Droid swan
1 like524 views
This document discusses the development of DroidSwan, a machine learning-based Android malware detection system. It begins with background on the prevalence of Android malware and need for effective detection. It then outlines the process used to build DroidSwan, including collecting a dataset of malware and benign apps, extracting relevant features, deriving an optimal feature set, building a classifier model, and evaluating performance based on ROC curve, recall rate, and detection rate. Key features for detection included suspicious permissions, permission combinations, API calls, and manifest violations. The system achieved high performance in detecting Android malware.
1 of 32
Download to read offline








Ad
Recommended
Insider theft detection
Insider theft detection SumanthKommineni
Ěý
The document discusses insider theft, which involves the unauthorized access and misuse of sensitive organizational data, primarily by current or former employees. It outlines the stages of data theft and emphasizes detection methods through network monitoring, machine learning with neural networks, and file access log analysis. Various Windows event codes are specified to identify suspicious activities, with the intention of maintaining cybersecurity and organizational integrity.Fraud and Malware Detection in Google Play by using Search Rank
Fraud and Malware Detection in Google Play by using Search Rankijtsrd
Ěý
1. The document presents a new system called FairPlay that aims to detect fraud and malware in Google Play apps.
2. FairPlay generates relational, behavioral and linguistic features from apps to train machine learning models to classify apps as fraudulent, benign, or malware.
3. Experimental results show that FairPlay achieves over 97% accuracy in detecting fraudulent apps and over 95% accuracy in detecting malware apps, outperforming existing approaches. FairPlay also discovered hundreds of fraudulent apps not detected by Google's systems.Hii assessing the_effectiveness_of_antivirus_solutions
Hii assessing the_effectiveness_of_antivirus_solutionsAnatoliy Tkachev
Ěý
The document summarizes a study that assessed the effectiveness of antivirus software in detecting newly created malware. Some key findings include:
- The initial detection rate of new viruses by antivirus software is less than 5%, and for some vendors it can take up to 4 weeks to detect a new virus.
- Free antivirus software from Avast and Emisoft had among the best detection capabilities, though they also had high false positive rates.
- Given the low effectiveness of antivirus software, the document suggests that enterprises and consumers should consider alternative security approaches and that compliance requirements around antivirus could be eased to allow budgets to be used more effectively.Top 5 cases of Data Breach caused by Human Error
Top 5 cases of Data Breach caused by Human ErrorCyware
Ěý
The document outlines five significant data breaches caused by human error, including incidents involving Sony Pictures, JPMorgan Chase, eBay, the Pentagon, and NHS. Each case highlights how attackers exploited phishing tactics or mismanagement of information to gain unauthorized access to sensitive data. It emphasizes the importance for security teams to promptly address vulnerabilities to prevent such breaches.Android App Security: What (not) to do!
Android App Security: What (not) to do!Thomas Methlie
Ěý
This document discusses common security issues for Android apps and provides recommendations to address them. It identifies issues such as overprivileged apps, information exposure through sent data, intent spoofing, unauthorized intent receipt, insufficient entropy, and use of hardcoded cryptographic keys. The document recommends techniques like using permissions and explicit intents to prevent spoofing, validating untrusted inputs, and parametrized queries to prevent SQL injection. It also cautions against sending sensitive data in sticky broadcasts.VirusTotal Threat Intelligence and DNIF Use Cases
VirusTotal Threat Intelligence and DNIF Use CasesDNIF
Ěý
The document discusses a method for detecting malicious URLs using DNIF in conjunction with the VirusTotal API. It outlines a query that fetches log events and triggers alerts if a URL is deemed malicious by VirusTotal. Additionally, it includes instructions for setting up notifications for affected parties.Google android security_2018_report
Google android security_2018_reportmalvvv
Ěý
This document summarizes the Android security landscape in 2018. It discusses improvements to protections on the Android platform, Google Play, and Google Play Protect that helped reduce the presence of potentially harmful applications (PHAs) on devices. Some key accomplishments include 84% more devices receiving security updates, Google Play Protect scanning over 50 billion apps daily, and preventing 242 builds containing PHAs from being released.Three Simple Steps to Prevent Targeted Attacks
Three Simple Steps to Prevent Targeted AttacksArgyle Executive Forum
Ěý
