Distributed Consensus: Making Impossible Possible
- 1. Distributed Consensus: Making Impossible Possible Heidi Howard PhD Student @ University of Cambridge heidi.howard@cl.cam.ac.uk @heidiann360
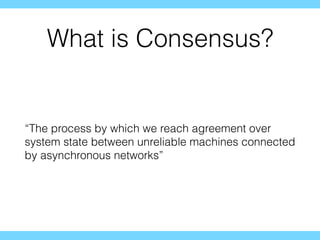
- 3. What is Consensus? ˇ°The process by which we reach agreement over system state between unreliable machines connected by asynchronous networksˇ±
- 4. Why? ? Distributed locking ? Banking ? Safety critical systems ? Distributed scheduling and coordination Anything which requires guaranteed agreement
- 5. A walk through history We are going to take a journey through the developments in distributed consensus, spanning 3 decades. We are going to search for answers to questions like: ? how do we reach consensus? ? what is the best method for reaching consensus? ? can we even reach consensus? ? whatˇŻs next in the ?eld?
- 6. FLP Result off to a slippery start Impossibility of distributed consensus with one faulty process Michael Fischer, Nancy Lynch and Michael Paterson ACM SIGACT-SIGMOD Symposium on Principles of Database Systems 1983
- 7. FLP We cannot guarantee agreement in an asynchronous system where even one host might fail. Why? We cannot reliably detect failures. We cannot know for sure the difference between a slow host/network and a failed host NB: We can still guarantee safety, the issue limited to guaranteeing liveness.
- 8. Solution to FLP In practice: We accept that sometimes the system will not be available. We mitigate this using timers and backoffs. In theory: We make weaker assumptions about the synchrony of the system e.g. messages arrive within a year.
- 9. Paxos LamportˇŻs original consensus algorithm The Part-Time Parliament Leslie Lamport ACM Transactions on Computer Systems May 1998
- 10. Paxos The original consensus algorithm for reaching agreement on a single value. ? two phase process: promise and commit ? majority agreement ? monotonically increasing numbers
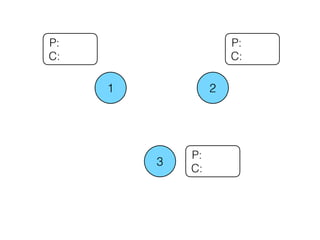
- 11. Paxos Example - Failure Free
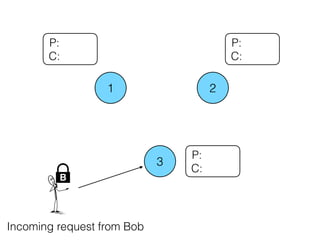
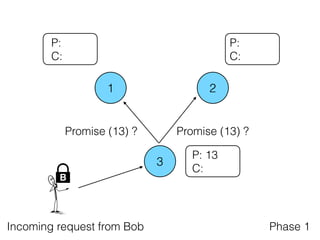
- 13. 1 2 3 P: C: P: C: P: C: B Incoming request from Bob
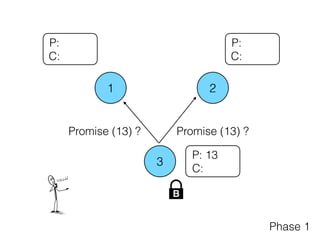
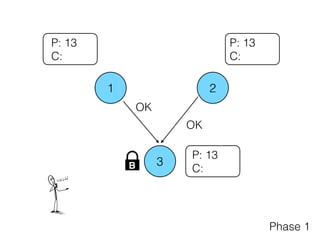
- 14. 1 2 3 P: C: P: 13 C: P: C: B Promise (13) ? Phase 1 Promise (13) ?
