E securty
Download as pptx, pdf0 likes265 views
The document discusses e-security and covers several topics including network system structure, types of attacks, cryptography, and malware. It describes the OSI model layers, common attacks like passive attacks and buffer overflows. It also explains cryptography concepts such as encryption algorithms, digital signatures, and how cryptography provides confidentiality, integrity, authentication and non-repudiation. Different types of malware are defined like exploits, worms, rootkits, trojans, adware and spyware along with examples.
1 of 61
Downloaded 10 times


































Ad
Recommended
Party pronto pres new



Party pronto pres newSteven Montgomery
?
PartyPronto is a service that connects party hosts with venues and vendors to plan events. It asks 5 fundamental questions about what goods and services it will provide, how it will produce and deliver them, who the customers will be, how it will adapt to changes, and how it will drive progress. The service takes a 5-7% fee from each booking made through its site, charging both guests and owners, and will generate revenue through ads and homepage promotions to cover its expenses which include development, marketing, employment, utilities, site hosting, IT maintenance, and other costs.Basic Network Security_Primer



Basic Network Security_Primern|u - The Open Security Community
?
This document discusses network security techniques such as authentication and encryption. It provides an overview of 802.1X authentication, which authenticates network clients using unique client information and credentials known only to the client. MAC authentication bypass (MAB) is also discussed, which enables port-based access control using the MAC address of the connecting device. Common encryption techniques are examined, including WEP (outdated), WPA/TKIP, and WPA2/AES. Symmetric key encryption uses a shared secret key for encryption and decryption, while asymmetric encryption uses public/private key pairs.Network Security Tools and applications



Network Security Tools and applicationswebhostingguy
?
The document discusses network security best practices. It covers common network security risks due to issues with the TCP/IP protocol. It then discusses mistakes that users and IT professionals make that compromise security. The document outlines various security best practices for networks, firewalls, intrusion detection systems, and host-level security. These include recommendations around backups, access control, firewall configurations, personal firewalls, and keeping systems patched.Presentation1 new (1) (1)cf



Presentation1 new (1) (1)cftoamma
?
Network security aims to protect networks from unauthorized access, data loss, and viruses. There are two main types of network security: physical security and logical security. Key goals of network security are confidentiality, integrity, and availability of data. While network security safeguards data through encryption, firewalls, and anti-virus software, it also has disadvantages such as cost and potential for a false sense of security.Networksecurity&cryptography



Networksecurity&cryptographyPresentaionslive.blogspot.com
?
The document discusses various aspects of network and computer security. It covers topics like password security guidelines, email security measures using antivirus software, evolving online threats like blended attacks and identity theft. It also explains cryptography concepts like encryption, decryption, conventional and public key cryptography. Security is a shared responsibility and requires cooperation from everyone through intelligent policies and consistent practices.

Contaminacion del aire y de las aguas Jorge Salazar
?
La contaminación de las aguas y el aire se define como una modificación de estos, generalmente provocada por el ser humano, que los vuelve impropios o peligrosos. Cuando hay una cantidad excesiva de ciertas sustancias orgánicas en el agua, su descomposición puede asfixiar la fauna acuática y hacer desaparecer la vida vegetal. En el aire, la presencia de materias o formas de energía que impliquen riesgo pueden da?ar a las personas y bienes. El documento propone combatir esta contaminación aNetwork security & cryptography



Network security & cryptographypinkutinku26
?
The document discusses the importance of securing information in the digital age. It states that information is a valuable asset that needs to be kept confidential from unauthorized access, protected from unauthorized changes, and available when needed. It then defines some key concepts in information security including confidentiality, authentication, integrity, and access/availability. The document goes on to discuss network security and some common threats. It lists components used for network security like antivirus software, firewalls, and intrusion detection systems. Finally, it briefly covers encryption techniques including symmetric key algorithms and asymmetric/public-private key algorithms.Celebrity Cricket League 2016 - http://ccl5.com/ 



Celebrity Cricket League 2016 - http://ccl5.com/ Tania Agni
?
CCL - http://ccl5.com/
Celebrity Cricket League 2016 - http://ccl5.com/
CCL teams - http://ccl5.com/ccl-2016-kits/
Live Stream -http://ccl5.com/ccl-2016-live-score-ball-by-ball-today-match/Rashed al kamdah network security threats



Rashed al kamdah network security threatsrashidalkamdah
?
This document discusses various security threats to networks and proposes solutions. It identifies 10 major network threats according to ITSecurity.com: viruses and worms, Trojan horses, spam, phishing, packet sniffers, maliciously coded websites, password attacks, hardware loss and data fragments, shared computers, and zombie computers/botnets. Each threat is described along with how it could harm a network. Solutions proposed include installing security software like antivirus and firewall programs to protect against these threats. Strong encryption is also recommended to prevent packet sniffing. Cryptography and network security



Cryptography and network securityMahipesh Satija
?
In this project we develop an application for translation of information in any language to Cipher/Encrypted , which otherwise is done by using different software in the present scenario. Our attempt is to overcome the various shortcomings in different software available in the market and develop the best (Encryptor/Decryptor) with most useful algorithms. We explore and implement Tiny Algorith, Neural Algorithm, A hybrid blend Neural and Tiny algorithm, Rijandel Agorithm, Stegnography (for Image and Audio files), Video Encryption and Decryption, and a Chat server for secret Communication oiver the software.
Presentation network security



Presentation network securitycegonsoft1999
?
Network security involves securing a computer network from unauthorized access. A network administrator implements security policies, software, and hardware to protect the network and resources while allowing authorized employee access. Common network security threats include viruses, worms, spyware, identity theft, and denial of service attacks. An effective network security system consists of components like antivirus software, firewalls, intrusion prevention, and VPNs working together to minimize risks.Network security and cryptography



Network security and cryptographyPavithra renu
?
This document discusses network security and cryptography. It begins by defining a network and some common network threats. It then discusses network security goals like avoiding denial of service attacks. The document outlines different cryptography techniques like symmetric and asymmetric key cryptography. Symmetric cryptography uses a shared key while asymmetric uses public and private keys. Specific algorithms like RSA and DES are described. The document proposes combining numerals and alphabets in encryption to increase security. It concludes cryptography can securely hide and transmit data through encryption and decryption.Network and network security



Network and network securityRuchi Gupta
?
This document discusses computer networks and network security. It defines what a network is and its components. It describes the benefits of networks and different network types and topologies. It then defines network security and discusses common security threats. It outlines techniques to secure networks such as firewalls, intrusion detection systems, encryption, and identity services. The document stresses the importance of network security and provides tips to enhance security.Nymble: Blocking System



