Data security
- 1. IT Applications Theory šÝšÝßĢshows Data Security By Mark Kelly Vceit.com
- 2. Contents ? Procedures & equipment to protect data ? Consequences of not protecting data ĄŪZitsĄŊ
- 3. Data Security ? Virtual teams often work with confidential or secret data ? All data needs to be protected against loss or damage ? Sensitive information needs protection against theft
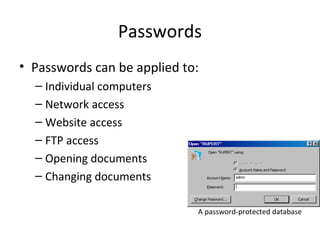
- 4. Passwords ? Passwords can be applied to: ĻC Individual computers ĻC Network access ĻC Website access ĻC FTP access ĻC Opening documents ĻC Changing documents A password-protected database
- 5. Biometric ID ? Passwords are weak protection ? Easily forgotten, discovered, guessed ? Biometric ID measures a unique physical attribute of an individual, e.g. ĻC Fingerprint ĻC Iris pattern (the coloured bit of the eye) ĻC Retinal pattern (the blood vessels at the back of the eye) ? CanĄŊt be copied, faked, stolen as passwords and swipe cards can
- 6. Encryption ? Makes information unreadable for unauthorised people ? Public Key encryption does not have an unlocking key - the weak point of all previous encryption systems ? Public key encryption (look up RSA, PGP, SSL) is very, VERY hard to break ? Even if an encrypted document is stolen or copied, it is worthless to the thief
- 7. Encryption ? SSL (Secure Socket Layer) encrypts web traffic ? Is active when the padlock in your browser snaps shut ? Messages between web servers (e.g. banks) and visitors are encrypted by the sender and decrypted by the recipient ? Secure sites sometimes identifiable by a HTTPS:// prefix
- 8. Access hierarchy ? Different users get different levels of access to data ? Level of access based on what they need to get their work done ? Prevents unskilled, stupid or evil people deliberately, carelessly or accidentally destroying data
- 9. Safe Disposal ? ĄŪDeletedĄŊ files are easily recovered ? To be safe, unwanted files should be wiped ? Military-grade wiping involves overwriting data at least 7 times with rubbish data ? Computers being disposed of should have their hard disks reformatted. ? But reformatting can be reversed! ? Some organisers shred used hard disks to be sure. The disks are physically pulverised.
- 10. Hard disk destruction Hours of crushing funĄ http://www.youtube.com/watch?v=sQYPCPB1g3o http://www.youtube.com/watch?v=8qImGK8bHjE
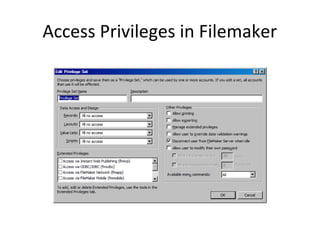
- 11. Access hierarchy ? Databases, for example, can assign rights such as: ĻC See some data, but not all ĻC See all data, but not add/delete/change change it ĻC Add data but not delete any ĻC Add and delete data but not change any programming or presentation layouts ĻC Access all areas
- 12. Access Privileges in Filemaker
- 13. Backups ? Backup = copying data so it can be restored if the original is lost or damaged ? Must be done regularly (daily!) ? Must be stored offsite ? Procedure must be tested and documented
- 14. Backup types ? Full = copy absolutely everything: new and old data and programs ? Incremental (partial, differential) = copy only files that are new or have been changed since the last full backup.
- 15. Typical Scheme ? Weekly full backups ? Daily incremental backups ? To restore data, reload the latest full backup and then add on all the incremental backups made since then. ? Look up Ą°grandfather-father-sonĄą scheme, a variety of Ą°rotation backupĄą
- 16. Backup Media ? Ą°MediaĄą = what the data is saved to ? Tape = large capacity, slow, wears out, expensive. Very common ? Removable hard disk = fast, large capacity, cheap. ? CD/DVD = relatively low capacity, easily damaged. Non-magnetic, so not hurt by electromagnetic fields as are tapes, HDDs.
- 17. Backup Media ? Selection criteria: ĻC Read/write speed ĻC Capacity ĻC Lifetime of recorded data ĻC Durability of media
- 18. Archiving ? Copy obsolete data to secondary storage (e.g. DVD) and delete the original data. ? Backing up = copy data, keep the original.
- 19. Continuous Data Protection (CDP) ? Changed files are automatically saved to local or remote storage ? Different versions of the same-named file can be restored ? Can save to cloud, local network, or remtoe friendĄŊs computer ? E.g. CRASHPLAN.COM
- 20. Virus scanners ? Must have up-to-date virus definitions ? Must be running all the time ? Must be accurate: ĻC false-positives ĻC wrongly believes a virus exists ĻC false-negatives ĻC fails to identify a virus ? Even market-leading products are imperfect ? Some free products (e.g. Avira) outperformed Symantec & McAfee in a test in 2009.
- 21. Other scanners ? Malware ĻC spyware, adware. Either does bad things (e.g. monitoring usersĄŊ actions) or is badly programmed and badly affects the stability of computers.
- 22. Other scanners Trojan Horses ĻC bad software installed by users who think itĄŊs innocent. Payloads: ĻC Keylogger: records passwords, credit card info, bank account logins & sends them to hackers. ĻC Spamming agent: your computer acts as a zombie sending spam on behalf of the hacker ĻC Distributed Denial Of Service (DDOS) attack: your computer is taken over and joins a concerted attack on a server chosen by the hacker.
- 23. Firewalls ? Closes unused internet communication ports ? Your computer has 65535 of them, but you only use about 3. ? Hackers can gain entry to a PC through unguarded ports ? Firewalls close the unused ports ? Open ports are watched to ensure only authorised programs use them (preventing Trojans sending spam or DDOS attacks)
- 24. Software Firewalls ? Can be software or hardware firewalls ? Software: Windows Firewall, Zone Alarm ? Needs training when first installed. You teach it which programs are allowed to connect to the internet
- 25. Hardware firewalls ? Routers ĻC on all Local Area Networks, and in nearly all home/office cable/ADSL modems ? Can use Stateful Packet Inspection (SPI) to examine inside data packets to see if theyĄŊre harmful. ? Protect against incoming bad data, but not outgoing bad data. If youĄŊre already infected by a Trojan, a router wonĄŊt stop your PC sending spam, keylogs etc
- 26. Consequences of not protecting data
- 27. Consequences ? loss of trade secrets ? potential violation of the Privacy Policy if personal information is damaged or released ? loss of reputation as a trustworthy organisation ? loss of income after catastrophic data loss destroys your ability to get paid by customers or conduct business ? prosecution by the tax office if tax records are lost ? corporate death
- 28. IT APPLICATIONS SLIDESHOWS By Mark Kelly mark@vceit.com vceit.com These slideshows may be freely used, modified or distributed by teachers and students anywhere on the planet (but not elsewhere). They may NOT be sold. They must NOT be redistributed if you modify them.