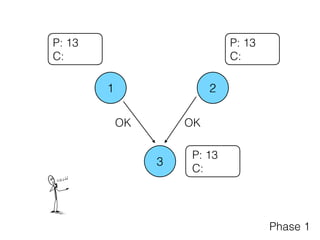
- 15. 1 2 3 P: 13 C: OKOK P: 13 C: P: 13 C: Phase 1
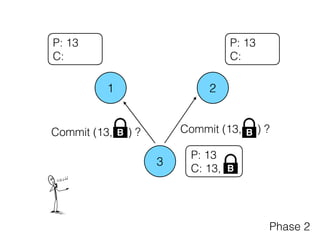
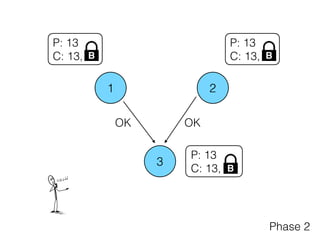
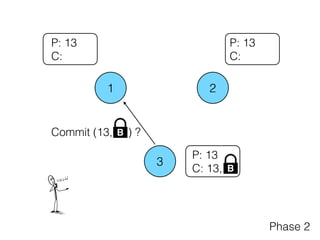
- 16. 1 2 3 P: 13 C: 13, B P: 13 C: P: 13 C: Phase 2 Commit (13, ) ?B Commit (13, ) ?B
- 17. 1 2 3 P: 13 C: 13, B P: 13 C: 13, P: 13 C: 13, Phase 2 B B OKOK
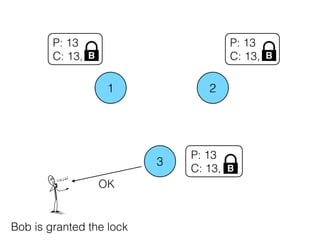
- 18. 1 2 3 P: 13 C: 13, B P: 13 C: 13, P: 13 C: 13, B B OK Bob is granted the lock
- 19. Paxos Example - Node Failure
- 21. 1 2 3 P: C: P: 13 C: P: C: Promise (13) ? Phase 1 B Incoming request from Bob Promise (13) ?
- 22. 1 2 3 P: 13 C: P: 13 C: P: 13 C: Phase 1 B OK OK
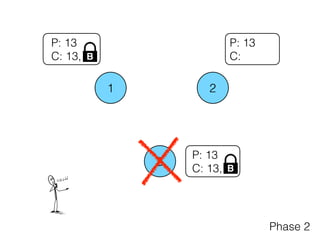
- 23. 1 2 3 P: 13 C: P: 13 C: 13, P: 13 C: Phase 2 Commit (13, ) ?B B
- 24. 1 2 3 P: 13 C: P: 13 C: 13, P: 13 C: 13, Phase 2 B B
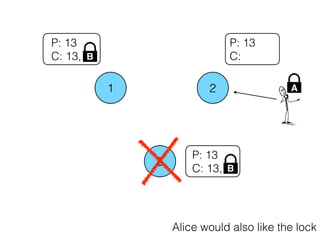
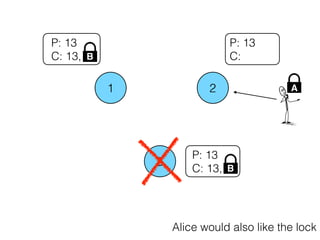
- 25. 1 2 3 P: 13 C: P: 13 C: 13, P: 13 C: 13, Alice would also like the lock B B A
- 26. 1 2 3 P: 13 C: P: 13 C: 13, P: 13 C: 13, Alice would also like the lock B B A
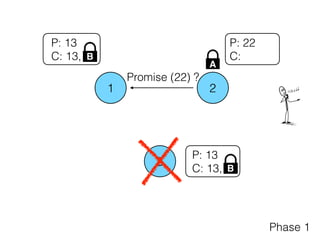
- 27. 1 2 3 P: 22 C: P: 13 C: 13, P: 13 C: 13, Phase 1 B B A Promise (22) ?