The document discusses the increase in targeted attack campaigns and zero-day vulnerabilities from 2012 to 2013, highlighting the need for improved security measures. It outlines three steps to prevent attacks: running more than antivirus on endpoints, protecting websites by patching vulnerabilities, and ensuring that partners maintain good security practices. Specific examples of cyberattacks targeting industries like energy are provided to illustrate the evolving threat landscape.ANDROINSPECTOR: A SYSTEM FOR COMPREHENSIVE ANALYSIS OF ANDROID APPLICATIONS
ANDROINSPECTOR: A SYSTEM FOR COMPREHENSIVE ANALYSIS OF ANDROID APPLICATIONSIJNSA Journal
Ěý
The document presents Androinspector, a system designed for the comprehensive analysis of Android applications through static and dynamic analysis techniques. It addresses the challenge of identifying malicious applications in the Android marketplace, integrating machine learning methods for classification and automating application execution to monitor runtime behaviors. Androinspector combines feature extraction from applications with the analysis of traces during execution to classify applications as either benign or malicious effectively.Androinspector a system for
Androinspector a system forIJNSA Journal
Ěý
The document presents 'AndroInspector', a system designed for comprehensive analysis of Android applications through both static and dynamic analysis techniques to identify malicious software. It addresses the growing prevalence of malware in the Android market due to ineffective detection mechanisms, using a machine learning model trained on a dataset of malicious and benign applications to classify apps. The analysis includes automated execution of apps in an emulator, tracking behaviors to detect pre-defined malicious actions, alongside extracting critical features for classification.DROIDSWAN: Detecting Malicious Android Applications Based on Static Feature A...
DROIDSWAN: Detecting Malicious Android Applications Based on Static Feature A...csandit
Ěý
The document discusses Droidswan, a system designed to detect malicious Android applications through static feature analysis and machine learning techniques. It emphasizes the algorithm's ability to classify applications as benign or malicious by extracting and analyzing various crucial features from APK files while achieving high detection rates with a weighted approach. The study utilizes a dataset of malware and benign applications to train the classifier, with Random Forest showing the best performance concerning false positive rates.A FRAMEWORK FOR THE DETECTION OF BANKING TROJANS IN ANDROID
A FRAMEWORK FOR THE DETECTION OF BANKING TROJANS IN ANDROIDIJNSA Journal
Ěý
The document presents a framework for detecting Android Banking Trojans (ABTs) using a hybrid analysis approach that combines static and dynamic feature extraction. The proposed model utilizes machine learning techniques, achieving accuracy rates of up to 98% with selected algorithms, particularly the random forest classifier. The framework focuses on specific features such as permissions and API calls extracted from a dataset of 2,182 applications, including both malicious and non-malicious samples.18-mobile-malware.pptx
18-mobile-malware.pptxsundar110567
Ěý
This document summarizes mobile malware and security issues in Android apps. It discusses identifying malware at app stores rather than on devices. It also describes a study that analyzed over 1 million Android apps from the Google Play store, finding that 85% used web interfaces and many were vulnerable. Additionally, it covers how outdated Android apps may disable security patches by targeting older Android versions and behaving in riskier default ways.Bitdefender mobile security for android
Bitdefender mobile security for androidKazi Sarwar Hossain
Ěý
Bitdefender, founded in 2001 in Romania, operates in over 100 countries and has over 500 million users, offering complete protection for various user types. In Bangladesh since May 2014, Bitdefender focuses on branding and support through a network of over 650 channel partners. The document also details various types of mobile malware and the statistics regarding their prevalence and impact on users globally.Why Serverless is scary without DevSecOps and Observability
Why Serverless is scary without DevSecOps and ObservabilityEficode
Ěý
This document discusses the security challenges of serverless computing without proper DevSecOps practices and observability. It notes that serverless applications are often seen as more secure since the cloud provider manages the infrastructure, but they can still be vulnerable to events, libraries, and code issues. The document recommends implementing DevSecOps with a focus on permissions, security analysis, public scrutiny of practices, and crowdsourcing security through bug bounties and hackathons. It also stresses the importance of observability tools to monitor serverless applications and catch issues.A Preliminary Conceptualization and Analysis on Automated Static Analysis Too...
