[DockerCon•œ•§•È•§•»] OpenPubKey§À§Ë§Î•§•·©`•∏§Œ √˚§»ó ‘^.pdf
- 1. OpenPubKey §À§Ë§Î•§•·©`•∏§Œ √˚§»ó ‘^ NTT •Ω•’•»•¶•ß•¢•§•Œ•Ÿ©`•∑•Á•Û•ª•Û•ø Ìö? Á¯? DockerCon 2023 •œ•§•È•§•» (2023/11/2)
- 2. ? Moby (Docker Engine§Œupstream)°¢BuildKit°¢containerd°¢runc § §…§Œ OSS§Œ•≥•þ•√•ø ? Ω҃ͧŒDockerCon§«§œ °∞Reproducible builds with BuildKit for software supply chain security°± §ÀÈv§∑§∆µ«âØ ®C https://medium.com/nttlabs/dockercon-2023-reproducible-builds-with-buildkit- for-software-supply-chain-security-0e5aedd1aaa7 ? ΩÒ?§œ??§Œ»°§ÍΩM§þ§À§ƒ§§§∆§«§œ§ §Ø°¢ Docker…Á?BastionZero …Á§À §Ë§Î OpenPubKey §ÿ§Œ»°§ÍΩM§þ§À§ƒ§§§∆ΩBΩÈ ? Reproducible builds §À§‚ OpenPubKey §ÚèÍ?§∑§∆§§§≠§ø§§§»Àº§√§∆§§§Î 2 ??ΩBΩÈ
- 3. ? 2023/10/4: Demystify Secure Supply Chain Metadata ®C Christian Dupuis, Sr Principal Engineer, Docker ? 2023/10/5: Building the Software Supply Chain on Docker Official Images ®C Ethan Heilman, CTO & Co-Founder, BastionZero James Carnegie, Computer Programmer, Docker ? https://www.dockercon.com/ §´§È§Þ§¿“ï¬óø…ƒÐ 3 DockerCon §«§Œ OpenPubKey ÈvþB•ª•√•∑•Á•Û
- 5. ? OpenID Connect (OIDC) §ÚèÍ?§∑°¢π´È_ÊIª˘±P§»§∑§∆ π§®§Î§Ë§¶§À§∑§ø§‚§Œ °∞In essence, OpenPubkey is a protocol for getting OpenID Providers (OPs) to bind identities to public keys.°± ( https://github.com/openpubkey/openpubkey ) ? ¿˝§®§–°¢GitHub Actions …œ§«Docker•§•·©`•∏§Ú•”•Î•…§π§ÎÎH§À°¢GitHub•Í•ð•∏•» •Í§Œorganization ID§Ú∫¨§ý √˚§Ú∏∂º”§«§≠§Î ? GitHub Actions §Œ Secrets §À√ÿ√ÐÊI§Ú•¢•√•◊•Ì©`•…§∑§ø§Í§∑§ §Ø§∆§Ë§§ ? GitHub Actions “‘Õ‚§Œ OpenID •◊•Ì•–•§•¿ §ÿ§Œåùèͧ‚»ð“◊°£ •◊•Ì•–•§•¿Ç»§«§ŒåùèÍ◊˜òI§œ(‘≠Ñtµƒ§À)≤ª“™°£ ? Sigstore §Œ Cosign (keyless) §ÀÀ∆§∆§§§Î§¨°¢§Ë§Í•∑•Û•◊•Î§ òã≥… 5 OpenPubKey
- 6. ? GitHub Actions§ŒYAML: https://github.com/openpubkey/demo ? BuildKit §ÿ§Œ•—•√•¡ (Œ¥•Þ©`•∏): https://github.com/openpubkey/buildkit/tree/opk-signing ? docker verify •≥•Þ•Û•…: https://github.com/openpubkey/verify-docker-cli-plugin 6 DockerCon§«§ŒOpenPubKey§Œ•«•‚
- 7. 7 GitHub Actions §Œ YAML - name: Setup Docker buildx uses: docker/setup-buildx-action@v3.0.0 with: driver-opts: | image=openpubkey/buildkit:opk-signing env.ACTIONS_ID_TOKEN_REQUEST_URL=${{ env.ACTIONS_ID_TOKEN_REQUEST_URL }} env.ACTIONS_ID_TOKEN_REQUEST_TOKEN=${{ env.ACTIONS_ID_TOKEN_REQUEST_TOKEN }} - name: Build and push Docker image on push id: build-and-push uses: docker/build-push-action@v4.0.0 with: context: . push: true °≠ sbom: true provenance: true °≠ https://github.com/openpubkey/demo/blob/6b29027/.github/workflows/docker-build.yaml
