DataPower DoS/DDoS
Download as pptx, pdf0 likes241 views
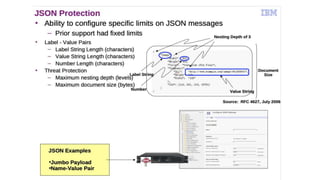
The document discusses the application of policies to JSON payloads or any well-formed payloads. It mentions the use of SLM or rate-limit policies to implement these measures. This indicates a focus on controlling data flow and management.
1 of 11
Downloaded 12 times







Ad
Recommended
AWS view of Financial Services Industry
AWS view of Financial Services IndustryAmazon Web Services LATAM
╠²
The document outlines how Amazon Web Services (AWS) assists financial institutions in transitioning to cloud computing, emphasizing the need for agile, cost-effective solutions that improve customer engagement and operational efficiency. It highlights AWS's extensive services tailored for the financial sector, including compliance, risk management, and data analytics, while showcasing success stories from various Latin American companies transitioning to AWS. Additionally, it discusses the evolving landscape of financial services and the growing necessity of cloud adoption for competitive advantage and transformation.MySQL Operator for Kubernetes
MySQL Operator for KubernetesKenny Gryp
╠²
The document introduces the MySQL Operator for Kubernetes, which automates the deployment and management of MySQL databases on Kubernetes. It leverages MySQL InnoDB Cluster to deploy high availability MySQL clusters on Kubernetes with no data loss. The operator provides self-healing, backup/restore, and allows scaling MySQL servers and routers with minimal downtime. A public beta of the open source community edition will be released in the coming weeks.DataPower API Gateway Performance Benchmarks
DataPower API Gateway Performance BenchmarksIBM DataPower Gateway
╠²
The document discusses the performance capabilities of IBM API Connect and DataPower, highlighting various deployment options including physical appliances and virtual containers. It emphasizes a 10x increase in performance with a natively built API gateway, capable of handling high transaction rates with low latency. Additionally, it provides comparative performance metrics for different gateway configurations and includes disclaimers regarding the information presented.Oracle Cloud Infrastructure Overview Deck.pptx
Oracle Cloud Infrastructure Overview Deck.pptxLabibKhairi
╠²
Oracle Cloud Infrastructure is a cloud platform designed to help customers modernize, adapt, and innovate. It provides over 100 platform services to support workloads, runs in 46 global cloud regions, and offers flexibility through public cloud, hybrid cloud, and multicloud options. OCI aims to help customers modernize their entire application portfolio and infrastructure more efficiently and with more agility.Kubernetes Native Infrastructure and CoreOS Operator Framework for 5G Edge Cl...
Kubernetes Native Infrastructure and CoreOS Operator Framework for 5G Edge Cl...Hidetsugu Sugiyama
╠²
The document presents an overview of Kubernetes native infrastructure and operator frameworks tailored for 5G edge cloud computing, focusing on deployments using OpenShift/Kubernetes on OpenStack. Key subjects include the adaptation of network functions virtualization (NFV), service-based architecture (SBA) for 5G, and the integration of artificial intelligence (AI) capabilities at the edge. Additionally, it highlights operational frameworks for managing container applications and emphasizes the transition from traditional virtualization models to a Kubernetes-centric infrastructure for enhanced service delivery and scalability.Python for Linux System Administration
Python for Linux System Administrationvceder
╠²
The document discusses the advantages of using Python for Linux system administration compared to traditional scripting languages like Bash, Perl, and Awk. It highlights Python's readability, built-in libraries, and versatility while addressing some limitations, such as less common regular expressions and indentation syntax. Additionally, it mentions practical examples and external resources for further learning, as well as the upcoming transition to Python 3.Microservices, Node, Dapr and more - Part One (Fontys Hogeschool, Spring 2022)
Microservices, Node, Dapr and more - Part One (Fontys Hogeschool, Spring 2022)Lucas Jellema
╠²
The document discusses the implementation and benefits of microservices architecture using Node.js and Dapr, highlighting their design, interaction, and operational advantages. It covers essential topics like state management, communication via HTTP/gRPC, and asynchronous message handling with Apache Kafka. The content is oriented towards developers, providing practical insights and hands-on sessions for efficiently utilizing these technologies in real-world applications.10.) vxlan
10.) vxlanJeff Green
╠²
The document provides a comprehensive overview of VXLAN encapsulation, including its terminology, scalability limits, and configuration methods for Extreme Networks. It discusses the hardware requirements, network topologies, and design considerations, highlighting features like dynamic VNI learning and automation through the 'ezvxlan.py' script. Key points include the lack of IP multicast support and specific limits on virtual network identifiers across switches.Uncover the Flex Gateway with a Demonstration (1).pdf
Uncover the Flex Gateway with a Demonstration (1).pdfPankajGoyal164048
╠²