A Preliminary Conceptualization and Analysis on Automated Static Analysis Too...SEAA 2022
Ěý
The document analyzes the performance and capabilities of automated static analysis tools for detecting vulnerabilities in Android applications. It identifies 11 high-level and 41 low-level vulnerability categories, with a focus on issues like insecure communication, privacy, and access control. Although a range of tools exists, their effectiveness varies, and many vulnerabilities remain undetected or are only partially covered.Automated Android Malware Detection Using Optimal Ensemble Learning Approach ...
Automated Android Malware Detection Using Optimal Ensemble Learning Approach ...Shakas Technologies
Ěý
This document presents an automated android malware detection technique using an optimal ensemble learning approach (AAMD-OELAC) aimed at improving cybersecurity. It employs data preprocessing and combines three machine learning models to enhance detection accuracy, with results indicating superior performance compared to existing methods. Additionally, the paper discusses the evolving nature of malware and emphasizes the need for adaptive detection solutions integrated with current security frameworks.IEEE ANDROID APPLICATION 2016 TITLE AND ABSTRACT
IEEE ANDROID APPLICATION 2016 TITLE AND ABSTRACTtsysglobalsolutions
Ěý
The document discusses various research papers centered on Android application security and reliability, presenting systems designed for malware detection, resource leak detection, and reliable context provisioning in mobile apps. Notable contributions include MADAM, which blocks over 96% of malicious apps, and ICCDetector, which achieves a malware detection accuracy of 97.4%. Each study emphasizes the importance of enhancing detection methods and optimizing performance while minimizing false positives in Android applications.Icsm2011 syer
Icsm2011 syerSAIL_QU
Ěý
This document explores the development of micro-apps across different mobile platforms. It finds that Android apps are typically smaller in size than equivalent apps on BlackBerry, but Android apps also depend more on third-party libraries and the platform itself. This high platform dependency for Android apps can reduce development effort due to platform support but also increases maintenance effort and makes porting apps to other platforms more difficult. The document discusses how these findings for micro-apps may differ compared to desktop applications.Android security
Android security Hassan Abutair
Ěý
The document summarizes a research paper that studied detecting malicious Android applications in official and third-party Android app markets. The researchers developed a system called DroidRanger that uses permission-based filtering and behavioral analysis to detect both known and unknown malware. DroidRanger revealed 211 malicious apps total, with 32 from the official market and 179 from alternative markets. It also discovered a sophisticated zero-day malware with 40 samples, 11 of which were in the official market.MOTODEV App Validator
MOTODEV App ValidatorMotorola Mobility - MOTODEV
Ěý
The document outlines the features and benefits of the Motodev App Validator, a static analysis tool designed to improve the quality of enterprise Android applications. It details how the validator operates, including its ability to check for permissions, localized strings, and code issues, as well as its integration options. Additionally, it emphasizes the importance of using the tool prior to deployment to catch potential errors early in the development process.Cyber Code Intelligence for Android Malware Detection.pdf
Cyber Code Intelligence for Android Malware Detection.pdfOKOKPROJECTS
Ěý
This document presents a new multiview feature intelligence (MFI) framework for detecting evolving Android malware, addressing the shortcomings of existing machine-learning methods that struggle with zero-day malware families. The framework employs reverse engineering to extract diverse features and learns representations from known malware families, allowing it to recognize unknown threats with similar capabilities. Experiments on a newly created dataset show that the MFI framework significantly outperforms three state-of-the-art detection methods.IRJET- Android Malware Detection System
IRJET- Android Malware Detection SystemIRJET Journal
Ěý
This document presents a proposed machine learning-based Android malware detection system. It discusses how Android devices are increasingly being targeted by malware due to the open nature of the Android app marketplace. The proposed system would use machine learning classifiers to analyze permission-based features and events from Android apps to classify them as goodware or malware. It would monitor apps and detect malware to enhance security and privacy for smartphone users. The system design uses k-means clustering and naive Bayes classification on XML and DEX file features to detect malware in two layers if needed.Malware Detection in Android Applications
Malware Detection in Android Applicationsijtsrd
Ěý
The paper discusses a proposed dynamic malware detection approach for Android applications that utilizes system call analysis. Using naive Bayes classifiers with 3-gram and 5-gram techniques, the method achieves 85% and 89% accuracy in detecting malware applications, respectively. The approach enhances detection efficiency by filtering system calls based on frequency before classification.Bitdefender mobile security for android
Bitdefender mobile security for androidKazi Sarwar Hossain
Ěý
Bitdefender, founded in 2001 in Romania, operates in over 100 countries and supports more than 500 million users by offering comprehensive security solutions. Bitdefender Bangladesh, established in May 2014, focuses on branding and market strategies without direct sales, while providing 24/7 online technical support. The document also outlines different types of mobile malware and provides statistics on mobile threats, with Bangladesh ranking high among countries attacked by mobile malware.Verizon Breach Investigation Report (VBIR).pdf
Verizon Breach Investigation Report (VBIR).pdfPriyanka Aash
Ěý
The Verizon Breach Investigation Report (VBIR) is an annual report analyzing cybersecurity incidents based on real-world data. It categorizes incidents and identifies emerging trends, threat actors, motivations, attack vectors, affected industries, common attack patterns, and recommendations. Each report provides the latest insights and data to give organizations a global perspective on evolving cyber threats.Next Generation Defense in Depth Model - Tari Schreider, CCISO, Chief Cybers...
