dbms.ppt
- 1. Database Management System MIS 520 ÔÇô Database Theory Fall 2001 (Day) Lecture 13
- 2. Database Management System Database: A collection of related data. It should support ÔÇô Definition ÔÇô Construction ÔÇô Manipulation Database Management System: A collection of programs that enable the users to create and maintain a database.
- 3. Features of DBMS 1. Data storage, retrieval, and update: The ability to store, retrieve, and update the data that are in the database. 2. User-accessible catalog: where descriptions of database components are stored and are accessible to the users 3. Shared update support: A mechanism to ensure accuracy when several users are updating the database at the same time 4. Backup and Recovery Services: Mechanisms for recovering the database in the event that a database is damaged somehow. 5. Security Services: Mechanisms to ensure that certain rules are followed with regard to data in the database and any changes that are made in the data
- 4. Features of DBMS 5. Integrity services: Mechanisms to ensure that certain rules are followed with regard to data in the database and any changes that are made in the data. 6. Data Independence: Facilities to support the independence of programs from the structure of the database. 7. Replication support: A facility to manage copies of the same data at multiple locations. 8. Utility Services: DBMS provided services that assist in the general maintenance of the database.
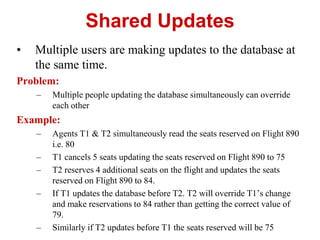
- 5. Shared Updates ÔÇó Multiple users are making updates to the database at the same time. Problem: ÔÇô Multiple people updating the database simultaneously can override each other Example: ÔÇô Agents T1 & T2 simultaneously read the seats reserved on Flight 890 i.e. 80 ÔÇô T1 cancels 5 seats updating the seats reserved on Flight 890 to 75 ÔÇô T2 reserves 4 additional seats on the flight and updates the seats reserved on Flight 890 to 84. ÔÇô If T1 updates the database before T2. T2 will override T1ÔÇÖs change and make reservations to 84 rather than getting the correct value of 79. ÔÇô Similarly if T2 updates before T1 the seats reserved will be 75
- 6. Shared Updates: Solution ÔÇó Batch Processing ÔÇô Allow multiple users to retrieve data simultaneously ÔÇô Updates are added to a batch file which does the appropriate processing ÔÇô Does not work for real time situations ÔÇó Locking ÔÇô Restrict access to the record being updated by a user till the transaction is complete.
- 7. Two Phase Lock ÔÇó Required when multiple records are updated as a result of a user action (e.g. filling form etc.) ÔÇó All the records accessed are locked progressively till the required updates are completed ÔÇô Growing Phase: More and more locks are added without releasing locks ÔÇô After all locks are placed the database is updated ÔÇô Shrinking Phase: All locks are removed and no new ones are added
- 8. Deadlock ÔÇó When two transactions require a common set of records. ÔÇó Both of them are in growing phase and each locks some of the records ÔÇó None of the records are released and they wait for each other to release the locked records They will wait forever!!!
- 9. Breaking Deadlock Facilities ÔÇó Programs can lock entire tables or an individual row ÔÇó Programs can release any or all of the locks they currently hold ÔÇó Programs can inquire whether a given row or table is locked Rules ÔÇó If more than one row is required then the entire table must be locked ÔÇó Limit the amount of wait for a lock to be released beyond which a transaction is aborted ÔÇó A well designed transaction should lock all the rows and tables before starting the transaction ÔÇó Users should release locks as soon as possible to improve the efficiency of the database
- 10. Security ÔÇó Protection against unauthorized access: either intentional or accidental. ÔÇó Three main features for protection ÔÇô Passwords: Allows only authorized users to access the database. Access privileges can be provided based on access needs ÔÇô Encryption: Encodes data to non-decipherable. Data decoded on demand to prevent hackers from accessing data ÔÇô Views: Different snapshot of the data ensures that users only get access to data they need
- 11. Integrity ÔÇó Integrity Constraints are the conditions that data must satisfy during initial input & updates. ÔÇó There are four categories of constraints ÔÇô Data Type ÔÇô Legal Values ÔÇô Format ÔÇô Key Constraints ÔÇó Entity Integrity Constraints (Primary Key) ÔÇô Enforces the uniqueness of the primary key ÔÇó Referential Integrity Constraints (Foreign Key) ÔÇô Value of foreign key must match the value of primary key for some row in another table
- 12. Integrity: Solutions ÔÇó Ignore constraint ÔÇô Undesirable as it can lead to inconsistent data ÔÇó Let user enforce the constraint ÔÇô Undesirable since user mistakes can be disastrous ÔÇó Let programmer build the logic of constraints in the programs ÔÇô Makes programs complex: harder to write, harder to maintain, and expensive ÔÇó Place burden on the DBMS. ÔÇô Preferred way: Cost of DBMS development amortized over large user base, hence economical
- 13. Replication ÔÇó Duplication of data at multiple physical locations ÔÇó Each replica of the data can be changed independently ÔÇó Periodically the replicas update their data to the master database ÔÇô this process is called synchronization
- 14. Disaster Planning: Backup & Recovery ÔÇó Database can be damaged in a number of ways ÔÇô Power outage, disk crashes, floods, user errors ÔÇó Periodic backups limit the loss due to sudden failures ÔÇó Data can be recovered from the latest backup and the changes since the backup need to be done in either of two ways ÔÇô Manually ÔÇô From a catalog (if exists) recording all updates to the database since the last backup.
- 15. Catalog/Data Dictionary ÔÇó Contains information describing the database ÔÇô Schema for the database ÔÇô Characteristic for each field ÔÇô Possible values for each field ÔÇô Description of the data ÔÇô Relationships ÔÇô Description of the programs ÔÇó Data Dictionary is same as catalog but may contain wider set of information than catalog