The document provides an agenda and details for a MuleSoft Meetup event on demonstrating the Flex Gateway. The agenda includes introductions, a discussion on universal API management, why API gateways are important, and what a secure API gateway does. It then covers Anypoint Platform gateway options, an introduction to Flex Gateway, benefits and modes of Flex Gateway, and a planned demo. Details are also provided on speakers, a safe harbor statement, housekeeping, and deployment options for Flex Gateway using Docker.Bndtools and Maven: A Brave New World - N Bartlett & T Ward
Bndtools and Maven: A Brave New World - N Bartlett & T Wardmfrancis
╠²
The document provides an overview of the bndtools and Maven integration for OSGi development, detailing the history, workflow, and project structure. It includes instructions for generating modules and testing bundles, along with coding examples and essential commands for setting up a project. Additionally, the document outlines the creation of a web application and various components within the OSGi framework.IBK ņŗ£ņŖżĒģ£ņØś Ēü┤ļØ╝ņÜ░ļō£ ĻĖ░ļ░ś ĻĖłņ£Ą Ēöīļ×½ĒÅ╝ ļ╣äņ”łļŗłņŖż ņĀäļץ - AWS Summit Seoul 2017
IBK ņŗ£ņŖżĒģ£ņØś Ēü┤ļØ╝ņÜ░ļō£ ĻĖ░ļ░ś ĻĖłņ£Ą Ēöīļ×½ĒÅ╝ ļ╣äņ”łļŗłņŖż ņĀäļץ - AWS Summit Seoul 2017Amazon Web Services Korea
╠²
Ansible Automation - Enterprise Use Cases | Juncheng Anthony Lin
Ansible Automation - Enterprise Use Cases | Juncheng Anthony LinVietnam Open Infrastructure User Group
╠²
This document discusses using Ansible for automation across various IT use cases. It provides examples of how Ansible can be used for infrastructure orchestration, patch management, network automation, and managing various network devices and platforms including Cisco, Palo Alto, and Fortinet devices. It also provides examples of playbooks for tasks like provisioning servers, configuring firewall rules, and checking for configuration drift. Overall it promotes Ansible as a simple, agentless, and extensible automation tool that can automate technologies across IT operations, DevOps, security and more.AMQP
AMQPKarlen Kishmiryan
╠²
This document provides an introduction and overview of message queueing and the Advanced Message Queueing Protocol (AMQP). It discusses why messaging is useful, how message queues work, and the main features of message queueing including decoupling applications and asynchronous communication. It then describes AMQP specifically, including why it was developed, how it defines a network protocol and message model, and some key AMQP concepts like exchanges, bindings, queues, and message routing.API Integration For Building Software Applications Powerpoint Presentation Sl...
API Integration For Building Software Applications Powerpoint Presentation Sl...║▌║▌▀ŻTeam
╠²
The document discusses the development and implementation of Application Programming Interfaces (APIs) in relation to business goals, highlighting the importance of API solutions, integration processes, testing pipelines, and team requirements. It provides insights into the financial implications before and after API implementation, current API issues, and features that enhance performance and security. Additionally, it includes a roadmap for API development and budget estimates, emphasizing the need for effective management and strategic alignment with organizational goals.Dell Boomi Integration with Salesforce
Dell Boomi Integration with SalesforceNagarjuna Kaipu
╠²
Dell Boomi is a cloud integration platform that connects cloud and on-premises applications. It has a low-code interface that makes integration easy through a drag-and-drop visual workflow. The integration process in Boomi has three phases - build, deploy, and manage. In the build phase, the integration logic is specified by connecting input sources to output destinations and mapping the data fields. The process is then deployed and monitored in the other phases. For example, a process can be built to get account details from Salesforce as input, check if an account already exists in a MySQL database, and insert it if not.Engage.UG 2022 - Domino TOTP/2FA - Best Practices and Pitfalls
Engage.UG 2022 - Domino TOTP/2FA - Best Practices and PitfallsMilan Matejic
╠²
This document discusses best practices and pitfalls for implementing Time-based One-Time Password (TOTP) two-factor authentication (2FA) with HCL Domino. It covers topics such as motivation, terminology, how TOTP works, prerequisites, setup instructions, user and administrator workflows, troubleshooting, questions and answers, and references. The document provides detailed steps for configuring TOTP authentication for both Domino servers and Traveler mobile clients.AWS AppFlow
AWS AppFlowManas Mondal
╠²
Amazon AppFlow allows administrators to automate data flows between AWS services and SaaS applications like Salesforce, Zendesk, and ServiceNow without months of waiting for IT integration projects. It can transfer data both to and from SaaS applications and AWS services, encrypting the data in transit. Some SaaS applications integrate with AWS PrivateLink for an extra layer of security by keeping traffic on the Amazon network. AppFlow also simplifies capturing and analyzing SaaS data using AWS services like Glue, Athena, and Redshift.Distributed Locking in Mule
Distributed Locking in MuleSunil Kumar
╠²
Mule provides distributed locking capabilities through a lock factory that custom components can access programmatically to synchronize access to resources across a server cluster. With Mule's locks, code can be deployed to a single server or cluster without issues coordinating shared resources. Mule's locking system offers a simple API for components to use shared locks.Custom Reports & Integrations with GraphQL