Nymble: Blocking SystemManzeer Fasaludeen
?
The document describes the Nymble blocking system, which allows websites to selectively blacklist users of anonymizing networks without seeing their IP addresses. It maintains users' anonymity while blocking blacklisted users from future connections. The system architecture includes users, a pseudonym manager, Nymble manager, and servers. It aims to achieve blacklistability, rate-limiting, nonframeability, and anonymity.network security, cryptography,steganography



network security, cryptography,steganographyNikhil l
?
Network security involves protecting computer networks through tools like firewalls, encryption, and digital signatures. Common security threats include TCP hijacking, packet sniffing, and unauthorized access to networks. Cryptography and steganography are methods used to secure communications and information. Cryptography involves encrypting data using techniques like public key infrastructure, while steganography hides secret messages within ordinary files like images or audio files. Both have benefits but also limitations, as strong encryption does not guarantee security if other vulnerabilities exist.Network security - Basic concepts



Network security - Basic conceptsKhoa Nguyen
?
The document discusses various network security techniques including eavesdropping, cryptanalysis, and password pilfering. It also covers common tools and techniques used for denial of service attacks, malicious software, and encryption basics. Specific methods mentioned are social engineering, guessing common passwords, cryptanalysis using math and powerful computers, and types of buffer overflow attacks.Pgp security mule



Pgp security muleSindhu VL
?
This document discusses how to configure Pretty Good Privacy (PGP) security on Mule connectors. PGP provides encryption and authentication for data communication. Key elements needed for PGP include a security manager, key manager, and credential accessor. The security manager holds encryption strategy and key rings. The key manager reads the key rings and requires configuration of public/secret rings, alias ID, and passphrase. The credential accessor determines the key ID to use for encryption/decryption based on message contents. Examples show configuring these elements and using encrypt/decrypt transformers.Pgp smime



Pgp smimeTania Agni
?
PGP and S/MIME are two standards for securing email. PGP uses asymmetric encryption and digital signatures to provide authentication, confidentiality, and compression of messages. It utilizes public/private key pairs and trust is established through signatures on public keys. S/MIME is an Internet standard that provides similar security services to MIME messages as PGP, using PKI/certificates and industry standard algorithms. Both standards encrypt messages and attach digital signatures to authenticate senders and guarantee message integrity.Cryptography and network security



Cryptography and network securityNagendra Um
?
This presentation introduces the Basics of Cryptography and Network Security concepts. Heavily derived from content from William Stalling's book with the same title.key distribution in network security



key distribution in network securitybabak danyal
?
Symmetric encryption uses the same key to encrypt and decrypt data, providing confidentiality. Keys must be distributed securely between parties. Common approaches involve using a key distribution center (KDC) that shares secret keys with parties and can provide temporary session keys. Link encryption protects data as it travels over each network link, while end-to-end encryption protects data for its entire journey but leaves some header data unencrypted. Key distribution, storage, renewal and replacement are important aspects of maintaining security when using symmetric encryption.Network security & cryptography



Network security & cryptographyRahulprasad Yadav
?
This document summarizes a presentation on network security and cryptography. The presentation covers the objectives of security, password auditing, data security, and authentication. It also discusses encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. The presentation includes a demonstration of a public key system and concludes by emphasizing the importance of securing data through cryptography and network security techniques.Email Security Overview



Email Security Overview- Mark - Fullbright
?
Websense offers several email security solutions to address modern threats. Their solutions leverage the Websense ThreatSeeker Intelligence Cloud and Advanced Classification Engine (ACE) to detect known and unknown malware, spam, and targeted attacks. Key capabilities include gateway threat analysis, point-of-click URL sandboxing, behavioral file sandboxing, and built-in data loss prevention. Websense solutions can be deployed in the cloud, on-premises with appliances, or in a hybrid model.S/MIME & E-mail Security (Network Security)



S/MIME & E-mail Security (Network Security)Prafull Johri
?
This document discusses email security and encryption. It explains that email travels through unprotected networks and is exposed to attacks. It describes how email privacy aims to protect email from unauthorized access. Some remedies discussed are encrypting communication between servers using TLS and SASL authentication. The document also discusses using public-key cryptography for email encryption with tools like PGP and S/MIME, which can encrypt email content and add digital signatures for authentication. S/MIME is described as a security enhancement to the MIME email standard that provides encrypted and signed data functionality.Authentication Application in Network Security NS4



Authentication Application in Network Security NS4koolkampus
?
The document summarizes authentication methods including Kerberos and X.509. It outlines security concerns around confidentiality and timeliness. It provides an overview of how Kerberos works, including the authentication dialogue process. It also describes X.509 certificates and certification authorities. Recommended reading and websites on authentication topics are listed.Network security desighn principles and authentication



Network security desighn principles and authenticationEdgar Mwangangi
?
This document discusses network security and principles for data access design. It begins with an introduction to security principles like least privilege, fail-safe defaults, and separation of privilege. It then analyzes systems access and authentication, covering authentication protocols, procedures like two-party authentication, and third-party authentication using Kerberos. The document concludes by identifying phases of penetration testing like profiling, enumeration, vulnerability analysis, and exploitation, with the goal of assessing security and identifying deficiencies.DEF CON 27 - DANIEL ROMERO and MARIO RIVAS - why you should fear your mundane...



DEF CON 27 - DANIEL ROMERO and MARIO RIVAS - why you should fear your mundane...Felipe Prado
?
The document discusses vulnerabilities found in common office equipment like printers. It begins with an introduction explaining the researchers' approach of analyzing the security of enterprise printers from various manufacturers through a red teaming methodology. They found printers pose risks as they sit on corporate networks, process sensitive data, and are often assumed to be low risk. The document then covers the large attack surface printers present, including exposed services, firmware, and hardware issues. It describes common flaws found like weak configurations, default credentials, and memory corruption issues. Finally, it provides an example of exploiting a stack buffer overflow vulnerability to achieve remote code execution on a printer.Event - Internet Thailand - Total Security Perimeters



Event - Internet Thailand - Total Security PerimetersSomyos U.
?
This document summarizes Symantec's enterprise security solutions, including vulnerability management, firewalls, intrusion detection, virus protection, and managed security services. It discusses why security is important for businesses, common security threats, and how Symantec's layered approach addresses these threats through technologies like firewalls, VPNs, antivirus software, and vulnerability scanning.Web Application Security



