DISHA PATEL COMPUTER VIRUS PPT.pptx
Download as pptx, pdf0 likes68 views
This document discusses different types of computer viruses and how to prevent them. It defines viruses and explains how they spread by attaching to other program files or through external storage devices. Common symptoms of a virus are slow computer performance, low memory, and files being deleted. The presentation recommends using up-to-date antivirus software, enabling firewalls, and being cautious of email attachments to prevent virus infection. Various virus types are outlined, including boot sector viruses, program file viruses, macro viruses, and malware like worms and spyware.
1 of 17
Download to read offline














Recommended
Viruses andthreats@dharmesh



Viruses andthreats@dharmeshDharmesh Kumar Sharma
╠²
Computer viruses and related threats were presented. Malware is defined as software designed to harm computers without the owner's consent. Common malware types were discussed including viruses, trojans, spyware, and worms. Viruses can replicate and spread, infecting files and corrupting data. Antivirus software uses signature detection, behavior monitoring, and heuristic analysis to identify and remove viruses and prevent infection. Regular antivirus updates and safe computing practices were recommended to protect against evolving malware threats.computer virus ppt.pptx



computer virus ppt.pptxAbiniyavk
╠²
A computer virus is a malicious program that can replicate itself and spread from computer to computer without permission. It can slow down or damage infected systems. The first computer virus, called "Creeper," was created in 1971. Later viruses caused more harm by deleting files or collecting users' personal data. To avoid viruses, users should only download files from trusted sources, use antivirus software, keep systems updated, and be wary of email attachments from unknown senders. Other malware like spyware and Trojans also pose threats by monitoring users' activities or gaining control of infected devices without consent.Viruses notes



Viruses notesDara Corporates
╠²
Computer viruses are malicious programs that can copy themselves and spread from one computer to another without permission. They infect files and can cause damage like deleting data or overwriting files. Antivirus software uses different techniques like real-time protection, on-demand scanning, automatic updates, and file quarantining to detect, remove, and prevent viruses from infecting computers. Common types of viruses include macro viruses, boot viruses, polymorphic viruses, and Trojan horses which can have various harmful effects if not addressed by antivirus protection.Computer Viruses



Computer VirusesAman Chaudhary
╠²
A computer virus is a malicious software program that spreads by copying itself to other computers. It can corrupt or delete data on a computer. Viruses are often spread through email attachments, downloads, and removable media. There are several types of viruses including boot viruses, program viruses, macro viruses, and polymorphic viruses. Symptoms of a virus infection include programs not working properly, critical files being deleted, and the computer running slower. It is important to have antivirus software installed and keep it updated to protect computers from virus infections.Virusandantivirusfinalppt 110413033802-phpapp02 (1)



Virusandantivirusfinalppt 110413033802-phpapp02 (1)Cimab Butt
╠²
This document discusses malware and how antivirus software works to protect systems. It defines malware as software designed to harm systems without consent. Common types of malware include viruses, trojans, spyware, adware, and rootkits. Viruses can damage data and systems. Antivirus software uses virus definitions and monitors program behavior to identify malware. It provides regular updates to address new threats and scans systems to find and remove malware. Disconnecting systems from networks and running full antivirus scans is recommended if malware is suspected.Computer viruses



Computer virusesaagmansaini
╠²
Computer viruses are programs that can replicate themselves and spread from one computer to another. They can corrupt files, crash systems, and steal private information. There are several types of viruses including program viruses, boot viruses, macro viruses, malware, worms, Trojan horses, spyware, and spam. It is important to have antivirus software installed and keep it updated to protect against new viruses, and to be cautious of external devices and downloads that could introduce viruses.Ch. 3 computer virus



Ch. 3 computer virusComputer Science
╠²
A computer virus is a program that infects and disrupts the normal functioning of a computer without the user's permission or knowledge. There are different types of viruses, including program file viruses and boot sector viruses. Symptoms of a virus infection include frequent computer shutdowns and restarts, malfunctioning applications, inaccessible drives, and unexpected error messages. Viruses can spread through removable storage devices, the internet by visiting infected websites or opening email attachments, and through fake antivirus software called "sweepers". It is important to have effective antivirus software installed and keep it updated to detect and remove viruses.COMPUTER VIRUS affecting to computer software



COMPUTER VIRUS affecting to computer softwaresonajidongre
╠²
This document discusses computer viruses and anti-virus software. It defines a computer virus as a program that can copy itself and infect computers without permission. It then describes different types of viruses like boot sector viruses, file infector viruses, and macro viruses. The document also covers malware like spyware, adware, worms, and trojans. It explains how anti-virus software works to detect viruses using signature definitions and heuristic algorithms. Finally, it provides tips for preventing viruses like regularly updating anti-virus software and scanning removable drives.Viruses notes1