Custom Reports & Integrations with GraphQLLeanIX GmbH
╠²
The document provides insights into utilizing GraphQL for creating custom reports and integrations with LeanIX, highlighting its advantages over REST in terms of performance and customization. It outlines motivations for embedding LeanIX, presents case studies, and introduces the LeanIX custom report framework and its functionalities. Key takeaways emphasize the ease of using GraphQL directly from the UI and the support available to get started.Apache Kafka® Use Cases for Financial Services
Apache Kafka® Use Cases for Financial Servicesconfluent
╠²
The document discusses various use cases for Confluent Kafka in the financial services sector, highlighting a shift from traditional batch processing to real-time data streaming for fraud detection, credit analytics, and regulatory compliance. It emphasizes the importance of modern data platforms supporting event processing to enhance customer experiences, optimize operational data, and facilitate regulatory requirements. Additionally, it covers challenges related to legacy systems and the modernization of data architecture through microservices and cloud integration.Docker Introduction
Docker IntroductionHao Fan
╠²
This document discusses Docker, including what it is, why it is used, and how it works. Docker provides lightweight software containers that package code and its dependencies so the application runs quickly and consistently on any computing infrastructure. It allows applications to be easily deployed and migrated across computing environments. The document outlines how Docker addresses issues like managing multiple software stacks and hardware environments by creating portable containers that can be run anywhere without reconfiguration. Examples of using Docker for microservices, DevOps, and data centers are also provided.The business case for SD WAN in the enterprise
The business case for SD WAN in the enterprise Colt Technology Services
╠²
The document discusses the business case for SD-WAN in enterprises, outlining the benefits and use cases from real implementations. It emphasizes two main customer propositions, on-demand and multi-site WAN solutions, and highlights the strong demand for SD-WAN in various sectors such as automotive and banking. The report also presents cost comparisons and automation benefits associated with SD-WAN deployments.Introduction to Azure Blueprints
Introduction to Azure BlueprintsCheah Eng Soon
╠²
Azure Blueprints allows cloud architects to create a repeatable set of Azure resources that align with organizational standards. This tool facilitates rapid environment setup while ensuring compliance through built-in components. It includes features such as assignment sequencing, resource locking, and various artifact management for organized deployment.VPNaaS in Neutron
VPNaaS in NeutronKazunori Takeuchi
╠²
- VPNaaS in Neutron aims to provide virtual private network services to OpenStack tenants through the Neutron API and plugins.
- Initial work focused on IPsec VPN support, including defining a resource model and APIs for VPN services, connections, policies and more.
- Future work will explore supporting BGP/MPLS VPNs, which provide inter-AS connectivity and require integration with external MPLS domains and protocols like BGP.
- Two potential architectures are proposed for BGP/MPLS VPN support: one relying on configuring provider edge routers from Neutron, and another using an L3 agent and separate controller/forwarder.Virtualization and cloud computing
Virtualization and cloud computingDeep Gupta
╠²
The document discusses the fundamentals of virtualization and cloud computing, emphasizing their importance in resource management, cost efficiency, and scalability. It covers various types of virtualization, cloud deployment models, and specific applications for industries such as banking. Additionally, it addresses security challenges and outlines a community cloud model specifically designed for banking applications.The Top 5 Apache Kafka Use Cases and Architectures in 2022
The Top 5 Apache Kafka Use Cases and Architectures in 2022Kai W├żhner
╠²
This document discusses the top 5 use cases and architectures for data in motion in 2022. It describes:
1) The Kappa architecture as an alternative to the Lambda architecture that uses a single stream to handle both real-time and batch data.
2) Hyper-personalized omnichannel experiences that integrate customer data from multiple sources in real-time to provide personalized experiences across channels.
3) Multi-cloud deployments using Apache Kafka and data mesh architectures to share data across different cloud platforms.
4) Edge analytics that deploy stream processing and Kafka brokers at the edge to enable low-latency use cases and offline functionality.
5) Real-time cybersecurity applications that use streaming data[ßäŗßģ®ßäæßģ│ßå½ßäēßģ®ßäēßģ│ßäÅßģźßå½ßäēßģźßå»ßäÉßģĄßå╝] VMware ßäāßģóßäŗßģĪßå½ Ļ▓ĆĒåĀļź╝ ņ£äĒĢ£ ĒöäļØ╝ņØ┤ļ╣Ś Ēü┤ļØ╝ņÜ░ļō£ ņåöļŻ©ņģś ņĀ£ņ¢Ė
[ßäŗßģ®ßäæßģ│ßå½ßäēßģ®ßäēßģ│ßäÅßģźßå½ßäēßģźßå»ßäÉßģĄßå╝] VMware ßäāßģóßäŗßģĪßå½ Ļ▓ĆĒåĀļź╝ ņ£äĒĢ£ ĒöäļØ╝ņØ┤ļ╣Ś Ēü┤ļØ╝ņÜ░ļō£ ņåöļŻ©ņģś ņĀ£ņ¢ĖOpen Source Consulting
╠²
VMņø©ņ¢┤ ļīĆņ▓┤ ņĀäļץ ņäĖļ»ĖļéśņŚÉņä£ ņśżĒöłņåīņŖżņ╗©ņäżĒīģ Ļ╣ĆĒśĖņ¦ä ņāüļ¼┤ļŗś ņäĖņģśņØĖ 'VMware ļīĆņĢł Ļ▓ĆĒåĀļź╝ ņ£äĒĢ£ ĒöäļØ╝ņØ┤ļ╣Ś Ēü┤ļØ╝ņÜ░ļō£ ņåöļŻ©ņģś ņĀ£ņ¢Ė' ļ░£Ēæ£ ņ×ÉļŻīņ×ģļŗłļŗż. Grokking Techtalk #39: How to build an event driven architecture with Kafka ...