Next Generation Defense in Depth Model - Tari Schreider, CCISO, Chief Cybers...EC-Council
Ěý
The document discusses the evolution and relevance of the defense in depth cybersecurity model, highlighting the need for adaptation to modern attack vectors. It outlines key components and missing tiers across different domains such as threat management, application security, and security operations, providing use cases and recommendations for CISOs. The emphasis is on creating a holistic and responsive cybersecurity strategy aligned with organizational goals and internal capabilities.EDR - Cehckpoint CPX 2024 Harmony Endpoint.pptx
EDR - Cehckpoint CPX 2024 Harmony Endpoint.pptxAldoPalominoBravo
Ěý
The document outlines Check Point's advanced security solutions, emphasizing comprehensive protection against ransomware and phishing attacks through multi-layered endpoint security. It highlights features such as data loss prevention, threat intelligence, and incident management, all managed via a unified interface. Check Point's offerings are designed to safeguard organizations from evolving cyber threats, utilizing AI and automation for optimal security performance.More Related Content
Similar to Droid swan (20)
ANDROINSPECTOR: A SYSTEM FOR COMPREHENSIVE ANALYSIS OF ANDROID APPLICATIONS
ANDROINSPECTOR: A SYSTEM FOR COMPREHENSIVE ANALYSIS OF ANDROID APPLICATIONSIJNSA Journal
Ěý
The document presents Androinspector, a system designed for the comprehensive analysis of Android applications through static and dynamic analysis techniques. It addresses the challenge of identifying malicious applications in the Android marketplace, integrating machine learning methods for classification and automating application execution to monitor runtime behaviors. Androinspector combines feature extraction from applications with the analysis of traces during execution to classify applications as either benign or malicious effectively.Androinspector a system for
Androinspector a system forIJNSA Journal
Ěý
The document presents 'AndroInspector', a system designed for comprehensive analysis of Android applications through both static and dynamic analysis techniques to identify malicious software. It addresses the growing prevalence of malware in the Android market due to ineffective detection mechanisms, using a machine learning model trained on a dataset of malicious and benign applications to classify apps. The analysis includes automated execution of apps in an emulator, tracking behaviors to detect pre-defined malicious actions, alongside extracting critical features for classification.DROIDSWAN: Detecting Malicious Android Applications Based on Static Feature A...
