Dr erdas sap ilm_basics
Download as PPTX, PDF0 likes69 views
How to implement GDPR using SAP ILM Customization of ILM Objects for ERP, HCM BW to identify personal data, how to create a PoC or deletion, block or residence with legal cases concept
1 of 23
Download to read offline
















Recommended
Breaking, forensicating and anti-forensicating SAP Portal and J2EE Engine



Breaking, forensicating and anti-forensicating SAP Portal and J2EE EngineERPScan
?
SAP is the most popular business application with more than one hundred eighty thousand installations all over the world. But people spend enormous amounts of money to install it and then forget about security. In ERP systems, all business processes are performed, all critical information is stored like finances, HR, clients. Not to care about the security of this data is not very sensible.
The presentation provides examples of simple and advanced attacks along with ways to avoid them.
OUTSYSTEMS AND SAP 2015



OUTSYSTEMS AND SAP 2015Mustafa Ku?u
?
The document discusses how organizations are struggling to customize SAP to meet new pressures from mobility, customer experience, and operational excellence. It is difficult to customize SAP due to its large and complex landscape. The OutSystems platform allows organizations to extend SAP applications without modifying core SAP, through rapid application development capabilities and tight integration with SAP that inherits security, governance, and other capabilities. Developers can discover and consume SAP APIs easily to build new applications on any device.An easy way into your sap systems v3.0



An easy way into your sap systems v3.0Cyber Security Alliance
?
Default accounts are commonly exploited to gain unauthorized access to SAP systems. The presentation identifies several new default accounts in SAP Solution Manager with the password "init1234" that can be used to retrieve passwords, execute operating system commands, and fully compromise associated SAP systems. It provides examples of how these accounts can be exploited and advises customers to use available tools to detect and remediate exposed default accounts.Practical SAP pentesting workshop (NullCon Goa)



Practical SAP pentesting workshop (NullCon Goa)ERPScan
?
All business processes are generally contained in ERP systems. Any information an attacker might want is stored in a company’s ERP. This information can include financial, customer or public relations, intellectual property, personally identifiable information and more. And SAP is the most popular business application vendor with more than 250000 customers worldwide.
The workshop conducted by Alexander Polyakov, CTO of ERPScan, at NullCon Goa Conference is a practical SAP pentesting guide.
Managing SAP Custom Code



Managing SAP Custom CodeTony de Thomasis
?
The document discusses how SAP Solution Manager can be used to manage custom code. It describes how Solution Manager provides transparency into an organization's custom code through tools that create a central repository. It also allows for control of custom code through reporting, governance, and testing tools. Solution Manager offers optimization of custom code through capabilities like clone finding and code inspection. It provides reporting and governance over custom code through business intelligence reports and dashboards.A crushing blow at the heart of SAP’s J2EE Engine. 



A crushing blow at the heart of SAP’s J2EE Engine. ERPScan
?
Automation of business processes like ERP, PLM, CRM, SRM based on ABAP.
There are the following integration, collaboration and management based on J2EE engine:
- SAP Portal
- SAP PI
- SAP XI
- SAP Mobile Infrastructure
- SAP Solution Manager.
Administrators, developers, pentesters, and researchers mostly focus on ABAP stack. Hackers know about it, so they will find easier ways to control your business.
The presentation describes SAP J2EE Platform Architecture and provides examples of internal and external attacks and ways of its prevention.Practical SAP pentesting (B-Sides San Paulo)



Practical SAP pentesting (B-Sides San Paulo)ERPScan
?
All business processes are generally contained in ERP systems. Any information an attacker might want is stored in a company’s ERP. This information can include financial, customer or public relations, intellectual property, personally identifiable information and more. And SAP is the most popular business application vendor with more than 250000 customers worldwide.
The workshop conducted by Alexander Polyakov, CTO of ERPScan, at B-Sides Conference 2014 (San Paulo) is a practical SAP pentesting guide.Injecting evil code in your SAP J2EE systems. Security of SAP Software Deploy...



Injecting evil code in your SAP J2EE systems. Security of SAP Software Deploy...ERPScan
?
SAP is the most popular business application with more than two hundred forty thousand installations all over the world. But people spend enormous amounts of money to install it and then forget about security. However, in ERP systems, all business processes are performed, all critical information is stored like finances, HR, clients. Not to care about the security of this data is not very sensible.
SAP NetWeaver Development Infrastructure is a complex item. It combines the characteristics and advantages of local development environments with a server-based development landscape. All this stuff centrally provides opportunities to support the software, implement new features, manage lifecycle of a product, etc. So, the main aim is to control deployment of components in the system landscape in a standardized manner.
The key component in DI scheme is Software Deployment Manager (SDM). It is directly related to the production systems, that is why it is so critical.
The presentation describes special features of SDM and provides several SDM attack scenarios along with the ways to prevent them.SAP SDM Hacking



SAP SDM HackingERPScan
?
SAP is the most popular business application with more than two hundred forty thousand installations all over the world. But people spend enormous amounts of money to install it and then forget about security. However, in ERP systems, all business processes are performed, all critical information is stored like finances, HR, clients. Not to care about the security of this data is not very sensible.
SAP NetWeaver Development Infrastructure is a complex item. It combines the characteristics and advantages of local development environments with a server-based development landscape. All this stuff centrally provides opportunities to support the software, implement new features, manage lifecycle of a product, etc. So, the main aim is to control deployment of components in the system landscape in a standardized manner.
The key component in DI scheme is Software Deployment Manager (SDM). It is directly related to the production systems, that is why it is so critical.
The presentation describes special features of SDM and provides several SDM attack scenarios along with the ways to prevent them.
Sitnl erp sec-2011



Sitnl erp sec-2011jvandevis
?
This presentation tries to raise awareness on SAP Security (Platform security). Some default settings that might need adjustment are shown.Caarcpm



CaarcpmSoubhagya447
?
This document provides information about archiving processes and functions for various objects in SAP's Plant Maintenance and Customer Service (PM/CS) module, including equipment, functional locations, serial number histories, measurement documents, and maintenance notifications. For each archiving object, the document outlines application-specific features, customizing options, dependencies, authorization requirements, and logs to view archived objects or monitor the archiving process. The goal of archiving is to optimize system performance by removing old, inactive master data from the database.SAP portal: breaking and forensicating 



SAP portal: breaking and forensicating ERPScan
?
The document discusses security issues related to SAP systems and portals. It notes that while SAP is widely used, security vulnerabilities are common due to lack of logging and exposure of services. The document emphasizes that SAP portals deserve attention as they provide a common entry point for attackers and link to other critical systems. Proper monitoring of portals and exposed services is needed to detect attacks and unauthorized access.Bn1033 demo sap basis