Grokking Techtalk #39: How to build an event driven architecture with Kafka ...Grokking VN
╠²
The document discusses building an event-driven architecture using Apache Kafka and Kafka Connect. It describes how VeXeRe uses this approach to stream data from their MS SQL database into Kafka. Key points covered include event sourcing, how Kafka Connect works using connectors and tasks, best practices for monitoring connectors, and handling database schema evolution. Real-world use cases at VeXeRe like syncing data to data warehouses and search indexes are also examined.APIConnect Security Best Practice
APIConnect Security Best PracticeShiu-Fun Poon
╠²
The document outlines security best practices for IBM API Connect and DataPower Gateway, emphasizing the importance of configurable security measures, monitoring, and traffic management. It details functionalities such as API discovery, usage analytics, and OAuth support for compliance with regulations like PSD2 and Open Banking. Additionally, it highlights the need for robust access control, load management, and dynamic security policies to protect APIs against various cyber threats.GraphQL Security
GraphQL SecurityShiu-Fun Poon
╠²
The document discusses GraphQL as a query language that allows users to specify the exact data they need from a single endpoint, contrasting it with REST. It outlines various security considerations such as transport protection, rate limiting, data leakage, authentication methods, and authorization strategies. Additionally, it highlights the need for careful management of query complexity and compliance with regulations like GDPR and PCI compliance.More Related Content
What's hot (20)
Uncover the Flex Gateway with a Demonstration (1).pdf
Uncover the Flex Gateway with a Demonstration (1).pdfPankajGoyal164048
╠²
The document provides an agenda and details for a MuleSoft Meetup event on demonstrating the Flex Gateway. The agenda includes introductions, a discussion on universal API management, why API gateways are important, and what a secure API gateway does. It then covers Anypoint Platform gateway options, an introduction to Flex Gateway, benefits and modes of Flex Gateway, and a planned demo. Details are also provided on speakers, a safe harbor statement, housekeeping, and deployment options for Flex Gateway using Docker.Bndtools and Maven: A Brave New World - N Bartlett & T Ward
Bndtools and Maven: A Brave New World - N Bartlett & T Wardmfrancis
╠²
The document provides an overview of the bndtools and Maven integration for OSGi development, detailing the history, workflow, and project structure. It includes instructions for generating modules and testing bundles, along with coding examples and essential commands for setting up a project. Additionally, the document outlines the creation of a web application and various components within the OSGi framework.IBK ņŗ£ņŖżĒģ£ņØś Ēü┤ļØ╝ņÜ░ļō£ ĻĖ░ļ░ś ĻĖłņ£Ą Ēöīļ×½ĒÅ╝ ļ╣äņ”łļŗłņŖż ņĀäļץ - AWS Summit Seoul 2017
IBK ņŗ£ņŖżĒģ£ņØś Ēü┤ļØ╝ņÜ░ļō£ ĻĖ░ļ░ś ĻĖłņ£Ą Ēöīļ×½ĒÅ╝ ļ╣äņ”łļŗłņŖż ņĀäļץ - AWS Summit Seoul 2017Amazon Web Services Korea
╠²
Ansible Automation - Enterprise Use Cases | Juncheng Anthony Lin
Ansible Automation - Enterprise Use Cases | Juncheng Anthony LinVietnam Open Infrastructure User Group
╠²
This document discusses using Ansible for automation across various IT use cases. It provides examples of how Ansible can be used for infrastructure orchestration, patch management, network automation, and managing various network devices and platforms including Cisco, Palo Alto, and Fortinet devices. It also provides examples of playbooks for tasks like provisioning servers, configuring firewall rules, and checking for configuration drift. Overall it promotes Ansible as a simple, agentless, and extensible automation tool that can automate technologies across IT operations, DevOps, security and more.AMQP
AMQPKarlen Kishmiryan
╠²
This document provides an introduction and overview of message queueing and the Advanced Message Queueing Protocol (AMQP). It discusses why messaging is useful, how message queues work, and the main features of message queueing including decoupling applications and asynchronous communication. It then describes AMQP specifically, including why it was developed, how it defines a network protocol and message model, and some key AMQP concepts like exchanges, bindings, queues, and message routing.API Integration For Building Software Applications Powerpoint Presentation Sl...