DROIDSWAN: Detecting Malicious Android Applications Based on Static Feature A...csandit
Ěý
The document discusses Droidswan, a system designed to detect malicious Android applications through static feature analysis and machine learning techniques. It emphasizes the algorithm's ability to classify applications as benign or malicious by extracting and analyzing various crucial features from APK files while achieving high detection rates with a weighted approach. The study utilizes a dataset of malware and benign applications to train the classifier, with Random Forest showing the best performance concerning false positive rates.A FRAMEWORK FOR THE DETECTION OF BANKING TROJANS IN ANDROID
A FRAMEWORK FOR THE DETECTION OF BANKING TROJANS IN ANDROIDIJNSA Journal
Ěý
The document presents a framework for detecting Android Banking Trojans (ABTs) using a hybrid analysis approach that combines static and dynamic feature extraction. The proposed model utilizes machine learning techniques, achieving accuracy rates of up to 98% with selected algorithms, particularly the random forest classifier. The framework focuses on specific features such as permissions and API calls extracted from a dataset of 2,182 applications, including both malicious and non-malicious samples.18-mobile-malware.pptx
18-mobile-malware.pptxsundar110567
Ěý
This document summarizes mobile malware and security issues in Android apps. It discusses identifying malware at app stores rather than on devices. It also describes a study that analyzed over 1 million Android apps from the Google Play store, finding that 85% used web interfaces and many were vulnerable. Additionally, it covers how outdated Android apps may disable security patches by targeting older Android versions and behaving in riskier default ways.Bitdefender mobile security for android
Bitdefender mobile security for androidKazi Sarwar Hossain
Ěý
Bitdefender, founded in 2001 in Romania, operates in over 100 countries and has over 500 million users, offering complete protection for various user types. In Bangladesh since May 2014, Bitdefender focuses on branding and support through a network of over 650 channel partners. The document also details various types of mobile malware and the statistics regarding their prevalence and impact on users globally.Why Serverless is scary without DevSecOps and Observability
Why Serverless is scary without DevSecOps and ObservabilityEficode
Ěý
This document discusses the security challenges of serverless computing without proper DevSecOps practices and observability. It notes that serverless applications are often seen as more secure since the cloud provider manages the infrastructure, but they can still be vulnerable to events, libraries, and code issues. The document recommends implementing DevSecOps with a focus on permissions, security analysis, public scrutiny of practices, and crowdsourcing security through bug bounties and hackathons. It also stresses the importance of observability tools to monitor serverless applications and catch issues.A Preliminary Conceptualization and Analysis on Automated Static Analysis Too...
A Preliminary Conceptualization and Analysis on Automated Static Analysis Too...SEAA 2022
Ěý
The document analyzes the performance and capabilities of automated static analysis tools for detecting vulnerabilities in Android applications. It identifies 11 high-level and 41 low-level vulnerability categories, with a focus on issues like insecure communication, privacy, and access control. Although a range of tools exists, their effectiveness varies, and many vulnerabilities remain undetected or are only partially covered.Automated Android Malware Detection Using Optimal Ensemble Learning Approach ...
Automated Android Malware Detection Using Optimal Ensemble Learning Approach ...Shakas Technologies
Ěý
This document presents an automated android malware detection technique using an optimal ensemble learning approach (AAMD-OELAC) aimed at improving cybersecurity. It employs data preprocessing and combines three machine learning models to enhance detection accuracy, with results indicating superior performance compared to existing methods. Additionally, the paper discusses the evolving nature of malware and emphasizes the need for adaptive detection solutions integrated with current security frameworks.IEEE ANDROID APPLICATION 2016 TITLE AND ABSTRACT
IEEE ANDROID APPLICATION 2016 TITLE AND ABSTRACTtsysglobalsolutions
Ěý
The document discusses various research papers centered on Android application security and reliability, presenting systems designed for malware detection, resource leak detection, and reliable context provisioning in mobile apps. Notable contributions include MADAM, which blocks over 96% of malicious apps, and ICCDetector, which achieves a malware detection accuracy of 97.4%. Each study emphasizes the importance of enhancing detection methods and optimizing performance while minimizing false positives in Android applications.Icsm2011 syer
Icsm2011 syerSAIL_QU
Ěý
This document explores the development of micro-apps across different mobile platforms. It finds that Android apps are typically smaller in size than equivalent apps on BlackBerry, but Android apps also depend more on third-party libraries and the platform itself. This high platform dependency for Android apps can reduce development effort due to platform support but also increases maintenance effort and makes porting apps to other platforms more difficult. The document discusses how these findings for micro-apps may differ compared to desktop applications.Android security
