Distributed file systems dfs
Download as PPT, PDF0 likes1,216 views
A distributed file system allows files to be stored on multiple computers that are connected over a network. It implements a common file system that can be accessed by all computers. Key goals are network transparency, so users can access files without knowing their location, and high availability, so files can always be easily accessed regardless of physical location. The main components are a name server that maps file names to locations, and cache managers that store copied of remote files locally to improve performance. Mechanisms like mounting, caching, bulk data transfer, and encryption help build robust distributed file systems.
1 of 12
Downloaded 62 times






Recommended
Distributed file system



Distributed file systemAnamika Singh
╠²
The document discusses key concepts related to distributed file systems including:
1. Files are accessed using location transparency where the physical location is hidden from users. File names do not reveal storage locations and names do not change when locations change.
2. Remote files can be mounted to local directories, making them appear local while maintaining location independence. Caching is used to reduce network traffic by storing recently accessed data locally.
3. Fault tolerance is improved through techniques like stateless server designs, file replication across failure independent machines, and read-only replication for consistency. Scalability is achieved by adding new nodes and using decentralized control through clustering.GOOGLE FILE SYSTEM



GOOGLE FILE SYSTEMJYoTHiSH o.s
╠²
Designed by Sanjay Ghemawat , Howard Gobioff and Shun-Tak Leung of Google in 2002-03.
Provides fault tolerance, serving large number of clients with high aggregate performance.
The field of Google is beyond the searching.
Google store the data in more than 15 thousands commodity hardware.
Handles the exceptions of Google and other Google specific challenges in their distributed file system.
message passing



message passingAshish Kumar
╠²
The document discusses various design issues related to interprocess communication using message passing. It covers topics like synchronization methods, buffering strategies, process addressing schemes, reliability in message passing, and group communication. The key synchronization methods are blocking and non-blocking sends/receives. Issues addressed include blocking forever if the receiving process crashes, buffering strategies like null, single-message and finite buffers, and naming schemes like explicit and implicit addressing. Reliability is achieved using protocols like four-message, three-message and two-message. Group communication supports one-to-many, many-to-one and many-to-many communication with primitives for multicast, membership and different ordering semantics.Storage Area Networks Unit 2 Notes



Storage Area Networks Unit 2 NotesSudarshan Dhondaley
╠²
INTELLIGENT DISK SUBSYSTEMS ŌĆō 2, I/O TECHNIQUES ŌĆō 1
Caching: Acceleration of Hard Disk Access; Intelligent disk subsystems; Availability of disk subsystems. The Physical I/O path from the CPU to the Storage System; SCSI.
I/O TECHNIQUES ŌĆō 2, NETWORK ATTACHED STORAGE
Fibre Channel Protocol Stack; Fibre Channel SAN; IP Storage. The NAS Architecture, The NAS hardware Architecture, The NAS Software Architecture, Network connectivity, NAS as a storage system. Distributed system architecture



Distributed system architectureYisal Khan
╠²
A distributed system is a collection of computational and storage devices connected through a communications network. In this type of system, data, software, and users are distributed.
Understanding das-nas-san



Understanding das-nas-sanAshwin Pawar
╠²
https://inode-2-blocks.blogspot.com/
NFS vs SAN
/AshwinPawar/nas-vs-sanPeer to Peer services and File systems



Peer to Peer services and File systemsMNM Jain Engineering College
╠²
Peer-to-peer Systems ŌĆō Introduction ŌĆō Napster and its legacy ŌĆō Peer-to-peer ŌĆō Middleware ŌĆō Routing overlays. Overlay case studies: Pastry, Tapestry- Distributed File Systems ŌĆōIntroduction ŌĆō File service architecture ŌĆō Andrew File system. File System: Features-File model -File accessing models ŌĆō File sharing semantics Naming: Identifiers, Addresses, Name Resolution ŌĆō Name Space Implementation ŌĆō Name Caches ŌĆō LDAP.Google file system GFS



Google file system GFSzihad164
╠²
Google File System is a distributed file system developed by Google to provide efficient and reliable access to large amounts of data across clusters of commodity hardware. It organizes clusters into clients that interface with the system, master servers that manage metadata, and chunkservers that store and serve file data replicated across multiple machines. Updates are replicated for fault tolerance, while the master and chunkservers work together for high performance streaming and random reads and writes of large files.Replication in Distributed Systems



Replication in Distributed SystemsKavya Barnadhya Hazarika
╠²
Replication in computing involves sharing information so as to ensure consistency between redundant resources, such as software or hardware components, to improve reliability, fault-tolerance, or accessibility. Distributed deadlock



Distributed deadlockMd. Mahedi Mahfuj
╠²
Distributed deadlock occurs when processes are blocked while waiting for resources held by other processes in a distributed system without a central coordinator. There are four conditions for deadlock: mutual exclusion, hold and wait, non-preemption, and circular wait. Deadlock can be addressed by ignoring it, detecting and resolving occurrences, preventing conditions through constraints, or avoiding it through careful resource allocation. Detection methods include centralized coordination of resource graphs or distributed probe messages to identify resource waiting cycles. Prevention strategies impose timestamp or age-based priority to resource requests to eliminate cycles.Deadlock in Distributed Systems



Deadlock in Distributed SystemsPritom Saha Akash
╠²
Deadlocks occur when processes are waiting for resources held by other processes, resulting in a circular wait. Four conditions must be met: mutual exclusion, hold and wait, no preemption, and circular wait. Deadlocks can be handled through avoidance, prevention, or detection and recovery. Avoidance algorithms allocate resources only if it ensures the system remains in a safe state where deadlocks cannot occur. Prevention methods make deadlocks impossible by ensuring at least one condition is never satisfied, such as through collective or ordered resource requests. Detection finds existing deadlocks by analyzing resource allocation graphs or wait-for graphs to detect cycles.Message passing in Distributed Computing Systems



