Eap edit
- 1. The EAP Protocol • The EAP protocol is a one sided authentication protocol - the PEER must identify himself to the AUTHENTICATOR. • EAP allows for mutual authentication by running the protocol in both directions.
- 2. (The EAP Protocol (2 • A request-response protocol. • Uses 4 different kinds of messages: 1. EAP request 2. EAP response 3. EAP success 4. EAP failure
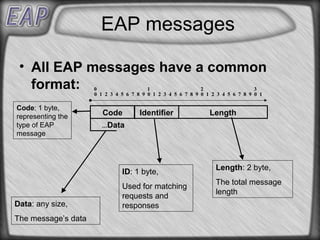
- 3. EAP messages • All EAP messages have a common format: 0 1 2 3 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 Code: 1 byte, representing the Code Identifier Length type of EAP ...Data message Length: 2 byte, ID: 1 byte, The total message Used for matching length requests and Data: any size, responses The message’s data
- 4. EAP messages 2 • EAP request and response messages have the same format , with code=1 for requests and code=2 for responses 0 1 2 3 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 Code Identifier Length Type .Type Data Type: 1 byte, Data: any size, The type of Data used for the authentication protocol authentication process used
- 5. EAP messages 3 • EAP Success messages are EAP messages with code 3 and no data. • A success message means that the authentication concluded successfully. • EAP failure messages are EAP messages with code 4 and no data. • A Failure message means that the authentication has failed.
- 6. The authentication sequence • The Authenticator sends the peer an Identity request (optional(. • The Peer sends a response to the identity request identifying himself (optional(. • The Authenticator sends a request with a type according to which authentication method he wants to use and the data needed for the authentication. • The Peer sends back a response of the same type or of type Nak signifying he refuses to use the requested authentication method.
- 7. The authentication sequence • The Authenticator may at this point send another request (to repeat the process( or a success/failure message. • If the authentication was successful and mutual authentication is required ,the sides change roles and the authentication is repeated in the other direction.
- 8. Notes • All the messages pass on the communication line in plain-text (unless there is a protection mechanism in the link layer below( • The messages are not signed/authenticated at the EAP level although individual EAP methods may MAC/sign/encrypt their data.
- 9. Generic EAP Example Peer Authenticator Identity Request Identity Response EAP Request Repeated as many times as needed EAP Response with the same type or a Nak EAP Success or EAP Failure message Identity Request If mutual Identity Response Auth EAP Request Is required Repeated as needed EAP Response with the same type or a Nak EAP Success or failure message
- 10. Error/duplicate handling • To overcome a possibly unreliable link- layer below, EAP has built in duplicate handling and retransmission facilities. • The authenticator is responsible for all retransmissions , if a response is lost the request will time-out and be resent. • Duplicate handling is done by discarding any unexpected messages.
- 11. Using a Back-End Server • The NAS forwards all the EAP messages it gets to the Back-End server. • The Back-End Server sends all outgoing EAP messages to the peer through the NAS. • If the Back-End server sends a failure message the NAS Sees it and closes the connection, if a success message is sent the NAS knows that the peer passed the authentication.
- 12. Basic EAP Methods • In the initial definition of EAP included several built in authentication methods: •Identity - request the other side to identify itself. •Notification - to send notifications to the other side. •Nak - peer refuses to use the authentication method. •MD5-Challenge - an implementation of chap over EAP. •One Time Password - used for one time passwords. •Generic Token Card - used for generic token cards. •Vendor Specific - *
- 13. Authentication example using MD5 Authenticator Peer Identity Request Code=1 Identifier=I Length=the total length Type=1 = IdentityData …Type Response Code=2 Identifier=I Length=the total length EAP-MD5 Request Type=1 Type Data= peer identity Code=1 Identifier=I Length=the total length Type=4 .EAP – MD5 Response Type Data= the md5 challenge string Code=2 Identifier=I Length=the total length Type=4 (Type Data=hash(I&Secret&md5-challange EAP Success or EAP Failure message Code=3 Identifier=I Length=the total length
- 14. MD5 Security properties • Normal user-names and passwords may be used. • Password is not transmitted exposed, it is protected by the md5 hashing function. • Replay attack protection is done using the challenge field.
- 15. Security weaknesses • The MD5 challenge has serious security problems. • An offline dictionary attack on the user’s password is possible, because the challenge is known. • The protocol is completely exposed to man in the middle and session hijacking attacks. • Mounting a DOS attack is also very simple.
- 16. Are these attacks ? really a problem • Not really, because we are supposed to be working on a SECURE line. • A man in the middle, session hijacking and DOS attacks need access to the physical communication line. • The offline dictionary attack may still be a problem. However, this can be solved.
- 17. Conclusion • It is reasonable to use the MD5-challenge authentication method over a secure line for non-critical data. • It is however completely irresponsible to use EAP for authentication over insecure lines.