Android security Hassan Abutair
Ěý
The document summarizes a research paper that studied detecting malicious Android applications in official and third-party Android app markets. The researchers developed a system called DroidRanger that uses permission-based filtering and behavioral analysis to detect both known and unknown malware. DroidRanger revealed 211 malicious apps total, with 32 from the official market and 179 from alternative markets. It also discovered a sophisticated zero-day malware with 40 samples, 11 of which were in the official market.MOTODEV App Validator
MOTODEV App ValidatorMotorola Mobility - MOTODEV
Ěý
The document outlines the features and benefits of the Motodev App Validator, a static analysis tool designed to improve the quality of enterprise Android applications. It details how the validator operates, including its ability to check for permissions, localized strings, and code issues, as well as its integration options. Additionally, it emphasizes the importance of using the tool prior to deployment to catch potential errors early in the development process.Cyber Code Intelligence for Android Malware Detection.pdf
Cyber Code Intelligence for Android Malware Detection.pdfOKOKPROJECTS
Ěý
This document presents a new multiview feature intelligence (MFI) framework for detecting evolving Android malware, addressing the shortcomings of existing machine-learning methods that struggle with zero-day malware families. The framework employs reverse engineering to extract diverse features and learns representations from known malware families, allowing it to recognize unknown threats with similar capabilities. Experiments on a newly created dataset show that the MFI framework significantly outperforms three state-of-the-art detection methods.IRJET- Android Malware Detection System
IRJET- Android Malware Detection SystemIRJET Journal
Ěý
This document presents a proposed machine learning-based Android malware detection system. It discusses how Android devices are increasingly being targeted by malware due to the open nature of the Android app marketplace. The proposed system would use machine learning classifiers to analyze permission-based features and events from Android apps to classify them as goodware or malware. It would monitor apps and detect malware to enhance security and privacy for smartphone users. The system design uses k-means clustering and naive Bayes classification on XML and DEX file features to detect malware in two layers if needed.Malware Detection in Android Applications
Malware Detection in Android Applicationsijtsrd
Ěý
The paper discusses a proposed dynamic malware detection approach for Android applications that utilizes system call analysis. Using naive Bayes classifiers with 3-gram and 5-gram techniques, the method achieves 85% and 89% accuracy in detecting malware applications, respectively. The approach enhances detection efficiency by filtering system calls based on frequency before classification.Bitdefender mobile security for android
Bitdefender mobile security for androidKazi Sarwar Hossain
Ěý
Bitdefender, founded in 2001 in Romania, operates in over 100 countries and supports more than 500 million users by offering comprehensive security solutions. Bitdefender Bangladesh, established in May 2014, focuses on branding and market strategies without direct sales, while providing 24/7 online technical support. The document also outlines different types of mobile malware and provides statistics on mobile threats, with Bangladesh ranking high among countries attacked by mobile malware.Verizon Breach Investigation Report (VBIR).pdf
Verizon Breach Investigation Report (VBIR).pdfPriyanka Aash
Ěý
The Verizon Breach Investigation Report (VBIR) is an annual report analyzing cybersecurity incidents based on real-world data. It categorizes incidents and identifies emerging trends, threat actors, motivations, attack vectors, affected industries, common attack patterns, and recommendations. Each report provides the latest insights and data to give organizations a global perspective on evolving cyber threats.Next Generation Defense in Depth Model - Tari Schreider, CCISO, Chief Cybers...
Next Generation Defense in Depth Model - Tari Schreider, CCISO, Chief Cybers...EC-Council
Ěý
The document discusses the evolution and relevance of the defense in depth cybersecurity model, highlighting the need for adaptation to modern attack vectors. It outlines key components and missing tiers across different domains such as threat management, application security, and security operations, providing use cases and recommendations for CISOs. The emphasis is on creating a holistic and responsive cybersecurity strategy aligned with organizational goals and internal capabilities.EDR - Cehckpoint CPX 2024 Harmony Endpoint.pptx
EDR - Cehckpoint CPX 2024 Harmony Endpoint.pptxAldoPalominoBravo
Ěý
The document outlines Check Point's advanced security solutions, emphasizing comprehensive protection against ransomware and phishing attacks through multi-layered endpoint security. It highlights features such as data loss prevention, threat intelligence, and incident management, all managed via a unified interface. Check Point's offerings are designed to safeguard organizations from evolving cyber threats, utilizing AI and automation for optimal security performance.Automated Android Malware Detection Using Optimal Ensemble Learning Approach ...