API Integration For Building Software Applications Powerpoint Presentation Sl...║▌║▌▀ŻTeam
╠²
The document discusses the development and implementation of Application Programming Interfaces (APIs) in relation to business goals, highlighting the importance of API solutions, integration processes, testing pipelines, and team requirements. It provides insights into the financial implications before and after API implementation, current API issues, and features that enhance performance and security. Additionally, it includes a roadmap for API development and budget estimates, emphasizing the need for effective management and strategic alignment with organizational goals.Dell Boomi Integration with Salesforce
Dell Boomi Integration with SalesforceNagarjuna Kaipu
╠²
Dell Boomi is a cloud integration platform that connects cloud and on-premises applications. It has a low-code interface that makes integration easy through a drag-and-drop visual workflow. The integration process in Boomi has three phases - build, deploy, and manage. In the build phase, the integration logic is specified by connecting input sources to output destinations and mapping the data fields. The process is then deployed and monitored in the other phases. For example, a process can be built to get account details from Salesforce as input, check if an account already exists in a MySQL database, and insert it if not.Engage.UG 2022 - Domino TOTP/2FA - Best Practices and Pitfalls
Engage.UG 2022 - Domino TOTP/2FA - Best Practices and PitfallsMilan Matejic
╠²
This document discusses best practices and pitfalls for implementing Time-based One-Time Password (TOTP) two-factor authentication (2FA) with HCL Domino. It covers topics such as motivation, terminology, how TOTP works, prerequisites, setup instructions, user and administrator workflows, troubleshooting, questions and answers, and references. The document provides detailed steps for configuring TOTP authentication for both Domino servers and Traveler mobile clients.AWS AppFlow
AWS AppFlowManas Mondal
╠²
Amazon AppFlow allows administrators to automate data flows between AWS services and SaaS applications like Salesforce, Zendesk, and ServiceNow without months of waiting for IT integration projects. It can transfer data both to and from SaaS applications and AWS services, encrypting the data in transit. Some SaaS applications integrate with AWS PrivateLink for an extra layer of security by keeping traffic on the Amazon network. AppFlow also simplifies capturing and analyzing SaaS data using AWS services like Glue, Athena, and Redshift.Distributed Locking in Mule
Distributed Locking in MuleSunil Kumar
╠²
Mule provides distributed locking capabilities through a lock factory that custom components can access programmatically to synchronize access to resources across a server cluster. With Mule's locks, code can be deployed to a single server or cluster without issues coordinating shared resources. Mule's locking system offers a simple API for components to use shared locks.Custom Reports & Integrations with GraphQL
Custom Reports & Integrations with GraphQLLeanIX GmbH
╠²
The document provides insights into utilizing GraphQL for creating custom reports and integrations with LeanIX, highlighting its advantages over REST in terms of performance and customization. It outlines motivations for embedding LeanIX, presents case studies, and introduces the LeanIX custom report framework and its functionalities. Key takeaways emphasize the ease of using GraphQL directly from the UI and the support available to get started.Apache Kafka® Use Cases for Financial Services
Apache Kafka® Use Cases for Financial Servicesconfluent
╠²
The document discusses various use cases for Confluent Kafka in the financial services sector, highlighting a shift from traditional batch processing to real-time data streaming for fraud detection, credit analytics, and regulatory compliance. It emphasizes the importance of modern data platforms supporting event processing to enhance customer experiences, optimize operational data, and facilitate regulatory requirements. Additionally, it covers challenges related to legacy systems and the modernization of data architecture through microservices and cloud integration.Docker Introduction
Docker IntroductionHao Fan
╠²
This document discusses Docker, including what it is, why it is used, and how it works. Docker provides lightweight software containers that package code and its dependencies so the application runs quickly and consistently on any computing infrastructure. It allows applications to be easily deployed and migrated across computing environments. The document outlines how Docker addresses issues like managing multiple software stacks and hardware environments by creating portable containers that can be run anywhere without reconfiguration. Examples of using Docker for microservices, DevOps, and data centers are also provided.The business case for SD WAN in the enterprise
The business case for SD WAN in the enterprise Colt Technology Services
╠²
The document discusses the business case for SD-WAN in enterprises, outlining the benefits and use cases from real implementations. It emphasizes two main customer propositions, on-demand and multi-site WAN solutions, and highlights the strong demand for SD-WAN in various sectors such as automotive and banking. The report also presents cost comparisons and automation benefits associated with SD-WAN deployments.Introduction to Azure Blueprints
Introduction to Azure BlueprintsCheah Eng Soon
╠²
Azure Blueprints allows cloud architects to create a repeatable set of Azure resources that align with organizational standards. This tool facilitates rapid environment setup while ensuring compliance through built-in components. It includes features such as assignment sequencing, resource locking, and various artifact management for organized deployment.VPNaaS in Neutron
VPNaaS in NeutronKazunori Takeuchi
╠²
- VPNaaS in Neutron aims to provide virtual private network services to OpenStack tenants through the Neutron API and plugins.
- Initial work focused on IPsec VPN support, including defining a resource model and APIs for VPN services, connections, policies and more.
- Future work will explore supporting BGP/MPLS VPNs, which provide inter-AS connectivity and require integration with external MPLS domains and protocols like BGP.
- Two potential architectures are proposed for BGP/MPLS VPN support: one relying on configuring provider edge routers from Neutron, and another using an L3 agent and separate controller/forwarder.Virtualization and cloud computing
Virtualization and cloud computingDeep Gupta
╠²
The document discusses the fundamentals of virtualization and cloud computing, emphasizing their importance in resource management, cost efficiency, and scalability. It covers various types of virtualization, cloud deployment models, and specific applications for industries such as banking. Additionally, it addresses security challenges and outlines a community cloud model specifically designed for banking applications.The Top 5 Apache Kafka Use Cases and Architectures in 2022
The Top 5 Apache Kafka Use Cases and Architectures in 2022Kai W├żhner
╠²
This document discusses the top 5 use cases and architectures for data in motion in 2022. It describes:
1) The Kappa architecture as an alternative to the Lambda architecture that uses a single stream to handle both real-time and batch data.