Web Application SecurityAbdul Wahid
?
The document summarizes key points about web application security vulnerabilities and how to address them. It discusses common vulnerabilities like parameter manipulation, cross-site scripting, and SQL injection that occur due to improper validation of user input. It emphasizes the importance of validating all user input on the server-side to prevent attacks, and not storing sensitive values in cookies or hidden form fields that can be manipulated by attackers.[CB20] Operation I am Tom: How APT actors move laterally in corporate network...![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
[CB20] Operation I am Tom: How APT actors move laterally in corporate network...CODE BLUE
?
This document discusses techniques used by threat actors to move laterally within corporate networks. It begins with an introduction and covers post-exploitation techniques including Mimikatz for credential theft, Skeleton Key and Wdigest for password dumping, webshell deployment on IIS and Exchange servers, and other miscellaneous techniques such as abusing VPNs and using rootkits. Precautions are provided for each technique discussed.Proxy Servers & Firewalls



Proxy Servers & FirewallsMehdi Poustchi Amin
?
Proxy servers and firewalls both act as gateways between internal networks and external networks like the internet. Proxy servers improve performance by caching frequently requested content, control bandwidth usage, and filter requests. Firewalls protect internal networks from external threats by packet filtering, analyzing packets, providing proxy services, and logging and alerting administrators of potential threats. Popular proxy software includes Squid, ISA Server, and WinRoute, while popular firewall software includes ISA Server, Cisco PIX, Norton Internet Security, and ZoneAlarm.Ad
More Related Content
Viewers also liked (17)
Rashed al kamdah network security threats



Rashed al kamdah network security threatsrashidalkamdah
?
This document discusses various security threats to networks and proposes solutions. It identifies 10 major network threats according to ITSecurity.com: viruses and worms, Trojan horses, spam, phishing, packet sniffers, maliciously coded websites, password attacks, hardware loss and data fragments, shared computers, and zombie computers/botnets. Each threat is described along with how it could harm a network. Solutions proposed include installing security software like antivirus and firewall programs to protect against these threats. Strong encryption is also recommended to prevent packet sniffing. Cryptography and network security



Cryptography and network securityMahipesh Satija
?
In this project we develop an application for translation of information in any language to Cipher/Encrypted , which otherwise is done by using different software in the present scenario. Our attempt is to overcome the various shortcomings in different software available in the market and develop the best (Encryptor/Decryptor) with most useful algorithms. We explore and implement Tiny Algorith, Neural Algorithm, A hybrid blend Neural and Tiny algorithm, Rijandel Agorithm, Stegnography (for Image and Audio files), Video Encryption and Decryption, and a Chat server for secret Communication oiver the software.
Presentation network security



Presentation network securitycegonsoft1999
?
Network security involves securing a computer network from unauthorized access. A network administrator implements security policies, software, and hardware to protect the network and resources while allowing authorized employee access. Common network security threats include viruses, worms, spyware, identity theft, and denial of service attacks. An effective network security system consists of components like antivirus software, firewalls, intrusion prevention, and VPNs working together to minimize risks.Network security and cryptography



Network security and cryptographyPavithra renu
?
This document discusses network security and cryptography. It begins by defining a network and some common network threats. It then discusses network security goals like avoiding denial of service attacks. The document outlines different cryptography techniques like symmetric and asymmetric key cryptography. Symmetric cryptography uses a shared key while asymmetric uses public and private keys. Specific algorithms like RSA and DES are described. The document proposes combining numerals and alphabets in encryption to increase security. It concludes cryptography can securely hide and transmit data through encryption and decryption.Network and network security



Network and network securityRuchi Gupta
?
This document discusses computer networks and network security. It defines what a network is and its components. It describes the benefits of networks and different network types and topologies. It then defines network security and discusses common security threats. It outlines techniques to secure networks such as firewalls, intrusion detection systems, encryption, and identity services. The document stresses the importance of network security and provides tips to enhance security.Nymble: Blocking System



Nymble: Blocking SystemManzeer Fasaludeen
?
The document describes the Nymble blocking system, which allows websites to selectively blacklist users of anonymizing networks without seeing their IP addresses. It maintains users' anonymity while blocking blacklisted users from future connections. The system architecture includes users, a pseudonym manager, Nymble manager, and servers. It aims to achieve blacklistability, rate-limiting, nonframeability, and anonymity.network security, cryptography,steganography



network security, cryptography,steganographyNikhil l
?
Network security involves protecting computer networks through tools like firewalls, encryption, and digital signatures. Common security threats include TCP hijacking, packet sniffing, and unauthorized access to networks. Cryptography and steganography are methods used to secure communications and information. Cryptography involves encrypting data using techniques like public key infrastructure, while steganography hides secret messages within ordinary files like images or audio files. Both have benefits but also limitations, as strong encryption does not guarantee security if other vulnerabilities exist.Network security - Basic concepts



Network security - Basic conceptsKhoa Nguyen
?
The document discusses various network security techniques including eavesdropping, cryptanalysis, and password pilfering. It also covers common tools and techniques used for denial of service attacks, malicious software, and encryption basics. Specific methods mentioned are social engineering, guessing common passwords, cryptanalysis using math and powerful computers, and types of buffer overflow attacks.Pgp security mule



Pgp security muleSindhu VL
?
This document discusses how to configure Pretty Good Privacy (PGP) security on Mule connectors. PGP provides encryption and authentication for data communication. Key elements needed for PGP include a security manager, key manager, and credential accessor. The security manager holds encryption strategy and key rings. The key manager reads the key rings and requires configuration of public/secret rings, alias ID, and passphrase. The credential accessor determines the key ID to use for encryption/decryption based on message contents. Examples show configuring these elements and using encrypt/decrypt transformers.Pgp smime



Pgp smimeTania Agni
?
PGP and S/MIME are two standards for securing email. PGP uses asymmetric encryption and digital signatures to provide authentication, confidentiality, and compression of messages. It utilizes public/private key pairs and trust is established through signatures on public keys. S/MIME is an Internet standard that provides similar security services to MIME messages as PGP, using PKI/certificates and industry standard algorithms. Both standards encrypt messages and attach digital signatures to authenticate senders and guarantee message integrity.Cryptography and network security