Message passing in Distributed Computing SystemsAlagappa Govt Arts College, Karaikudi
╠²
This document discusses interprocess communication (IPC) and message passing in distributed systems. It covers key topics such as:
- The two main approaches to IPC - shared memory and message passing
- Desirable features of message passing systems like simplicity, uniform semantics, efficiency, reliability, correctness, flexibility, security, and portability
- Issues in message passing IPC like message format, synchronization methods (blocking vs. non-blocking), and buffering strategies File models and file accessing models



File models and file accessing modelsishmecse13
╠²
This document discusses different file models and methods for accessing files. It describes unstructured and structured file models, as well as mutable and immutable files. It also covers remote file access using remote service and data caching models. Finally, it discusses different units of data transfer for file access, including file-level, block-level, byte-level, and record-level transfer models.Distributed Systems



Distributed SystemsRupsee
╠²
Distributed systems allow independent computers to appear as a single coherent system by connecting them through a middleware layer. They provide advantages like increased reliability, scalability, and sharing of resources. Key goals of distributed systems include resource sharing, openness, transparency, and concurrency. Common types are distributed computing systems, distributed information systems, and distributed pervasive systems.File replication



File replicationKlawal13
╠²
File Replication : High availability is a desirable feature of a good distributed file system and file replication is the primary mechanism for improving file availability. Replication is a key strategy for improving reliability, fault tolerance and availability. Therefore duplicating files on multiple machines improves availability and performance.
Replicated file : A replicated file is a file that has multiple copies, with each copy located on a separate file server. Each copy of the set of copies that comprises a replicated file is referred to as replica of the replicated file.
Replication is often confused with caching, probably because they both deal with multiple copies of data. The two concepts has the following basic differences:
A replica is associated with server, whereas a cached copy is associated with a client.
The existence of cached copy is primarily dependent on the locality in file access patterns, whereas the existence of a replica normally depends on availability and performance requirements.
Satynarayanana [1992] distinguishes a replicated copy from a cached copy by calling the first-class replicas and second-class replicas respectively
Chapter 11 - File System Implementation



Chapter 11 - File System ImplementationWayne Jones Jnr
╠²
File-System Structure
File-System Implementation
Directory Implementation
Allocation Methods
Free-Space Management
Efficiency and Performance
Recovery
Log-Structured File Systems
NFS
Example: WAFL File SystemNaming in Distributed System



Naming in Distributed SystemMNM Jain Engineering College
╠²
The document discusses naming in distributed systems. It covers desirable features of naming systems like location transparency and location independence. It differentiates between human-oriented and system-oriented names. It also discusses name spaces, name servers, name resolution including recursive and iterative approaches, and name caching.Distributed File Systems 



Distributed File Systems Maurvi04
╠²
This document discusses key aspects of distributed file systems including file caching schemes, file replication, and fault tolerance. It describes different cache locations, modification propagation techniques, and methods for replica creation. File caching schemes aim to reduce network traffic by retaining recently accessed files in memory. File replication provides increased reliability and availability through independent backups. Distributed file systems must also address being stateful or stateless to maintain information about file access and operations.Communication in Distributed Systems



Communication in Distributed SystemsDilum Bandara
╠²
Overview of Network Programming, Remote Procedure Calls, Remote Method Invocation, Message Oriented Communication, and web services in distributed systemsFault tolerance



Fault toleranceGaurav Rawat
╠²
This document discusses fault tolerance in computing systems. It defines fault tolerance as building systems that can continue operating satisfactorily even in the presence of faults. It describes different types of faults like transient, intermittent, and permanent hardware faults. It also discusses concepts like errors, failures, fault taxonomy, attributes of fault tolerance like availability and reliability. It explains various techniques used for fault tolerance like error detection, system recovery, fault masking, and redundancy.Distributed Objects and Remote Invocation



Distributed Objects and Remote InvocationMedicaps University
╠²
Distributed Objects and Remote Invocation: Communication between distributed objects
Remote procedure call, Events and notifications, operating system layer Protection, Processes
and threads, Operating system architecture. Introduction to Distributed shared memory,
Design and implementation issue of DSM.Case Study: CORBA and JAVA RMI.Distributed web based systems



Distributed web based systemsReza Gh
╠²
This document provides an overview of distributed web-based systems, including the key components and technologies that enable them. It discusses the World Wide Web and how documents are accessed via URLs. It also describes HTTP and how connections and requests/responses work. Other topics covered include caching, content distribution networks, web services, traditional and multi-tiered web architectures, web server clusters, and web security protocols like SSL. distributed shared memory



distributed shared memoryAshish Kumar
╠²
Distributed shared memory (DSM) provides processes with a shared address space across distributed memory systems. DSM exists only virtually through primitives like read and write operations. It gives the illusion of physically shared memory while allowing loosely coupled distributed systems to share memory. DSM refers to applying this shared memory paradigm using distributed memory systems connected by a communication network. Each node has CPUs, memory, and blocks of shared memory can be cached locally but migrated on demand between nodes to maintain consistency.Foult Tolerence In Distributed System



Foult Tolerence In Distributed SystemRajan Kumar
╠²
Distributed systems use multiple autonomous computers that communicate via messages to improve processing throughput, allow for CPU specialization, and provide fault tolerance. Faults in distributed systems can include data corruption, hanging processes, misleading return values, hardware/software/network outages, and resource overcommitment. To provide fault tolerance, processes are replicated across multiple computers so the system can continue functioning even if some processes fail. There are different types of faults like crash faults, omission faults, and Byzantine faults. Recovery from failures can use backward or forward recovery approaches.Deadlock in distribute system by saeed siddik