Bn1033 demo sap basisconline training
?
Visit Us: http://www.conlinetraining.com/
Facebook : https://www.facebook.com/conlinetraining/
Google+ : https://plus.google.com/u/0/collections?arp=1&cfem=111
Twitter : https://twitter.com/conlinetrainin9
Drop your Response :http://www.conlinetraining.com/educationwp/SAP AC020 - Investment Management



SAP AC020 - Investment ManagementVannak9
?
This document provides a summary of the Investment Management training course offered by SAP. It covers navigating the SAP system, the investment management lifecycle, creating master data, planning and budgeting investments, implementing measures, settling investments, and performing the fiscal year change process. The target users are project managers and team members responsible for investment planning and management.MySQL-Performance Schema- What's new in MySQL-5.7 DMRs



MySQL-Performance Schema- What's new in MySQL-5.7 DMRsMayank Prasad
?
I presented these slides in Oracle Open World, 2014. It lists down new features/enhancements done in MySQL-Performance Schema in MySQL 5.7 (DMRs).Implementing Process Controls and Risk Management with Novell Compliance Mana...



Implementing Process Controls and Risk Management with Novell Compliance Mana...Novell
?
The document discusses Novell's Compliance Management Platform and its extension for SAP environments. The platform provides integrated identity and security management through components like Identity Vault, Identity Manager, Sentinel, and Access Manager. The extension for SAP includes tools like a Role Mapping Administrator and enhanced SAP drivers. It aims to develop synergies between Identity Manager and SAP BusinessObjects Access Control for improved provisioning, access control, risk analysis, and monitoring capabilities. Three scenarios are presented showing how provisioning and access control can be integrated between the solutions.Implementing Process Controls and Risk Management with Novell Compliance Mana...



Implementing Process Controls and Risk Management with Novell Compliance Mana...Novell
?
The document discusses Novell's Compliance Management Platform and its extension for SAP environments. The platform provides integrated identity and security management through components like Identity Vault, Identity Manager, Sentinel, and Access Manager. The extension for SAP adds tools like a Role Mapping Administrator and new/enhanced SAP drivers. It aims to develop synergies between Identity Manager and SAP Access Control and extend existing integrations with SAP products. Scenarios show how the platform can be used for SAP user provisioning and access control. Risk management integration is also discussed.Basis week5



Basis week5nanda nanda
?
The document discusses performance analysis and tuning in SAP systems. It provides an overview of workload analysis techniques, including analyzing wait times, database times, and other components of transaction response times. It also describes various performance monitors in SAP systems for analyzing the basis and application layers, such as the workload monitor, transaction profile, work process overview, and operating system monitor. The goal is to help consultants identify and address performance bottlenecks.Architecture vulnerabilities in?SAP?platforms



Architecture vulnerabilities in?SAP?platformsERPScan
?
SAP security becomes a hot theme nowadays. Attacks on SAP can put a business at risk of Espionage, Sabotage and Fraud.
The presentation covers the following architecture and unusual issues:
Authentication Bypass
1. Verb tampering
2. Invoker servlet
Encryption
3. Storage – SAPGUI
4. Authentication – P4
5. Transfer – RFC, Diag
SSRF
6. Port Scan
7. Command execution
8. Security bypass
Also, the presentation gives advice for developers and describes future trends in SAP Security area.Managing SAP Custom Code



Managing SAP Custom CodeTony de Thomasis
?
The document discusses managing custom code in SAP systems. It covers the reasons to control custom code, providing transparency into how much custom code exists, controlling custom code through its lifecycle, and optimizing custom code quality. It describes tools in SAP Solution Manager and standalone systems for custom code management, including Custom Code Lifecycle Management, ABAP Test Cockpit, SAP Coverage Analyzer, and SAP Code Inspector.Resume



ResumePratham kapoor
?
Pratham Kapoor has over 3 years of experience as an SAP ABAP Technical Developer with Infosys Technologies Ltd, where he has worked on projects involving SAP SRM 7.01 customizations including workflow enhancements, Webdynpro component development, and ABAP programming. He has expertise in ABAP/4, SAPGUI, Windows operating systems, ABAP OO, BRF workflow, ALV reports, and data mapping. Pratham holds a B.Tech in Computer Science from Jaypee University of Engineering & Technology.All Requirements



All RequirementsShravan Thalla
?
The document contains a list of skills and corresponding designations for various roles. It includes roles in areas like Oracle IDM, TVM/WAS, CC&B, Oracle Apps DBA, Oracle Apps Functional, I-Procurement, Hyperion, SAP QM, and SAP SRM. For each role, it provides responsibilities, required skills, experience and qualifications.Storage Sizing for SAP



Storage Sizing for SAPCenk Ersoy
?
The document discusses sizing storage for SAP implementations. It describes different types of sizing including greenfield, brownfield, and hybrid. It also covers sizing tools from SAP like QuickSizer that estimate hardware requirements based on metrics like CPU time, memory usage, and disk space. The document emphasizes that sizing is an iterative process that requires validating assumptions with usage data and testing.Redefining SAP technology landscape



Redefining SAP technology landscapeBhavya Bhandary
?
Visually understand the redefined SAP technology landscape on:
how it improves decision making
automates business processes of a given enterprise
increases productivity with a digital core that supports all the mission-critical business processesCONFidence 2014: Dimitriy Chastuhin: All your sap p@$$w0яd z belong to us



CONFidence 2014: Dimitriy Chastuhin: All your sap p@$$w0яd z belong to usPROIDEA
?
Nowadays, everyone knows about the great importance of SAP systems and the critical data processed by them. Large companies install SAP Security Notes regularly so as not to repeat the mistake of Nvidia. One bug is not enough anymore to get access to all corporate SAP systems. Pentesters frequently find themselves in a situation where the OS of an SAP server has been compromised successfully, but they have not got an access to the ERP system. In addition, it is rather common to have an unprivileged account, which give them access to the encrypted password, but not to the whole system. Sometimes they even try to break into other systems with help of the passwords, which users usually use in the systems they’ve already broken, but they can’t, because they need them to be decrypted first. Where do we find the treasured password to access the financial transactions and revenues of NASDAQ monsters?
Where and how does SAP store user passwords? Are all passwords stored as hashes, or can attackers find passwords in plaintext?
This talk reviews the many places where SAP stores critical credentials, such as usernames and passwords, and, which is more interesting, the way it stores them. Methods of retrieving them will be described, and decryption utilities will be presented.
SAP GUI shortcuts, RFC connections, SAP Security Storage, logs, traces, Database links, SAP HANA Storage, you name it – all varieties of SAP modules will be discussed in this talk.z/OS small enhancements, episode 2018A



z/OS small enhancements, episode 2018AMarna Walle
?
Small older technical enhancements you might have missed in z/OS releases you have (or have migrated from). CoreToEdge Company Presentation



