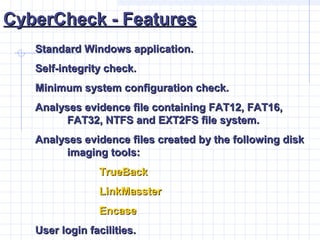
- 39. CyberCheck - FeaturesCyberCheck - Features Standard Windows application.Standard Windows application. Self-integrity check.Self-integrity check. Minimum system configuration check.Minimum system configuration check. Analyses evidence file containing FAT12, FAT16,Analyses evidence file containing FAT12, FAT16, FAT32, NTFS and EXT2FS file system.FAT32, NTFS and EXT2FS file system. Analyses evidence files created by the following diskAnalyses evidence files created by the following disk imaging tools:imaging tools: TrueBackTrueBack LinkMassterLinkMasster EncaseEncase User login facilities.User login facilities.
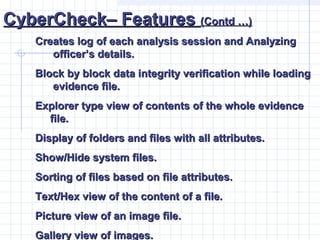
- 40. CyberCheckŌĆō FeaturesCyberCheckŌĆō Features (Contd ŌĆ”)(Contd ŌĆ”) Creates log of each analysis session and AnalyzingCreates log of each analysis session and Analyzing officerŌĆÖs details.officerŌĆÖs details. Block by block data integrity verification while loadingBlock by block data integrity verification while loading evidence file.evidence file. Explorer type view of contents of the whole evidenceExplorer type view of contents of the whole evidence file.file. Display of folders and files with all attributes.Display of folders and files with all attributes. Show/Hide system files.Show/Hide system files. Sorting of files based on file attributes.Sorting of files based on file attributes. Text/Hex view of the content of a file.Text/Hex view of the content of a file. Picture view of an image file.Picture view of an image file. Gallery view of images.Gallery view of images.
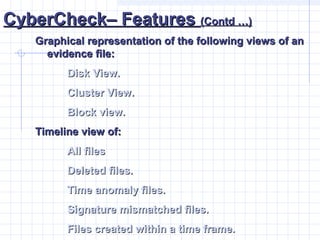
- 41. CyberCheckŌĆō FeaturesCyberCheckŌĆō Features (Contd ŌĆ”)(Contd ŌĆ”) Graphical representation of the following views of anGraphical representation of the following views of an evidence file:evidence file: Disk View.Disk View. Cluster View.Cluster View. Block view.Block view. Timeline view of:Timeline view of: All filesAll files Deleted files.Deleted files. Time anomaly files.Time anomaly files. Signature mismatched files.Signature mismatched files. Files created within a time frame.Files created within a time frame.
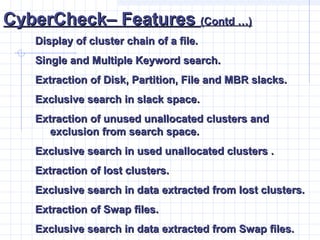
- 42. CyberCheckŌĆō FeaturesCyberCheckŌĆō Features (Contd ŌĆ”)(Contd ŌĆ”) Display of cluster chain of a file.Display of cluster chain of a file. Single and Multiple Keyword search.Single and Multiple Keyword search. Extraction of Disk, Partition, File and MBR slacks.Extraction of Disk, Partition, File and MBR slacks. Exclusive search in slack space.Exclusive search in slack space. Extraction of unused unallocated clusters andExtraction of unused unallocated clusters and exclusion from search space.exclusion from search space. Exclusive search in used unallocated clusters .Exclusive search in used unallocated clusters . Extraction of lost clusters.Extraction of lost clusters. Exclusive search in data extracted from lost clusters.Exclusive search in data extracted from lost clusters. Extraction of Swap files.Extraction of Swap files. Exclusive search in data extracted from Swap files.Exclusive search in data extracted from Swap files.
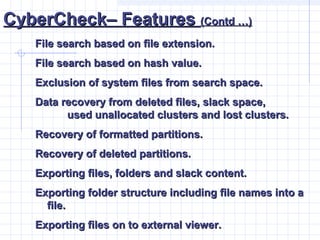
- 43. CyberCheckŌĆō FeaturesCyberCheckŌĆō Features (Contd ŌĆ”)(Contd ŌĆ”) File search based on file extension.File search based on file extension. File search based on hash value.File search based on hash value. Exclusion of system files from search space.Exclusion of system files from search space. Data recovery from deleted files, slack space,Data recovery from deleted files, slack space, used unallocated clusters and lost clusters.used unallocated clusters and lost clusters. Recovery of formatted partitions.Recovery of formatted partitions. Recovery of deleted partitions.Recovery of deleted partitions. Exporting files, folders and slack content.Exporting files, folders and slack content. Exporting folder structure including file names into aExporting folder structure including file names into a file.file. Exporting files on to external viewer.Exporting files on to external viewer.
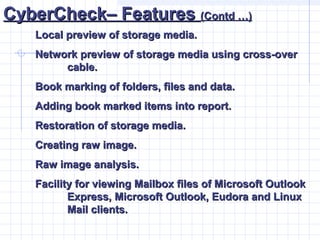
- 44. CyberCheckŌĆō FeaturesCyberCheckŌĆō Features (Contd ŌĆ”)(Contd ŌĆ”) Local preview of storage media.Local preview of storage media. Network preview of storage media using cross-overNetwork preview of storage media using cross-over cable.cable. Book marking of folders, files and data.Book marking of folders, files and data. Adding book marked items into report.Adding book marked items into report. Restoration of storage media.Restoration of storage media. Creating raw image.Creating raw image. Raw image analysis.Raw image analysis. Facility for viewing Mailbox files of Microsoft OutlookFacility for viewing Mailbox files of Microsoft Outlook Express, Microsoft Outlook, Eudora and LinuxExpress, Microsoft Outlook, Eudora and Linux Mail clients.Mail clients.