Cryptography and network securityNagendra Um
?
This presentation introduces the Basics of Cryptography and Network Security concepts. Heavily derived from content from William Stalling's book with the same title.key distribution in network security



key distribution in network securitybabak danyal
?
Symmetric encryption uses the same key to encrypt and decrypt data, providing confidentiality. Keys must be distributed securely between parties. Common approaches involve using a key distribution center (KDC) that shares secret keys with parties and can provide temporary session keys. Link encryption protects data as it travels over each network link, while end-to-end encryption protects data for its entire journey but leaves some header data unencrypted. Key distribution, storage, renewal and replacement are important aspects of maintaining security when using symmetric encryption.Network security & cryptography



Network security & cryptographyRahulprasad Yadav
?
This document summarizes a presentation on network security and cryptography. The presentation covers the objectives of security, password auditing, data security, and authentication. It also discusses encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. The presentation includes a demonstration of a public key system and concludes by emphasizing the importance of securing data through cryptography and network security techniques.Email Security Overview



Email Security Overview- Mark - Fullbright
?
Websense offers several email security solutions to address modern threats. Their solutions leverage the Websense ThreatSeeker Intelligence Cloud and Advanced Classification Engine (ACE) to detect known and unknown malware, spam, and targeted attacks. Key capabilities include gateway threat analysis, point-of-click URL sandboxing, behavioral file sandboxing, and built-in data loss prevention. Websense solutions can be deployed in the cloud, on-premises with appliances, or in a hybrid model.S/MIME & E-mail Security (Network Security)



S/MIME & E-mail Security (Network Security)Prafull Johri
?
This document discusses email security and encryption. It explains that email travels through unprotected networks and is exposed to attacks. It describes how email privacy aims to protect email from unauthorized access. Some remedies discussed are encrypting communication between servers using TLS and SASL authentication. The document also discusses using public-key cryptography for email encryption with tools like PGP and S/MIME, which can encrypt email content and add digital signatures for authentication. S/MIME is described as a security enhancement to the MIME email standard that provides encrypted and signed data functionality.Authentication Application in Network Security NS4



Authentication Application in Network Security NS4koolkampus
?
The document summarizes authentication methods including Kerberos and X.509. It outlines security concerns around confidentiality and timeliness. It provides an overview of how Kerberos works, including the authentication dialogue process. It also describes X.509 certificates and certification authorities. Recommended reading and websites on authentication topics are listed.Network security desighn principles and authentication



Network security desighn principles and authenticationEdgar Mwangangi
?
This document discusses network security and principles for data access design. It begins with an introduction to security principles like least privilege, fail-safe defaults, and separation of privilege. It then analyzes systems access and authentication, covering authentication protocols, procedures like two-party authentication, and third-party authentication using Kerberos. The document concludes by identifying phases of penetration testing like profiling, enumeration, vulnerability analysis, and exploitation, with the goal of assessing security and identifying deficiencies.Similar to E securty (20)
DEF CON 27 - DANIEL ROMERO and MARIO RIVAS - why you should fear your mundane...



DEF CON 27 - DANIEL ROMERO and MARIO RIVAS - why you should fear your mundane...Felipe Prado
?
The document discusses vulnerabilities found in common office equipment like printers. It begins with an introduction explaining the researchers' approach of analyzing the security of enterprise printers from various manufacturers through a red teaming methodology. They found printers pose risks as they sit on corporate networks, process sensitive data, and are often assumed to be low risk. The document then covers the large attack surface printers present, including exposed services, firmware, and hardware issues. It describes common flaws found like weak configurations, default credentials, and memory corruption issues. Finally, it provides an example of exploiting a stack buffer overflow vulnerability to achieve remote code execution on a printer.Event - Internet Thailand - Total Security Perimeters



Event - Internet Thailand - Total Security PerimetersSomyos U.
?
This document summarizes Symantec's enterprise security solutions, including vulnerability management, firewalls, intrusion detection, virus protection, and managed security services. It discusses why security is important for businesses, common security threats, and how Symantec's layered approach addresses these threats through technologies like firewalls, VPNs, antivirus software, and vulnerability scanning.Web Application Security



Web Application SecurityAbdul Wahid
?
The document summarizes key points about web application security vulnerabilities and how to address them. It discusses common vulnerabilities like parameter manipulation, cross-site scripting, and SQL injection that occur due to improper validation of user input. It emphasizes the importance of validating all user input on the server-side to prevent attacks, and not storing sensitive values in cookies or hidden form fields that can be manipulated by attackers.[CB20] Operation I am Tom: How APT actors move laterally in corporate network...![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
[CB20] Operation I am Tom: How APT actors move laterally in corporate network...CODE BLUE
?
This document discusses techniques used by threat actors to move laterally within corporate networks. It begins with an introduction and covers post-exploitation techniques including Mimikatz for credential theft, Skeleton Key and Wdigest for password dumping, webshell deployment on IIS and Exchange servers, and other miscellaneous techniques such as abusing VPNs and using rootkits. Precautions are provided for each technique discussed.Proxy Servers & Firewalls



Proxy Servers & FirewallsMehdi Poustchi Amin
?
Proxy servers and firewalls both act as gateways between internal networks and external networks like the internet. Proxy servers improve performance by caching frequently requested content, control bandwidth usage, and filter requests. Firewalls protect internal networks from external threats by packet filtering, analyzing packets, providing proxy services, and logging and alerting administrators of potential threats. Popular proxy software includes Squid, ISA Server, and WinRoute, while popular firewall software includes ISA Server, Cisco PIX, Norton Internet Security, and ZoneAlarm.Hacking



HackingSUNY Oneonta
?
The document discusses various cybercrime topics including viruses, hacking, denial of service attacks, and privacy concerns regarding technologies like RFID and GPS. It provides examples of how viruses, worms, and Trojan horses work to infect computers. It also explains common hacking techniques like password guessing, port scanning, and wireless network attacks. The document warns that both individuals and large organizations are at risk of cybercrimes.Internets Manage Communication Procedure and Protection that Crash on Servers



Internets Manage Communication Procedure and Protection that Crash on ServersIRJET Journal
?
This document summarizes a research study that evaluated the performance of the Windows Server and Mac OS X Server operating systems when subjected to different types of ICMP-based denial-of-service attacks. The attacks tested were ping floods and Smurf attacks. Both servers were installed on the same Apple Mac Pro hardware platform to isolate the effects of the operating systems. The Windows Server was able to handle more legitimate HTTP connections than the Mac OS X Server under ping flood attacks, but crashed at a much lower bandwidth of Smurf attack traffic (150 Mbps) compared to the Mac OS X Server (500 Mbps). The study concludes that while Windows Server performed better against ping floods, its built-in protections were less effective against Smurf attacksWeb TEchnology hackers Encryption VPN Firewall Unit 5.doc