CoreToEdge Company PresentationCore To Edge
?
This document provides information about CoreToEdge, a technology services company. It details CoreToEdge's mission, vision, history, services, products, customers, and partners. CoreToEdge's services include SAP hosting, cloud services, training, and technology services. Their products include BasisCockpit for real-time SAP system monitoring and Verilista for predictive maintenance. The document shares CoreToEdge's numbers, locations, and social media accounts.Your Salesforce toolbelt – Practical recommendations to keep your Org healthy



Your Salesforce toolbelt – Practical recommendations to keep your Org healthyYeurDreamin'
?
The challenges involved in keeping a healthy, performant and scalable Org are many and come in different shapes and sizes. Clearly these increase with the complexity of the customisations performed on your Orgs, but even if you are sticking to the Out of the Box processes as much as possible, and keeping your APEX codebase to the minimum, it is still possible to find yourself in a situation in which issues show up in your productive Org.Dr erdas sap ilm_basics



Dr erdas sap ilm_basicsProf Dr Mehmed ERDAS
?
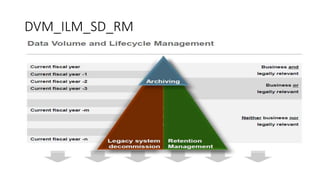
ILM archiving strategy involves using SAP tools like Launchpad, Archiving IQ, and DVM to archive and decommission data according to retention policies. Key transactions and reports are used to configure and monitor the ILM process which archives objects like customer, vendor, material, and HR data according to dependencies. Sample SAP notes provide guidance on configuring and validating ILM policies for customer/vendor destruction.Sap ilm hcm prof.dr.mehmet erdas



Sap ilm hcm prof.dr.mehmet erdasProf Dr Mehmed ERDAS
?
This document provides an overview of SAP Information Lifecycle Management (ILM), including its functionality, relevant business functions, main transactions, and setup steps. It discusses analyzing ILM objects, assigning objects to audit areas, creating ILM rules and policies, and archiving ILM stores. References for additional information on SAP ILM and related topics such as data archiving, retention management, and data privacy are also provided.More Related Content
Similar to Dr erdas sap ilm_basics (20)
SAP SDM Hacking



SAP SDM HackingERPScan
?
SAP is the most popular business application with more than two hundred forty thousand installations all over the world. But people spend enormous amounts of money to install it and then forget about security. However, in ERP systems, all business processes are performed, all critical information is stored like finances, HR, clients. Not to care about the security of this data is not very sensible.
SAP NetWeaver Development Infrastructure is a complex item. It combines the characteristics and advantages of local development environments with a server-based development landscape. All this stuff centrally provides opportunities to support the software, implement new features, manage lifecycle of a product, etc. So, the main aim is to control deployment of components in the system landscape in a standardized manner.
The key component in DI scheme is Software Deployment Manager (SDM). It is directly related to the production systems, that is why it is so critical.
The presentation describes special features of SDM and provides several SDM attack scenarios along with the ways to prevent them.
Sitnl erp sec-2011



Sitnl erp sec-2011jvandevis
?
This presentation tries to raise awareness on SAP Security (Platform security). Some default settings that might need adjustment are shown.Caarcpm



CaarcpmSoubhagya447
?
This document provides information about archiving processes and functions for various objects in SAP's Plant Maintenance and Customer Service (PM/CS) module, including equipment, functional locations, serial number histories, measurement documents, and maintenance notifications. For each archiving object, the document outlines application-specific features, customizing options, dependencies, authorization requirements, and logs to view archived objects or monitor the archiving process. The goal of archiving is to optimize system performance by removing old, inactive master data from the database.SAP portal: breaking and forensicating 



SAP portal: breaking and forensicating ERPScan
?
The document discusses security issues related to SAP systems and portals. It notes that while SAP is widely used, security vulnerabilities are common due to lack of logging and exposure of services. The document emphasizes that SAP portals deserve attention as they provide a common entry point for attackers and link to other critical systems. Proper monitoring of portals and exposed services is needed to detect attacks and unauthorized access.Bn1033 demo sap basis



Bn1033 demo sap basisconline training
?
Visit Us: http://www.conlinetraining.com/
Facebook : https://www.facebook.com/conlinetraining/
Google+ : https://plus.google.com/u/0/collections?arp=1&cfem=111
Twitter : https://twitter.com/conlinetrainin9
Drop your Response :http://www.conlinetraining.com/educationwp/SAP AC020 - Investment Management



SAP AC020 - Investment ManagementVannak9
?
This document provides a summary of the Investment Management training course offered by SAP. It covers navigating the SAP system, the investment management lifecycle, creating master data, planning and budgeting investments, implementing measures, settling investments, and performing the fiscal year change process. The target users are project managers and team members responsible for investment planning and management.MySQL-Performance Schema- What's new in MySQL-5.7 DMRs



MySQL-Performance Schema- What's new in MySQL-5.7 DMRsMayank Prasad
?
I presented these slides in Oracle Open World, 2014. It lists down new features/enhancements done in MySQL-Performance Schema in MySQL 5.7 (DMRs).Implementing Process Controls and Risk Management with Novell Compliance Mana...



Implementing Process Controls and Risk Management with Novell Compliance Mana...Novell
?
The document discusses Novell's Compliance Management Platform and its extension for SAP environments. The platform provides integrated identity and security management through components like Identity Vault, Identity Manager, Sentinel, and Access Manager. The extension for SAP includes tools like a Role Mapping Administrator and enhanced SAP drivers. It aims to develop synergies between Identity Manager and SAP BusinessObjects Access Control for improved provisioning, access control, risk analysis, and monitoring capabilities. Three scenarios are presented showing how provisioning and access control can be integrated between the solutions.Implementing Process Controls and Risk Management with Novell Compliance Mana...



