Encryption: Fact and Fiction
1 like856 views
Dr. V. Kumar Murty is the CTO of Perfect Cloud Corp. He has extensive experience in information security as a professor at the University of Toronto, with over 100 papers published. The document discusses concepts related to data security including encryption algorithms, identity management, and the importance of both technology and policies for protecting data throughout its lifecycle.
1 of 23
Downloaded 11 times




















Ad
Recommended
Introduction to LavaPasswordFactory
Introduction to LavaPasswordFactoryChristopher Grayson
╠²
The document discusses authentication, emphasizing the significance of identity verification through passwords, security tokens, and biometrics, and outlines common issues with password usage. It highlights the vulnerabilities associated with password-based attacks and introduces the lava.password.factory tool designed for generating and managing passwords for secure authentication. The presentation is delivered by Christopher Grayson, a senior security analyst, who encourages feedback on the ongoing development of the tool.Corporate Espionage without the Hassle of Committing Felonies
Corporate Espionage without the Hassle of Committing FeloniesJohn Bambenek
╠²
The document discusses the challenges of corporate cybersecurity, particularly the imbalance between malware proliferation and the number of analysts available to combat it. It critiques common solutions, like cloud computing and automation, for their limitations and risks, including the misuse of services like VirusTotal that can expose sensitive data. The author emphasizes the importance of cautious data management and the need for appropriate security measures to prevent sensitive information leaks.Cloud storage security
Cloud storage securityPankaj Watekar
╠²
Cloud storage security is important as companies are still afraid to use clouds due to issues like lack of trust, loss of control, and multi-tenancy issues. Some key aspects of cloud storage security include encrypting data at rest and in transit using industry standards for encryption and key management. Researchers are working on authorization, encryption, and segmentation techniques like multi-level authorization, fuzzy vaults, and AES/RSA encryption to improve cloud data security.White-box Cryptography -BayThreat 2013
White-box Cryptography -BayThreat 2013Nick Sullivan
╠²
The document discusses the need for white-box cryptography to protect keys from attackers with physical access to systems. It outlines the threat model of white-box cryptography, its history, and implementation strategies for secure key management, particularly in contexts like digital rights management. An initiative called Open Whitebox aims to develop open-source solutions to make white-box cryptography more accessible.Owasp joy of proactive security
Owasp joy of proactive securityScott Behrens
╠²
The document discusses Netflix's approach to proactive security. It defines proactive security as anticipating and addressing security issues before they become problems through automation, intelligence, and continuous monitoring and improvement. Some key aspects of Netflix's proactive security program include using tools like Monterey to automatically discover and scan assets, the Simian Army to test resiliency, Dirty Laundry to find exposed assets, Security Monkey to monitor AWS changes, and sharing security knowledge and tools through open source projects. The document advocates for simplifying security to encourage developer adoption and continuously reevaluating approaches as environments change.Web Application Security - DevFest + GDay George Town 2016
Web Application Security - DevFest + GDay George Town 2016Gareth Davies
╠²
The document is a presentation by Gareth Davies on web application security, covering fundamental principles of information security, including the CIA triad (confidentiality, integrity, availability) and common best practices. It highlights key do's and don'ts for web applications, stresses the importance of OWASP's top 10 vulnerabilities, and emphasizes the need for secure user authentication and data protection. Additionally, Davies discusses his background in information security and the evolution of his infosec blog and forums.Defcon Crypto Village - OPSEC Concerns in Using Crypto
Defcon Crypto Village - OPSEC Concerns in Using CryptoJohn Bambenek
╠²
The document discusses operational security (opsec) and the pitfalls of using cryptography, emphasizing that not only is it vital to keep secrets, but also to not appear as if one has secrets worth hiding. It highlights various opsec problems with encryption, including the retention of metadata, the risks associated with SSL/TLS certificates, and how poor tech decisions can lead to exposure. Ultimately, it argues that effective opsec requires careful consideration of the adversaries involved and the notion of appearing 'normal' to avoid drawing unnecessary attention.Identity theft- Horowitz Law
Identity theft- Horowitz LawSanford Horowitz
╠²
