Cybersecurity and Data Protection Executive Briefing
- 2. RFA ŌĆō GLOBAL TECHNOLOGY CONSULTANCY 30 Years Founded in 1989 550+ Clients 200+Engineers Latest certifications 24/7/365 Monitoring & Support GLOBAL OPERATIONS EMEA HQ in London WORLD CLASS LEADERSHIP TEAM
- 3. RFA ŌĆō FOCUS AREAS Cloud Innovation Automation
- 4. RFA ŌĆō SERVICES IT Service Management Cloud Design & Migration Managed Private & Public Cloud Development & Workflow Automation Compliance & RegTech Application Design & Hosting
- 5. 3 LINES OF DEFENCE CONSULTING Compliance Risk Management Governance
- 6. 3 LINES OF DEFENCE CONSULTING FINANCIAL SERVICES MULTINATIONAL CORPORATES PROFESSIONAL SERVICES SECTORS Compliance Financial crime prevention Governance / Ethics Legal / Expert Witness Operational risk COO Info Security Investigations SKILLS
- 7. DATA IS ESSENTIAL TO LIFE AND BUSINESS Environment ŌĆó Data is one of your most valuable assets ŌĆó Clients and staff expect fast systems and responses ŌĆó Millennials and children DATA DRIVEN WORLD Dangers ŌĆó Clients are less loyal ŌĆó No one is safe; large, small, mid sized businesses
- 8. WHAT IS DATA PROTECTION IN A DATA DRIVEN WORLD? Soft copy Hard copy Humans Hardware ŌĆó Protecting the information ŌĆó Ensuring the information is used correctly ŌĆó Security when adding, storing, deleting or removing data ŌĆó Protecting the firm, clients and third parties
- 9. WHY DOES DATA PROTECTION MATTER? ŌĆó Correct thing to do! ŌĆó Potential target ŌĆó Reputational risk / client retention ŌĆó Client expectations ŌĆó Proportionate risk based approach ŌĆó Legal / regulatory requirements
- 10. WHEN IT GOES WRONG? ŌĆó Australian Government ŌĆō Filing Cabinets ŌĆó Target ŌĆō Outsourcer risk (70m customers) ŌĆó Uber ŌĆō Ransom (57m clients/drivers) ŌĆó Morrisons ŌĆō Published payroll data ŌĆó Equifax ŌĆó SEC ŌĆó Laptops are always going missing
- 12. GDPR: THE FACTS ŌĆó Who is affected? ŌĆó Personal Data ŌĆó Data Controllers and Data Processors ŌĆó Consent
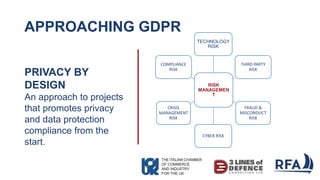
- 13. APPROACHING GDPR RISK MANAGEMEN T TECHNOLOGY RISK THIRD PARTY RISK FRAUD & MISCONDUCT RISK CYBER RISK CRISIS MANAGEMENT RISK COMPLIANCE RISK PRIVACY BY DESIGN An approach to projects that promotes privacy and data protection compliance from the start.
- 14. WHAT DOES THIS MEAN?
- 15. GAINING CONSENT POST GDPR Read our privacy statement Why we collect this information When you contact us, we collect this information to ensure we can respond appropriately, specifically we collect: Name: So we know how to address you. Your details will also be transferred to our customer relationship system and your name will form part of your unique identifier. Why we collect this information Phone: So we have a method of contacting you. This will also be transferred to our customer relationship system.Why we collect this information Subject: This will help categorise the contacts we have. It may also help us to understand common questions we receive, which can be answered in our FAQ section. Why we collect this information Description: This will also be transferred to our customer relationship system so if you contact us again, we have a history of our communications with you. Why we collect this information Email: So that we can contact you in an alternative way. This will also be transferred to our customer relationship system.Why we collect this information Company Name: So that we know which company you work for and can associate you with other contacts from the same company, and tailor the information that we send you.Privacy Statement None of the information provided through this form will be used for other reasons than to answer your query. It will not be shared with any third party. This information will be deleted 1 year after our last contact with you. If you do not want us to store your data please select the Send No data retained button. Otherwise you are consenting to the above. Send No data retained SendCancel
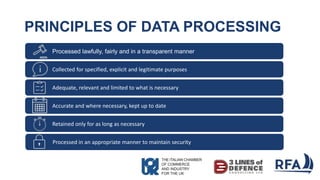
- 16. PRINCIPLES OF DATA PROCESSING Processed lawfully, fairly and in a transparent manner Adequate, relevant and limited to what is necessary Accurate and where necessary, kept up to date Retained only for as long as necessary Collected for specified, explicit and legitimate purposes Processed in an appropriate manner to maintain security
- 17. 5 STEP ACTION PLAN ŌĆó Data Analysis ŌĆó Technology Infrastructure Review ŌĆó Policy Review ŌĆó Supply Chain Review ŌĆó Building an Implementation Team
- 18. KEY TAKEAWAYS Data What data do you have and where is it stored? What do you use it for? Have you classified it as public, sensitive, confidential? How long can you keep the data for? Infrastructure Where is your data held? Do you use any cloud or outsourced technology service providers? Are your systems and networks secure? Processes Do you have Senior Management Systems and Controls SYSC, DR and Business Continuity plans in place, or a Cyber Incident Response Plan? Do you include cybersecurity training in your staff onboarding process? People Who do you share data with? Do you have a team in place to steer GDPR implementation? Do you have the right skills in house to ensure your data is protected and compliant?
- 19. Final Comment The cost and effort associated with building resilience and a solid data protection strategy can be high However, the cost of failure is far worse
- 20. WHO CAN I CALL FOR HELP? Simon Elvidge, Managing Director 3 Lines of Defence Consulting Tel: 020 7129 1270 Email: simon.elvidge@3ldc.com George Ralph, Managing Director RFA (UK) Ltd Tel: 0207 093 5000 Email gralph@rfa.com