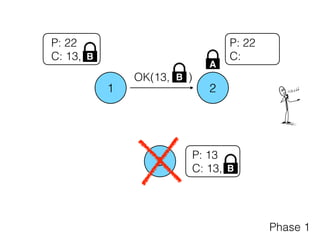
- 28. 1 2 3 P: 22 C: P: 13 C: 13, P: 22 C: 13, Phase 1 B B A OK(13, )B
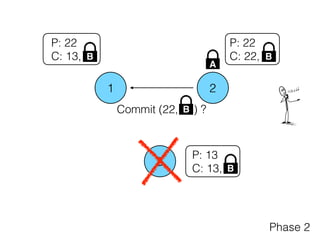
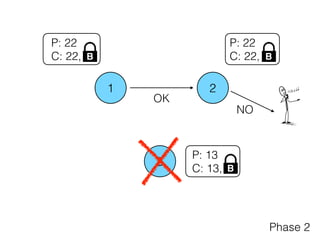
- 29. 1 2 3 P: 22 C: 22, P: 13 C: 13, P: 22 C: 13, Phase 2 B B A Commit (22, ) ?B B
- 30. 1 2 3 P: 22 C: 22, P: 13 C: 13, P: 22 C: 22, Phase 2 B B OK B NO
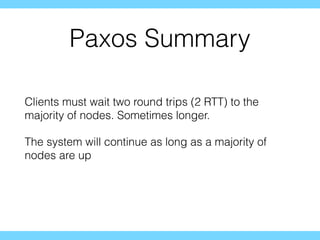
- 31. Paxos Summary Clients must wait two round trips (2 RTT) to the majority of nodes. Sometimes longer. The system will continue as long as a majority of nodes are up
- 32. Multi-Paxos LamportˇŻs leader-driven consensus algorithm Paxos Made Moderately Complex Robbert van Renesse and Deniz Altinbuken ACM Computing Surveys April 2015 Not the original, but highly recommended
- 33. Multi-Paxos LamportˇŻs insight: Phase 1 is not speci?c to the request so can be done before the request arrives and can be reused. Implication: Bob now only has to wait one RTT
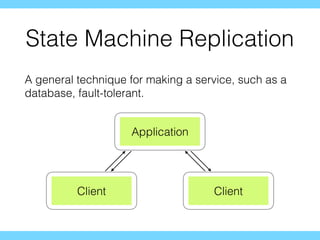
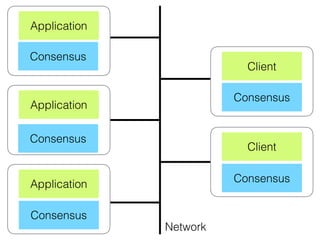
- 34. State Machine Replication fault-tolerant services using consensus Implementing Fault-Tolerant Services Using the State Machine Approach: A Tutorial Fred Schneider ACM Computing Surveys 1990
- 35. State Machine Replication A general technique for making a service, such as a database, fault-tolerant. Application Client Client
- 39. CAP Theorem You cannot have your cake and eat it CAP Theorem Eric Brewer Presented at Symposium on Principles of Distributed Computing, 2000
- 40. Consistency, Availability & Partition Tolerance - Pick Two 1 2 3 4 B C
- 41. Paxos Made Live How google uses Paxos Paxos Made Live - An Engineering Perspective Tushar Chandra, Robert Griesemer and Joshua Redstone ACM Symposium on Principles of Distributed Computing 2007
- 42. Paxos Made Live Paxos made live documents the challenges in constructing Chubby, a distributed coordination service, built using Multi-Paxos and SMR.
- 43. IsnˇŻt this a solved problem? ˇ°There are signi?cant gaps between the description of the Paxos algorithm and the needs of a real-world system. In order to build a real-world system, an expert needs to use numerous ideas scattered in the literature and make several relatively small protocol extensions. The cumulative effort will be substantial and the ?nal system will be based on an unproven protocol.ˇ±
- 44. Challenges ? Handling disk failure and corruption ? Dealing with limited storage capacity ? Effectively handling read-only requests ? Dynamic membership & recon?guration ? Supporting transactions ? Verifying safety of the implementation
- 45. Fast Paxos Like Multi-Paxos, but faster Fast Paxos Leslie Lamport Microsoft Research Tech Report MSR-TR-2005-112
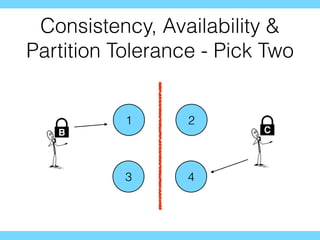
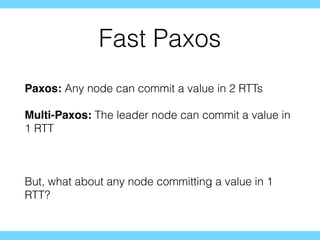
- 46. Fast Paxos Paxos: Any node can commit a value in 2 RTTs Multi-Paxos: The leader node can commit a value in 1 RTT But, what about any node committing a value in 1 RTT?