Viruses notes1Dara Corporates
╠²
Computer viruses are programs that can copy themselves and infect computers without permission. They spread by getting transferred to other computers through files or disks. There are several types of viruses like macro viruses, boot viruses, polymorphic viruses, and worms. Antivirus software helps prevent, detect, and remove viruses through features like real-time protection, file scanning, updates, and alerts. It uses different scanning techniques such as conventional disk scanning, memory resident scanning, startup scanning, and inoculation. However, antivirus software can sometimes slow computers down or be difficult for inexperienced users.Computer Viruses 



Computer Viruses Tanu Basoiya
╠²
VIRUSES - types, how computer virus spreads, damages virus causes, some common viruses and preventions.Virus bashdar



Virus bashdarBashdar Rahman
╠²
This document discusses computer viruses including their similarities to biological viruses, what they do, types of computer viruses, sources of virus attacks, symptoms of virus infection, prevention and cures, antivirus software, and reasons why people create computer viruses. It covers main types of viruses like macro viruses, boot sector viruses, worms, Trojan horses, and logic bombs. It also discusses how viruses spread and the damage they can cause. Prevention methods include installing antivirus software and being cautious of email attachments and downloads from untrusted sources.Computer virus



Computer virusSammer Khizer
╠²
Computer viruses are programs that spread by infecting other programs and files. They spread through infected data or programs copied from one system to another, or through email and internet files. There are different types of viruses like boot sector viruses, file infecting viruses, and program viruses. Viruses can damage systems by corrupting and deleting files, slowing performance, and erasing data. It is important to use antivirus software to scan for and remove viruses, keep backups, and avoid opening unknown files.Virus and antivirus final ppt



Virus and antivirus final pptaritradutta22
╠²
This document discusses malware and provides information about common types of malware like viruses, trojans, worms, spyware, and adware. It then discusses antivirus and anti-spyware software that can be used to protect systems from malware by identifying, removing, and preventing malware infections. Regularly updating antivirus software and scanning systems is recommended to keep systems secure from evolving malware threats.Computer virus



Computer virusUtchi
╠²
This document defines a computer virus and discusses how viruses spread and the types of damage they can cause. It outlines symptoms of a virus infection and types of viruses like boot sector viruses, macro viruses, and script viruses. The document recommends installing antivirus software from reputable companies, backing up files regularly, being cautious of email attachments, and avoiding unknown programs as ways to prevent virus infections.Kinds of Viruses



Kinds of Virusesjenniel143
╠²
Viruses, worms, and Trojan horses are types of malicious software (malware) that can damage computers. Viruses spread by attaching to host programs and replicating, worms spread across networks without user action, and Trojans allow hackers remote access. Some examples provided include the CIH virus from 1998 that overwrites partition tables, the 2001 Code Red worm that allowed network hacking, and the 2012 Trojan.Flame malware that stole data. Basic safety tips to avoid malware include keeping systems updated, using antivirus software, avoiding unsafe files/links, and being wary of suspicious messages.Virus project



Virus projectShehrevar Davierwala
╠²
This document provides information about computer viruses, including:
- What a computer virus is and how it spreads by infecting files and programs.
- The different types of viruses like direct action, resident, overwrite, and directory viruses.
- The differences between viruses, worms, and Trojan horses.
- Symptoms of an infected computer and what to do if suspecting a virus attack.
- Popular antivirus software options and factors to consider like update frequency and scanning capabilities.
- How antivirus software works to detect, remove, and quarantine viruses to prevent spreading.
- General precautions like scanning removable media and keeping software updated.Computer viruses



Computer virusesPrabesh Shrestha
╠²
This document discusses computer viruses. It defines a virus as a program that infects and damages files. Viruses replicate by attaching themselves to other programs. They can be transmitted via email attachments, downloaded files, removable drives, or networks. Common symptoms of virus infection include computers running slowly, files changing or deleting unexpectedly, and error messages. The document recommends using antivirus software, scanning downloads, and avoiding suspicious websites or attachments to prevent virus infections. It describes two main types of viruses: boot sector viruses, which infect the boot sector and prevent computers from starting up, and file infecting viruses, which change the contents of files and replicate within files.Computer security.pptx



Computer security.pptxGovandJamal
╠²
Computer security how tnxnxjxjxixjxjxodkxkixjxjdidkfkfkfnifnfjfn xnxjoxnxifncjchjxndhbxbxxnxnxjxjxjxjjxjxc. Xjxnxjxnjxncjcjcnxicncnjxnx xxjkxjxnxkzznxkxmx. Xjxnxkxmsjisjdidksjs djskskkxnd dkxkjdksksjsjdkdnsndnddndnidnd djsndbd. Djmddbjdmdnd djjmv Computer virus



Computer virusKawsar Ahmed
╠²
The document discusses computer viruses, how they spread and affect systems. It describes how the first virus, called "Creeper, was created in 1970s and outlines common ways viruses enter systems like through email attachments. Different virus types are outlined like memory resident viruses, boot sector viruses and macro viruses that hide in various parts of the system. Symptoms of virus infection and basic prevention tips are provided.Computer viruses and antiviruses PPT