2) Hyper-personalized omnichannel experiences that integrate customer data from multiple sources in real-time to provide personalized experiences across channels.
3) Multi-cloud deployments using Apache Kafka and data mesh architectures to share data across different cloud platforms.
4) Edge analytics that deploy stream processing and Kafka brokers at the edge to enable low-latency use cases and offline functionality.
5) Real-time cybersecurity applications that use streaming data[ßäŗßģ®ßäæßģ│ßå½ßäēßģ®ßäēßģ│ßäÅßģźßå½ßäēßģźßå»ßäÉßģĄßå╝] VMware ßäāßģóßäŗßģĪßå½ Ļ▓ĆĒåĀļź╝ ņ£äĒĢ£ ĒöäļØ╝ņØ┤ļ╣Ś Ēü┤ļØ╝ņÜ░ļō£ ņåöļŻ©ņģś ņĀ£ņ¢Ė
[ßäŗßģ®ßäæßģ│ßå½ßäēßģ®ßäēßģ│ßäÅßģźßå½ßäēßģźßå»ßäÉßģĄßå╝] VMware ßäāßģóßäŗßģĪßå½ Ļ▓ĆĒåĀļź╝ ņ£äĒĢ£ ĒöäļØ╝ņØ┤ļ╣Ś Ēü┤ļØ╝ņÜ░ļō£ ņåöļŻ©ņģś ņĀ£ņ¢ĖOpen Source Consulting
╠²
VMņø©ņ¢┤ ļīĆņ▓┤ ņĀäļץ ņäĖļ»ĖļéśņŚÉņä£ ņśżĒöłņåīņŖżņ╗©ņäżĒīģ Ļ╣ĆĒśĖņ¦ä ņāüļ¼┤ļŗś ņäĖņģśņØĖ 'VMware ļīĆņĢł Ļ▓ĆĒåĀļź╝ ņ£äĒĢ£ ĒöäļØ╝ņØ┤ļ╣Ś Ēü┤ļØ╝ņÜ░ļō£ ņåöļŻ©ņģś ņĀ£ņ¢Ė' ļ░£Ēæ£ ņ×ÉļŻīņ×ģļŗłļŗż. Grokking Techtalk #39: How to build an event driven architecture with Kafka ...
Grokking Techtalk #39: How to build an event driven architecture with Kafka ...Grokking VN
╠²
The document discusses building an event-driven architecture using Apache Kafka and Kafka Connect. It describes how VeXeRe uses this approach to stream data from their MS SQL database into Kafka. Key points covered include event sourcing, how Kafka Connect works using connectors and tasks, best practices for monitoring connectors, and handling database schema evolution. Real-world use cases at VeXeRe like syncing data to data warehouses and search indexes are also examined.IBK ņŗ£ņŖżĒģ£ņØś Ēü┤ļØ╝ņÜ░ļō£ ĻĖ░ļ░ś ĻĖłņ£Ą Ēöīļ×½ĒÅ╝ ļ╣äņ”łļŗłņŖż ņĀäļץ - AWS Summit Seoul 2017
IBK ņŗ£ņŖżĒģ£ņØś Ēü┤ļØ╝ņÜ░ļō£ ĻĖ░ļ░ś ĻĖłņ£Ą Ēöīļ×½ĒÅ╝ ļ╣äņ”łļŗłņŖż ņĀäļץ - AWS Summit Seoul 2017Amazon Web Services Korea
╠²
Ansible Automation - Enterprise Use Cases | Juncheng Anthony Lin
Ansible Automation - Enterprise Use Cases | Juncheng Anthony LinVietnam Open Infrastructure User Group
╠²
[ßäŗßģ®ßäæßģ│ßå½ßäēßģ®ßäēßģ│ßäÅßģźßå½ßäēßģźßå»ßäÉßģĄßå╝] VMware ßäāßģóßäŗßģĪßå½ Ļ▓ĆĒåĀļź╝ ņ£äĒĢ£ ĒöäļØ╝ņØ┤ļ╣Ś Ēü┤ļØ╝ņÜ░ļō£ ņåöļŻ©ņģś ņĀ£ņ¢Ė
[ßäŗßģ®ßäæßģ│ßå½ßäēßģ®ßäēßģ│ßäÅßģźßå½ßäēßģźßå»ßäÉßģĄßå╝] VMware ßäāßģóßäŗßģĪßå½ Ļ▓ĆĒåĀļź╝ ņ£äĒĢ£ ĒöäļØ╝ņØ┤ļ╣Ś Ēü┤ļØ╝ņÜ░ļō£ ņåöļŻ©ņģś ņĀ£ņ¢ĖOpen Source Consulting
╠²
More from Shiu-Fun Poon (19)
APIConnect Security Best Practice
APIConnect Security Best PracticeShiu-Fun Poon
╠²
The document outlines security best practices for IBM API Connect and DataPower Gateway, emphasizing the importance of configurable security measures, monitoring, and traffic management. It details functionalities such as API discovery, usage analytics, and OAuth support for compliance with regulations like PSD2 and Open Banking. Additionally, it highlights the need for robust access control, load management, and dynamic security policies to protect APIs against various cyber threats.GraphQL Security
GraphQL SecurityShiu-Fun Poon
╠²
The document discusses GraphQL as a query language that allows users to specify the exact data they need from a single endpoint, contrasting it with REST. It outlines various security considerations such as transport protection, rate limiting, data leakage, authentication methods, and authorization strategies. Additionally, it highlights the need for careful management of query complexity and compliance with regulations like GDPR and PCI compliance.IBM APIc API security protection mechanism
IBM APIc API security protection mechanismShiu-Fun Poon
╠²
This document discusses different security mechanisms for APIs, including API keys, basic authentication, OAuth 2.0, and mutual TLS (mTLS). API keys function similarly to usernames and passwords for applications to access APIs. Basic authentication is for user authentication to be used with API keys. OAuth 2.0 involves obtaining an access token to access resources, and has two-legged and three-legged flows. It exposes credentials only during the initial handshake, while API keys and basic auth expose them with each request. OAuth 2.0 thus has a lower chance of compromise if a token is stolen, since it is only valid for a limited time.How to create a User Defined Policy with IBM APIc (v10)
How to create a User Defined Policy with IBM APIc (v10)Shiu-Fun Poon
╠²
The document outlines the steps to create a custom policy using IBM API Connect (APIC) with the APIGW toolkit, including prerequisites such as downloading the toolkit and setting up credentials. It provides detailed instructions on creating a YAML file for the policy, packaging it, logging in via the toolkit, and uploading the policy to a sandbox or catalog. Additionally, it includes commands for managing organizations, catalogs, and policies through the command line interface.Cheatsheet to run DP docker
Cheatsheet to run DP dockerShiu-Fun Poon
╠²
This document discusses running IBM DataPower appliances using Docker and provides a Docker Hub link for the official IBM DataPower image. It also includes an optional section about bypassing insecure connection checks in Chrome by following steps outlined in a Medium article.How to migrate an application in IBM APIc, and preserve its client credential
How to migrate an application in IBM APIc, and preserve its client credentialShiu-Fun Poon
╠²