Automated Android Malware Detection Using Optimal Ensemble Learning Approach ...Shakas Technologies
Ěý
Droid swan
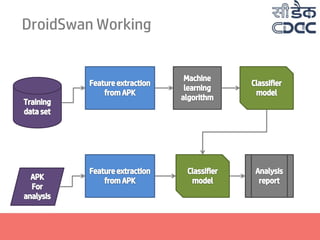
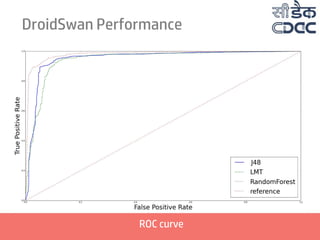
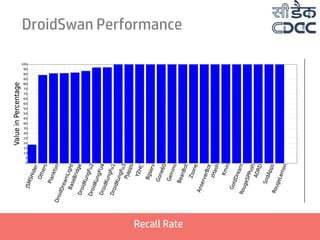
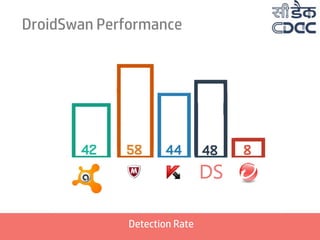
- 2. Presentation Structure 01 Why DroidSwan? 02 Android and Malware 03 Building DroidSwan 05 Extracting Features 06 Deriving Feature set 07 DroidSwan Working 04 Identifying Features 08 DroidSwan Performance
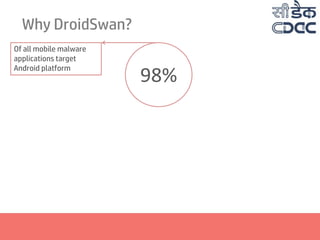
- 3. Why DroidSwan? Of all mobile malware applications target Android platform 98%
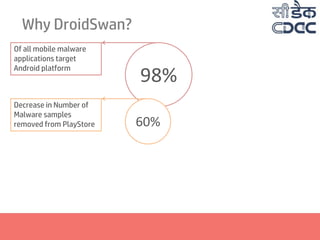
- 4. Why DroidSwan? Of all mobile malware applications target Android platform Decrease in Number of Malware samples removed from PlayStore 98% 60%
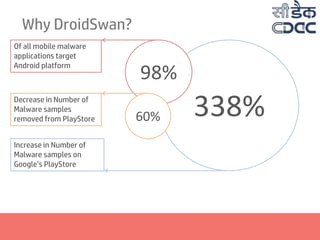
- 5. Why DroidSwan? 338% Of all mobile malware applications target Android platform Decrease in Number of Malware samples removed from PlayStore Increase in Number of Malware samples on Google’s PlayStore 98% 60%
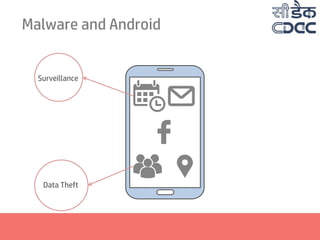
- 9. Malware and Android Surveillance Data Theft Privacy Invasion
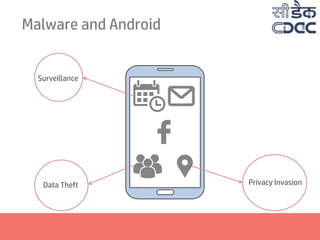
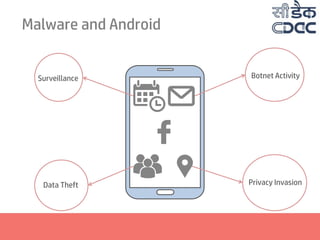
- 10. Malware and Android Surveillance Data Theft Botnet Activity Privacy Invasion
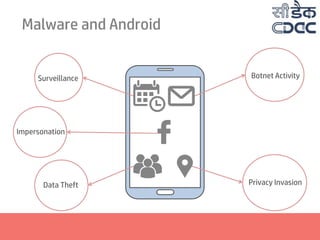
- 11. Malware and Android Surveillance Impersonation Data Theft Botnet Activity Privacy Invasion
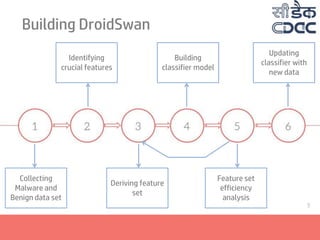
- 12. Building DroidSwan Collecting Malware and Benign data set Updating classifier with new data Feature set efficiency analysis Building classifier model Deriving feature set Identifying crucial features
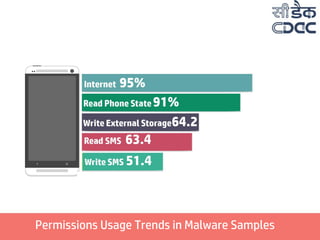
- 15. Permissions Usage Trends in Malware Samples
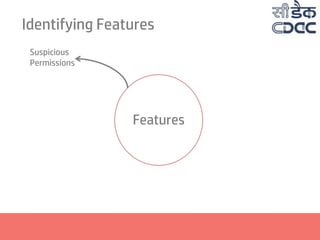
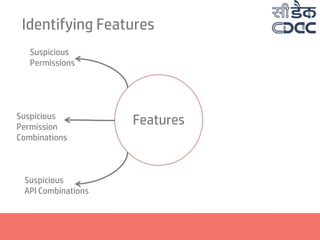
- 17. Identifying Features Features Suspicious Permissions Suspicious Permission Combinations Suspicious API Combinations Presence of Executables
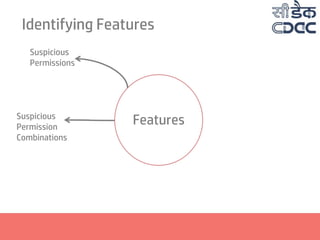
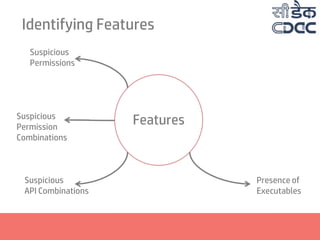