Web TEchnology hackers Encryption VPN Firewall Unit 5.docuthayashangar1
?
Web Technology hackers Encryption VPN Firewall Unit 5.docProxy servers-firewalls



Proxy servers-firewallsAli Asgar Patanwala
?
Proxy servers and firewalls act as intermediaries between internal networks and external networks like the internet. Proxy servers can cache content to improve performance, control bandwidth usage, and filter requests. Firewalls protect internal networks from external threats by analyzing and filtering incoming and outgoing packets. Popular proxy software includes Squid, ISA Server, and WinRoute, while popular firewall software includes ZoneAlarm, Norton Internet Security, and Cisco PIX.Lecture about network and host security to NII students



Lecture about network and host security to NII studentsAkiumi Hasegawa
?
The document discusses securing IT environments and provides an overview of key topics in IT security. It begins with an anecdote from the author about receiving an email on New Year's Eve 1999 regarding attacks originating from their university network. The document then covers agendas items like keywords in security including CIA and AAA. Current security trends from the Ministry of Internal Affairs and Communication are examined, along with malware trends and the top 10 security threats. The document concludes with remarks on how to avoid malware infections through software updates, anti-malware software, firewalls, and safe email practices.FMS Administration Seminar



FMS Administration SeminarYoss Cohen
?
This document provides an overview of Flash Media Server, including what it is, its versions and types, how to configure applications and streams, and how to install and set up the server. It discusses topics like RTMP, shared objects, NetStream connections, and database integration. Code examples are provided for connecting to the server and playing streams.Malware Analysis Made Simple



Malware Analysis Made SimplePaul Melson
?
Malware analysis is important for responding quickly to security incidents and keeping costs down. Malware is the number one external threat and is adapting to evade traditional defenses like firewalls and antivirus software. When incidents do occur, organizations should have an in-house capability to analyze malware using free and open-source tools to understand the scope of infections and prevent recurrences.Lecture7-8-Network Protocls attack in cyber.ppt



Lecture7-8-Network Protocls attack in cyber.pptMuhammadSaleemKhan26
?
These slides are about the network protocols and attacks in cyber spaceCracking Into Embedded Devices - HACK.LU 2K8



Cracking Into Embedded Devices - HACK.LU 2K8guest441c58b71
?
The document discusses offensive techniques for compromising embedded devices, focusing on exploiting vulnerabilities in HTTP, UPnP, SNMP, and Wi-Fi to gain remote access. Many examples are provided of specific devices that were compromised through bugs like cross-site request forgery, privilege escalation flaws, and password leaks. The goal of the research is to show how embedded devices are easier to hack than general purpose systems and can be used as stepping stones into internal corporate networks.Sembang2 Keselamatan It 2004



Sembang2 Keselamatan It 2004Linuxmalaysia Malaysia
?
The document discusses various cybersecurity threats and exploitation techniques. It introduces vulnerability scanning tools like Nessus and Nikto that can identify security weaknesses. It also discusses methods for exploiting vulnerabilities, including through SQL injection, Perl/CGI issues, and cross-site scripting (XSS) attacks. The document promotes finding and sharing hacking tricks and exploits from security conferences and communities.Information security & ethical hacking



Information security & ethical hackingeiti panchkula
?
This document discusses information security and ethical hacking. It provides an overview of common security threats like viruses, worms, Trojan horses, and keyloggers. It then demonstrates how to conduct various hacking techniques like cracking passwords, creating viruses, exploiting SQL injection vulnerabilities, and performing phishing attacks. The document encourages learning these hacking methods but also provides some tips for security like using antivirus software and firewalls, as well as how to identify phishing emails and attacks.Layer 7 Technologies: Web Services Hacking And Hardening



Layer 7 Technologies: Web Services Hacking And HardeningCA API Management
?
Adam Vincent, Layer 7 Federal Technical Director looks at concepts and tools used for Web services securityWifi Security, or Descending into Depression and Drink



Wifi Security, or Descending into Depression and DrinkSecurityTube.Net
?
This document discusses various techniques for exploiting weaknesses in WiFi security to intercept and manipulate web traffic. It describes how unencrypted management frames and shared wireless media allow spoofing access points and intercepting sessions. With tools like LORCON, attackers can inject packets to hijack TCP streams and manipulate browsers by rewriting HTML, JavaScript and redirecting HTTPS to HTTP. Persistent attacks are also possible by caching manipulated content for long periods.Hacking and its Defence



Hacking and its DefenceGreater Noida Institute Of Technology
?
This document discusses hacking and methods for defending against it. It provides background on common hacking techniques like smurfing and spoofing. It also lists estimated costs of major computer worms and viruses. The document demonstrates hacking methodology, including gathering target information, identifying services, exploiting vulnerabilities, and preventing attacks. It recommends defenses like firewalls, intrusion detection systems, and keeping software patched.Hacking and Computer Forensics



Hacking and Computer ForensicsKristian Arjianto
?
The document summarizes hacking techniques used by hackers:
1) Hackers perform reconnaissance like scanning public information, networks, and systems to find vulnerabilities.
2) This allows them to gain initial access, often by exploiting configuration or software errors.
3) They then use this initial access to get further system privileges or access additional machines.Ad
Recently uploaded (15)
Cloud-to-cloud Migration presentation.pptx



Cloud-to-cloud Migration presentation.pptxmarketing140789
?
What Is Cloud-to-Cloud Migration?
Moving workloads, data, and services from one cloud provider to another (e.g., AWS → Azure).
Common in multi-cloud strategies, M&A, or cost optimization efforts.
Key Challenges
Data integrity & security
Downtime or service interruption
Compatibility of services & APIs
Managing hybrid environments
Compliance during migrationDEF CON 25 - Whitney-Merrill-and-Terrell-McSweeny-Tick-Tick-Boom-Tech-and-the...



DEF CON 25 - Whitney-Merrill-and-Terrell-McSweeny-Tick-Tick-Boom-Tech-and-the...werhkr1
?
cybersecurity defconPresentation Mehdi Monitorama 2022 Cancer and Monitoring



Presentation Mehdi Monitorama 2022 Cancer and Monitoringmdaoudi
?
What observability can learn from medicine: why diagnosing complex systems takes more than one tool—and how to think like an engineer and a doctor.
What do a doctor and an SRE have in common? A diagnostic mindset.
Here’s how medicine can teach us to better understand and care for complex systems. CompTIA-Security-Study-Guide-with-over-500-Practice-Test-Questions-Exam-SY0-7...