Deadlock in distribute system by saeed siddikSaeed Siddik
╠²
The document discusses deadlocks in distributed systems, outlining the four conditions required for a deadlock, strategies to handle deadlocks such as ignoring, detecting, preventing, and avoiding them, and algorithms for centralized deadlock detection and distributed deadlock detection and prevention. It provides examples of resource allocation graphs to illustrate deadlock conditions and explains how distributed deadlock detection and prevention algorithms work.Agreement Protocols, distributed File Systems, Distributed Shared Memory



Agreement Protocols, distributed File Systems, Distributed Shared MemorySHIKHA GAUTAM
╠²
Agreement Protocols, Distributed Resource Management: Issues in distributed File Systems, Mechanism for building distributed file systems, Design issues in Distributed Shared Memory, Algorithm for Implementation of Distributed Shared Memory.
Distributed Operating System



Distributed Operating SystemAjithaG9
╠²
*DISTRIBUTED COMPUTING SYSTEM MODELS
*ISSUES IN DESIGNING DISTRIBUTED
OPERATING SYSTEMS
*COMPONENTS OF DISTRIBUTED COMPUTING ENVIRONMENT
(DCE)
Introduction to Distributed System



Introduction to Distributed SystemSunita Sahu
╠²
The document provides an introduction to distributed systems, defining them as a collection of independent computers that communicate over a network to act as a single coherent system. It discusses the motivation for and characteristics of distributed systems, including concurrency, lack of a global clock, and independence of failures. Architectural categories of distributed systems include tightly coupled and loosely coupled, with examples given of different types of distributed systems such as database management systems, ATM networks, and the internet.Distributed File System.ppt



Distributed File System.pptKhawajaWaqasRaheel
╠²
Distributed file systems allow files to be accessed across a network in a transparent manner. They achieve high availability by allowing users easy access to files irrespective of physical location. A DFS uses name servers to map file names to storage locations and cache managers to copy remote files to clients for faster access. Key components include caching, replication for availability, and consistency protocols to ensure clients see up-to-date file data. Design goals involve scalability to large numbers of clients and servers as well as maintaining strong file semantics even in distributed systems.CS9222 ADVANCED OPERATING SYSTEMS



CS9222 ADVANCED OPERATING SYSTEMSKathirvel Ayyaswamy
╠²
Distributed File systems ŌĆō Architecture ŌĆō Mechanisms ŌĆō Design Issues ŌĆō Distributed Shared
Memory ŌĆō Architecture ŌĆō Algorithm ŌĆō Protocols - Design Issues. Distributed Scheduling ŌĆō Issues
ŌĆō Components ŌĆō Algorithms.
More Related Content
What's hot (20)
Replication in Distributed Systems



Replication in Distributed SystemsKavya Barnadhya Hazarika
╠²
Replication in computing involves sharing information so as to ensure consistency between redundant resources, such as software or hardware components, to improve reliability, fault-tolerance, or accessibility. Distributed deadlock



Distributed deadlockMd. Mahedi Mahfuj
╠²
Distributed deadlock occurs when processes are blocked while waiting for resources held by other processes in a distributed system without a central coordinator. There are four conditions for deadlock: mutual exclusion, hold and wait, non-preemption, and circular wait. Deadlock can be addressed by ignoring it, detecting and resolving occurrences, preventing conditions through constraints, or avoiding it through careful resource allocation. Detection methods include centralized coordination of resource graphs or distributed probe messages to identify resource waiting cycles. Prevention strategies impose timestamp or age-based priority to resource requests to eliminate cycles.Deadlock in Distributed Systems



Deadlock in Distributed SystemsPritom Saha Akash
╠²
Deadlocks occur when processes are waiting for resources held by other processes, resulting in a circular wait. Four conditions must be met: mutual exclusion, hold and wait, no preemption, and circular wait. Deadlocks can be handled through avoidance, prevention, or detection and recovery. Avoidance algorithms allocate resources only if it ensures the system remains in a safe state where deadlocks cannot occur. Prevention methods make deadlocks impossible by ensuring at least one condition is never satisfied, such as through collective or ordered resource requests. Detection finds existing deadlocks by analyzing resource allocation graphs or wait-for graphs to detect cycles.Message passing in Distributed Computing Systems



Message passing in Distributed Computing SystemsAlagappa Govt Arts College, Karaikudi
╠²
This document discusses interprocess communication (IPC) and message passing in distributed systems. It covers key topics such as:
- The two main approaches to IPC - shared memory and message passing
- Desirable features of message passing systems like simplicity, uniform semantics, efficiency, reliability, correctness, flexibility, security, and portability
- Issues in message passing IPC like message format, synchronization methods (blocking vs. non-blocking), and buffering strategies File models and file accessing models



File models and file accessing modelsishmecse13
╠²
This document discusses different file models and methods for accessing files. It describes unstructured and structured file models, as well as mutable and immutable files. It also covers remote file access using remote service and data caching models. Finally, it discusses different units of data transfer for file access, including file-level, block-level, byte-level, and record-level transfer models.Distributed Systems



Distributed SystemsRupsee
╠²
Distributed systems allow independent computers to appear as a single coherent system by connecting them through a middleware layer. They provide advantages like increased reliability, scalability, and sharing of resources. Key goals of distributed systems include resource sharing, openness, transparency, and concurrency. Common types are distributed computing systems, distributed information systems, and distributed pervasive systems.File replication



File replicationKlawal13
╠²
File Replication : High availability is a desirable feature of a good distributed file system and file replication is the primary mechanism for improving file availability. Replication is a key strategy for improving reliability, fault tolerance and availability. Therefore duplicating files on multiple machines improves availability and performance.
Replicated file : A replicated file is a file that has multiple copies, with each copy located on a separate file server. Each copy of the set of copies that comprises a replicated file is referred to as replica of the replicated file.
Replication is often confused with caching, probably because they both deal with multiple copies of data. The two concepts has the following basic differences:
A replica is associated with server, whereas a cached copy is associated with a client.
The existence of cached copy is primarily dependent on the locality in file access patterns, whereas the existence of a replica normally depends on availability and performance requirements.
Satynarayanana [1992] distinguishes a replicated copy from a cached copy by calling the first-class replicas and second-class replicas respectively
Chapter 11 - File System Implementation



