Data Integrity Checks & Lunh Algorithm
- 2. #whoami – Savan Gadhiya ■ Senior Security Consultant at NotSoSecure ■ Hacker, Security Researcher, Developer and Bounty Hunter ☺ ■ 7 years of experience in Information Technology ■ Master of Engineering in IT Systems and Network Security ■ LinkedIn: https://in.linkedin.com/in/gadhiyasavan ■ Twitter: https://twitter.com/gadhiyasavan
- 3. Information Security – Key Concepts Integrity Availability Confidentiality
- 4. Information Security – Key Concepts ■ CIA/AIC Triad – Confidentiality – Data should be accessible to authorized persons only – Integrity – Data should be unaltered – Availability – Data should be available when required to authorized entities ■ Others – Authentication – Identify the user – Non-Repudiation – Data ownership disputes – Access Control – Who should be able to access what?
- 5. Data Integrity ■ As a process, data integrity verifies that data has remained unaltered in transit from creation to reception ■ Data must be kept free from corruption, modification, insertion, deletion or replay ■ Assurance of data integrity: – Data encryption, which locks data by cipher – Data backup, which stores a copy of data in an alternate location – Access controls, including assignment of read/write privileges – Input validation, to prevent incorrect data entry – Data validation, to certify uncorrupted transmission
- 6. Checksum ■ A checksum is a small-sized datum derived from a block of digital data for the purpose of detecting errors which may have been introduced during its transmission or storage ■ Checksum is usually applied to an installation file after it is received from the download server. By themselves, checksums are often used to verify data integrity but are not relied upon to verify data authenticity
- 7. Luhn Algorithm – Checksum formula ■ Luhn Algorithm also known as “modulus 10” or “mod 10” algorithm ■ A simple checksum formula used to validate a variety of identification numbers ■ Widely used for: – Credit Card Numbers – International Mobile Equipment Identity(IMEI) Numbers – Social Security Numbers – Social Insurance Numbers
- 8. Luhn Algorithm Checksum Digit • Right most digit Double Second Digit • Double the every other/second digit • Starting from next digit to Checksum • Right to Left (except the checksum) Sum Digits • Sum each digits Identify the Checksum • Method 1: • Take the units digit from Sum – e.g. 67 → 7 • Subtract units digit from 10 – e.g. 10 – 7 = 3 • If sum digit ends with 0 then checksum is 0 – 60 → 0 • Method 2: • Multiply sum with 9 – e.g. 67*9 = 603 • Units digit is checksum – e.g. 603 → 3
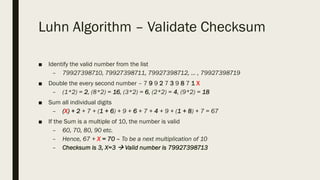
- 9. Luhn Algorithm – Validate Checksum ■ Identify the valid number from the list – 79927398710, 79927398711, 79927398712, … , 79927398719 ■ Double the every second number – 7 9 9 2 7 3 9 8 7 1 X – (1*2) = 2, (8*2) = 16, (3*2) = 6, (2*2) = 4, (9*2) = 18 ■ Sum all individual digits – (X) + 2 + 7 + (1 + 6) + 9 + 6 + 7 + 4 + 9 + (1 + 8) + 7 = 67 ■ If the Sum is a multiple of 10, the number is valid – 60, 70, 80, 90 etc. – Hence, 67 + X = 70 – To be a next multiplication of 10 – Checksum is 3, X=3 → Valid number is 79927398713
- 10. Luhn Algorithm – Penetration Testing ■ Luhn Algorithm/mod 10 will produce only ONE valid number from 10 sequential numbers ■ Most of the banking/payment websites prevent from brute-force attack and uses rate limit – Brute force the card numbers from 4242 4242 4242 0000 to 4242 4242 4242 9999 – 10,000 possibilities - Ah rate-limit is only 1,000  ■ Unique numbers will be only 1,000 then why do we need to brute-force all? ■ How can we brute force effectively using Lunn Number? – Burp Payload Processing ■ Extension: Burp Luhn Payload Processor
- 11. Demo – Burp Luhn Payload Processor ■ How can we brute force effectively using Lunn Number? – Burp Payload Processing ■ Extension: Burp Luhn Payload Processor – Figure shows list of valid numbers
- 12. References ■ https://en.wikipedia.org/wiki/Information_security ■ https://en.wikipedia.org/wiki/Luhn_algorithm ■ https://patentimages.storage.googleapis.com/ec/2a/f7/b9af046ed26128/US295 0048.pdf ■ https://github.com/EnableSecurity/burp-luhn-payload-processor
- 13. Questions?