Computer viruses and antiviruses PPTEva Harshita
╠²
A computer virus is a malicious program that can copy itself and infect computers without permission. It spreads when an infected computer is connected to uninfected ones, such as via a network or removable storage. There are different types of viruses that infect different parts of a computer system. Malware is a broader term that includes viruses as well as other malicious software like spyware, adware, worms, and trojans. Anti-virus software uses techniques like signature matching, sandboxing, and heuristics to identify and remove viruses and other malware from an infected system. Users should practice safe computing habits and use anti-virus software to help prevent and remove virus infections.Computer viruses and antiviruses



Computer viruses and antivirusesSanguine_Eva
╠²
A computer virus is a malicious program that can copy itself and infect computers without permission. It spreads when an infected computer is connected to uninfected ones, such as via a network or removable storage. There are different types of viruses that infect different parts of a computer system. Malware is a broader term that includes viruses as well as other malicious software like spyware, adware, worms, and trojans. Anti-virus software uses techniques like signature matching, sandboxing, and heuristics to identify and remove viruses and other malware from an infected system. Users should practice safe computing habits and use anti-virus software to help prevent and remove virus infections.Computer virus (Microsoft Word)



Computer virus (Microsoft Word)ainizbahari97
╠²
This document provides information about computer viruses including what they are, how they spread, and how to remove them. It defines viruses as small programs that can copy themselves and infect computers without permission in order to interfere with operations. Viruses are often spread through email attachments and downloading files. To remove a virus, the document recommends using an online scanner from Microsoft or another security provider and checking for antivirus software updates. It also provides examples of other types of malware like worms, trojans, and bacteria that differ from viruses in their behaviors.1311782 634629102605888750



1311782 634629102605888750bhagatsigh
╠²
A computer virus is a program that spreads from one computer to another and interferes with computer operation. Viruses can corrupt or delete data. They replicate by attaching themselves to other programs or files. Common types include macro, polymorphic, and metamorphic viruses. Symptoms of a virus include slow performance, random restarts, and loss of disk space. Viruses are typically spread through email attachments, networks, removable media, and pirated software. People create viruses for fun, profit, or revenge, while info attackers aim to disrupt networks. To protect against viruses, users should install and regularly update antivirus software, avoid unknown emails/files, and use security measures like firewalls.Securing The Computer From Viruses ...



Securing The Computer From Viruses ...Rahman_Hussain
╠²
Name - Md Mustafizur Rahman
Course - M.Ed
Department of Education
Central University of Punjab , Bathinda (151001)Computervirus 



Computervirus Dushyant Shekhawat
╠²
Computer viruses are small programs that spread from computer to computer and interfere with operations. They are often spread through email attachments and can corrupt or delete files. To remove a virus, you can use an online scanner like Microsoft Safety Scanner or restart your computer in safe mode and run a scanner. In addition to viruses, other types of malware include Trojans, worms, and bacteria. Viruses can activate and potentially damage files in various ways like playing sounds, showing pictures, or formatting disks. It is important to have antivirus software and be cautious of suspicious files and downloads.Antivirus security



Antivirus securitymPower Technology
╠²
In this era of modern technology, computers play a very important role in our
daily lives. Computers play its functions in private homes, offices, workspaces, hospitals,
schools, and everywhere else. It is undeniable that computers are very important
nowadays but of course, no matter how great the technology is, there will still be some
flaws and problems. The existence of computer viruses revolutionized the way the
computer works and what type of security measures are supposed to be taken to prevent
this serious problem.Virus and malware presentation



Virus and malware presentationAmjad Bhutto
╠²
Viruses and malware can damage computers. Viruses spread by copying themselves, while malware is designed to access or harm devices without owner knowledge. Common malware includes adware, bugs, rootkits, Trojans, and ransomware. It is important to use updated antivirus software, strong passwords, firewalls, and be cautious of suspicious links and downloads to protect devices from viruses and malware.CP SEMINAR.pptx



CP SEMINAR.pptxCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This document summarizes a seminar presentation on the use of plastics in everyday life and agriculture. It begins by acknowledging those who guided and supported the project. It then defines plastics and describes common types. It outlines various uses of plastics in daily life and agriculture, including benefits like increased crop yields from practices like plastic mulching. However, it also discusses problems with plastic pollution in soil and the environment. Microplastics in particular can harm earthworms and reduce soil fertility. The document concludes by suggesting methods to reduce plastic pollution like alternative materials and reducing single-use plastics.tushar is - 13488.pptx



tushar is - 13488.pptxCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This document discusses an Indian standard (IS 13488 - 2008) for irrigation equipment emitting pipe systems. It provides definitions and classifications for emitting pipes and describes tests to evaluate properties like uniformity of emission rates, resistance to pressure and tension, and carbon black content and dispersion. Emitting pipes are used in drip irrigation systems and are manufactured from polyethylene with emitters that slowly drip water to plant roots. The standard specifies requirements and test methods to ensure proper functioning under various pressures and environmental conditions.More Related Content
Similar to DISHA PATEL COMPUTER VIRUS PPT.pptx (20)
Viruses notes1