The document outlines the process of migrating an application within IBM API Connect while preserving client credentials, specifically focusing on the challenges posed by the transition from plaintext to hashed client secrets. It details the steps needed to extract, verify, and recreate application credentials in a new catalog, along with prerequisites and error messaging to ensure successful migration. Additionally, it emphasizes the importance of keeping the client_id and hashed client_secret for seamless application operation during the migration process.DataPower as PCI
DataPower as PCIShiu-Fun Poon
╠²
The WebSphere DataPower solution addresses all 12 requirements for securing cardholder data by building and maintaining a secure network, protecting stored cardholder data, maintaining vulnerability management, implementing strong access controls, regularly monitoring networks, and maintaining an information security policy. The solution provides a complete solution or partial solution for each requirement.How to integration with 3rd Party OAuth Provider with IBM APIc
How to integration with 3rd Party OAuth Provider with IBM APIcShiu-Fun Poon
╠²
This provides a high level on how to integrate with a 3rd party OAuth provider using IBM APIcHow to integration DataPower with Zos
How to integration DataPower with ZosShiu-Fun Poon
╠²
DataPower leverages z/OS Network Security Services (NSS) to integrate with z/OS security. NSS provides authentication, authorization, and certificate services to DataPower using centralized security definitions in SAF. DataPower can retrieve certificates and keys from the SAF keyring to perform encryption/decryption locally or request private key operations on z/OS. The document also discusses DataPower extension functions like generate-passticket() and zosnss-author() to interface with NSS.DataPower Security Hardening
DataPower Security HardeningShiu-Fun Poon
╠²
DataPower can be used to provide security for applications and APIs. It supports many security standards and protocols for authentication, authorization, encryption, and more. As a purpose-built appliance, it offers a secure platform with features like a hardened operating system, physical security protections, and no ability to install arbitrary third-party software. DataPower gateways are well-suited for roles like API management, security enforcement, and acting as a secure intermediary.IBM Apic toolkit cheatsheet
IBM Apic toolkit cheatsheetShiu-Fun Poon
╠²
The document discusses IBM's APIc toolkit and provides instructions for downloading, logging in, and using functions in the toolkit. There are two default identity providers for the admin and provider realms. When using functions, the default output format is YAML but the --format flag must be set to YAML or JSON for certain functions like cloud-settings:topology and cloud-settings:mail-server-configured.White vs Black list
White vs Black listShiu-Fun Poon
╠²
The document discusses the advantages and disadvantages of using whitelists and blacklists in various contexts, particularly in data protection and session management. It highlights the complexity of determining which list is better based on specific use cases, such as message and HTTP header protection, and token management. Ultimately, the decision between whitelisting and blacklisting depends on the particular requirements of the system and may benefit from a combined approach.APIC/DataPower security
APIC/DataPower securityShiu-Fun Poon
╠²
The document details best practices for security using IBM's API Connect and DataPower, emphasizing the importance of confidentiality and performance metrics. It outlines various security mechanisms, including API management, authentication methods, and the integration of advanced threat detection technologies. Additionally, it highlights features such as OAuth support and blockchain compliance for API security, accompanied by guidelines for monitoring and deploying secure APIs.Open Banking via APIc 2018
Open Banking via APIc 2018Shiu-Fun Poon
╠²
The document discusses IBM's support for open banking and PSD2 regulations through its API Connect platform. It provides an overview of traditional versus open banking platforms and the customer experience implications. It also outlines how IBM API Connect supports open banking standards through features that enable secure authentication, third party provider management, and accelerators for APIs, directories, and portals that facilitate PSD2 compliance.Gateway/APIC security
Gateway/APIC securityShiu-Fun Poon
╠²
This document outlines IBM's API Connect and DataPower security features, describing potential future product directions and the disclaimer that information may change without notice. Key features discussed include API management, traffic handling, security enhancements, and integration with microservices. It emphasizes the significance of maintaining API security against various cyber threats, employing advanced technologies like AI and machine learning for threat detection and prevention.Gateway deepdive
Gateway deepdiveShiu-Fun Poon
╠²
The document discusses IBM's API Connect and DataPower products. It provides information on IBM's statements regarding future products and features, which are subject to change. It also notes that performance will vary depending on individual configurations and workloads. The document then provides an overview comparison of features between API Connect, DataPower, and API gateway technologies.Token, token... From SAML to OIDC
Token, token... From SAML to OIDCShiu-Fun Poon
╠²
This document compares and contrasts three token-based authentication and authorization protocols: SAML, OAuth access tokens, and OpenID Connect ID tokens.