Implementing Process Controls and Risk Management with Novell Compliance Mana...Novell
?
The document discusses Novell's Compliance Management Platform and its extension for SAP environments. The platform provides integrated identity and security management through components like Identity Vault, Identity Manager, Sentinel, and Access Manager. The extension for SAP adds tools like a Role Mapping Administrator and new/enhanced SAP drivers. It aims to develop synergies between Identity Manager and SAP Access Control and extend existing integrations with SAP products. Scenarios show how the platform can be used for SAP user provisioning and access control. Risk management integration is also discussed.Basis week5



Basis week5nanda nanda
?
The document discusses performance analysis and tuning in SAP systems. It provides an overview of workload analysis techniques, including analyzing wait times, database times, and other components of transaction response times. It also describes various performance monitors in SAP systems for analyzing the basis and application layers, such as the workload monitor, transaction profile, work process overview, and operating system monitor. The goal is to help consultants identify and address performance bottlenecks.Architecture vulnerabilities in?SAP?platforms



Architecture vulnerabilities in?SAP?platformsERPScan
?
SAP security becomes a hot theme nowadays. Attacks on SAP can put a business at risk of Espionage, Sabotage and Fraud.
The presentation covers the following architecture and unusual issues:
Authentication Bypass
1. Verb tampering
2. Invoker servlet
Encryption
3. Storage – SAPGUI
4. Authentication – P4
5. Transfer – RFC, Diag
SSRF
6. Port Scan
7. Command execution
8. Security bypass
Also, the presentation gives advice for developers and describes future trends in SAP Security area.Managing SAP Custom Code



Managing SAP Custom CodeTony de Thomasis
?
The document discusses managing custom code in SAP systems. It covers the reasons to control custom code, providing transparency into how much custom code exists, controlling custom code through its lifecycle, and optimizing custom code quality. It describes tools in SAP Solution Manager and standalone systems for custom code management, including Custom Code Lifecycle Management, ABAP Test Cockpit, SAP Coverage Analyzer, and SAP Code Inspector.Resume



ResumePratham kapoor
?
Pratham Kapoor has over 3 years of experience as an SAP ABAP Technical Developer with Infosys Technologies Ltd, where he has worked on projects involving SAP SRM 7.01 customizations including workflow enhancements, Webdynpro component development, and ABAP programming. He has expertise in ABAP/4, SAPGUI, Windows operating systems, ABAP OO, BRF workflow, ALV reports, and data mapping. Pratham holds a B.Tech in Computer Science from Jaypee University of Engineering & Technology.All Requirements



All RequirementsShravan Thalla
?
The document contains a list of skills and corresponding designations for various roles. It includes roles in areas like Oracle IDM, TVM/WAS, CC&B, Oracle Apps DBA, Oracle Apps Functional, I-Procurement, Hyperion, SAP QM, and SAP SRM. For each role, it provides responsibilities, required skills, experience and qualifications.Storage Sizing for SAP



Storage Sizing for SAPCenk Ersoy
?
The document discusses sizing storage for SAP implementations. It describes different types of sizing including greenfield, brownfield, and hybrid. It also covers sizing tools from SAP like QuickSizer that estimate hardware requirements based on metrics like CPU time, memory usage, and disk space. The document emphasizes that sizing is an iterative process that requires validating assumptions with usage data and testing.Redefining SAP technology landscape



Redefining SAP technology landscapeBhavya Bhandary
?
Visually understand the redefined SAP technology landscape on:
how it improves decision making
automates business processes of a given enterprise
increases productivity with a digital core that supports all the mission-critical business processesCONFidence 2014: Dimitriy Chastuhin: All your sap p@$$w0яd z belong to us



CONFidence 2014: Dimitriy Chastuhin: All your sap p@$$w0яd z belong to usPROIDEA
?
Nowadays, everyone knows about the great importance of SAP systems and the critical data processed by them. Large companies install SAP Security Notes regularly so as not to repeat the mistake of Nvidia. One bug is not enough anymore to get access to all corporate SAP systems. Pentesters frequently find themselves in a situation where the OS of an SAP server has been compromised successfully, but they have not got an access to the ERP system. In addition, it is rather common to have an unprivileged account, which give them access to the encrypted password, but not to the whole system. Sometimes they even try to break into other systems with help of the passwords, which users usually use in the systems they’ve already broken, but they can’t, because they need them to be decrypted first. Where do we find the treasured password to access the financial transactions and revenues of NASDAQ monsters?
Where and how does SAP store user passwords? Are all passwords stored as hashes, or can attackers find passwords in plaintext?
This talk reviews the many places where SAP stores critical credentials, such as usernames and passwords, and, which is more interesting, the way it stores them. Methods of retrieving them will be described, and decryption utilities will be presented.
SAP GUI shortcuts, RFC connections, SAP Security Storage, logs, traces, Database links, SAP HANA Storage, you name it – all varieties of SAP modules will be discussed in this talk.z/OS small enhancements, episode 2018A



z/OS small enhancements, episode 2018AMarna Walle
?
Small older technical enhancements you might have missed in z/OS releases you have (or have migrated from). CoreToEdge Company Presentation



CoreToEdge Company PresentationCore To Edge
?
This document provides information about CoreToEdge, a technology services company. It details CoreToEdge's mission, vision, history, services, products, customers, and partners. CoreToEdge's services include SAP hosting, cloud services, training, and technology services. Their products include BasisCockpit for real-time SAP system monitoring and Verilista for predictive maintenance. The document shares CoreToEdge's numbers, locations, and social media accounts.Your Salesforce toolbelt – Practical recommendations to keep your Org healthy



Your Salesforce toolbelt – Practical recommendations to keep your Org healthyYeurDreamin'
?
The challenges involved in keeping a healthy, performant and scalable Org are many and come in different shapes and sizes. Clearly these increase with the complexity of the customisations performed on your Orgs, but even if you are sticking to the Out of the Box processes as much as possible, and keeping your APEX codebase to the minimum, it is still possible to find yourself in a situation in which issues show up in your productive Org.More from Prof Dr Mehmed ERDAS (18)
Dr erdas sap ilm_basics



Dr erdas sap ilm_basicsProf Dr Mehmed ERDAS
?
ILM archiving strategy involves using SAP tools like Launchpad, Archiving IQ, and DVM to archive and decommission data according to retention policies. Key transactions and reports are used to configure and monitor the ILM process which archives objects like customer, vendor, material, and HR data according to dependencies. Sample SAP notes provide guidance on configuring and validating ILM policies for customer/vendor destruction.Sap ilm hcm prof.dr.mehmet erdas



Sap ilm hcm prof.dr.mehmet erdasProf Dr Mehmed ERDAS
?
This document provides an overview of SAP Information Lifecycle Management (ILM), including its functionality, relevant business functions, main transactions, and setup steps. It discusses analyzing ILM objects, assigning objects to audit areas, creating ILM rules and policies, and archiving ILM stores. References for additional information on SAP ILM and related topics such as data archiving, retention management, and data privacy are also provided.Prof.Dr.Dipl.Wirtsch:ing. Mehmet Erdas sap ilm_schulung



Prof.Dr.Dipl.Wirtsch:ing. Mehmet Erdas sap ilm_schulungProf Dr Mehmed ERDAS
?
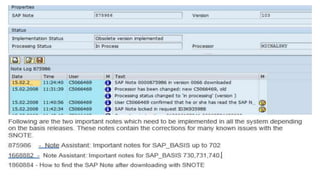
The document discusses important SAP notes related to information lifecycle management (ILM) and GDPR compliance. It lists several SAP notes that can help standardize and customize ILM objects. It also discusses how to assign application rule variants to ILM rules and applications. Finally, it provides details on legal case management in SAP, including how to enable legal hold to extend data retention on business objects involved in a legal case.