Chapter 11 - File System ImplementationWayne Jones Jnr
╠²
File-System Structure
File-System Implementation
Directory Implementation
Allocation Methods
Free-Space Management
Efficiency and Performance
Recovery
Log-Structured File Systems
NFS
Example: WAFL File SystemNaming in Distributed System



Naming in Distributed SystemMNM Jain Engineering College
╠²
The document discusses naming in distributed systems. It covers desirable features of naming systems like location transparency and location independence. It differentiates between human-oriented and system-oriented names. It also discusses name spaces, name servers, name resolution including recursive and iterative approaches, and name caching.Distributed File Systems 



Distributed File Systems Maurvi04
╠²
This document discusses key aspects of distributed file systems including file caching schemes, file replication, and fault tolerance. It describes different cache locations, modification propagation techniques, and methods for replica creation. File caching schemes aim to reduce network traffic by retaining recently accessed files in memory. File replication provides increased reliability and availability through independent backups. Distributed file systems must also address being stateful or stateless to maintain information about file access and operations.Communication in Distributed Systems



Communication in Distributed SystemsDilum Bandara
╠²
Overview of Network Programming, Remote Procedure Calls, Remote Method Invocation, Message Oriented Communication, and web services in distributed systemsFault tolerance



Fault toleranceGaurav Rawat
╠²
This document discusses fault tolerance in computing systems. It defines fault tolerance as building systems that can continue operating satisfactorily even in the presence of faults. It describes different types of faults like transient, intermittent, and permanent hardware faults. It also discusses concepts like errors, failures, fault taxonomy, attributes of fault tolerance like availability and reliability. It explains various techniques used for fault tolerance like error detection, system recovery, fault masking, and redundancy.Distributed Objects and Remote Invocation



Distributed Objects and Remote InvocationMedicaps University
╠²
Distributed Objects and Remote Invocation: Communication between distributed objects
Remote procedure call, Events and notifications, operating system layer Protection, Processes
and threads, Operating system architecture. Introduction to Distributed shared memory,
Design and implementation issue of DSM.Case Study: CORBA and JAVA RMI.Distributed web based systems



Distributed web based systemsReza Gh
╠²
This document provides an overview of distributed web-based systems, including the key components and technologies that enable them. It discusses the World Wide Web and how documents are accessed via URLs. It also describes HTTP and how connections and requests/responses work. Other topics covered include caching, content distribution networks, web services, traditional and multi-tiered web architectures, web server clusters, and web security protocols like SSL. distributed shared memory



distributed shared memoryAshish Kumar
╠²
Distributed shared memory (DSM) provides processes with a shared address space across distributed memory systems. DSM exists only virtually through primitives like read and write operations. It gives the illusion of physically shared memory while allowing loosely coupled distributed systems to share memory. DSM refers to applying this shared memory paradigm using distributed memory systems connected by a communication network. Each node has CPUs, memory, and blocks of shared memory can be cached locally but migrated on demand between nodes to maintain consistency.Foult Tolerence In Distributed System



Foult Tolerence In Distributed SystemRajan Kumar
╠²
Distributed systems use multiple autonomous computers that communicate via messages to improve processing throughput, allow for CPU specialization, and provide fault tolerance. Faults in distributed systems can include data corruption, hanging processes, misleading return values, hardware/software/network outages, and resource overcommitment. To provide fault tolerance, processes are replicated across multiple computers so the system can continue functioning even if some processes fail. There are different types of faults like crash faults, omission faults, and Byzantine faults. Recovery from failures can use backward or forward recovery approaches.Deadlock in distribute system by saeed siddik



Deadlock in distribute system by saeed siddikSaeed Siddik
╠²
The document discusses deadlocks in distributed systems, outlining the four conditions required for a deadlock, strategies to handle deadlocks such as ignoring, detecting, preventing, and avoiding them, and algorithms for centralized deadlock detection and distributed deadlock detection and prevention. It provides examples of resource allocation graphs to illustrate deadlock conditions and explains how distributed deadlock detection and prevention algorithms work.Agreement Protocols, distributed File Systems, Distributed Shared Memory



Agreement Protocols, distributed File Systems, Distributed Shared MemorySHIKHA GAUTAM
╠²
Agreement Protocols, Distributed Resource Management: Issues in distributed File Systems, Mechanism for building distributed file systems, Design issues in Distributed Shared Memory, Algorithm for Implementation of Distributed Shared Memory.
Distributed Operating System



Distributed Operating SystemAjithaG9
╠²
*DISTRIBUTED COMPUTING SYSTEM MODELS
*ISSUES IN DESIGNING DISTRIBUTED
OPERATING SYSTEMS
*COMPONENTS OF DISTRIBUTED COMPUTING ENVIRONMENT
(DCE)
Introduction to Distributed System



Introduction to Distributed SystemSunita Sahu
╠²
The document provides an introduction to distributed systems, defining them as a collection of independent computers that communicate over a network to act as a single coherent system. It discusses the motivation for and characteristics of distributed systems, including concurrency, lack of a global clock, and independence of failures. Architectural categories of distributed systems include tightly coupled and loosely coupled, with examples given of different types of distributed systems such as database management systems, ATM networks, and the internet.Similar to Distributed file systems dfs (20)
Distributed File System.ppt