SAML uses XML assertions for identity and authorization. Access tokens in OAuth are opaque bearer strings, while ID tokens in OpenID Connect are JSON Web Tokens (JWTs) containing user information. SAML is for web services and uses WS-Security, while access tokens and ID tokens can be used by web and mobile apps via HTTP. Both SAML and ID tokens can be used to represent user identities, while access tokens and SAML assertions can authorize access to protected resources. Security considerations for each include confidentiality, integrity, and replay attacks.OAuth 2.0 with IBM WebSphere DataPower
OAuth 2.0 with IBM WebSphere DataPowerShiu-Fun Poon
╠²
OAuth 2.0 allows third party applications to access resources without sharing credentials. It uses grant types like authorization code and implicit grant to obtain an access token. The access token is then used by the client to access resources from the resource server. DataPower supports OAuth 2.0 and provides customization options like additional grant types and extension points to customize the OAuth handshake process.Ad
Recently uploaded (20)
AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
╠²
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowCoordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the SamePyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash
╠²
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and PrivacyUsing the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
╠²
The SQLExecutor is one of FMEŌĆÖs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation ŌĆōValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55
╠²
CurieTech AI in Action ŌĆō Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AIŌĆÖs purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samplesŌĆö95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specificationsŌĆöspeeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10├Ś productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflowŌĆöletting you focus on innovation, not repetition.Mastering AI Workflows with FME by Mark Do╠łring
Mastering AI Workflows with FME by Mark Do╠łringSafe Software
╠²
Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FMEŌĆÖs powerful tools for training, optimization, and seamless integrationWebdriverIO & JavaScript: The Perfect Duo for Web Automation
WebdriverIO & JavaScript: The Perfect Duo for Web Automationdigitaljignect
╠²
In todayŌĆÖs dynamic digital landscape, ensuring the quality and dependability of web applications is essential. While Selenium has been a longstanding solution for automating browser tasks, the integration of WebdriverIO (WDIO) with Selenium and JavaScript marks a significant advancement in automation testing. WDIO enhances the testing process by offering a robust interface that improves test creation, execution, and management. This amalgamation capitalizes on the strengths of both tools, leveraging SeleniumŌĆÖs broad browser support and WDIOŌĆÖs modern, efficient approach to test automation. As automation testing becomes increasingly vital for faster development cycles and superior software releases, WDIO emerges as a versatile framework, particularly potent when paired with JavaScript, making it a preferred choice for contemporary testing teams.Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu
╠²
Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
╠²
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnŌĆÖt yielding any results, so I expanded my search to second-hand dealer sitesŌĆöonly to realise that periodically checking each one was going to be tedious. ThatŌĆÖs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformŌĆÖs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, IŌĆÖll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canŌĆÖt buy a car for youŌĆöyetŌĆöit can certainly help you find the one youŌĆÖre after!MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
╠²
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.AI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software
╠²
In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike.AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc
╠²
AI VIDEO MAGAZINE - r/aivideo community newsletter ŌĆō Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash
╠²
Oh, the Possibilities - Balancing Innovation and Risk with Generative AISalesforce Summer '25 Release Frenchgathering.pptx.pdf
Salesforce Summer '25 Release Frenchgathering.pptx.pdfyosra Saidani
╠²
Salesforce Summer '25 Release Frenchgathering.pptx.pdfAd
DataPower DoS/DDoS
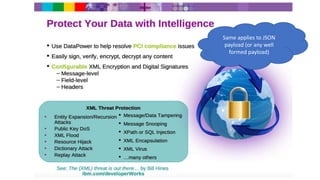
- 7. Same applies to JSON payload (or any well formed payload)
- 8. Same applies to JSON payload (or any well formed payload)
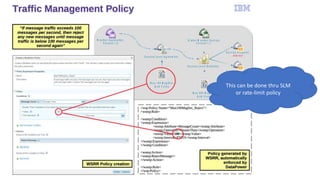
- 10. This can be done thru SLM or rate-limit policy