The document outlines identity theft, explaining how personal information can be used fraudulently without consent, primarily during tax season. It offers advice on protecting oneself, including shredding documents and monitoring credit reports, and details steps to take if one becomes a victim, such as reporting to law enforcement and contacting credit reporting agencies. Additionally, it highlights relevant laws in California regarding identity theft and provides resources for further assistance.Secure Cloud Environment Using RSA Algorithm
Secure Cloud Environment Using RSA AlgorithmIRJET Journal
╠²
This document discusses using the RSA algorithm to provide security in cloud computing environments. It first provides background on cloud computing and discusses some of the security challenges in cloud environments. It then describes how public key cryptography algorithms like RSA can help address some of these security issues by allowing for secure storage and transmission of data through encryption with public/private key pairs. The document goes on to provide an overview of how the RSA algorithm works, including key generation and the encryption/decryption process. It proposes implementing RSA to provide security for data stored in the cloud.Secure File Sharing In Cloud Using Encryption with Digital Signature
Secure File Sharing In Cloud Using Encryption with Digital Signature IJMER
╠²
The document discusses secure file sharing in cloud computing through encryption and digital signatures, emphasizing the need for data confidentiality and integrity. It details the use of the Advanced Encryption Standard (AES) for data encryption, digital signature generation for authentication, and systematic steps for file upload and download processes. The proposed methodology aims to eliminate redundancy and ensure secure transactions in a multi-user environment.SECURE DATA TRANSFER BASED ON CLOUD COMPUTING
SECURE DATA TRANSFER BASED ON CLOUD COMPUTINGIRJET Journal
╠²
This document summarizes a research paper on secure data transfer based on cloud computing. The paper proposes a method to securely store sensitive data on the cloud through encryption. Data owners can encrypt files before uploading them to the cloud. When recipients want to access the encrypted data, data owners can send decryption keys through secure channels. Even if hackers obtain the encrypted data from the cloud, they will be unable to read it without the decryption keys. The proposed method aims to address security and privacy concerns of cloud computing by encrypting data at rest and controlling access through encryption keys.Cloud Cryptography
Cloud Cryptographyijtsrd
╠²
The document discusses the importance of cloud computing and the associated security challenges, particularly focusing on cryptographic techniques for data protection. It highlights various algorithms, such as RSA, AES, and elliptic curve cryptography, as well as the potential vulnerabilities like data breaches and account hijacking. The paper concludes by emphasizing the need for effective security measures to mitigate risks and enhance the benefits of cloud technology.U04503119122
U04503119122IJERA Editor
╠²
The document discusses privacy protection in cloud computing using the RSA algorithm, emphasizing the need for enhanced security measures due to existing vulnerabilities in cloud storage. It outlines an architecture that incorporates RSA for data encryption and an auto-backup policy, aiming to improve user trust in cloud services. The paper also compares different cloud service models and current security mechanisms while highlighting the importance of data integrity, availability, and protection from unauthorized access.A Review on Key-Aggregate Cryptosystem for Climbable Knowledge Sharing in Clo...
A Review on Key-Aggregate Cryptosystem for Climbable Knowledge Sharing in Clo...Editor IJCATR
╠²
The document reviews a key-aggregate cryptosystem designed for secure and efficient data sharing in cloud storage, allowing for the delegation of decryption rights with constant-size ciphertexts while keeping other files confidential. It highlights the importance of cryptography in providing data privacy and integrity amidst rising security concerns in cloud computing. The paper also discusses various encryption techniques, emphasizing the need to securely share encrypted data without compromising user anonymity.Improving Data Storage Security in Cloud using Hadoop
Improving Data Storage Security in Cloud using HadoopIJERA Editor
╠²
The paper discusses improving data storage security in cloud computing by using the Advanced Encryption Standard (AES) encryption method combined with Hadoop's MapReduce framework. It highlights the vulnerabilities of cloud data when transferred and emphasizes encryption as a crucial solution for secure transmission, while also addressing the need for efficient data compression. The findings indicate that the proposed approach effectively enhances data security in the cloud environment, particularly showing that gzip compression outperforms lz4 compression.IRJET- Secure Sharing of Personal Data on Cloud using Key Aggregation and...