Viruses notes1Dara Corporates
╠²
Computer viruses are programs that can copy themselves and infect computers without permission. They spread by getting transferred to other computers through files or disks. There are several types of viruses like macro viruses, boot viruses, polymorphic viruses, and worms. Antivirus software helps prevent, detect, and remove viruses through features like real-time protection, file scanning, updates, and alerts. It uses different scanning techniques such as conventional disk scanning, memory resident scanning, startup scanning, and inoculation. However, antivirus software can sometimes slow computers down or be difficult for inexperienced users.Computer Viruses 



Computer Viruses Tanu Basoiya
╠²
VIRUSES - types, how computer virus spreads, damages virus causes, some common viruses and preventions.Virus bashdar



Virus bashdarBashdar Rahman
╠²
This document discusses computer viruses including their similarities to biological viruses, what they do, types of computer viruses, sources of virus attacks, symptoms of virus infection, prevention and cures, antivirus software, and reasons why people create computer viruses. It covers main types of viruses like macro viruses, boot sector viruses, worms, Trojan horses, and logic bombs. It also discusses how viruses spread and the damage they can cause. Prevention methods include installing antivirus software and being cautious of email attachments and downloads from untrusted sources.Computer virus



Computer virusSammer Khizer
╠²
Computer viruses are programs that spread by infecting other programs and files. They spread through infected data or programs copied from one system to another, or through email and internet files. There are different types of viruses like boot sector viruses, file infecting viruses, and program viruses. Viruses can damage systems by corrupting and deleting files, slowing performance, and erasing data. It is important to use antivirus software to scan for and remove viruses, keep backups, and avoid opening unknown files.Virus and antivirus final ppt



Virus and antivirus final pptaritradutta22
╠²
This document discusses malware and provides information about common types of malware like viruses, trojans, worms, spyware, and adware. It then discusses antivirus and anti-spyware software that can be used to protect systems from malware by identifying, removing, and preventing malware infections. Regularly updating antivirus software and scanning systems is recommended to keep systems secure from evolving malware threats.Computer virus



Computer virusUtchi
╠²
This document defines a computer virus and discusses how viruses spread and the types of damage they can cause. It outlines symptoms of a virus infection and types of viruses like boot sector viruses, macro viruses, and script viruses. The document recommends installing antivirus software from reputable companies, backing up files regularly, being cautious of email attachments, and avoiding unknown programs as ways to prevent virus infections.Kinds of Viruses



Kinds of Virusesjenniel143
╠²
Viruses, worms, and Trojan horses are types of malicious software (malware) that can damage computers. Viruses spread by attaching to host programs and replicating, worms spread across networks without user action, and Trojans allow hackers remote access. Some examples provided include the CIH virus from 1998 that overwrites partition tables, the 2001 Code Red worm that allowed network hacking, and the 2012 Trojan.Flame malware that stole data. Basic safety tips to avoid malware include keeping systems updated, using antivirus software, avoiding unsafe files/links, and being wary of suspicious messages.Virus project



Virus projectShehrevar Davierwala
╠²
This document provides information about computer viruses, including:
- What a computer virus is and how it spreads by infecting files and programs.
- The different types of viruses like direct action, resident, overwrite, and directory viruses.
- The differences between viruses, worms, and Trojan horses.
- Symptoms of an infected computer and what to do if suspecting a virus attack.
- Popular antivirus software options and factors to consider like update frequency and scanning capabilities.
- How antivirus software works to detect, remove, and quarantine viruses to prevent spreading.
- General precautions like scanning removable media and keeping software updated.Computer viruses



Computer virusesPrabesh Shrestha
╠²
This document discusses computer viruses. It defines a virus as a program that infects and damages files. Viruses replicate by attaching themselves to other programs. They can be transmitted via email attachments, downloaded files, removable drives, or networks. Common symptoms of virus infection include computers running slowly, files changing or deleting unexpectedly, and error messages. The document recommends using antivirus software, scanning downloads, and avoiding suspicious websites or attachments to prevent virus infections. It describes two main types of viruses: boot sector viruses, which infect the boot sector and prevent computers from starting up, and file infecting viruses, which change the contents of files and replicate within files.Computer security.pptx



Computer security.pptxGovandJamal
╠²
Computer security how tnxnxjxjxixjxjxodkxkixjxjdidkfkfkfnifnfjfn xnxjoxnxifncjchjxndhbxbxxnxnxjxjxjxjjxjxc. Xjxnxjxnjxncjcjcnxicncnjxnx xxjkxjxnxkzznxkxmx. Xjxnxkxmsjisjdidksjs djskskkxnd dkxkjdksksjsjdkdnsndnddndnidnd djsndbd. Djmddbjdmdnd djjmv Computer virus



Computer virusKawsar Ahmed
╠²
The document discusses computer viruses, how they spread and affect systems. It describes how the first virus, called "Creeper, was created in 1970s and outlines common ways viruses enter systems like through email attachments. Different virus types are outlined like memory resident viruses, boot sector viruses and macro viruses that hide in various parts of the system. Symptoms of virus infection and basic prevention tips are provided.Computer viruses and antiviruses PPT



