Draft: building secure applications with keycloak (oidc/jwt)
- 1. Building secure applications with keycloak (OIDC/JWT) Abhishek Koserwal Red Hat
- 2. Agenda Ī± IAAA Security factor Ī± Oauth2/OpenID Ī± Why? Keycloak Ī± OIDC/SAML - Keycloak adapters (which & why?) Ī± Understanding Json Web Token (JWT) Ī± Integrating frontend(Angular/React) with keycloak adapter. - Ī± Access token/refresh token Ī± JWT Validation at backend & securing API endpoints Ī± Q & A
- 3. Ī± Identification: set of attributes related to an entity (person -> attribute [name, email] ) Ī± Authentication: is the process of verifying an identity (who they say they are) Ī± Authorization: is the process of verifying what someone is allowed to do (permissions) Ī± Accounting: logs, user action, traceability of action IAAA Security Factor
- 4. Are we using Oauth2/OpenID? Delegation Auth Allow website to access my data without providing my password? ? Authentication/Identity Level ? Authorization/Access Control Level ? Site needs to manage security ? Store hash password, verify the hash against a database
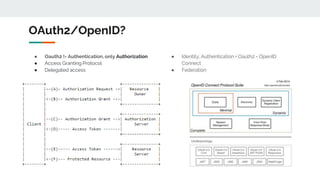
- 5. Ī± Oauth2 != Authentication, only Authorization Ī± Access Granting Protocol Ī± Delegated access OAuth2/OpenID? Ī± Identity, Authentication + Oauth2 = OpenID Connect Ī± Federation
- 6. Why? Keycloak Ī± Open source Identity and Access Management solution (https://github.com/keycloak/keycloak) Ī± Browsers, mobiles and clouds Ī± Many accounts Ī± Admin headache Features Ī± SSO Ī± Admin console Ī± Login forms Ī± Account management Ī± Multi-factor auth Ī± Social login Ī± ..
- 7. Setup: keycloak docker pull jboss/keycloak docker run -d -e KEYCLOAK_USER=<USERNAME> -e KEYCLOAK_PASSWORD=<PASSWORD> -p 8081:8080 jboss/keycloak Require docker daemon running Standalone server distribution (https://www.keycloak.org/downloads.htm)


![Ī± Identification: set of attributes related to an entity
(person -> attribute [name, email] )
Ī± Authentication: is the process of verifying an identity (who they say they are)
Ī± Authorization: is the process of verifying what someone is allowed to do
(permissions)
Ī± Accounting: logs, user action, traceability of action
IAAA Security Factor](https://image.slidesharecdn.com/vjvcsowdqwiscvi11bq9-signature-bfa48c0cb7507fc8a7e4f5c326ae0fe4f63559a39e602afe2bad7425998b8940-poli-180927134521/85/Draft-building-secure-applications-with-keycloak-oidc-jwt-3-320.jpg)