White Paper0_



White Paper0_Prof Dr Mehmed ERDAS
?
This white paper discusses new approaches to network planning given convergence of fixed and mobile networks and divergence of applications and services. It proposes optimizing network planning to maximize benefits for investors, suppliers and operators while minimizing risks. The paper outlines challenges like self-similar traffic, dynamic routing and topological constraints. It advocates dividing the network planning problem into smaller subproblems and using techniques like queueing theory, simulation and optimization algorithms to develop short, medium and long-term plans that meet technical, economic and business factors over time as networks and technologies evolve.Big data analytics for telecom operators final use cases 0712-2014_prof_m erdas



Big data analytics for telecom operators final use cases 0712-2014_prof_m erdasProf Dr Mehmed ERDAS
?
Big Data Analytics for TELCOs Customer Experience Management Permission Based Marketing for Location and Movement Data Data Modelling Business Use Cases Data Mining BSS OSS COTS OTT Churm Modeling Markov Processes HANA HADOOP INtegration Video Streaming Test casesBig data analytics for telecom operators final use cases 0712-2014_prof_m erdas



Big data analytics for telecom operators final use cases 0712-2014_prof_m erdasProf Dr Mehmed ERDAS
?
Big Data Analytics for TELCOs CEM Business Use Cases for Location and Movement permission Based Marketing Churn Analyticsproject proposal guidelines for bw on hana Dr Erdas



project proposal guidelines for bw on hana Dr ErdasProf Dr Mehmed ERDAS
?
The document outlines the phases and steps for migrating an existing SAP landscape including ECC 6, BW 7.3, and other components to SAP HANA. It involves scoping, blueprinting, implementation, testing, and go-live preparation over 5-6 months. Key steps include identifying data sources, reviewing reports, installing HANA, migrating and converting BW objects to in-memory structures, authorization changes, testing, and go-live support. Required resources include project managers, solution architects, and application consultants for each system.sap nw bw7.3 on sap hana ramp up project approach (2)



sap nw bw7.3 on sap hana ramp up project approach (2)Prof Dr Mehmed ERDAS
?
This document provides a summary of Eldorado's SAP HANA ramp up project. It outlines the project description and scope, including the tasks and responsibilities of the ramp up coach. It also includes the project plan with timelines and resource assignments for migrating Eldorado's existing SAP BW landscape to SAP HANA. The goals of the project are to enable Eldorado to become an early adopter of SAP BW on HANA in order to gain strategic advantages from new capabilities like real-time analytics and improved supply chain processes.White paper0 



White paper0 Prof Dr Mehmed ERDAS
?
This white paper discusses new approaches to telecommunications network planning given convergence of fixed and mobile networks and divergence of applications and services. It proposes optimizing network planning to maximize benefits for investors, suppliers and operators while minimizing risks. The paper provides an overview of factors to consider in network planning like traffic patterns, routing, and topology. These include technological, economic, financial, business, organizational and environmental factors. It also discusses approaches like dividing the problem into smaller subproblems and using algorithms like integer programming, graph theory and simulation to optimize network design and costs over time.01 Onsoz Ingilizce



01 Onsoz IngilizceProf Dr Mehmed ERDAS
?
This document discusses the challenges of localizing English terms related to SAP programming into Turkish for the first time. It explains how providing conceptual consistency and avoiding contradictions with existing definitions is difficult but important. It also notes that understanding ABAP code is still necessary even with new graphic tools, and introduces a book on ABAP by Yener Türkeli aimed at both beginners and experienced SAP and ABAP users. A recommendation for the book is provided by Prof. Dr. Mehmet Erda?.Bb Consulting Profil Me 2008 English 08072008 08 38 Am10 Jul 08



Bb Consulting Profil Me 2008 English 08072008 08 38 Am10 Jul 08Prof Dr Mehmed ERDAS
?
This document provides a competence profile for Prof. Dr. Dipl. Ing. Mehmet Erdas, an SAP BI 7.0 Senior Consultant and Trainer. It outlines his professional qualifications and over 25 years of IT experience, including fluency in German, English, and Turkish. It also details his hands-on project experience delivering SAP BI solutions, as well as the courses and certifications he has completed. His areas of expertise include SAP BI, data modeling, ETL, reporting, and performance optimization.White Paper0



White Paper0Prof Dr Mehmed ERDAS
?
This document provides a literature list of 20 German, English, and Turkish language books related to SAP ERP BW BI. The books cover topics such as SAP BI project management, data warehousing with SAP BW, warehouse management with SAP, SAP BW performance optimization, SAP BW data modeling, and sales and inventory planning with SAP APO. It also lists abbreviations and websites related to SAP NetWeaver and provides a list of consulting firms in Germany that specialize in ERP, PPS, production, and consulting for various industries.

Eu OsterweiterungProf Dr Mehmed ERDAS
?
The Ost Extension of European Union; Selection Criteria and PrioritiesMerdas.Pps



Merdas.PpsProf Dr Mehmed ERDAS
?
Enterprise Resource Planning; Business Intelligence, Management Scenarios

Big data analytics for telecom operators final use cases 0712-2014_prof_m erdas



Big data analytics for telecom operators final use cases 0712-2014_prof_m erdasProf Dr Mehmed ERDAS
?
Big data analytics for telecom operators final use cases 0712-2014_prof_m erdas



Big data analytics for telecom operators final use cases 0712-2014_prof_m erdasProf Dr Mehmed ERDAS
?