Distributed File System.pptKhawajaWaqasRaheel
╠²
Distributed file systems allow files to be accessed across a network in a transparent manner. They achieve high availability by allowing users easy access to files irrespective of physical location. A DFS uses name servers to map file names to storage locations and cache managers to copy remote files to clients for faster access. Key components include caching, replication for availability, and consistency protocols to ensure clients see up-to-date file data. Design goals involve scalability to large numbers of clients and servers as well as maintaining strong file semantics even in distributed systems.CS9222 ADVANCED OPERATING SYSTEMS



CS9222 ADVANCED OPERATING SYSTEMSKathirvel Ayyaswamy
╠²
Distributed File systems ŌĆō Architecture ŌĆō Mechanisms ŌĆō Design Issues ŌĆō Distributed Shared
Memory ŌĆō Architecture ŌĆō Algorithm ŌĆō Protocols - Design Issues. Distributed Scheduling ŌĆō Issues
ŌĆō Components ŌĆō Algorithms.
OSCh16



OSCh16Joe Christensen
╠²
This document discusses distributed file systems (DFS), including their structure, naming and transparency, remote file access, caching, consistency issues, stateful vs stateless service, file replication, and examples like the Andrew distributed computing environment. Key points are that a DFS manages dispersed storage across a network, provides location and naming transparency, uses caching to improve performance of remote access, and must address consistency between cached and master copies of files.Ch16 OS



Ch16 OSC.U
╠²
This document provides an overview of distributed file systems (DFS), including naming and transparency, remote file access, caching techniques, and example systems such as the Andrew file system. Some key points are:
- A DFS manages dispersed storage devices across a network to provide a shared file space for multiple users. It provides location transparency so file locations are hidden from clients.
- Caching is used to improve performance of remote file access by retaining frequently used data locally. Consistency must be maintained between cached and master copies.
- Systems can use stateful or stateless file service. Stateful requires maintaining client session data while stateless makes each request self-contained.
- The Andrew file system example illustratesOS_Ch16



OS_Ch16Supriya Shrivastava
╠²
This document provides an overview of distributed file systems (DFS), including their structure, naming and transparency, remote file access, caching, and example systems. Some key points:
- A DFS manages dispersed storage devices across a network to provide shared files and storage. It provides location transparency so the physical location of files is hidden from users.
- Remote file access in DFS is enabled through caching, where frequently accessed data is cached locally to reduce network traffic. This raises cache consistency issues in keeping cached copies up-to-date.
- The Andrew distributed computing environment example presented a DFS with a shared name space spanning over 5,000 workstations using whole-file caching for remote access.Chapter 17 - Distributed File Systems



Chapter 17 - Distributed File SystemsWayne Jones Jnr
╠²
Background
Naming and Transparency
Remote File Access
Stateful versus Stateless Service
File Replication
An Example: AFSDFS PPT.pptx



DFS PPT.pptxVMahesh5
╠²
In computing, a distributed file system (DFS) or network file system is any file system that allows access to files from multiple hosts sharing via a computer network. This makes it possible for multiple users on multiple machines to share files and storage resources.Document 22.pdf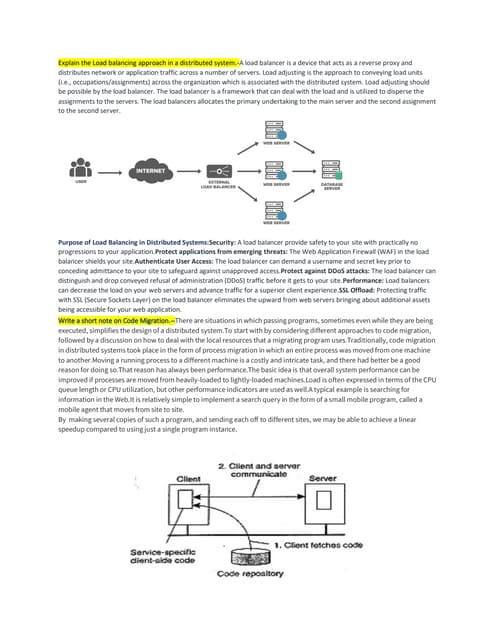



Document 22.pdfrahulsahu887608
╠²
Load balancing is an approach to distributing work units across multiple servers in a distributed system. The load balancer acts as a reverse proxy to distribute network or application traffic evenly among servers. It allocates the first task to the first server, second task to the second server, and so on, to balance loads. Load balancing provides security, protects applications from threats using a web application firewall, authenticates user access, protects against DDoS attacks, and improves performance by reducing load on servers and optimizing traffic.Survey of distributed storage system



Survey of distributed storage systemZhichao Liang
╠²
This slide introduces DAS, NAS, SAN and something about object storage, storage virtualization and distributed file system.Dos unit 4



Dos unit 4JebasheelaSJ
╠²
Distributed file system
Desirable features
file models
unstructured and structured files
mutable
immutable
file accessing file
accessing remote file
file sharing semantics
file caching scheme
replication
fault tolerance
atomic transaction
design principle
12. dfs



12. dfsDr Sandeep Kumar Poonia
╠²
This document discusses distributed file systems. It defines a distributed file system as a classical file system model that is distributed across multiple machines to promote sharing of dispersed files. The key aspects covered are that clients, servers, and storage are dispersed across machines and clients should view a distributed file system the same way as a centralized file system, with the distribution hidden at a lower level. Performance concerns for distributed file systems include throughput and response time.11. dfs



11. dfsDr Sandeep Kumar Poonia
╠²
A Distributed File System(DFS) is simply a classical model of a file system distributed across multiple machines.The purpose is to promote sharing of dispersed files.Distributed file systems chapter 9



Distributed file systems chapter 9Alagappa Government Arts College, Karaikudi
╠²
This chapter deals with the various concepts ind distributed file systems text authored by Pradeep K, SinhaAuthenticated key exchange protocols for parallel