Computer viruses and antiviruses PPTEva Harshita
╠²
A computer virus is a malicious program that can copy itself and infect computers without permission. It spreads when an infected computer is connected to uninfected ones, such as via a network or removable storage. There are different types of viruses that infect different parts of a computer system. Malware is a broader term that includes viruses as well as other malicious software like spyware, adware, worms, and trojans. Anti-virus software uses techniques like signature matching, sandboxing, and heuristics to identify and remove viruses and other malware from an infected system. Users should practice safe computing habits and use anti-virus software to help prevent and remove virus infections.Computer viruses and antiviruses



Computer viruses and antivirusesSanguine_Eva
╠²
A computer virus is a malicious program that can copy itself and infect computers without permission. It spreads when an infected computer is connected to uninfected ones, such as via a network or removable storage. There are different types of viruses that infect different parts of a computer system. Malware is a broader term that includes viruses as well as other malicious software like spyware, adware, worms, and trojans. Anti-virus software uses techniques like signature matching, sandboxing, and heuristics to identify and remove viruses and other malware from an infected system. Users should practice safe computing habits and use anti-virus software to help prevent and remove virus infections.Computer virus (Microsoft Word)



Computer virus (Microsoft Word)ainizbahari97
╠²
This document provides information about computer viruses including what they are, how they spread, and how to remove them. It defines viruses as small programs that can copy themselves and infect computers without permission in order to interfere with operations. Viruses are often spread through email attachments and downloading files. To remove a virus, the document recommends using an online scanner from Microsoft or another security provider and checking for antivirus software updates. It also provides examples of other types of malware like worms, trojans, and bacteria that differ from viruses in their behaviors.1311782 634629102605888750



1311782 634629102605888750bhagatsigh
╠²
A computer virus is a program that spreads from one computer to another and interferes with computer operation. Viruses can corrupt or delete data. They replicate by attaching themselves to other programs or files. Common types include macro, polymorphic, and metamorphic viruses. Symptoms of a virus include slow performance, random restarts, and loss of disk space. Viruses are typically spread through email attachments, networks, removable media, and pirated software. People create viruses for fun, profit, or revenge, while info attackers aim to disrupt networks. To protect against viruses, users should install and regularly update antivirus software, avoid unknown emails/files, and use security measures like firewalls.Securing The Computer From Viruses ...



Securing The Computer From Viruses ...Rahman_Hussain
╠²
Name - Md Mustafizur Rahman
Course - M.Ed
Department of Education
Central University of Punjab , Bathinda (151001)Computervirus 



Computervirus Dushyant Shekhawat
╠²
Computer viruses are small programs that spread from computer to computer and interfere with operations. They are often spread through email attachments and can corrupt or delete files. To remove a virus, you can use an online scanner like Microsoft Safety Scanner or restart your computer in safe mode and run a scanner. In addition to viruses, other types of malware include Trojans, worms, and bacteria. Viruses can activate and potentially damage files in various ways like playing sounds, showing pictures, or formatting disks. It is important to have antivirus software and be cautious of suspicious files and downloads.Antivirus security



Antivirus securitymPower Technology
╠²
In this era of modern technology, computers play a very important role in our
daily lives. Computers play its functions in private homes, offices, workspaces, hospitals,
schools, and everywhere else. It is undeniable that computers are very important
nowadays but of course, no matter how great the technology is, there will still be some
flaws and problems. The existence of computer viruses revolutionized the way the
computer works and what type of security measures are supposed to be taken to prevent
this serious problem.Virus and malware presentation



Virus and malware presentationAmjad Bhutto
╠²
Viruses and malware can damage computers. Viruses spread by copying themselves, while malware is designed to access or harm devices without owner knowledge. Common malware includes adware, bugs, rootkits, Trojans, and ransomware. It is important to use updated antivirus software, strong passwords, firewalls, and be cautious of suspicious links and downloads to protect devices from viruses and malware.More from CENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY (12)
CP SEMINAR.pptx



CP SEMINAR.pptxCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This document summarizes a seminar presentation on the use of plastics in everyday life and agriculture. It begins by acknowledging those who guided and supported the project. It then defines plastics and describes common types. It outlines various uses of plastics in daily life and agriculture, including benefits like increased crop yields from practices like plastic mulching. However, it also discusses problems with plastic pollution in soil and the environment. Microplastics in particular can harm earthworms and reduce soil fertility. The document concludes by suggesting methods to reduce plastic pollution like alternative materials and reducing single-use plastics.tushar is - 13488.pptx



tushar is - 13488.pptxCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This document discusses an Indian standard (IS 13488 - 2008) for irrigation equipment emitting pipe systems. It provides definitions and classifications for emitting pipes and describes tests to evaluate properties like uniformity of emission rates, resistance to pressure and tension, and carbon black content and dispersion. Emitting pipes are used in drip irrigation systems and are manufactured from polyethylene with emitters that slowly drip water to plant roots. The standard specifies requirements and test methods to ensure proper functioning under various pressures and environmental conditions.Himanshu IS 13487.pptx