CompTIA-Security-Study-Guide-with-over-500-Practice-Test-Questions-Exam-SY0-7...emestica1
?
guia security +How to Install & Activate ListGrabber - eGrabber



How to Install & Activate ListGrabber - eGrabbereGrabber
?
ListGrabber: Build Targeted Lists Online in Minutes美国文凭明尼苏达大学莫里斯分校毕业证范本鲍惭惭学位证书



美国文凭明尼苏达大学莫里斯分校毕业证范本鲍惭惭学位证书Taqyea
?
保密服务明尼苏达大学莫里斯分校英文毕业证书影本美国成绩单明尼苏达大学莫里斯分校文凭【q微1954292140】办理明尼苏达大学莫里斯分校学位证(UMM毕业证书)原版高仿成绩单【q微1954292140】帮您解决在美国明尼苏达大学莫里斯分校未毕业难题(University of Minnesota, Morris)文凭购买、毕业证购买、大学文凭购买、大学毕业证购买、买文凭、日韩文凭、英国大学文凭、美国大学文凭、澳洲大学文凭、加拿大大学文凭(q微1954292140)新加坡大学文凭、新西兰大学文凭、爱尔兰文凭、西班牙文凭、德国文凭、教育部认证,买毕业证,毕业证购买,买大学文凭,购买日韩毕业证、英国大学毕业证、美国大学毕业证、澳洲大学毕业证、加拿大大学毕业证(q微1954292140)新加坡大学毕业证、新西兰大学毕业证、爱尔兰毕业证、西班牙毕业证、德国毕业证,回国证明,留信网认证,留信认证办理,学历认证。从而完成就业。明尼苏达大学莫里斯分校毕业证办理,明尼苏达大学莫里斯分校文凭办理,明尼苏达大学莫里斯分校成绩单办理和真实留信认证、留服认证、明尼苏达大学莫里斯分校学历认证。学院文凭定制,明尼苏达大学莫里斯分校原版文凭补办,扫描件文凭定做,100%文凭复刻。
特殊原因导致无法毕业,也可以联系我们帮您办理相关材料:
1:在明尼苏达大学莫里斯分校挂科了,不想读了,成绩不理想怎么办???
2:打算回国了,找工作的时候,需要提供认证《UMM成绩单购买办理明尼苏达大学莫里斯分校毕业证书范本》【Q/WeChat:1954292140】Buy University of Minnesota, Morris Diploma《正式成绩单论文没过》有文凭却得不到认证。又该怎么办???美国毕业证购买,美国文凭购买,【q微1954292140】美国文凭购买,美国文凭定制,美国文凭补办。专业在线定制美国大学文凭,定做美国本科文凭,【q微1954292140】复制美国University of Minnesota, Morris completion letter。在线快速补办美国本科毕业证、硕士文凭证书,购买美国学位证、明尼苏达大学莫里斯分校Offer,美国大学文凭在线购买。
美国文凭明尼苏达大学莫里斯分校成绩单,UMM毕业证【q微1954292140】办理美国明尼苏达大学莫里斯分校毕业证(UMM毕业证书)【q微1954292140】成绩单COPY明尼苏达大学莫里斯分校offer/学位证国外文凭办理、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决明尼苏达大学莫里斯分校学历学位认证难题。
主营项目:
1、真实教育部国外学历学位认证《美国毕业文凭证书快速办理明尼苏达大学莫里斯分校修改成绩单分数电子版》【q微1954292140】《论文没过明尼苏达大学莫里斯分校正式成绩单》,教育部存档,教育部留服网站100%可查.
2、办理UMM毕业证,改成绩单《UMM毕业证明办理明尼苏达大学莫里斯分校毕业证样本》【Q/WeChat:1954292140】Buy University of Minnesota, Morris Certificates《正式成绩单论文没过》,明尼苏达大学莫里斯分校Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
3、真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
4、留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
《明尼苏达大学莫里斯分校国外学历认证美国毕业证书办理UMM100%文凭复刻》【q微1954292140】学位证1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。
高仿真还原美国文凭证书和外壳,定制美国明尼苏达大学莫里斯分校成绩单和信封。成绩单办理UMM毕业证【q微1954292140】办理美国明尼苏达大学莫里斯分校毕业证(UMM毕业证书)【q微1954292140】做一个在线本科文凭明尼苏达大学莫里斯分校offer/学位证研究生文凭、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决明尼苏达大学莫里斯分校学历学位认证难题。
明尼苏达大学莫里斯分校offer/学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作【q微1954292140】Buy University of Minnesota, Morris Diploma购买美国毕业证,购买英国毕业证,购买澳洲毕业证,购买加拿大毕业证,以及德国毕业证,购买法国毕业证(q微1954292140)购买荷兰毕业证、购买瑞士毕业证、购买日本毕业证、购买韩国毕业证、购买新西兰毕业证、购买新加坡毕业证、购买西班牙毕业证、购买马来西亚毕业证等。包括了本科毕业证,硕士毕业证。GiacomoVacca - WebRTC - troubleshooting media negotiation.pdf



GiacomoVacca - WebRTC - troubleshooting media negotiation.pdfGiacomo Vacca
?
Presented at Kamailio World 2025.
Establishing WebRTC sessions reliably and quickly, and maintaining good media quality throughout a session, are ongoing challenges for service providers. This presentation dives into the details of session negotiation and media setup, with a focus on troubleshooting techniques and diagnostic tools. Special attention will be given to scenarios involving FreeSWITCH as the media server and Kamailio as the signalling proxy, highlighting common pitfalls and practical solutions drawn from real-world deployments.Breaking Down the Latest Spectrum Internet Plans.pdf



Breaking Down the Latest Spectrum Internet Plans.pdfInternet Bundle Now
?
Explore updated Spectrum Internet Plans with expert guidance, your trusted Internet Service Provider reliable Spectrum Customer Service.IoT PPT introduction to internet of things



IoT PPT introduction to internet of thingsVaishnaviPatil3995
?
IoT PPT introduction to internet of things学生卡英国搁颁础毕业证皇家艺术学院电子毕业证学历证书