IRJET- Secure Sharing of Personal Data on Cloud using Key Aggregation and...IRJET Journal
╠²
This document proposes a method for secure sharing of personal data on cloud storage using key aggregation and cryptography. It discusses how traditional cloud storage raises privacy and security issues due to outsourcing of data. The proposed method uses key-aggregate encryption to encrypt data files and generate a single aggregate key, reducing the need to exchange keys for individual files. This allows data owners to selectively and securely share a large number of encrypted files with data users by distributing the aggregate encryption key. When data users search for files, a trapdoor is generated and sent to the cloud for searching over authorized encrypted files. The method aims to enable secure, efficient and flexible sharing of encrypted personal data on cloud storage.CLOUD SECURITY.pptx
CLOUD SECURITY.pptxMrPrathapG
╠²
The document discusses cloud security architecture and covers the following topics:
1. Governance, risk management, and compliance to maintain effective security.
2. Implementing measures to minimize threats and vulnerabilities like maturity models and risk portfolios.
3. Ensuring proper user access and privileges through identity and access management.
4. Managing threats, vulnerabilities, compliance testing and penetration testing.
5. Securing servers, endpoints, networks and applications.
6. Managing the data lifecycle and protecting data and intellectual property.
7. Developing security policies and standards based on business requirements.IRJET- Secure Data Protection in Cloud Computing
IRJET- Secure Data Protection in Cloud ComputingIRJET Journal
╠²
This document proposes a system to securely store data in the cloud by using honeypot technology and cryptographic algorithms. The proposed system aims to provide better data security for users by only allowing authenticated users to access encrypted data stored in the cloud. If an unauthenticated user attempts to access the data, the system will send them garbage files using honeypot technology to detect unauthorized access attempts. The system uses RSA encryption to encrypt user files before storing them in the cloud, requiring the private key to decrypt files, ensuring only authenticated users can access the encrypted user data stored remotely.Kp3419221926
Kp3419221926IJERA Editor
╠²
The paper discusses the challenges and security issues in cloud computing, particularly focusing on data security and user data protection through various encryption algorithms such as AES, DES, Blowfish, and RSA. It emphasizes the importance of securing data during transfer, storage, and retrieval, and presents a comparative analysis of the discussed algorithms. The findings indicate that AES is the most efficient in execution time, while Blowfish requires the least memory, establishing a framework for enhancing cloud security.Cloud Security 2014 AASNET
Cloud Security 2014 AASNETFarrukh Shahzad
╠²
The document is a comprehensive survey on cloud computing security challenges, practices, and solutions, focusing on the essential characteristics and service models of cloud computing. It discusses security risks, case studies like Amazon AWS, and introduces the Secure Access Controlled File Encryption (SAFE) system for cloud storage. The conclusion highlights the opportunities for research in secure cloud storage and the importance of security measures adopted by major cloud providers.Secure Data Sharing and Search in Cloud Based Data Using Authoritywise Dynami...