Recently uploaded (20)
2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLM



2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLMTimothy Spann
?
2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLM
https://aaai.org/conference/aaai/aaai-25/workshop-list/#ws14原版复刻加拿大多伦多大学成绩单(UTSG毕业证书) 文凭



原版复刻加拿大多伦多大学成绩单(UTSG毕业证书) 文凭taqyed
?
毕业证书加拿大文凭多伦多大学成绩单?【q薇1954292140】复刻成绩单加拿大多伦多大学毕业证(UTSG毕业证书)成绩单定购 多伦多大学毕业证办理,毕业证文凭样本加拿大多伦多大学文凭办理,加拿大多伦多大学成绩单办理和真实留信认证、留服认证、多伦多大学学历认证。学院文凭定制,多伦多大学原版文凭补办,扫描件文凭定做,100%文凭复刻。【q薇1954292140】Buy St. George campus Diploma购买美国毕业证,购买英国毕业证,购买澳洲毕业证,购买加拿大毕业证,以及德国毕业证,购买法国毕业证(q薇1954292140)购买荷兰毕业证、购买瑞士毕业证、购买日本毕业证、购买韩国毕业证、购买新西兰毕业证、购买新加坡毕业证、购买西班牙毕业证、购买马来西亚毕业证等。包括了本科毕业证,硕士毕业证。
如果您在英、加、美、澳、欧洲等留学过程中或回国后:
1、在校期间因各种原因未能顺利毕业《UTSG成绩单工艺详解》【Q/WeChat:1954292140】《Buy St. George campus Transcript快速办理多伦多大学教育部学历认证书毕业文凭证书》,拿不到官方毕业证;
2、面对父母的压力,希望尽快拿到;
3、不清楚认证流程以及材料该如何准备;
4、回国时间很长,忘记办理;
5、回国马上就要找工作《正式成绩单多伦多大学毕业证书》【q薇1954292140】《购买毕业证UTSG成绩单定购》办给用人单位看;
6、企事业单位必须要求办理的;
7、需要报考公务员、购买免税车、落转户口、申请留学生创业基金。
加拿大文凭多伦多大学成绩单,UTSG毕业证【q薇1954292140】办理加拿大多伦多大学毕业证(UTSG毕业证书)【q薇1954292140】成绩单影本多伦多大学offer/学位证研究生学历信息、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决多伦多大学学历学位认证难题。
加拿大文凭购买,加拿大文凭定制,加拿大文凭补办。专业在线定制加拿大大学文凭,定做加拿大本科文凭,【q薇1954292140】复制加拿大St. George campus completion letter。在线快速补办加拿大本科毕业证、硕士文凭证书,购买加拿大学位证、多伦多大学Offer,加拿大大学文凭在线购买。高仿真还原加拿大文凭证书和外壳,定制加拿大多伦多大学成绩单和信封。办硕士学位证UTSG毕业证【q薇1954292140】办理加拿大多伦多大学毕业证(UTSG毕业证书)【q薇1954292140】成绩单定制多伦多大学offer/学位证学历认证报告怎么弄、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决多伦多大学学历学位认证难题。
特殊原因导致无法毕业,也可以联系我们帮您办理相关材料:
1:在多伦多大学挂科了,不想读了,成绩不理想怎么办???
2:打算回国了,找工作的时候,需要提供认证《UTSG成绩单购买办理多伦多大学毕业证书范本》【Q/WeChat:1954292140】Buy St. George campus Diploma《正式成绩单论文没过》有文凭却得不到认证。又该怎么办???加拿大毕业证购买,加拿大文凭购买,
3:回国了找工作没有多伦多大学文凭怎么办?有本科却要求硕士又怎么办?
帮您解决在加拿大多伦多大学未毕业难题(St. George campus)文凭购买、毕业证购买、大学文凭购买、大学毕业证购买、买文凭、日韩文凭、英国大学文凭、美国大学文凭、澳洲大学文凭、加拿大大学文凭(q薇1954292140)新加坡大学文凭、新西兰大学文凭、爱尔兰文凭、西班牙文凭、德国文凭、教育部认证,买毕业证,毕业证购买,买大学文凭,购买日韩毕业证、英国大学毕业证、美国大学毕业证、澳洲大学毕业证、加拿大大学毕业证(q薇1954292140)新加坡大学毕业证、新西兰大学毕业证、爱尔兰毕业证、西班牙毕业证、德国毕业证,回国证明,留信网认证,留信认证办理,学历认证。从而完成就业。
主营项目:
1、真实教育部国外学历学位认证《加拿大毕业文凭证书快速办理多伦多大学成绩单GPA修改》【q薇1954292140】《论文没过多伦多大学正式成绩单》,教育部存档,教育部留服网站100%可查.
2、办理UTSG毕业证,改成绩单《UTSG毕业证明办理多伦多大学学校原版文凭补办》【Q/WeChat:1954292140】Buy St. George campus Certificates《正式成绩单论文没过》,多伦多大学Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
3、真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
4、留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
《多伦多大学扫描件文凭定做加拿大毕业证书办理UTSG文凭定制您的学术成就》【q薇1954292140】学位证1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。
【q薇1954292140】办理多伦多大学毕业证(UTSG毕业证书)仿造在线制作本科文凭【q薇1954292140】多伦多大学offer/学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作加拿大多伦多大学毕业证(UTSG毕业证书)学位证书样本
留信认证的作用:
1. 身份认证:留信认证可以证明你的留学经历是真实的,且你获得的学历或学位是正规且经过认证的。这对于一些用人单位来说,尤其是对留学经历有高度要求的公司(如跨国公司或国内高端公司),这是非常重要的一个凭证。
专业评定:留信认证不仅认证你的学位证书,还会对你的所学专业进行评定。这有助于展示你的学术背景,特别是对于国内公司而言,能够清楚了解你所学专业的水平和价值。
国家人才库入库:认证后,你的信息将被纳入国家人才库,并且可以在国家人才网等平台上展示,供包括500强公司等大型公司挑选和聘用人才。这对于回国找工作特别是进入大公司,具有非常积极的作用。MusicAggregators and comparissons distributions.pdf



MusicAggregators and comparissons distributions.pdfirramos8843
?
Main Reason: Its flat annual fee and unlimited uploads make it cost-effective for independent artists with multiple releases. Introduction to database and analysis software’s suitable for.pptx



Introduction to database and analysis software’s suitable for.pptxnabinparajuli9
?
This ppt provides brief introduction and major strengths and limitations of database and analysis software’s suitable for health research.
2024-07-eb-big-book-of-data-engineering-3rd-edition.pdf