- 8. 8 GitHub Actions §Œ YAML - name: Setup Docker buildx uses: docker/setup-buildx-action@v3.0.0 with: driver-opts: | image=openpubkey/buildkit:opk-signing env.ACTIONS_ID_TOKEN_REQUEST_URL=${{ env.ACTIONS_ID_TOKEN_REQUEST_URL }} env.ACTIONS_ID_TOKEN_REQUEST_TOKEN=${{ env.ACTIONS_ID_TOKEN_REQUEST_TOKEN }} - name: Build and push Docker image on push id: build-and-push uses: docker/build-push-action@v4.0.0 with: context: . push: true °≠ sbom: true provenance: true °≠ https://github.com/openpubkey/demo/blob/6b29027/.github/workflows/docker-build.yaml GitHub §À§Ë§Í?Ñ”µƒ§À‘O∂®§µ§Ï§Î OIDCÈvþB§Œ≠hæ≥≠˝§Ú BuildKit •«©`•‚•Û §ÀŪ≤•§µ§ª§Î OpenPubKey§Àåùèͧ∑§ø fork §Ú÷∏∂®§π§Î https://github.com/openpubkey/buildkit SBOM§™§Ë§”SLSA Provenance (•”•Î•…«ÈàÛ) §Ú •§•·©`•∏§À∏∂º”§π§Î°£ Å„§ª§∆°¢SBOM§‰SLSA Provenance §Àåù§π§Î √˚ (i.e., •§•·©`•∏§Àåù§π§Î √˚) §‚∏∂º”§π§Î°£
- 9. ? Docker CLI •◊•È•∞•§•Û§»§∑§∆÷π© https://github.com/openpubkey/verify-docker-cli-plugin ? Docker Hub …œ§Œ•§•·©`•∏ °∞openpubkey/demo@sha256°≠°± §¨°¢GitHub organization °∞openpubkey°± §Œ GitHub Actions §«•”•Î•…§µ§Ï§ø§≥§»§Ú¥_’J §«§≠§ø ? §ø§¿§∑°¢GitHub Actions §Œ•≠©`•ª•√•» (https://token.actions.githubusercontent.com/.well-known/jwks) §Ú–≈Óm§« §≠§Î«∞÷ 9 docker verify •≥•Þ•Û•… $ gh api /orgs/openpubkey | jq .id 145685596 $ docker verify openpubkey/demo@sha256:6acf54fca0e7f9e9ef3d23c9b9ee306ce3c56b8315aa756643e4df25032bcdbe --repo-owner-id 145685596 °≠ Verified all required attestations are present
- 10. 10 docker verify •≥•Þ•Û•… (≥ˆ?»´ÃÂ) $ docker verify openpubkey/demo@sha256:6acf54fca0e7f9e9ef3d23c9b9ee306ce3c56b8315aa756643e4df25032bcdbe --repo-owner-id 145685596 Verifying 2 attestations for pkg:docker/openpubkey/demo?digest=sha256:6acf54fca0e7f9e9ef3d23c9b9ee306ce3c56b8315aa756643e4df25032bcdbe&platform =linux/amd64 Verifying https://spdx.dev/Document attestation ? Verified attestation refers to digest sha256:6fbb78f2482a527575558d85147aee5f5f9f5288133bb0af316f91ed525a7246 ? Verified OIDC token was signed by https://token.actions.githubusercontent.com ? Verified attestation digest was signed on a Github Actions run: https://github.com/openpubkey/demo/actions/runs/6628798402 ? Verified repository owner 145685596 (openpubkey) Verifying https://slsa.dev/provenance/v0.2 attestation ? Verified attestation refers to digest sha256:6fbb78f2482a527575558d85147aee5f5f9f5288133bb0af316f91ed525a7246 ? Verified OIDC token was signed by https://token.actions.githubusercontent.com ? Verified attestation digest was signed on a Github Actions run: https://github.com/openpubkey/demo/actions/runs/6628798402 ? Verified repository owner 145685596 (openpubkey) ? Verified signed git sha provenance 6b29027d7ddae1c2dcdcfb88ab402473af5d20c8 ? Verified signed git repo provenance openpubkey/demo Verified all required attestations are present