- 18. Identifying Features Features Suspicious Permissions Suspicious Permission Combinations Suspicious API Combinations Manifest Violation Presence of Executables
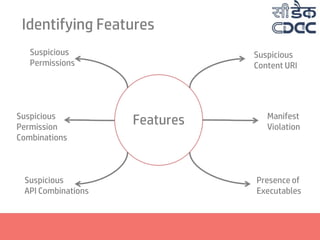
- 19. Features Suspicious Permissions Suspicious Permission Combinations Suspicious API Combinations Suspicious Content URI Manifest Violation Presence of Executables Identifying Features
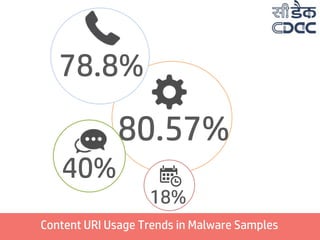
- 20. 80.57% Content URI Usage Trends in Malware Samples 40% 78.8% 18%
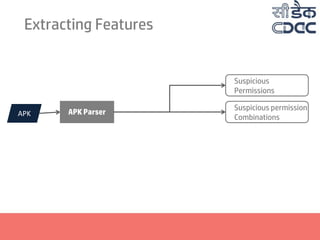
- 21. Extracting Features APK APK Parser Suspicious Permissions Suspicious permission Combinations
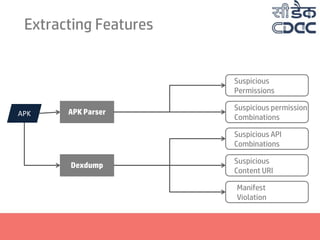
- 22. Extracting Features APK APK Parser Dexdump Suspicious Permissions Suspicious permission Combinations Suspicious API Combinations Suspicious Content URI Manifest Violation
- 23. Extracting Features APK APK Parser Dexdump Jar Disassembler Executables in resources Suspicious Permissions Suspicious permission Combinations Suspicious API Combinations Suspicious Content URI Manifest Violation
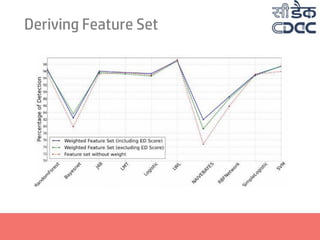
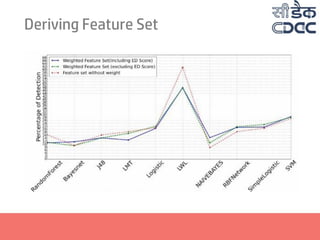
- 24. Deriving Feature Set Three variations of feature set considered : •Weighted feature set with ED as a feature •Weighted feature set without ED as a feature •Non-Weighted feature set
- 31. Babu Rajesh V has been working for three years in the field of mobile security and malware analysis. His areas of interests include mobile security and embedded security Himanshu Pareek has around six years of experience in developing and design of security solutions related to small sized networks. He has research papers published on topics like malware detection based on behaviour and application modelling Mahesh U Patil received master degree in electronics and communication. Presently he is working as Principal Technical Officer at CDAC. His research interests include Mobile Security and Embedded Systems Phaninder Reddy has been working for two years in the field of mobile security and malware analysis. His areas of interests include machine learning and data analytics Our Team