Authenticated key exchange protocols for paralleljpstudcorner
╠²
Chennai Office: JP INFOTECH, Old No.31, New No.86, 1st Floor, 1st Avenue, Ashok Nagar, Chennai-83. Landmark: Next to Kotak Mahendra Bank/Bharath Scans
Landline: (044) - 43012642 / Mobile: (0)9952649690
Pondicherry Office: JP INFOTECH, #45, Kamaraj Salai, Thattanchavady, Puducherry - 9
Landmark: Opp. to Thattanchavady Industrial Estate & Next to VVP Nagar Arch.
Landline: (0413) - 4300535 / Mobile: (0)8608600246 / (0)9952649690
Chapter-5-DFS.ppt



Chapter-5-DFS.pptrameshwarchintamani
╠²
The document discusses distributed file systems. It defines a distributed file system as a classical model of a file system distributed across multiple machines to promote sharing of dispersed files. Key aspects discussed include:
- Files are accessed using the same operations (create, read, etc.) regardless of physical location.
- Systems aim to make file locations transparent to clients through techniques like replication and unique file identifiers.
- Caching is used to improve performance by retaining recently accessed data locally to reduce remote access.
- Consistency must be maintained when copies are updated.Deduplication - Remove Duplicate



Deduplication - Remove Duplicatetxttoolsmanipulation
╠²
Data deDuplication - deDup
deDuplication - English
Deduplikace - ─īe┼Ītina
Deduplikation - Deutsch
Deduplicaci├│n Espa├▒ol
D├®duplication - Fran├¦ais
Datadeduplisering - Norsk
ąöąĄą┤čāą┐ą╗ąĖą║ą░čåąĖčÅ - ąĀčāčüčüą║ąĖą╣
ąöąĄą┤čāą▒ą╗č¢ą║ą░čåč¢čÅ - ąŻą║čĆą░茹Įčüčīą║ą░final-unit-ii-cc-cloud computing-2022.pdf



final-unit-ii-cc-cloud computing-2022.pdfSamiksha880257
╠²
The document discusses data storage and cloud computing. It provides an overview of different types of data storage, including direct attached storage (DAS), network attached storage (NAS), and storage area networks (SANs). It also describes different classes of cloud storage, such as unmanaged and managed cloud storage. The document outlines some of the challenges of cloud storage and how cloud providers create virtual storage containers to manage data storage in the cloud.A cloud environment for backup and data storage



A cloud environment for backup and data storageIGEEKS TECHNOLOGIES
╠²
The document proposes a cloud environment for backup and data storage using remote servers that can be accessed through the Internet. It involves using the disks of cluster nodes as a global storage system with PVFS2 parallel file system for improved performance. The proposed system aims to increase data availability and reduce information loss by storing data on a private cloud using PVFS2 and developing a multiplatform client application for fast data transfer. It allows reuse of existing infrastructure to reduce costs and gives users experience of managing a private cloud.A cloud enviroment for backup and data storage



A cloud enviroment for backup and data storageIGEEKS TECHNOLOGIES
╠²
IGeekS Technologies (Make Final Year Project)
No: 19, MN Complex, 2nd Cross,
Sampige Main Road, Malleswaram
Bangalore- 560003.
Phone No: 080-32487434 /9590544567 / 9739066172
Mail: nandu@igeekstechnologies.com , nanduigeeks2010@gmail.com
Land mark : Near to Mantri Mall, Malleswaram BangaloreDistributed database



Distributed databasesanjay joshi
╠²
A distributed database is a collection of logically interrelated databases distributed over a computer network. A distributed database management system manages the distributed database and provides transparent access to users. Distributed databases can be either homogeneous, with identical software and compatibility across sites, or heterogeneous, with different schemas, software, and data structures at different sites. Key challenges of distributed databases include concurrency control, recovery from failures, and maintaining data consistency across multiple locations.Recently uploaded (20)
Industry 4.0: Transforming Modern Manufacturing and Beyond



Industry 4.0: Transforming Modern Manufacturing and BeyondGtxDriver
╠²
This document explores the fundamental concepts, technologies, and applications of Industry 4.0. Topics include automation, IoT (Internet of Things), smart factories, cyber-physical systems, and the integration of AI and big data analytics in industrial processes. It serves as a comprehensive resource for students, professionals, and enthusiasts eager to delve into the fourth industrial revolution.MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx![MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx](https://cdn.slidesharecdn.com/ss_thumbnails/module01-cloudcomputing-250409082345-d719f5bc-thumbnail.jpg?width=560&fit=bounds)
![MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx](https://cdn.slidesharecdn.com/ss_thumbnails/module01-cloudcomputing-250409082345-d719f5bc-thumbnail.jpg?width=560&fit=bounds)
![MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx](https://cdn.slidesharecdn.com/ss_thumbnails/module01-cloudcomputing-250409082345-d719f5bc-thumbnail.jpg?width=560&fit=bounds)
![MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx](https://cdn.slidesharecdn.com/ss_thumbnails/module01-cloudcomputing-250409082345-d719f5bc-thumbnail.jpg?width=560&fit=bounds)
MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptxAlvas Institute of Engineering and technology, Moodabidri
╠²
Distributed System Models and Enabling Technologies: Scalable Computing Over the
Internet, Technologies for Network Based Systems, System Models for Distributed and
Cloud Computing, Software Environments for Distributed Systems and Clouds,
Performance, Security and Energy Efficiency.22PCOAM16 ML UNIT 2 NOTES & QB QUESTION WITH ANSWERS



22PCOAM16 ML UNIT 2 NOTES & QB QUESTION WITH ANSWERSGuru Nanak Technical Institutions
╠²
22PCOAM16 ML UNIT 2 NOTES & QB QUESTION WITH ANSWERS Intro of Airport Engg..pptx-Definition of airport engineering and airport pla...