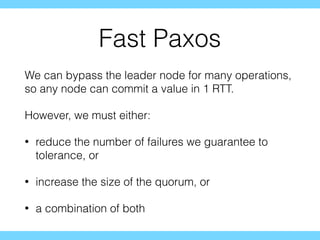
- 47. Fast Paxos We can bypass the leader node for many operations, so any node can commit a value in 1 RTT. However, we must either: ? reduce the number of failures we guarantee to tolerance, or ? increase the size of the quorum, or ? a combination of both
- 48. Egalitarian Paxos DonˇŻt restrict yourself unnecessarily There Is More Consensus in Egalitarian Parliaments Iulian Moraru, David G. Andersen, Michael Kaminsky SOSP 2013 also see Generalized Consensus and Paxos
- 49. Egalitarian Paxos The basis of SMR is that every replica of an application receives the same commands in the same order. However, sometimes the ordering can be relaxedˇ
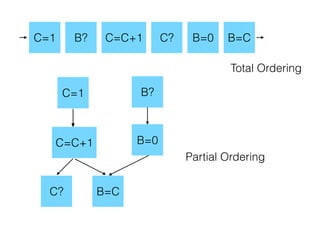
- 50. C=1 B? C=C+1 C? B=0 B=C C=1 B? C=C+1 C? B=0 B=C Partial Ordering Total Ordering
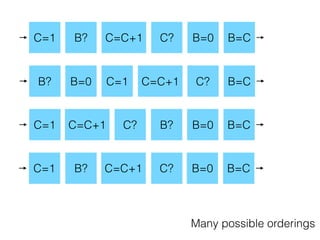
- 51. C=1 B? C=C+1 C? B=0 B=C Many possible orderings B? C=C+1 C?B=0 B=CC=1 B?C=C+1 C? B=0 B=CC=1 B? C=C+1 C? B=0 B=CC=1
- 52. Egalitarian Paxos Allow requests to be out-of-order if they are commutative. Con?ict becomes much less common. Works well in combination with Fast Paxos.
- 53. Viewstamped Replication Revisited the forgotten algorithm Viewstamped Replication Revisited Barbara Liskov and James Cowling MIT Tech Report MIT-CSAIL-TR-2012-021
- 54. Viewstamped Replication Revisited (VRR) Interesting and well explained variant of SMR + Multi- Paxos. Key features: ? Round robin leader election ? Dynamic Membership
- 55. Raft Consensus Paxos made understandable In Search of an Understandable Consensus Algorithm Diego Ongaro and John Ousterhout USENIX Annual Technical Conference 2014
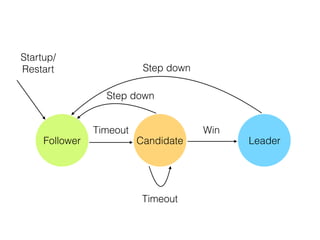
- 56. Raft Raft has taken the wider community by storm. Due to its understandable description. ItˇŻs another variant of SMR with Multi-Paxos. Key features: ? Really strong leadership - all other nodes are passive ? Dynamic membership and log compaction
- 57. Follower Candidate Leader Startup/ Restart Timeout Win Timeout Step down Step down
- 58. Ios Why do things yourself, when you can delegate it? to appear
- 59. Ios The issue with leader-driven algorithms like Multi- Paxos, Raft and VRR is that throughput is limited to one node. Ios allows a leader to safely and dynamically delegate their responsibilities to other nodes in the system.