- 11. 11 •’•Ì©` (1/2) BuildKit (OpenPubKeyåùèÍ∞Ê) GitHub Actions $ACTIONS_ID_TOKEN_REQUEST_TOKEN $ACTIONS_ID_TOKEN_REQUEST_URL HTTP GET $ACTIONS_ID_TOKEN_REQUEST_URL &audience=$AUDIENCE °∞Authorization: bearer $ACTIONS_ID_TOKEN_REQUEST_TOKEN°± ? ID Token §Ú∞k?§π§Î§ø§·§Œ Bearer Token §Ú∞k? ? •§•·©`•∏§Ú•”•Î•…§∑°¢ provenance§Ú?≥… ? ?ªÿœÞ§Í§ŒÊI•⁄•¢§Ú?≥… ? Client-Instance Claim (CIC) §Ú ?≥… {°Ærz°Ø: random(), °Æupk°Ø: publicKey, °Æalg°Ø: °ÆEC256°Ø, °Æatt°Ø: provenenceHash} ? CIC §Œ•œ•√•∑•Â§Ú °∞audience°± §»§∑§∆ID Token§Œ∞k?§Ú“™«Û °˘CIC §Œ•œ•√•∑•Â§œ°¢GitHub Actions § §…§Œ workload identity §«§œ audience §À∫¨§·§Î§¨°¢user identity §«§œ nonce §À∫¨§·§Î°£ audience (GHA§Œ•«•’•©•Î•»§«§œ •Í•ð•∏•»•Í §ŒURL) §À§œ»Œ“‚§Œ?◊÷¡–§Ú§§§Ï§∆§Ë§§§Œ§« OIDC§ŒAPI§Úâ‰∏¸§ª§∫§ÀCIC§Œ•œ•√•∑•Â§ÚÀէΠ§≥§»§¨§«§≠§Î
- 12. 12 •’•Ì©` (2/2) BuildKit (OpenPubKeyåùèÍ∞Ê) GitHub Actions ID Token: °∞SUBSTR0.SUBSTR1.SUBSTR2°± ? SUBSTR0: •ÿ•√•¿ §Œ base64 ? SUBSTR1: •⁄•§•Ì©`•…§Œ base64 (°∞aud°± § §…§Ú∫¨§ý) ? SUBSTR2: °±SUBST0.SUBST1°± §Àåù§π§Î √˚ ? Ч±»°§√§ø Bearer Token §¨ ∫œ§√§∆§§§Ï§–°¢ID Token §Ú∞k ?§π§Î ? ID Token§Œ÷˜§ •⁄•§•Ì©`•…: ? °∞aud°± (audience) ? °∞repository_owner_id°± (GitHub§Œorg§ŒID) ? °∞run_id°± (GHA§Œjob§Œ åg?ID) ? ID Token§œ°¢GHA??§¨≥÷§√ §∆§§§ÎÊI§« √˚§µ§Ï§Î ? ?≥÷§¡§ŒCIC§»°¢GHA§´§È Ð §±»°§√§øID Token§»§ÚΩM§þ∫œ §Ô§ª°¢ √˚§∑°¢ PK Token §Ú òã≥…§π§Î°£§≥§Ï§Ú•§•·©`•∏§À ∏∂º”§π§Î°£ ? Guillou-Quisquater (GQ) √˚ §À§Ë§Í°¢‘™§ŒID Token§ŒÇ駜 ÎL±Œ§µ§Ï§Î (•⁄•§•Ì©`•…§Œ ≤ø∑÷§œπ´È_§µ§Ï§Î) («∞í˜) CIC: Client-Instance Claim: {°Ærz°Ø: random(), °Æupk°Ø: publicKey, °Æalg°Ø: °ÆEC256, °Æatt°Ø: provenanceHash} audience: §≥§≥§«§œ CIC§Œ•œ•√•∑•Â ID Token §¨ÊI•⁄•¢§Àº~§≈§Ø °˘GQ √˚§œworkload identity§«§œ±ÿÌö°¢user identity §«§œ»Œ“‚ GHA§Œàˆ∫œ§œ•⁄•§•Ì©`•…§¨π´È_§µ§Ï§∆ÜñÓ}§ §§§¨°¢ À˚§ŒOpenID•◊•Ì•–•§•¿§«§œó ”맨±ÿ“™§Ω§¶
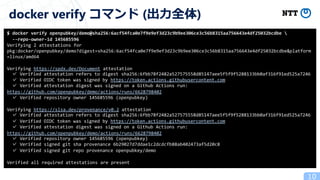
- 16. 16 { "payloadType":"application/vnd.in-toto+json", "payload": °≠, "signatures":[{"keyid":"OPK","sig": °≠}] } { "payload": °≠, "signatures": [ {"protected": °≠, "header": {"sig_type": "cic"}, "signature": °≠}, {"protected": °≠, "header": {"sig_type": "oidc_gq"}, "signature": °≠} ] } .signatures[0].sig { "jti": "66e345cc-0806-42a0-a346-7b98dc8ab2c0", "sub": "repo:openpubkey/demo:ref:refs/heads/main", "aud": "5km4t6i4IPk-tnv4qlmCcryfY0O-4PCNWOmFCJZJrzI", "ref": "refs/heads/main", "sha": "6b29027d7ddae1c2dcdcfb88ab402473af5d20c8", "repository": "openpubkey/demo", "repository_owner": "openpubkey", "repository_owner_id": "145685596", "run_id": "6628798402", "repository_id": "698282570", "iss": https://token.actions.githubusercontent.com °≠, } .payload { "alg": "ES256", "att": °≠ "rz": °≠, "upk": {"alg": "ES256", "crv": "P-256", "kty": "EC", "x": °≠, "y": °≠ } } { "typ": "JWT", "alg": "RS256", "x5t": "AB3c0BSoSOiCRXez5POu2zvPX_0", "kid": "001DDCD014A848E8824577B3E4F3AEDB3BCF5FFD" } .signatures[0].protected .signatures[1].protected application/vnd.in-toto.provenance+dsse (SLSA Provenance) .payload