Intro of Airport Engg..pptx-Definition of airport engineering and airport pla...Priyanka Dange
╠²
Definition of airport engineering and airport planning, Types of surveys required for airport site, Factors affecting the selection of site for AirportExplainability and Transparency in Artificial Intelligence: Ethical Imperativ...



Explainability and Transparency in Artificial Intelligence: Ethical Imperativ...AI Publications
╠²
Artificial Intelligence (AI) is increasingly embedded in high-stakes domains such as healthcare, finance, and law enforcement, where opaque decision-making raises significant ethical concerns. Among the core challenges in AI ethics are explainability and transparencyŌĆökey to fostering trust, accountability, and fairness in algorithmic systems. This review explores the ethical foundations of explainable AI (XAI), surveys leading technical approaches such as model-agnostic interpretability techniques and post-hoc explanation methods and examines their inherent limitations and trade-offs. A real-world case study from the healthcare sector highlights the critical consequences of deploying non-transparent AI models in clinical decision-making. The article also discusses emerging regulatory frameworks and underscores the need for interdisciplinary collaboration to address the evolving ethical landscape. The review concludes with recommendations for aligning technical innovation with ethical imperatives through responsible design and governance.Chemical_Safety | Chemical Safety Management | Gaurav Singh Rajput



Chemical_Safety | Chemical Safety Management | Gaurav Singh RajputGaurav Singh Rajput
╠²
Chemical_Safety | Chemical Safety Management | Gaurav Singh Rajput22PCOAM16_ML_Unit 1 notes & Question Bank with answers.pdf



22PCOAM16_ML_Unit 1 notes & Question Bank with answers.pdfGuru Nanak Technical Institutions
╠²
22 PCOAM16 _ML_ Unit 2 Full unit notes.pdfYSPH VMOC Special Report - Measles Outbreak Southwest US 4-8-2025 FINAL ver4...



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-8-2025 FINAL ver4...Yale School of Public Health - The Virtual Medical Operations Center (VMOC)
╠²
A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. 58 individuals have required hospitalization, and 3 deaths, 2 children in Texas and 1 adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003. The YSPH The Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources ŌĆō including status reports, maps, news articles, and web contentŌĆō into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The ŌĆ£unlocked" format enables other responders to share, copy, and adapt it seamlessly.
The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
Reinventando el CD_ Unificando Aplicaciones e Infraestructura con Crossplane-...



Reinventando el CD_ Unificando Aplicaciones e Infraestructura con Crossplane-...Alberto Lorenzo
╠²
En esta charla, exploraremos c├│mo Crossplane puede transformar la forma en que gestionamos despliegues, yendo m├Īs all├Ī de un simple IaC para convertirse en una potente herramienta de Continuous Deployment (CD).
Ō£ģ Aprenderemos que es Crossplane
Ō£ģ Como usar Crossplane como IaC pero sobretodo Deployment as Code de manera eficiente
Ō£ģ Unificar la gesti├│n de aplicaciones e infraestructura de forma nativa en KubernetesKamal 2, new features and practical examples



Kamal 2, new features and practical examplesIgor Aleksandrov
╠²
║▌║▌▀Żs about Kamal 2 features and some practical examples.
Showed live on the Tropical on Rails 2025, S├Żo Paulo, Brazil, April 4th, 2025.Artificial Neural Network to Identify Verical Fractured Wells Flow Period (Lo...



Artificial Neural Network to Identify Verical Fractured Wells Flow Period (Lo...Long Vo
╠²
Utilizing a filtering method of Neural networks to reduce non-uniqueness and accurately identify Hydraulicly Fractured Flow Regime.PCB Design - Top Factors Related to Data Routing and Layout



PCB Design - Top Factors Related to Data Routing and LayoutEpec Engineered Technologies
╠²
When it comes to PCB design and layout, the decisions made early in your project can significantly impact not only the functionality of your circuit board but also its manufacturability, cost, and lead time. Understanding these critical considerations helps ensure a seamless transition from design to production while avoiding costly errors or delays.
Key factors to address include material selection, maximum board thickness, layer count, and whether to incorporate advanced features like blind and buried vias.
Additionally, considerations around copper weights, trace widths and spacing, balanced copper distribution, and overall design complexity can heavily influence both manufacturability and reliability.
A crucial question is: When should you involve your PCB provider in the design process?
Engaging early can help identify potential roadblocks, ensure design-for-manufacturing (DFM) compatibility, and optimize your layout for efficient production.
In this webinar, we take a deep dive into PCB designs as they relate to manufacturing.
Whether youŌĆÖre developing a simple two-layer board or a complex multilayer design, this session will provide actionable insights to streamline your process and achieve the best results for your project.
For more information on our PCB solutions, visit https://www.epectec.com/pcb.Airport Components Part2 ppt.pptx-Apron,Hangers,Terminal building



Airport Components Part2 ppt.pptx-Apron,Hangers,Terminal buildingPriyanka Dange
╠²
Apron,Hangers,Terminal buildingMODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx![MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx](https://cdn.slidesharecdn.com/ss_thumbnails/module01-cloudcomputing-250409082345-d719f5bc-thumbnail.jpg?width=560&fit=bounds)
![MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx](https://cdn.slidesharecdn.com/ss_thumbnails/module01-cloudcomputing-250409082345-d719f5bc-thumbnail.jpg?width=560&fit=bounds)
![MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx](https://cdn.slidesharecdn.com/ss_thumbnails/module01-cloudcomputing-250409082345-d719f5bc-thumbnail.jpg?width=560&fit=bounds)
![MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptx](https://cdn.slidesharecdn.com/ss_thumbnails/module01-cloudcomputing-250409082345-d719f5bc-thumbnail.jpg?width=560&fit=bounds)
MODULE 01 - CLOUD COMPUTING [BIS 613D] .pptxAlvas Institute of Engineering and technology, Moodabidri
╠²
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-8-2025 FINAL ver4...