- 60. Hydra consensus for geo-replication to appear
- 61. Hydra Distributed consensus for systems which span multiple datacenters. We use Ios for replication within the datacenter and a Egalitarian Paxos like protocol for across datacenters. The system has a clear leader but most requests simply bypass the leader.
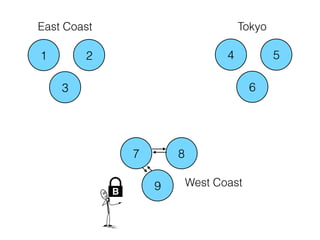
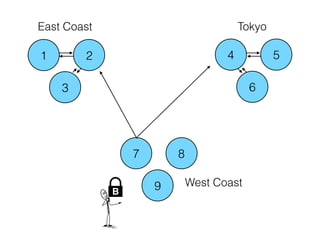
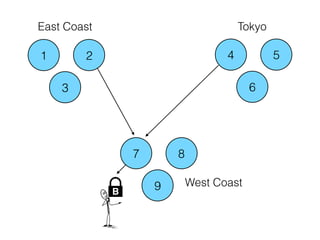
- 62. 1 2 3 4 5 6 7 8 9 Tokyo West Coast East Coast B
- 63. 1 2 3 4 5 6 7 8 9 Tokyo West Coast East Coast B
- 64. 1 2 3 4 5 6 7 8 9 Tokyo West Coast East Coast B
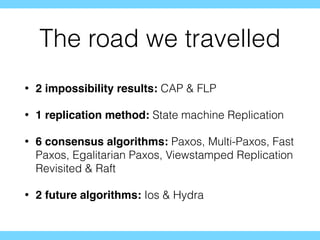
- 65. The road we travelled ? 2 impossibility results: CAP & FLP ? 1 replication method: State machine Replication ? 6 consensus algorithms: Paxos, Multi-Paxos, Fast Paxos, Egalitarian Paxos, Viewstamped Replication Revisited & Raft ? 2 future algorithms: Ios & Hydra
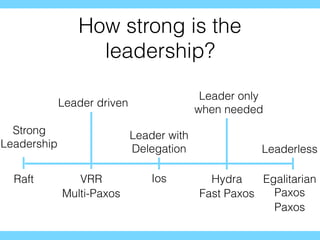
- 66. How strong is the leadership? Strong Leadership Leaderless Paxos Egalitarian Paxos Raft VRR Ios Hydra Multi-Paxos Fast Paxos Leader with Delegation Leader only when needed Leader driven
- 67. Who is the winner? Depends on the award: ? Best for minimum latency: VRR ? Easier to understand: Raft ? Best for WANs (con?icts rare): Egalitarian Paxos ? Best for WANs (con?icts common): Fast Paxos
- 68. Future 1. More algorithms offering a compromise between strong leadership and leaderless 2. More understandable consensus algorithms 3. Achieving consensus is getting cheaper, even in challenging settings 4. Deployment with micro-services and unikernels 5. Self-scaling replication - adapting resources to maintain resilience level.
- 69. Stops we drove passed We have seen one path through history, but many more exist. ? Alternative replication techniques e.g. chain replication and primary backup replication ? Alternative failure models e.g. nodes acting maliciously ? Alternative domains e.g. sensor networks, mobile networks, between cores
- 70. Summary Do not be discouraged by impossibility results and dense abstract academic papers. Consensus is useful and achievable. Find the right algorithm for your speci?c domain. heidi.howard@cl.cam.ac.uk @heidiann360



























![Distributed Consensus: Making Impossible Possible [Revised]](https://cdn.slidesharecdn.com/ss_thumbnails/impossibleconsensus-161020212626-thumbnail.jpg?width=560&fit=bounds)












