Himanshu IS 13487.pptxCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This document provides standards and requirements for irrigation emitters. It defines emitters as devices used to slowly drip water into soil at plant root zones. The document outlines classifications for emitters, required construction materials, test procedures, and mechanical standards including resistance to pressure and pull-out forces. Emitters must maintain water flow paths and connections, withstand high pressure tests without damage, and not pull out of pipes under specified tensile forces. The document seeks to ensure proper operation and performance of emitters in irrigation systems.CP SINGH IS-15410 new.pdf



CP SINGH IS-15410 new.pdfCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This document summarizes the key points from a presentation on testing PET containers. It discusses the purpose and common materials used for plastic containers. It then describes various tests conducted on containers, including transparency testing, closure leakage testing, vibration leakage testing, air pressure leakage testing, drop testing, migration testing, and color migration testing. The document provides details on the procedures for each of these tests.AMAN PPT 4985 Assignment-1.pptx



AMAN PPT 4985 Assignment-1.pptxCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This document provides a presentation on IS-4985, the specification for unplasticized PVC pipes for potable water supplies. It discusses the composition and manufacturing process of UPVC pipes. It also outlines the required test report format and specifications for pipe dimensions, visual appearance, opacity, and other tests according to the Indian standard. The presentation was submitted to Mr. Jagan Mehta by Aman Tiwari for their course at CIPET:IPT-Ahmedabad.ADITYA IS-4984.pptx



ADITYA IS-4984.pptxCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
The document provides test results from testing HDPE pipes according to Indian Standard IS-4984-2016. Various tests were conducted to evaluate the geometric characteristics, dimensions, hydraulic characteristics under pressure at different temperatures and durations, carbon black content, density, tensile strength, and slow crack growth rate of the HDPE pipes. All test results obtained were found to meet the specified requirements laid out in the Indian Standard.Wave motion bsc 



Wave motion bsc CENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This presentation discusses various topics related to wave motion, including:
1. The wave equation, which is an important differential equation used to describe waves in various fields like acoustics and fluid dynamics.
2. Plane progressive waves in fluid media, which travel continuously in the same direction without changing amplitude.
3. The principle of superposition, which states that when two or more waves pass through the same medium at the same time, the net displacement at any point is the sum of the individual wave displacements.Moment of inertia (1)



Moment of inertia (1)CENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
The document discusses parallel axis theorem and radius of gyration. It states that parallel axis theorem can be used to calculate the moment of inertia about any parallel axis through the centroidal axis using a formula that considers the first moment of area and distance between the two axes. Radius of gyration is defined as the root mean square distance of particles from the axis of rotation and represents the equivalent radius of a rotating body. Rotational energy is the kinetic energy due to an object's rotation and is part of its total kinetic energy, calculated as the torque times the angular velocity of a rotating body.Chemistry presentation



Chemistry presentationCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
The document is a presentation on periodic properties of elements. It discusses how elements arranged in order of atomic number show recurring patterns of properties. These properties include metallic/nonmetallic character, atomic radius, ionization energy, electronegativity, and reactivity. The modern periodic table organizes elements into periods and groups, with elements in the same group having similar properties due to their outer electron configuration. Periodic trends are shown for atomic size, ionization energy, electron affinity, and electronegativity.Simple hormonic motion



Simple hormonic motionCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This document is a presentation submitted by Aditya Verma, a first year BSC student, to Dr. Sharad Kumar on the topic of simple harmonic motion. Aditya Verma thanks Dr. Kumar for reviewing his presentation.Chemistry presentation on xenon compounds



Chemistry presentation on xenon compoundsCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
This presentation discusses xenon compounds, including xenon fluorine compounds and xenon oxygen compounds. It also mentions the use of noble gases and was submitted by Aditya Verma to Dr. Parul Mishra for a BSC first year course.Moment of inertia (1)



Moment of inertia (1)CENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
The document discusses parallel axis theorem and how it relates to moment of inertia. It states that the moment of inertia of an area about a parallel axis can be calculated as the sum of the moment of inertia about the centroidal axis and the first moment of area about the centroid. It also provides definitions for radius of gyration, which is the root mean square distance of particles from the axis of rotation, and rotational energy, which is the kinetic energy due to an object's rotation.Chemistry presentation on xenon compounds



Chemistry presentation on xenon compoundsCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
╠²
Recently uploaded (20)
Philosophical Basis of Curriculum Designing



Philosophical Basis of Curriculum DesigningAnkit Choudhary
╠²
The philosophical basis of curriculum refers to the foundational beliefs and values that shape the goals, content, structure, and methods of education. Major educational philosophiesŌĆöidealism, realism, pragmatism, and existentialismŌĆöguide how knowledge is selected, organized, and delivered to learners. In the digital age, understanding these philosophies helps educators and content creators design curriculum materials that are purposeful, learner-centred, and adaptable for online environments. By aligning educational content with philosophical principles and presenting it through interactive and multimedia formats.How to Configure Credit Card in Odoo 18 Accounting