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-8-2025 FINAL ver4...Yale School of Public Health - The Virtual Medical Operations Center (VMOC)
╠²
Distributed file systems dfs
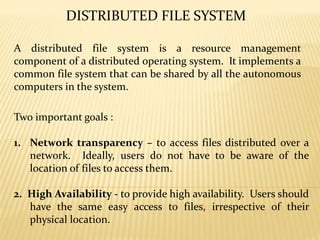
- 2. A distributed file system is a resource management component of a distributed operating system. It implements a common file system that can be shared by all the autonomous computers in the system. DISTRIBUTED FILE SYSTEM Two important goals : 1. Network transparency ŌĆō to access files distributed over a network. Ideally, users do not have to be aware of the location of files to access them. 2. High Availability - to provide high availability. Users should have the same easy access to files, irrespective of their physical location.
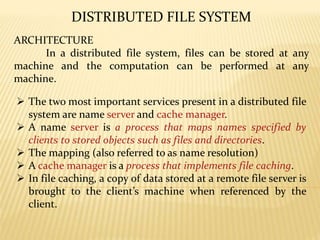
- 3. ARCHITECTURE In a distributed file system, files can be stored at any machine and the computation can be performed at any machine. ’āś The two most important services present in a distributed file system are name server and cache manager. ’āś A name server is a process that maps names specified by clients to stored objects such as files and directories. ’āś The mapping (also referred to as name resolution) ’āś A cache manager is a process that implements file caching. ’āś In file caching, a copy of data stored at a remote file server is brought to the clientŌĆÖs machine when referenced by the client. DISTRIBUTED FILE SYSTEM
- 4. ’āś Cache managers can be present at both clients and file servers. ’āś Cache managers at the servers cache files in the main memory to reduce delays due to disk latency. ’āś If multiple clients are allowed to cache a file and modify it, the copies can become inconsistent. ’āś To avoid this inconsistency problem, cache managers at both servers and clients coordinate to perform data storage and retrieval operations.
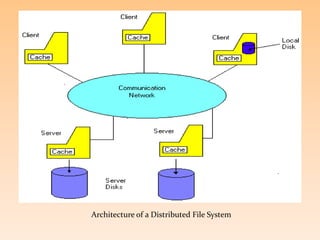
- 5. Architecture of a Distributed File System
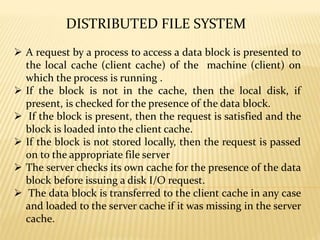
- 6. DISTRIBUTED FILE SYSTEM ’āś A request by a process to access a data block is presented to the local cache (client cache) of the machine (client) on which the process is running . ’āś If the block is not in the cache, then the local disk, if present, is checked for the presence of the data block. ’āś If the block is present, then the request is satisfied and the block is loaded into the client cache. ’āś If the block is not stored locally, then the request is passed on to the appropriate file server ’āś The server checks its own cache for the presence of the data block before issuing a disk I/O request. ’āś The data block is transferred to the client cache in any case and loaded to the server cache if it was missing in the server cache.
- 7. MECHANISMS FOR BUILDING DISTRIBUTED FILE SYSTEM Mounting A mount mechanism allows binding together of different filename spaces to form a single hierarchically structured name space. Two approaches to maintain the mount information: ’āś Mount information can be maintained at clients, in which case each client has to individually mount every required file system. This approach is employed in the Sun network file system. Since each client can mount a file system at any node in the name space tree, every client need not necessarily see an identical filename space.
- 8. ’āś Mount information can be maintained at servers, in which case it is possible that every client sees an identical filename space. If files are moved to a different server, then mount information need only be updated at the servers. In the first approach, every client needs to update its mount table.
- 9. ’āś Caching is commonly employed in distributed files systems to reduce delays in the accessing of data. ’āś In file caching, a copy of data stored at a remote file server is brought to the client when referenced by the client. ’āś The temporal locality of reference refers to the fact that a file recently accessed is likely to be accessed again in the near future. ’āś Data can either be cached in the main memory (server cache) at the servers to reduce disk access latency. ’āś Caching improves files system performance by reducing the delay in accessing data. CACHING
- 10. ’āś An alternative approach is to treat cached data as hints. ’āś In this case, cached data are not expected to be completely accurate. ’āś However, valid cache entries improve performance substantially without incurring the cost of maintaining cost consistency. ’āś The class of applications that can utilize hints are those which can recover after discovering that the cached data are invalid. HINTS
- 11. ’āś Transferring data in bulk reduces the protocol processing overhead at both servers and clients. ’āś In bulk data transfer, multiple consecutive data blocks are transferred from servers to clients instead of just the block referenced by clients. ’āś While file caching amortizes the high cost of accessing remote servers over several local references to the same information ’āś Bulk transfer amortizes the protocol processing overhead and disk seek time over many consecutive blocks of a file. ’āś Bulk transfers reduce file access overhead through obtaining a multiple number of blocks with a single seek; by formatting and transmitting a multiple number of large packets in a single context switch; and by reducing the number of acknowledgements that need to be sent. BULK DATA TRANSFER
- 12. ’āś Encryption is used for enforcing security in distributed systems. ’āś The work of Needham and Schroeder is the basis for most of the current security mechanisms in distributed systems. ’āś In their scheme, two entities wishing to communicate with each other establish a key for conversation with the help of an authentication server. ’āś It is important to note that the conversation key is determined by the authentication server, but is never spent in plain (unencrypted) text to either of the entities. ENCRYPTION







