Digital signatures
- 1. Digital Signatures -Kannan Ravindran
- 2. Who am I ? I am Kannan Ravindran, A Student of Velammal Engineering College, Ambattur undertaking Bachelor of Engineering concentration on Computer Science and Engineering. I am a member of NullCon - International security conference(Chennai Chapter). I am serving H4CK3R.in as a Moderator.
- 3. Contents Introduction Symmetric Key Encryption Message Digest Birthday Attack MD5, SHA and Other Techniques Conclusion
- 4. Introduction â What is it? Cryptography is primarily used as a tool to protect national secrets and strategies. It is extensively used by the military, the diplomatic services and the banking sector. One of the landmark developments in the history of cryptography was the introduction of the revolutionary concept of public-key. A cryptographic algorithm or cipher, is a mathematical function used in the encryption and decryption process. This mathematical function works in combination with a key to encrypt the plaintext (the original message)
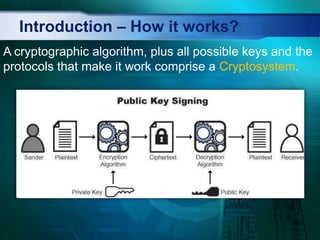
- 5. Introduction â How it works? A cryptographic algorithm, plus all possible keys and the protocols that make it work comprise a Cryptosystem.
- 6. Introduction - Objective ï§ Confidentiality is used to keep the content of information secret from unauthorized Persons This is achieved through symmetric and asymmetric encryption. ï§ Data integrity addresses the unauthorized alteration of data. This is addressed by hash functions. ï§ Authentication is related to identification. This applies to both entity and information itself. This is achieved through digital signature certificates and digital signatures.
- 7. Symmetric Cryptography In conventional Cryptography, also called secret-key or symmetric-key encryption , the same key is used for both encryption and decryption. Caesar's Cipher: Julius Caesar didnât trust his messengers. So when he sent a message to his generals, he replaced every âAâ with âDâ, every âBâ with âEâ and so on. Only the Caesar generals knew the âshift by 3â rule. So if we want to and the encrypt the word âNULLCONâ then the cipher will be âQXOOFRQâ. While decrypting it we follow the same âshift by 3â rule, but we shift in the opposite side.
- 8. Message Digest The original text: 7391743 Operation Result Multiply 7 by 3 21 Discard first digit 1 Multiply 1 by 9 9 Multiply 9 by 1 9 Multiply 9 by 7 63 Discard first digit 3 Multiply 3 by 4 12 Discard first digit 2 Multiply 2 by 3 6 The Message Digest is 6
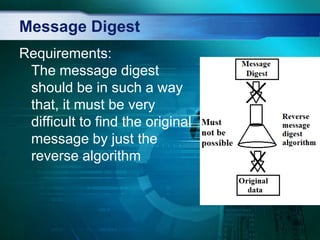
- 9. Message Digest Requirements: The given message should be very easy to find its corresponding message digest. Also the message digest should always be same every time.
- 10. Message Digest Requirements: The message digest should be in such a way that, it must be very difficult to find the original message by just the reverse algorithm
- 11. Birthday Attack ï§ How many people do you need so that the probability of having two of them share the same birthday is > 50% ? ï§ Random sample of n birthdays (input) taken from k (365, output) ï§ kn total number of possibilities ï§ (k)n=k(k-1)âĶ(k-n+1) possibilities without duplicate birthday ï§ Probability of no repetition: ï§ p = (k)n/kn ïŧ 1 - n(n-1)/2k ï§ For k=366, minimum n = 23 ï§ n(n-1)/2 pairs, each pair has a probability 1/k of having the same output ï§ n(n-1)/2k > 50% ïĻ n>k1/2
- 12. Birthday Attack Thus the birthday attack creates a problem in which more than one message can yield the same message digest. And this probability of this type of collision is more than 50% to prevent these birthday attacks algorithms like MD5 and SHA are used.
- 13. How many bits for hash? ï§ m bits, takes 2m/2 to find two with the same hash ï§ 64 bits, takes 232 messages to search (doable) ï§ Need at least 128 bits
- 14. Hash for authentication ï§ Alice to Bob: challenge rA ï§ Bob to Alice: MD(KAB|rA) ï§ Bob to Alice: rB ï§ Alice to Bob: MD(KAB|rB) ï§ Only need to compare MD results
- 15. MD5 input Message Output 128 bits Digest âĒ Until recently the most widely used hash algorithm â in recent times have both brute-force & cryptanalytic concerns âĒ Specified as Internet standard RFC1321
- 16. MD5 1. Pad message so its length is 448 mod 512 2. Append a 64-bit original length value to message 3. Initialise 4-word (128-bit) MD buffer (A,B,C,D) Process message in 16-word (512-bit) blocks: ï§ Using 4 rounds of 16 bit operations on message block & buffer ï§ Add output to buffer input to form new buffer value 4. Output hash value is the final buffer value
- 17. SHA ï§ Developed by NIST, specified in the Secure Hash Standard (SHS, FIPS Pub 180), 1993 ï§ SHA is specified as the hash algorithm in the Digital Signature Standard (DSS), NIST
- 18. SHA ï§ Input message must be < 264 bits ï§ not really a problem ï§ Message is processed in 512-bit blocks sequentially ï§ Message digest is 160 bits ï§ SHA design is similar to MD5, but a lot stronger
- 19. MD5 Vs SHA ï§ Brute force attack is harder (160 vs 128 bits for MD5) ï§ Not vulnerable to any known cryptanalytic attacks (compared to MD4/5) ï§ A little slower than MD5 (80 vs 64 steps) ï§ Both work well on a 32-bit architecture ï§ Both designed as simple and compact for implementation
- 20. Revised Secure Hash Standards ï§ NIST have issued a revision FIPS 180-2 ï§ adds 3 additional hash algorithms ï§ SHA-256, SHA-384, SHA-512 ï§ designed for compatibility with increased security provided by the AES cipher ï§ structure & detail is similar to SHA-1 ï§ hence analysis should be similar
- 21. Conclusion Thus different concepts of Digital signatures are discussed and a overview of the various algorithms used are discussed
- 22. Questions??