- 17. ? OpenID Connect (OIDC) §ÚèÍ?§∑°¢π´È_ÊIª˘±P§»§∑§∆ π§®§Î§Ë§¶§À§∑§ø§‚§Œ °∞In essence, OpenPubkey is a protocol for getting OpenID Providers (OPs) to bind identities to public keys.°± ( https://github.com/openpubkey/openpubkey ) ? ¿˝§®§–°¢GitHub Actions …œ§«Docker•§•·©`•∏§Ú•”•Î•…§π§ÎÎH§À°¢GitHub•Í•ð•∏•»•Í§Œ organization ID§Ú∫¨§ý √˚§Ú∏∂º”§«§≠§Î ? GitHub Actions §Œ Secrets §À√ÿ√ÐÊI§Ú•¢•√•◊•Ì©`•…§∑§ø§Í§∑§ §Ø§∆§Ë§§ ? GitHub Actions “‘Õ‚§Œ OpenID •◊•Ì•–•§•¿ §ÿ§Œåùèͧ‚»ð“◊°£ •◊•Ì•–•§•¿Ç»§«§ŒåùèÍ◊˜òI§œ(‘≠Ñtµƒ§À)≤ª“™°£ ? Sigstore §Œ Cosign (keyless) §ÀÀ∆§∆§§§Î§¨°¢§Ë§Í•∑•Û•◊•Î§ òã≥… 17 §Þ§»§· (‘Ÿí˜) •π•È•§•…: https://github.com/AkihiroSuda (°∞Presentation slides°± °˙ °∞2023°± °˙ °∞20231102 °≠°±)














![16
{
"payloadType":"application/vnd.in-toto+json",
"payload": °≠,
"signatures":[{"keyid":"OPK","sig": °≠}]
}
{
"payload": °≠,
"signatures": [
{"protected": °≠, "header": {"sig_type":
"cic"}, "signature": °≠},
{"protected": °≠, "header": {"sig_type":
"oidc_gq"}, "signature": °≠}
]
}
.signatures[0].sig
{
"jti": "66e345cc-0806-42a0-a346-7b98dc8ab2c0",
"sub": "repo:openpubkey/demo:ref:refs/heads/main",
"aud": "5km4t6i4IPk-tnv4qlmCcryfY0O-4PCNWOmFCJZJrzI",
"ref": "refs/heads/main",
"sha": "6b29027d7ddae1c2dcdcfb88ab402473af5d20c8",
"repository": "openpubkey/demo",
"repository_owner": "openpubkey",
"repository_owner_id": "145685596",
"run_id": "6628798402",
"repository_id": "698282570",
"iss": https://token.actions.githubusercontent.com
°≠,
}
.payload
{
"alg": "ES256",
"att": °≠
"rz": °≠,
"upk": {"alg": "ES256", "crv": "P-256",
"kty": "EC", "x": °≠, "y": °≠ }
}
{
"typ": "JWT",
"alg": "RS256",
"x5t": "AB3c0BSoSOiCRXez5POu2zvPX_0",
"kid": "001DDCD014A848E8824577B3E4F3AEDB3BCF5FFD"
}
.signatures[0].protected .signatures[1].protected
application/vnd.in-toto.provenance+dsse
(SLSA Provenance)
.payload](https://image.slidesharecdn.com/20231102dockerconhighlightjapaneseopenpubkey-231102173641-c7ae94d1/85/DockerCon-OpenPubKey-pdf-16-320.jpg)





























![20241115 [KubeCon NA Pavilion] Lima.pdf_](https://cdn.slidesharecdn.com/ss_thumbnails/20241115kubeconnapavilionlima-241126155415-98be49e8-thumbnail.jpg?width=560&fit=bounds)
![20241113 [KubeCon NA Pavilion] containerd.pdf](https://cdn.slidesharecdn.com/ss_thumbnails/20241113kubeconnapavilioncontainerd-241126154829-7a8fdf60-thumbnail.jpg?width=560&fit=bounds)


![20240415 [Container Plumbing Days] Usernetes Gen2 - Kubernetes in Rootless Do...](https://cdn.slidesharecdn.com/ss_thumbnails/20240415containerplumbingdaysusernetesgen2-kubernetesinrootlessdockerwithmultiplenodes-240415184952-ea0dfb7a-thumbnail.jpg?width=560&fit=bounds)