How to Configure Credit Card in Odoo 18 AccountingCeline George
╠²
Odoo 18 allows businesses to manage credit card payments efficiently within the Accounting module. HereŌĆÖs how you can configure a credit card as a payment method.Policies, procedures, subject selection and QTAC.pptx



Policies, procedures, subject selection and QTAC.pptxmansk2
╠²
Policies, procedures, subject selection and QTACOptical and non optical devices used in low vision



Optical and non optical devices used in low visionAligarh Muslim University, Aligarh, Uttar Pradesh, India
╠²
Low vision devices description for optometry students. For educational purposes.TechSoup - Microsoft Discontinuation of Selected Cloud Donated Offers 2025.05...



TechSoup - Microsoft Discontinuation of Selected Cloud Donated Offers 2025.05...TechSoup
╠²
Thousands of nonprofits rely on donated Microsoft 365 Business Premium and Office 365 E1 subscriptions. In this webinar, TechSoup discuss Microsoft's May 14 announcement that the donated versions of these licenses would no longer be available to nonprofits after July 1, 2025, and which options are best for nonprofits moving forward as they transition off these licenses.Primary Bash in Richmond 2025 - Literacy.pdf



Primary Bash in Richmond 2025 - Literacy.pdfFaye Brownlie
╠²
A 2 hour session focusing on whole class, inclusive literacy practices for all learners. Protest - Student Revision Booklet For VCE English



Protest - Student Revision Booklet For VCE Englishjpinnuck
╠²
The 'Protest Student Revision Booklet' is a comprehensive resource to scaffold students to prepare for writing about this idea framework on a SAC or for the exam. This resource helps students breakdown the big idea of protest, practise writing in different styles, brainstorm ideas in response to different stimuli and develop a bank of creative ideas.How to Automate Activities Using Odoo 18 CRM



How to Automate Activities Using Odoo 18 CRMCeline George
╠²
In Odoo 18, the CRM module's activity feature is designed to help users manage and track tasks related to customer interactions. These tasks could include phone calls, meetings, emails, or follow-ups, and are essential for progressing through sales and customer management processes.Low Vison introduction from Aligarh Muslim University



Low Vison introduction from Aligarh Muslim UniversityAligarh Muslim University, Aligarh, Uttar Pradesh, India
╠²
This is for optometry students for education purposeFlower Identification Class-10 by Kushal Lamichhane.pdf



Flower Identification Class-10 by Kushal Lamichhane.pdfkushallamichhame
╠²
This includes the overall cultivation practices of rose prepared by:
Kushal Lamichhane
Instructor
Shree Gandhi Adarsha Secondary School
Kageshowri Manohara-09, Kathmandu, NepalBasic principles involved in the traditional systems of medicine, Chapter 7,...



Basic principles involved in the traditional systems of medicine, Chapter 7,...ARUN KUMAR
╠²
Basic principles involved in the traditional systems of medicine include:
Ayurveda, Siddha, Unani, and Homeopathy
Method of preparation of Ayurvedic formulations like:
Arista, Asava, Gutika, Taila, Churna, Lehya and Bhasma
SAMARTH QUIZ 2024-25_ PRELIMINARY ROUNDS



SAMARTH QUIZ 2024-25_ PRELIMINARY ROUNDSAnand Kumar
╠²
SAMARTH QUIZ 2024-25 PRELIMNARY ROUND : Conducted as a part of SAIL level Management Business Quiz at DSP SAIL.Unit 1 Kali NetHunter is the official Kali Linux penetration testing platform...



Unit 1 Kali NetHunter is the official Kali Linux penetration testing platform...ChatanBawankar
╠²
Kali NetHunter is the official Kali Linux penetration testing platform for Android devices. EVALUATION AND MANAGEMENT OF OPEN FRACTURE



EVALUATION AND MANAGEMENT OF OPEN FRACTUREBipulBorthakur
╠²
class on open fracture , for MS orthopaedics Odoo 18 Point of Sale PWA - Odoo ║▌║▌▀Żs



Odoo 18 Point of Sale PWA - Odoo ║▌║▌▀ŻsCeline George
╠²
Progressive Web Apps (PWA) are web applications that deliver an app-like experience using modern web technologies, offering features like offline functionality, installability, and responsiveness across devices. Writing Research Papers: Guidance for Research Community



Writing Research Papers: Guidance for Research CommunityRishi Bankim Chandra Evening College, Naihati, North 24 Parganas, West Bengal, India
╠²
This study describe how to write the Research Paper and its related issues. It also presents the major sections of Research Paper and various tools & techniques used for Polishing Research Paper
before final submission.
Finding a Right Journal and Publication Ethics are explain in brief.
Optical and non optical devices used in low vision