学生卡英国搁颁础毕业证皇家艺术学院电子毕业证学历证书Taqyea
?
保密服务皇家艺术学院英文毕业证书影本英国成绩单皇家艺术学院文凭【q微1954292140】办理皇家艺术学院学位证(RCA毕业证书)假学历认证【q微1954292140】帮您解决在英国皇家艺术学院未毕业难题(Royal College of Art)文凭购买、毕业证购买、大学文凭购买、大学毕业证购买、买文凭、日韩文凭、英国大学文凭、美国大学文凭、澳洲大学文凭、加拿大大学文凭(q微1954292140)新加坡大学文凭、新西兰大学文凭、爱尔兰文凭、西班牙文凭、德国文凭、教育部认证,买毕业证,毕业证购买,买大学文凭,购买日韩毕业证、英国大学毕业证、美国大学毕业证、澳洲大学毕业证、加拿大大学毕业证(q微1954292140)新加坡大学毕业证、新西兰大学毕业证、爱尔兰毕业证、西班牙毕业证、德国毕业证,回国证明,留信网认证,留信认证办理,学历认证。从而完成就业。皇家艺术学院毕业证办理,皇家艺术学院文凭办理,皇家艺术学院成绩单办理和真实留信认证、留服认证、皇家艺术学院学历认证。学院文凭定制,皇家艺术学院原版文凭补办,扫描件文凭定做,100%文凭复刻。
特殊原因导致无法毕业,也可以联系我们帮您办理相关材料:
1:在皇家艺术学院挂科了,不想读了,成绩不理想怎么办???
2:打算回国了,找工作的时候,需要提供认证《RCA成绩单购买办理皇家艺术学院毕业证书范本》【Q/WeChat:1954292140】Buy Royal College of Art Diploma《正式成绩单论文没过》有文凭却得不到认证。又该怎么办???英国毕业证购买,英国文凭购买,【q微1954292140】英国文凭购买,英国文凭定制,英国文凭补办。专业在线定制英国大学文凭,定做英国本科文凭,【q微1954292140】复制英国Royal College of Art completion letter。在线快速补办英国本科毕业证、硕士文凭证书,购买英国学位证、皇家艺术学院Offer,英国大学文凭在线购买。
英国文凭皇家艺术学院成绩单,RCA毕业证【q微1954292140】办理英国皇家艺术学院毕业证(RCA毕业证书)【q微1954292140】专业定制国外文凭学历证书皇家艺术学院offer/学位证国外文凭办理、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决皇家艺术学院学历学位认证难题。
主营项目:
1、真实教育部国外学历学位认证《英国毕业文凭证书快速办理皇家艺术学院成绩单英文版》【q微1954292140】《论文没过皇家艺术学院正式成绩单》,教育部存档,教育部留服网站100%可查.
2、办理RCA毕业证,改成绩单《RCA毕业证明办理皇家艺术学院国外文凭办理》【Q/WeChat:1954292140】Buy Royal College of Art Certificates《正式成绩单论文没过》,皇家艺术学院Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
3、真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
4、留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
《皇家艺术学院快速办理毕业证书英国毕业证书办理RCA办学历认证》【q微1954292140】学位证1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。
高仿真还原英国文凭证书和外壳,定制英国皇家艺术学院成绩单和信封。办理学历认证RCA毕业证【q微1954292140】办理英国皇家艺术学院毕业证(RCA毕业证书)【q微1954292140】安全可靠的皇家艺术学院offer/学位证毕业证书不见了怎么办、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决皇家艺术学院学历学位认证难题。
皇家艺术学院offer/学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作【q微1954292140】Buy Royal College of Art Diploma购买美国毕业证,购买英国毕业证,购买澳洲毕业证,购买加拿大毕业证,以及德国毕业证,购买法国毕业证(q微1954292140)购买荷兰毕业证、购买瑞士毕业证、购买日本毕业证、购买韩国毕业证、购买新西兰毕业证、购买新加坡毕业证、购买西班牙毕业证、购买马来西亚毕业证等。包括了本科毕业证,硕士毕业证。Paper: World Game (s) Great Redesign.pdf



Paper: World Game (s) Great Redesign.pdfSteven McGee
?
Paper: The World Game (s) Great Redesign using Eco GDP Economic Epochs for programmable money pdf
Paper: THESIS: All artifacts internet, programmable net of money are formed using:
1) Epoch time cycle intervals ex: created by silicon microchip oscillations
2) Syntax parsed, processed during epoch time cycle intervalsThe Hidden Risks of Hiring Hackers to Change Grades: An Awareness Guide