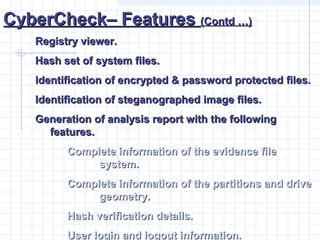
- 45. CyberCheckŌĆō FeaturesCyberCheckŌĆō Features (Contd ŌĆ”)(Contd ŌĆ”) Registry viewer.Registry viewer. Hash set of system files.Hash set of system files. Identification of encrypted & password protected files.Identification of encrypted & password protected files. Identification of steganographed image files.Identification of steganographed image files. Generation of analysis report with the followingGeneration of analysis report with the following features.features. Complete information of the evidence fileComplete information of the evidence file system.system. Complete information of the partitions and driveComplete information of the partitions and drive geometry.geometry. Hash verification details.Hash verification details. User login and logout information.User login and logout information.
- 46. CyberCheckŌĆō FeaturesCyberCheckŌĆō Features (Contd ŌĆ”)(Contd ŌĆ”) Exported content of text file and slackExported content of text file and slack information.information. Includes picture file as image.Includes picture file as image. Saving report, search hits and book markedSaving report, search hits and book marked items for later use.items for later use. Password protection of report.Password protection of report. Print report.Print report.
- 48. CASE #4 A young girl had been involved in a series of sexually explicit exchanges via instant messenger system and email. Upon investigation, the perpetrator was tracked to the home of a 50 year old prominent local physician. Computers seized from the physicianŌĆÖs house had 240GB hard disk each, full of files.
- 49. ISSUE #1 How to get convincing leads to go ahead with the case in a short time from among the overload of available material.
- 52. ISSUE #2 Computers contained many password protected/encrypted files. How to get into these files in a short time.
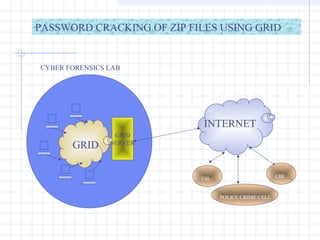
- 53. PASSWORD CRACKING GRID Enabled Password Cracker
- 54. GRID GRID SERVER FSL POLICE CRIME CELL CBI INTERNET PASSWORD CRACKING OF ZIP FILES USING GRID CYBER FORENSICS LAB
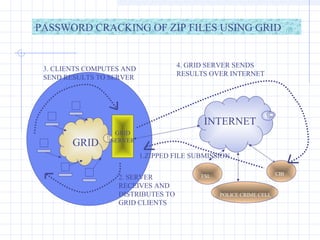
- 55. GRID GRID SERVER FSL POLICE CRIME CELL CBI INTERNET PASSWORD CRACKING OF ZIP FILES USING GRID 1.ZIPPED FILE SUBMISSION 2. SERVER RECEIVES AND DISTRIBUTES TO GRID CLIENTS 3. CLIENTS COMPUTES AND SEND RESULTS TO SERVER 4. GRID SERVER SENDS RESULTS OVER INTERNET
- 56. ISSUE #3 However, the case took a twist when it came to light that the doctorŌĆÖs 13-year- old son and 15 year old nephew had also been using the doctorŌĆÖs account. Who was at the keyboard then?
- 57. WHOŌĆÖS AT THE KEYBOARD? BIOMETRICS A software driver associated with the keyboard records the userŌĆÖs rhythm in typing. These rhythms are then used to generate a profile of the authentic user.
- 58. WHOŌĆÖS AT THE KEYBOARD? FORENSIC STYLISTICS A qualitative approach to authorship assesses errors and ŌĆ£idiosyncrasiesŌĆØ based on the examinerŌĆÖs experience. This approach could be quantified through Databasing.
- 59. WHOŌĆÖS AT THE KEYBOARD? STYLOMETRY It is quantitative and computational method, focusing on readily computable and countable language features, e.g. word length, phrase length, sentence length, vocabulary frequency, distribution of words of different lengths.
- 60. REAL CYBER FORENSIC CHALLENGE IS YET TO COME.. ŌĆ”.
- 61. GOAŌĆÖs SKYBUS MISHAP Konkan Railway Corporation Ltd's Skybus Metro dashed against a pole on the track during its trial run at Madgoan in Goa. "The skybus should have approached the station at the speed of 20 kmph. However, it was driving at 50 kmph. The sudden jerk after it hit the pole caused one person standing at the door, to fall off and two others to suffer major injuries."
- 62. QUESTIONS BEING ASKED Had the SKYBUS been tested sufficiently and should this controller bug have been found out during testing? WHO developed the control system software? Who carried out the design and who carried out the design approval?
Editor's Notes
- #4: GEQD, AVERAGE ONE CRIME/DAY, 2/3 QUALIFIED ENGINEERS, SEIZE/ACQUIRE/ANALYSE/COLLECT EVIDENCE/PRESERVE/DEPOSE, MOSTLY ECONOMIC OFFENCE; OTHERS CONSULT PRIVATE AGENCIES