Optical and non optical devices used in low visionAligarh Muslim University, Aligarh, Uttar Pradesh, India
╠²
Low Vison introduction from Aligarh Muslim University



Low Vison introduction from Aligarh Muslim UniversityAligarh Muslim University, Aligarh, Uttar Pradesh, India
╠²
Writing Research Papers: Guidance for Research Community



Writing Research Papers: Guidance for Research CommunityRishi Bankim Chandra Evening College, Naihati, North 24 Parganas, West Bengal, India
╠²
DISHA PATEL COMPUTER VIRUS PPT.pptx
- 1. Presented By- DISHA PATEL CLASS ŌĆō VII-D ROLL NO.- 13 SUBMITTED TO- MRS. khusHboO sahai A PRESENTATION ON COMPUTER VIRUS
- 2. ’āśIntroduction ’āśHow Does It Spread ’āśSymptoms ’āśPrevention ’āśTypes Of Computer Virus ’āśBoot Sector Virus ’āśProgram File Virus ’āśMultipartite Virus ’āśMacro Virus ’āśMalware ’āśWorm ’āśSpyware ’āśTrojen Horse ’āśConclusion
- 3. ’āśComputer viruses are a type of software program that, like a biological virus, reproduces and spreads itself. ’āśFull Form: Vital Information Resource Under Seizes. ’āśSome virus may display only a message on the screen, others may slow down the Pc. ’āśThey can also erase files or even format your floppy or hard disk and crash the system. ’āśCreeper Virus: The first detected on APRANET in the early 1970's. ’āśPopular Viruses: Jerusalem or Israeli Virus, Brain or Pakistani Virus, April First, Ping Pong or Bouncing Ball, Stoned, Dark Avengers, Love bug, Ransomware.
- 4. ’āś Computer viruses spread by attaching themselves to other computer program file. ’āś When you exchange a file or pen drive with a virus, the virus spreads from one computer to the another. ’āś Viruses also spreads when a Computer Engineer comes to repair your system and puts his/her diagnostics disks in your PC.
- 5. ’āśLetters looks like they are falling to the bottom of the screen. ’āśThe computer system becomes slow. ’āśThe size of available free memory reduces. ’āśThe hard disk runs out of space. ’āśThe computer does not boot. ’āśFail to print correctly. ’āśRestarts itself often.
- 6. ’āśUpload and use antivirus software. ’āś Be aware of the e- mails and attachments you open. ’āś Check for updates on antivirus software regularly. ’āś Make sure antivirus software is installed correctly. ’āśOn the computer, turn on the firewall. ’āśKeep the computer operating system up to date.
- 7. ’āśBoot Sector Virus ’āśProgram File Virus ’āśMultipartite Virus ’āśMacro Virus
- 8. ’āśInfects the boot or Master Boot record (MBR), contains info about the drive and the bootstrap loader of diskettes and hard drives through the sharing of infected disks and pirated software applications. ’āśOnce your hard drive is infected all diskettes that you use in your computer will be infected.
- 9. ’āśBecomes active when the program file (usually with extensions BIN, COM, EXE, OVL, DRV) carrying the virus is opened. ’āśIt then makes copies of itself and will infect other programs on the computer.
- 10. ’āśHybrid of a Boot Sector and Program viruses. ’āśIt infects program files and when the infected program is active it will affect the boot record.
- 11. ’āśProgrammed as a macro embedded in a document, usually found in Microsoft Word and Excel. ’āśOnce it gets in to your computer, every document you produce will become infected. ’āśRelatively new type of virus and may slip by your antivirus software if you don't have the most recent version installed.
- 12. ’āśMalware, short for malicious software, refers to any intrusive software developed by cybercriminals (often called hackers) to steal data and damage or destroy computers and computer systems. Examples of common malware include viruses, worms, Trojan viruses, spyware, adware, and ransomware.
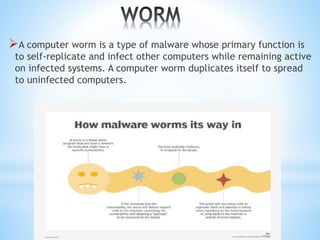
- 13. ’āśA computer worm is a type of malware whose primary function is to self-replicate and infect other computers while remaining active on infected systems. A computer worm duplicates itself to spread to uninfected computers.
- 14. ’āśSpyware is a type of malicious software -- or malware -- that is installed on a computing device without the end user's knowledge. It invades the device, steals sensitive information and internet usage data, and relays it to advertisers, data firms or external users.
- 15. ’āśTrojan horse is a program downloaded and installed on a computer that appears harmless, but is, in fact, malicious. Unexpected changes to computer settings and unusual activity, even when the computer should be idle, are strong indications that a Trojan is residing on a computer.
- 16. Computer viruses and worms can so easily be placed into your work station so you must be careful when going on the internet, opening emails from unknown users, make sure you have some kind of anti-virus software and always get updates so that you aren't helping to spread viruses and worms Other people as well as harming yourself and your pocket.