Secure Data Sharing and Search in Cloud Based Data Using Authoritywise Dynami...IOSRjournaljce
╠²
This document discusses a new cryptographic approach for secure data sharing in cloud computing, employing a key aggregate cryptosystem that allows for efficient delegation of decryption rights while maintaining data confidentiality. The proposed multi-cloud strategy enhances security and reliability by reducing risks related to service availability and insider threats. The study outlines algorithms for implementing the system and emphasizes the importance of flexible and secure data sharing mechanisms in cloud environments.Enhancing Privacy in Cloud Service Provider Using Cryptographic Algorithm
Enhancing Privacy in Cloud Service Provider Using Cryptographic AlgorithmIOSR Journals
╠²
This document discusses enhancing privacy in cloud service providers using cryptographic algorithms. It proposes using the RSA algorithm to provide data storage security. The RSA algorithm provides important security services like key generation, encryption, and decryption in cloud computing systems. It discusses how RSA works, including generating a public/private key pair, encrypting data with the public key, and decrypting with the private key. This ensures only authorized users can access encrypted data stored in the cloud. The document concludes RSA provides secure storage and management of data in the cloud.Cloud Data Security using Elliptic Curve Cryptography
Cloud Data Security using Elliptic Curve CryptographyIRJET Journal
╠²
This document discusses using elliptic curve cryptography to improve data security in cloud computing. It begins with an abstract that introduces cloud computing and data security as major issues. Then, it provides background on cryptography and classifications of cryptographic algorithms like symmetric, asymmetric, and hash functions. The document also discusses security issues in cloud computing like data isolation, secure data transfer, secure interfaces and access control. It proposes using elliptic curve cryptography to address these issues and provide confidentiality, integrity and authentication for data in the cloud. Overall, the document examines how cryptography can enhance security for data stored in cloud computing environments.IRJET- Ensuring Security in Cloud Computing Cryptography using Cryptography
IRJET- Ensuring Security in Cloud Computing Cryptography using CryptographyIRJET Journal
╠²
This document discusses cryptography techniques for ensuring security in cloud computing. It begins by providing background on cloud computing and noting that privacy and security are key concerns. It then discusses how cryptography can address these concerns through various encryption algorithms. Specifically, it outlines symmetric key algorithms like AES, DES, and 3DES that use a single private key for encryption and decryption. It also briefly mentions asymmetric key algorithms like RSA that use public/private key pairs. The document focuses on how properly implementing cryptography through these algorithms can help secure data storage, transmission, and access in cloud environments.IRJET- Model-Driven Platform for Service Security and Framework for Data ...
IRJET- Model-Driven Platform for Service Security and Framework for Data ...IRJET Journal
╠²
This document proposes a model-driven approach and framework to improve security and privacy for data stored in cloud computing environments. The key aspects of the proposed approach are:
1) A model-driven platform that allows security requirements to be defined at the modeling layer and then transformed into enforceable security configurations.
2) A framework for data security and privacy that uses multi-layer encryption techniques when storing data in the cloud. This is intended to enhance security and privacy for sensitive data.
3) The approach aims to address challenges around access control, insider threats, key management, and metadata privacy in cloud computing. Proper access controls and encryption are seen as important for securing data and services in cloud environments.deep dive down on how NCLA works in IOTs
deep dive down on how NCLA works in IOTsgavrielsembiring
╠²
This document presents a new lightweight cryptographic algorithm designed to enhance data security in cloud computing, utilizing a 16-byte block cipher and a 128-bit key inspired by Feistel and substitution-permutation methods. The proposed algorithm includes features such as flexible key lengths and operational turns, and shows promising experimental results in security levels and encryption efficiency compared to existing systems. It aims to address the growing security challenges faced by cloud computing due to rapid data growth and various external threats.IRJET- Anchoring of Cloud Information under Key Presentation
IRJET- Anchoring of Cloud Information under Key PresentationIRJET Journal
╠²
The document summarizes a research paper on securing cloud data through encryption and distribution of encrypted data across multiple cloud servers. It proposes a method called "Bastion" that generates private and signature keys to restrict access to encrypted data even if an attacker obtains the encryption key. The Bastion method distributes encrypted data blocks across multiple servers so that an attacker would need to compromise all servers to recover the original plaintext data. Experimental results showed Bastion improved security compared to existing schemes and introduced minimal overhead. The conclusion states that Bastion is well-suited for multi-cloud storage environments and enhances data security when encryption keys are obtained by attackers.Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
╠²
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu
╠²
Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.More Related Content
Similar to Encryption: Fact and Fiction (20)
Secure Cloud Environment Using RSA Algorithm
Secure Cloud Environment Using RSA AlgorithmIRJET Journal
╠²
This document discusses using the RSA algorithm to provide security in cloud computing environments. It first provides background on cloud computing and discusses some of the security challenges in cloud environments. It then describes how public key cryptography algorithms like RSA can help address some of these security issues by allowing for secure storage and transmission of data through encryption with public/private key pairs. The document goes on to provide an overview of how the RSA algorithm works, including key generation and the encryption/decryption process. It proposes implementing RSA to provide security for data stored in the cloud.Secure File Sharing In Cloud Using Encryption with Digital Signature
Secure File Sharing In Cloud Using Encryption with Digital Signature IJMER
╠²
The document discusses secure file sharing in cloud computing through encryption and digital signatures, emphasizing the need for data confidentiality and integrity. It details the use of the Advanced Encryption Standard (AES) for data encryption, digital signature generation for authentication, and systematic steps for file upload and download processes. The proposed methodology aims to eliminate redundancy and ensure secure transactions in a multi-user environment.SECURE DATA TRANSFER BASED ON CLOUD COMPUTING
SECURE DATA TRANSFER BASED ON CLOUD COMPUTINGIRJET Journal
╠²
This document summarizes a research paper on secure data transfer based on cloud computing. The paper proposes a method to securely store sensitive data on the cloud through encryption. Data owners can encrypt files before uploading them to the cloud. When recipients want to access the encrypted data, data owners can send decryption keys through secure channels. Even if hackers obtain the encrypted data from the cloud, they will be unable to read it without the decryption keys. The proposed method aims to address security and privacy concerns of cloud computing by encrypting data at rest and controlling access through encryption keys.Cloud Cryptography
Cloud Cryptographyijtsrd
╠²
The document discusses the importance of cloud computing and the associated security challenges, particularly focusing on cryptographic techniques for data protection. It highlights various algorithms, such as RSA, AES, and elliptic curve cryptography, as well as the potential vulnerabilities like data breaches and account hijacking. The paper concludes by emphasizing the need for effective security measures to mitigate risks and enhance the benefits of cloud technology.U04503119122
U04503119122IJERA Editor
╠²
The document discusses privacy protection in cloud computing using the RSA algorithm, emphasizing the need for enhanced security measures due to existing vulnerabilities in cloud storage. It outlines an architecture that incorporates RSA for data encryption and an auto-backup policy, aiming to improve user trust in cloud services. The paper also compares different cloud service models and current security mechanisms while highlighting the importance of data integrity, availability, and protection from unauthorized access.A Review on Key-Aggregate Cryptosystem for Climbable Knowledge Sharing in Clo...
A Review on Key-Aggregate Cryptosystem for Climbable Knowledge Sharing in Clo...Editor IJCATR
╠²
The document reviews a key-aggregate cryptosystem designed for secure and efficient data sharing in cloud storage, allowing for the delegation of decryption rights with constant-size ciphertexts while keeping other files confidential. It highlights the importance of cryptography in providing data privacy and integrity amidst rising security concerns in cloud computing. The paper also discusses various encryption techniques, emphasizing the need to securely share encrypted data without compromising user anonymity.Improving Data Storage Security in Cloud using Hadoop
Improving Data Storage Security in Cloud using HadoopIJERA Editor
╠²
The paper discusses improving data storage security in cloud computing by using the Advanced Encryption Standard (AES) encryption method combined with Hadoop's MapReduce framework. It highlights the vulnerabilities of cloud data when transferred and emphasizes encryption as a crucial solution for secure transmission, while also addressing the need for efficient data compression. The findings indicate that the proposed approach effectively enhances data security in the cloud environment, particularly showing that gzip compression outperforms lz4 compression.IRJET- Secure Sharing of Personal Data on Cloud using Key Aggregation and...
IRJET- Secure Sharing of Personal Data on Cloud using Key Aggregation and...IRJET Journal
╠²
This document proposes a method for secure sharing of personal data on cloud storage using key aggregation and cryptography. It discusses how traditional cloud storage raises privacy and security issues due to outsourcing of data. The proposed method uses key-aggregate encryption to encrypt data files and generate a single aggregate key, reducing the need to exchange keys for individual files. This allows data owners to selectively and securely share a large number of encrypted files with data users by distributing the aggregate encryption key. When data users search for files, a trapdoor is generated and sent to the cloud for searching over authorized encrypted files. The method aims to enable secure, efficient and flexible sharing of encrypted personal data on cloud storage.CLOUD SECURITY.pptx
CLOUD SECURITY.pptxMrPrathapG
╠²
The document discusses cloud security architecture and covers the following topics:
1. Governance, risk management, and compliance to maintain effective security.
2. Implementing measures to minimize threats and vulnerabilities like maturity models and risk portfolios.
3. Ensuring proper user access and privileges through identity and access management.
4. Managing threats, vulnerabilities, compliance testing and penetration testing.
5. Securing servers, endpoints, networks and applications.
6. Managing the data lifecycle and protecting data and intellectual property.
7. Developing security policies and standards based on business requirements.IRJET- Secure Data Protection in Cloud Computing
IRJET- Secure Data Protection in Cloud ComputingIRJET Journal
╠²
This document proposes a system to securely store data in the cloud by using honeypot technology and cryptographic algorithms. The proposed system aims to provide better data security for users by only allowing authenticated users to access encrypted data stored in the cloud. If an unauthenticated user attempts to access the data, the system will send them garbage files using honeypot technology to detect unauthorized access attempts. The system uses RSA encryption to encrypt user files before storing them in the cloud, requiring the private key to decrypt files, ensuring only authenticated users can access the encrypted user data stored remotely.Kp3419221926
Kp3419221926IJERA Editor
╠²
The paper discusses the challenges and security issues in cloud computing, particularly focusing on data security and user data protection through various encryption algorithms such as AES, DES, Blowfish, and RSA. It emphasizes the importance of securing data during transfer, storage, and retrieval, and presents a comparative analysis of the discussed algorithms. The findings indicate that AES is the most efficient in execution time, while Blowfish requires the least memory, establishing a framework for enhancing cloud security.Cloud Security 2014 AASNET
Cloud Security 2014 AASNETFarrukh Shahzad
╠²
The document is a comprehensive survey on cloud computing security challenges, practices, and solutions, focusing on the essential characteristics and service models of cloud computing. It discusses security risks, case studies like Amazon AWS, and introduces the Secure Access Controlled File Encryption (SAFE) system for cloud storage. The conclusion highlights the opportunities for research in secure cloud storage and the importance of security measures adopted by major cloud providers.Secure Data Sharing and Search in Cloud Based Data Using Authoritywise Dynami...
Secure Data Sharing and Search in Cloud Based Data Using Authoritywise Dynami...IOSRjournaljce
╠²
This document discusses a new cryptographic approach for secure data sharing in cloud computing, employing a key aggregate cryptosystem that allows for efficient delegation of decryption rights while maintaining data confidentiality. The proposed multi-cloud strategy enhances security and reliability by reducing risks related to service availability and insider threats. The study outlines algorithms for implementing the system and emphasizes the importance of flexible and secure data sharing mechanisms in cloud environments.Enhancing Privacy in Cloud Service Provider Using Cryptographic Algorithm
Enhancing Privacy in Cloud Service Provider Using Cryptographic AlgorithmIOSR Journals
╠²
This document discusses enhancing privacy in cloud service providers using cryptographic algorithms. It proposes using the RSA algorithm to provide data storage security. The RSA algorithm provides important security services like key generation, encryption, and decryption in cloud computing systems. It discusses how RSA works, including generating a public/private key pair, encrypting data with the public key, and decrypting with the private key. This ensures only authorized users can access encrypted data stored in the cloud. The document concludes RSA provides secure storage and management of data in the cloud.Cloud Data Security using Elliptic Curve Cryptography
Cloud Data Security using Elliptic Curve CryptographyIRJET Journal
╠²
This document discusses using elliptic curve cryptography to improve data security in cloud computing. It begins with an abstract that introduces cloud computing and data security as major issues. Then, it provides background on cryptography and classifications of cryptographic algorithms like symmetric, asymmetric, and hash functions. The document also discusses security issues in cloud computing like data isolation, secure data transfer, secure interfaces and access control. It proposes using elliptic curve cryptography to address these issues and provide confidentiality, integrity and authentication for data in the cloud. Overall, the document examines how cryptography can enhance security for data stored in cloud computing environments.IRJET- Ensuring Security in Cloud Computing Cryptography using Cryptography
IRJET- Ensuring Security in Cloud Computing Cryptography using CryptographyIRJET Journal
╠²
This document discusses cryptography techniques for ensuring security in cloud computing. It begins by providing background on cloud computing and noting that privacy and security are key concerns. It then discusses how cryptography can address these concerns through various encryption algorithms. Specifically, it outlines symmetric key algorithms like AES, DES, and 3DES that use a single private key for encryption and decryption. It also briefly mentions asymmetric key algorithms like RSA that use public/private key pairs. The document focuses on how properly implementing cryptography through these algorithms can help secure data storage, transmission, and access in cloud environments.IRJET- Model-Driven Platform for Service Security and Framework for Data ...