2024-07-eb-big-book-of-data-engineering-3rd-edition.pdfAlexandreMacedo50
?
The big book of data engineering 3rd-edition办理魁北克大学成绩单触购买加拿大鲍蚕础惭成绩单文凭定制



办理魁北克大学成绩单触购买加拿大鲍蚕础惭成绩单文凭定制taqyed
?
真实可查毕业证加拿大文凭购买,加拿大文凭定制,加拿大魁北克大学文凭补办【q薇1954292140】专业在线定制加拿大大学文凭成绩单用纸,定做加拿大本科文凭,【q薇1954292140】复制加拿大Université du Québec à Montréal completion letter。在线快速补办加拿大本科毕业证、硕士文凭证书,购买加拿大学位证、魁北克大学Offer,加拿大大学文凭在线购买。高仿真还原加拿大文凭证书和外壳,定制加拿大魁北克大学成绩单和信封。毕业证网上可查学历信息UQAM毕业证【q薇1954292140】办理加拿大魁北克大学毕业证(UQAM毕业证书)【q薇1954292140】毕业证外壳魁北克大学offer/学位证办学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决魁北克大学学历学位认证难题。
特殊原因导致无法毕业,也可以联系我们帮您办理相关材料:
1:在魁北克大学挂科了,不想读了,成绩不理想怎么办???
2:打算回国了,找工作的时候,需要提供认证《UQAM成绩单购买办理魁北克大学毕业证书范本》【Q/WeChat:1954292140】Buy Université du Québec à Montréal Diploma《正式成绩单论文没过》有文凭却得不到认证。又该怎么办???加拿大毕业证购买,加拿大文凭购买,
3:回国了找工作没有魁北克大学文凭怎么办?有本科却要求硕士又怎么办?
帮您解决在加拿大魁北克大学未毕业难题(Université du Québec à Montréal)文凭购买、毕业证购买、大学文凭购买、大学毕业证购买、买文凭、日韩文凭、英国大学文凭、美国大学文凭、澳洲大学文凭、加拿大大学文凭(q薇1954292140)新加坡大学文凭、新西兰大学文凭、爱尔兰文凭、西班牙文凭、德国文凭、教育部认证,买毕业证,毕业证购买,买大学文凭,购买日韩毕业证、英国大学毕业证、美国大学毕业证、澳洲大学毕业证、加拿大大学毕业证(q薇1954292140)新加坡大学毕业证、新西兰大学毕业证、爱尔兰毕业证、西班牙毕业证、德国毕业证,回国证明,留信网认证,留信认证办理,学历认证。从而完成就业。
如果您在英、加、美、澳、欧洲等留学过程中或回国后:
1、在校期间因各种原因未能顺利毕业《UQAM成绩单工艺详解》【Q/WeChat:1954292140】《Buy Université du Québec à Montréal Transcript快速办理魁北克大学教育部学历认证书毕业文凭证书》,拿不到官方毕业证;
2、面对父母的压力,希望尽快拿到;
3、不清楚认证流程以及材料该如何准备;
4、回国时间很长,忘记办理;
5、回国马上就要找工作《正式成绩单魁北克大学学历认证失败怎么办》【q薇1954292140】《成绩单水印UQAM成绩单如何办理》办给用人单位看;
6、企事业单位必须要求办理的;
7、需要报考公务员、购买免税车、落转户口、申请留学生创业基金。
加拿大文凭魁北克大学成绩单,UQAM毕业证【q薇1954292140】办理加拿大魁北克大学毕业证(UQAM毕业证书)【q薇1954292140】学历认证失败怎么办魁北克大学offer/学位证成绩单制作案例、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决魁北克大学学历学位认证难题。
【q薇1954292140】办理魁北克大学毕业证(UQAM毕业证书)毕业证范本【q薇1954292140】魁北克大学offer/学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作加拿大魁北克大学毕业证(UQAM毕业证书)学历学位证制作
主营项目:
1、真实教育部国外学历学位认证《加拿大毕业文凭证书快速办理魁北克大学在线制作假学位证》【q薇1954292140】《论文没过魁北克大学正式成绩单》,教育部存档,教育部留服网站100%可查.
2、办理UQAM毕业证,改成绩单《UQAM毕业证明办理魁北克大学毕业证书购买》【Q/WeChat:1954292140】Buy Université du Québec à Montréal Certificates《正式成绩单论文没过》,魁北克大学Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
3、真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
4、留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
《魁北克大学学位证书制作代办流程加拿大毕业证书办理UQAM学位证学生卡录取书》【q薇1954292140】学位证1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。
成绩单购买最佳渠道加拿大文凭魁北克大学成绩单【q薇1954292140】复刻成绩单加拿大魁北克大学毕业证(UQAM毕业证书)研究生学历文凭 魁北克大学毕业证办理,修改成绩单GPA加拿大魁北克大学文凭办理,加拿大魁北克大学成绩单办理和真实留信认证、留服认证、魁北克大学学历认证。学院文凭定制,魁北克大学原版文凭补办,扫描件文凭定做,100%文凭复刻。【q薇1954292140】Buy Université du Québec à Montréal Diploma购买美国毕业证,购买英国毕业证,购买澳洲毕业证,购买加拿大毕业证,以及德国毕业证,购买法国毕业证(q薇1954292140)购买荷兰毕业证、购买瑞士毕业证、购买日本毕业证、购买韩国毕业证、购买新西兰毕业证、购买新加坡毕业证、购买西班牙毕业证、购买马来西亚毕业证等。包括了本科毕业证,硕士毕业证。
留信认证的作用:
1. 身份认证:留信认证可以证明你的留学经历是真实的,且你获得的学历或学位是正规且经过认证的。这对于一些用人单位来说,尤其是对留学经历有高度要求的公司(如跨国公司或国内高端公司),这是非常重要的一个凭证。
专业评定:留信认证不仅认证你的学位证书,还会对你的所学专业进行评定。这有助于展示你的学术背景,特别是对于国内公司而言,能够清楚了解你所学专业的水平和价值。
国家人才库入库:认证后,你的信息将被纳入国家人才库,并且可以在国家人才网等平台上展示,供包括500强公司等大型公司挑选和聘用人才。这对于回国找工作特别是进入大公司,具有非常积极的作用。
2. 留信认证对就业的好处
提高竞争力:通过留信认证,尤其是对你所学专业的认证,可以大大提高你在国内求职时的竞争力。许多公司对留学生背景和所学专业有很高的要求,认证后的信息能够帮助公司快速识别符合条件的候选人。
增强信任度:公司往往会对没有认证的学历背景产生疑虑,而留信认证为你的学历背景提供了第三方权威机构的背书,增强了雇主的信任。Hire Android App Developers in India with Cerebraix



