Cyber Security in Bangladesh
- 1. Cyber Security The Present World Threat 1. Mahir Faysal 2015-2-55-0281. Mahir Faysal 2015-2-55-028 2. Md. Mohiuddin Murad 2015-2-55-0272. Md. Mohiuddin Murad 2015-2-55-027 3.Md. Jahirul Islam3.Md. Jahirul Islam 2015-2-55-0082015-2-55-008 4. Sadia Islam 2015-2-55-0204. Sadia Islam 2015-2-55-020 5. Md. Sagir Ahmed5. Md. Sagir Ahmed 2014-1-55-0382014-1-55-038 Presented ByPresented By
- 2. CONTENTS ïąINTRODUCTION ABOUT CYBER SECURITY ïąDESCRIPTION ïąTYPES OF ATTACKS ïąSECURITY/PREVENTIVE MEASURES ïąADVANTAGES ïąDISADVANTAGES ïąCONCLUSION
- 3. Cyber Security: ï Cyber security is the body of technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access. ï With an increasing amount of people getting connected to Internet, the security threats that cause massive harm are increasing also.
- 4. ï It is a combining form relating to information technology, the Internet, and virtual reality. Meaning of the Word CYBER
- 5. Need of cyber security ï―Cyber security is necessary since it helps in securing data from threats such as data theft or misuse, also safeguards your system from viruses.
- 6. Major security problems ï Virus ï Hacker ï Malware ï Trojan horses ï Password cracking ï Ransomware
- 7. Viruses and Worms ï A Virus is a âprogram that is loaded onto your computer without your knowledge and runs against your wishes
- 8. Solution ï― Install a security suite that protects the computer against threats such as viruses and worms.
- 10. Hackers ï―In common a hacker is a person who breaks into computers, usually by gaining access to administrative controls.
- 11. Types of Hackers ï―White Hat Hacker ï―Grey Hat Hacker ï―Black Hat Hacker
- 12. How To prevent hacking ï―It may be impossible to prevent computer hacking, however effective security controls including strong passwords, and the use of firewalls can helps.
- 13. Malware ï―The word "malware" comes from the term "MALicious softWARE." ï―Malware is any software that infects and damages a computer system without the owner's knowledge or permission.
- 14. To Stop Malware ï― Download an anti-malware program that also helps prevent infections. ï― Activate Network Threat Protection, Firewall, Antivirus.
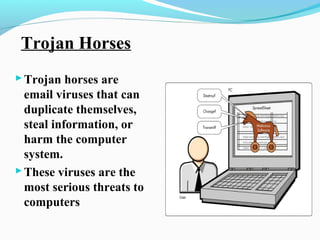
- 15. Trojan Horses ï―Trojan horses are email viruses that can duplicate themselves, steal information, or harm the computer system. ï―These viruses are the most serious threats to computers
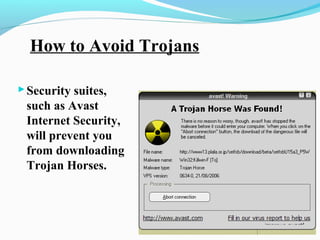
- 16. How to Avoid Trojans ï―Security suites, such as Avast Internet Security, will prevent you from downloading Trojan Horses.
- 17. Password Cracking ï―Password attacks are attacks by hackers that are able to determine passwords or find passwords to different protected electronic areas and social network sites.
- 18. How to Avoid Password Cracking Murad 302Murad 302 EncryptionEncryption 203 daruM203 daruM DecryptionDecryption Murad 302Murad 302
- 19. Ransomware & Present Cyber Security Situation in Bangladesh Ransomware : Malware that locks out computer and demands a ransom (payment) in exchange for access.
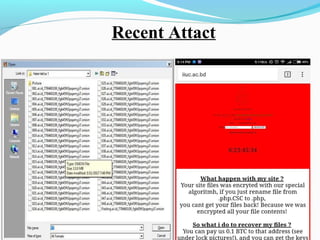
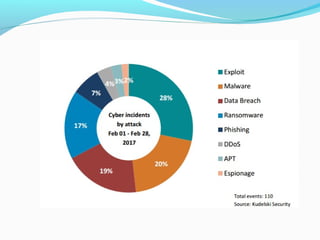
- 20. Recent Attact
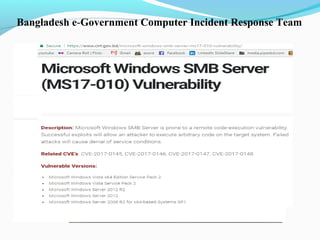
- 21. Bangladesh e-Government Computer Incident Response Team
- 22. Cyber Security Is EveryoneâsCyber Security Is Everyoneâs ResponsibilityResponsibility
- 23. Cyber Security Strategy â Bangladesh âĒ Security Policy, Legal Framework â ICT Act, 2006. â Digital Security Act 2016(Amendment) Bill, 2016 â Data Protection & Computer crimes âĒ Capacity building â Skill & Competence development âĒ Research and Development â Cyber Monitoring â Network Security âĒ International Collaboration
- 25. ADVANTAGES OF CYBER SECURITY ïPROTECTS THE COMPUTERS AGAINST VIRUS,WORMS AND MALWARE. ïPROTECTS AGAINST THE DATA FROM THEFT ïINCREASE IN CYBER DEFENSE ïINCREASES THE SECURITY ïWE CAN BROWSE THE SAFE WEBSITE ïINCREASE IN CYBER SPEED ïPROTECTS NETWORKS AND RESOURCES
- 26. DIS ADVANTAGES OF CYBER CRIMES ïžMAKES THE SYSTEM SLOWER THAN BEFORE. ïžFIREWALLS WOULD BE DIFFICULT TO CONFIGURE CORRECTLY. ïžHUGE AMOUNT OF LOSS IN MONEY FOR THE BANKS,COMPANIES ETC ïžHUGE AMOUNT OF DATA LOSS OCCURS IN THE DATABASE
- 27. Conclusion ïThe only system which is truly secure is one which is switched off and unplugged. ïSo , only way to be safe is Pay attention and Act smart.