![20240321 [KubeCon EU Pavilion] Lima.pdf_](https://cdn.slidesharecdn.com/ss_thumbnails/20240321kubeconeupavilionlima-240408065915-d80bbad0-thumbnail.jpg?width=560&fit=bounds)
![20240320 [KubeCon EU Pavilion] containerd.pdf](https://cdn.slidesharecdn.com/ss_thumbnails/20240320kubeconeupavilioncontainerd-240408065843-2d029142-thumbnail.jpg?width=560&fit=bounds)
![20240201 [HPC Containers] Rootless Containers.pdf](https://cdn.slidesharecdn.com/ss_thumbnails/20240201hpccontainersrootlesscontainers-240408065736-d40a3c26-thumbnail.jpg?width=560&fit=bounds)
![[Podman Special Event] Kubernetes in Rootless Podman](https://cdn.slidesharecdn.com/ss_thumbnails/20231116podmanspecialeventkubernetesinrootlesspodman-231117201823-4feac1e3-thumbnail.jpg?width=560&fit=bounds)
![[KubeConNA2023] Lima pavilion](https://cdn.slidesharecdn.com/ss_thumbnails/20231107kubeconnapavilionlima-231117201753-89cc5ec6-thumbnail.jpg?width=560&fit=bounds)
![[KubeConNA2023] containerd pavilion](https://cdn.slidesharecdn.com/ss_thumbnails/20231107kubeconnapavilioncontainerd-231117201655-55ef4553-thumbnail.jpg?width=560&fit=bounds)
![[CNCF TAG-Runtime] Usernetes Gen2](https://cdn.slidesharecdn.com/ss_thumbnails/20231027cncftag-runtimeusernetesgen2-231102173536-1d53a112-thumbnail.jpg?width=560&fit=bounds)
![[DockerCon 2023] Reproducible builds with BuildKit for software supply chain ...](https://cdn.slidesharecdn.com/ss_thumbnails/20231005dockerconreproduciblebuildswithbuildkitforsoftwaresupplychainsecurity-231008180210-7ccc319e-thumbnail.jpg?width=560&fit=bounds)

![[KubeConEU2023] Lima pavilion](https://cdn.slidesharecdn.com/ss_thumbnails/kceu2023-pavilion-lima-230427150225-16054d2b-thumbnail.jpg?width=560&fit=bounds)
![[KubeConEU2023] containerd pavilion](https://cdn.slidesharecdn.com/ss_thumbnails/kceu2023-pavilion-containerd-230427150109-5e56d29a-thumbnail.jpg?width=560&fit=bounds)
![[Container Plumbing Days 2023] Why was nerdctl made?](https://cdn.slidesharecdn.com/ss_thumbnails/containerplumbing2023whywasnerdctlmade-230323115340-794fba85-thumbnail.jpg?width=560&fit=bounds)
![[FOSDEM2023] Bit-for-bit reproducible builds with Dockerfile](https://cdn.slidesharecdn.com/ss_thumbnails/fosdem2023bitforbitreproduciblebuildswithdockerfile-230210133322-31a74c01-thumbnail.jpg?width=560&fit=bounds)
![[CNCF TAG-Runtime 2022-10-06] Lima](https://cdn.slidesharecdn.com/ss_thumbnails/cncftag-runtime2022-10-06lima-221007111035-3bb96dd9-thumbnail.jpg?width=560&fit=bounds)
![[KubeCon EU 2022] Running containerd and k3s on macOS](https://cdn.slidesharecdn.com/ss_thumbnails/lima-220519142933-3d747f68-thumbnail.jpg?width=560&fit=bounds)