Hire Android App Developers in India with Cerebraixcerebraixs
?
Android app developers are crucial for creating
high-quality, user-friendly, and innovative mobile
applications. Their expertise in mobile development,
UI/UX design, and seamless integration ensures robust
and scalable apps that drive user engagement and
business success in the competitive mobile market.Boosting MySQL with Vector Search Scale22X 2025.pdf



Boosting MySQL with Vector Search Scale22X 2025.pdfAlkin Tezuysal
?
As the demand for vector databases and Generative AI continues to rise, integrating vector storage and search capabilities into traditional databases has become increasingly important. This session introduces the *MyVector Plugin*, a project that brings native vector storage and similarity search to MySQL. Unlike PostgreSQL, which offers interfaces for adding new data types and index methods, MySQL lacks such extensibility. However, by utilizing MySQL's server component plugin and UDF, the *MyVector Plugin* successfully adds a fully functional vector search feature within the existing MySQL + InnoDB infrastructure, eliminating the need for a separate vector database. The session explains the technical aspects of integrating vector support into MySQL, the challenges posed by its architecture, and real-world use cases that showcase the advantages of combining vector search with MySQL's robust features. Attendees will leave with practical insights on how to add vector search capabilities to their MySQLThe truth behind the numbers: spotting statistical misuse.pptx



The truth behind the numbers: spotting statistical misuse.pptxandyprosser3
?
As a producer of official statistics, being able to define what misinformation means in relation to data and statistics is so important to us.
For our sixth webinar, we explored how we handle statistical misuse especially in the media. We were also joined by speakers from the Office for Statistics Regulation (OSR) to explain how they play an important role in investigating and challenging the misuse of statistics across government.Optimizing Common Table Expressions in Apache Hive with Calcite



Optimizing Common Table Expressions in Apache Hive with CalciteStamatis Zampetakis
?
In many real-world queries, certain expressions may appear multiple times, requiring repeated computations to construct the final result. These recurring computations, known as common table expressions (CTEs), can be explicitly defined in SQL queries using the WITH clause or implicitly derived through transformation rules. Identifying and leveraging CTEs is essential for reducing the cost of executing complex queries and is a critical component of modern data management systems.
Apache Hive, a SQL-based data management system, provides powerful mechanisms to detect and exploit CTEs through heuristic and cost-based optimization techniques.
This talk delves into the internals of Hive's planner, focusing on its integration with Apache Calcite for CTE optimization. We will begin with a high-level overview of Hive's planner architecture and its reliance on Calcite in various planning phases. The discussion will then shift to the CTE rewriting phase, highlighting key Calcite concepts and demonstrating how they are employed to optimize CTEs effectively.the data analytics process:Real life applications



the data analytics process:Real life applicationsjhanvisaxena30
?
the data analytics process: Real life applicationsMLecture 1 Introduction to AI . The basics.pptx



MLecture 1 Introduction to AI . The basics.pptxFaizaKhan720183
?
Machine learning and artificial intelligence introduction. Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Dr erdas sap ilm_basics
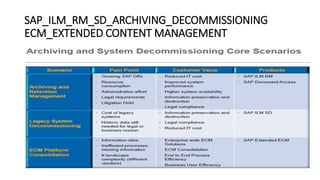
- 2. ARCHIVING STRATEGY;VISION; ONE LAUNCHPAD(ONECONTACT, STORAGE, ARCH_IQ)
- 5. RETENTION MANAGEMENT PROCESS ILMARA; IRMPOL; IRM_CUST; ILMSTOREADM; SARA;AOBJ
- 8. How to find&implement the ILMOBJ/ S_NOTE ? https://launchpad.support.sap.com/#/solutions/notesv2/?q=SAP%25 2520ILM%252520NOtes%252520List&sortBy=score&sortOrder=des ? ?
- 12. SAMPLE LIST OF SAP S_NOTES launchpad.support.sap.com/#/notes/Nr.
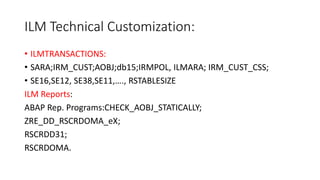
- 16. ILM Technical Customization: ? ILMTRANSACTIONS: ? SARA;IRM_CUST;AOBJ;db15;IRMPOL, ILMARA; IRM_CUST_CSS; ? SE16,SE12, SE38,SE11,…., RSTABLESIZE ILM Reports: ABAP Rep. Programs:CHECK_AOBJ_STATICALLY; ZRE_DD_RSCRDOMA_eX; RSCRDD31; RSCRDOMA.
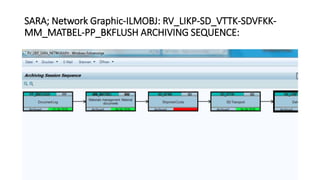
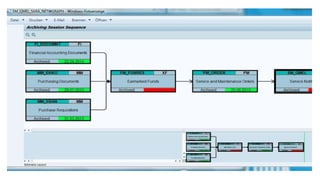
- 17. SARA; Network Graphic-ILMOBJ: RV_LIKP-SD_VTTK-SDVFKK- MM_MATBEL-PP_BKFLUSH ARCHIVING SEQUENCE:
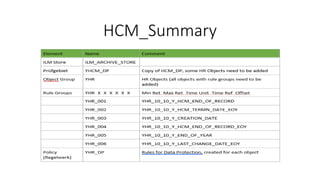
- 20. HCM_Summary
- 21. SAP Note 2298980; Customer/Vendor Destruction: ILM Policies checks and validation LO-MD-BP-DP ? KUNDE Domain RSCRDD31 Table Short description ? /WSWN/076 SPEEDI: Errortable of copy of scheduling agreements ? SER02 Document Header for Serial Nos for Maint.Contract (SD Order) ? VAKPA Sales Index: Orders by Partner Function ? VLKPA SD Index: Deliveries by Partner Functions ? VRKPA Sales Index: Bills by Partner Functions ? SAP_APPL 617 617 2066278 Customer/vendor master data destruction - New Enterprise Services - Interface note Part 2 LO-MD-BP-DP ? SAP_APPL 617 617 2112841 Customer/Vendor data Destruction: No ERP Layer EoP Check - Part 2 LO-MD-BP-DP ? SAP_APPL 617 617 2298980 Customer/Vendor Destruction: ILM Policies checks and validation LO-MD-BP-DP ? SAP_APPL 618 618 2298980 Customer/Vendor Destruction: ILM Policies checks and validation