The Hidden Risks of Hiring Hackers to Change Grades: An Awareness Guiderussellpeter1995
?
The Hidden Risks of Hiring Hackers to Change Grades: An Awareness GuideAd
E securty
- 2. WHAT WILL WE SEE IN THIS LECTURE
- 3. ?Structure of Network System ?Threats and Type of Attacks ?Cryptography ?Analysis of e-security
- 6. Physical Media,Signal and Binary Transmission Data Link Mac and LLC (Phyiscal addressing) Network Path Determination and TCP/IP (Logical addressing) Transport End to End Connections and Reliability Session Interhost Communication Presentation Data Representation and Encryption Application Network Process to Application
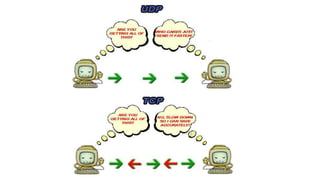
- 8. TCP VS UDP
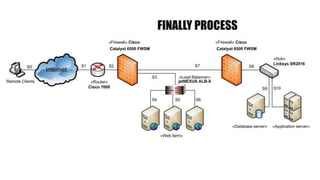
- 10. FINALLY PROCESS
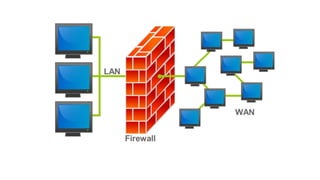
- 11. FIREWALL
- 15. TYPE OF ATTACKS
- 16. ?Passive Attack ?Active Attack ?Insider Attack ?Close-in Attack ?Phishing Attack ?Buffer overflow ?Exploit attack ?Password attack
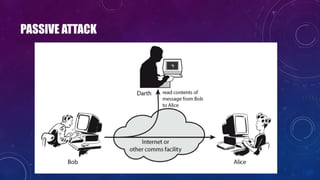
- 17. PASSIVE ATTACK
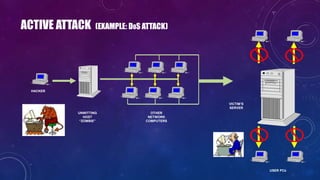
- 18. USER PCs HACKER UNWITTING HOST “ZOMBIE” OTHER NETWORK COMPUTERS VICTIM’S SERVER ACTIVE ATTACK (EXAMPLE: DOS ATTACK)
- 19. INSIDER ATTACK
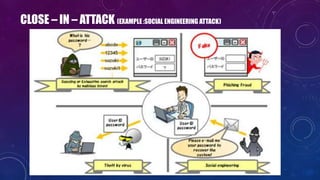
- 20. CLOSE – IN – ATTACK (EXAMPLE :SOCIAL ENGINEERING ATTACK)
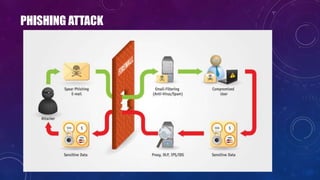
- 21. PHISHING ATTACK
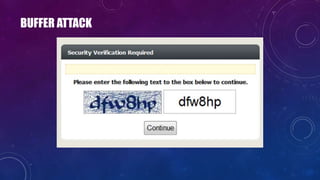
- 22. BUFFER ATTACK
- 23. EXPLOID ATTACK
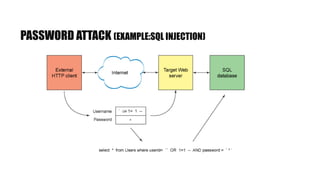
- 24. PASSWORD ATTACK (EXAMPLE:SQL INJECTION)
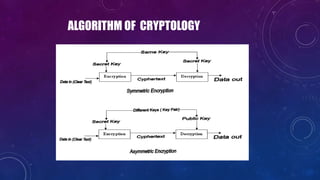
- 25. CRYPTOLOGY
- 26. WHAT IS THE CRYPTOLOGY?
- 29. ENIGMA
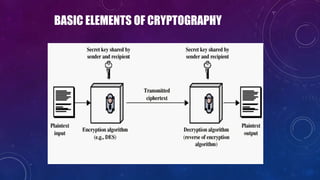
- 30. BASIC ELEMENTS OF CRYPTOGRAPHY
- 31. WHAT PROVIDES CRYPTOGRAPHY? ?Confidentiality ?Message Integrity ?Authentication ?Non-repudiation
- 33. Known Symmetrical Algorithms ?Data Encryption Standard (DES) ?56 bit key ?Triple DES, DESX, GDES, RDES ?168 bit key ?RC2, RC4, RC5 ?variable length up to 2048 bits ?IDEA - basis of PGP ?128 bit key ?Blowfish ?variable length up to 448 bits
- 34. CRYPTOGRAPHIC SERVICES ALLOW ?Digital Signatures ?Certificates (Digital Ids) ?Secure Channels
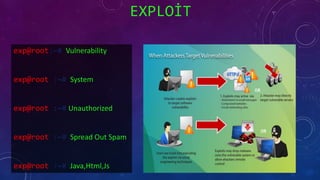
- 37. TYPES OF MALWARE root@root:~# Exploit root@root:~# WORM root@root:~# Rootkit root@root:~# Trojan root@root:~# Adware root@root:~# Spyware
- 38. EXPLO?T exp@root:~# Vulnerability exp@root :~# System exp@root :~# Unauthorized exp@root :~# Spread Out Spam exp@root :~# Java,Html,Js
- 39. EXPLO?T
- 40. WORM wrm@root:~# Auto Clone wrm@root :~# Spread wrm@root :~# Not need attach wrm@root :~# Consume wrm@root :~# Any action user wrm@root :~# Backdoor P2P
- 41. WORM
- 42. WORM #STORM wrm@root :~# 2007 wrm@root :~# attach mail wrm@root :~# wincom32.exe wrm@root :~# services.exe wrm@root :~# P2P #CONF?CKER wrm@root :~# 2008 wrm@root :~# Windows wrm@root :~# Buffer wrm@root :~# 9 billion wrm@root :~# Services #CODERED wrm@root :~# Servers wrm@root :~# 2001 wrm@root :~# IIS wrm@root :~# 359,000 wrm@root :~# Whitehouse
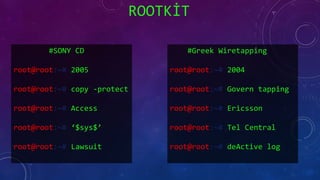
- 43. ROOTK?T root@root:~# System -Hide root@root:~# Response root@root:~# Not -alone root@root:~# Remote root@root:~# Crack -Keygen root@root:~# Use you -Pri
- 44. ROOTK?T #SONY CD root@root:~# 2005 root@root:~# copy -protect root@root:~# Access root@root:~# ‘$sys$’ root@root:~# Lawsuit #Greek Wiretapping root@root:~# 2004 root@root:~# Govern tapping root@root:~# Ericsson root@root:~# Tel Central root@root:~# deActive log
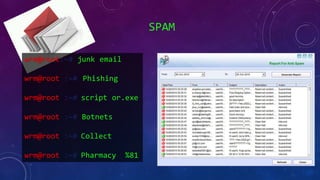
- 45. SPAM wrm@root:~# junk email wrm@root :~# Phishing wrm@root :~# script or.exe wrm@root :~# Botnets wrm@root :~# Collect wrm@root :~# Pharmacy %81
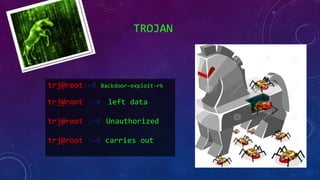
- 46. TROJAN trj@root:~# Backdoor-exploit-rk trj@root :~# left data trj@root :~# Unauthorized trj@root :~# carries out
- 47. ADWARE adw@root :~# Freeware adw@root :~# keylogger adw@root :~# Pop -up adw@root :~# Tracks adw@root :~# Related adw@root :~# Consume
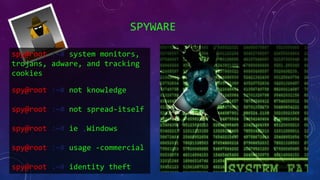
- 48. SPYWARE spy@root :~# system monitors, trojans, adware, and tracking cookies spy@root :~# not knowledge spy@root :~# not spread-itself spy@root :~# ie ,Windows spy@root :~# usage -commercial spy@root :~# identity theft
- 49. SPYWARE spy@root :~# -CoolWebSearch spy@root :~# -huntbar spy@root :~# -movieland spy@root :~# -kazaa
- 51. ?THREAT INTELLIGENCE ?SECURITY CAPABILITIES ?GEOPOLITICAL AND INDUSTRY ?USER AND CORPORATE