IRJET- Model-Driven Platform for Service Security and Framework for Data ...IRJET Journal
╠²
This document proposes a model-driven approach and framework to improve security and privacy for data stored in cloud computing environments. The key aspects of the proposed approach are:
1) A model-driven platform that allows security requirements to be defined at the modeling layer and then transformed into enforceable security configurations.
2) A framework for data security and privacy that uses multi-layer encryption techniques when storing data in the cloud. This is intended to enhance security and privacy for sensitive data.
3) The approach aims to address challenges around access control, insider threats, key management, and metadata privacy in cloud computing. Proper access controls and encryption are seen as important for securing data and services in cloud environments.deep dive down on how NCLA works in IOTs
deep dive down on how NCLA works in IOTsgavrielsembiring
╠²
This document presents a new lightweight cryptographic algorithm designed to enhance data security in cloud computing, utilizing a 16-byte block cipher and a 128-bit key inspired by Feistel and substitution-permutation methods. The proposed algorithm includes features such as flexible key lengths and operational turns, and shows promising experimental results in security levels and encryption efficiency compared to existing systems. It aims to address the growing security challenges faced by cloud computing due to rapid data growth and various external threats.IRJET- Anchoring of Cloud Information under Key Presentation
IRJET- Anchoring of Cloud Information under Key PresentationIRJET Journal
╠²
The document summarizes a research paper on securing cloud data through encryption and distribution of encrypted data across multiple cloud servers. It proposes a method called "Bastion" that generates private and signature keys to restrict access to encrypted data even if an attacker obtains the encryption key. The Bastion method distributes encrypted data blocks across multiple servers so that an attacker would need to compromise all servers to recover the original plaintext data. Experimental results showed Bastion improved security compared to existing schemes and introduced minimal overhead. The conclusion states that Bastion is well-suited for multi-cloud storage environments and enhances data security when encryption keys are obtained by attackers.Recently uploaded (20)
Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
╠²
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu
╠²
Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science
╠²
As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI╠²- Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI╠²- How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems╠²- How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment╠²- Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether youŌĆÖre modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata
╠²
The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
¤æŗ Introducing Data Contracts: An agreement between data producers and consumers
¤ōØ Data Contracts key components: Understanding a contract and its purpose
¤¦æŌĆŹ¤Ä© Writing your first contract: How to create your own contracts in OpenMetadata
¤”Š An OpenMetadata MCP Server update!
Ō×Ģ And More!Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019
╠²
A presentation at Internetware 2025.MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
╠²
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55
╠²
CurieTech AI in Action ŌĆō Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AIŌĆÖs purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samplesŌĆö95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specificationsŌĆöspeeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10├Ś productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflowŌĆöletting you focus on innovation, not repetition." How to survive with 1 billion vectors and not sell a kidney: our low-cost c...
" How to survive with 1 billion vectors and not sell a kidney: our low-cost c...Fwdays
╠²
Let's talk about our history. How we started the project with a small vector database of less than 2 million records. Later, we received a request for +100 million records, then another +100... And so gradually we reached almost 1 billion. Standard tools were quickly running out of steam - we were running into performance, index size, and very limited resources. After a long series of trials and errors, we built our own low-cost cluster, which today stably processes thousands of queries to more than 1B vectors.AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.Techniques for Automatic Device Identification and Network Assignment.pdf
Techniques for Automatic Device Identification and Network Assignment.pdfPriyanka Aash
╠²
Techniques for Automatic Device Identification and Network AssignmentWebdriverIO & JavaScript: The Perfect Duo for Web Automation
WebdriverIO & JavaScript: The Perfect Duo for Web Automationdigitaljignect
╠²
In todayŌĆÖs dynamic digital landscape, ensuring the quality and dependability of web applications is essential. While Selenium has been a longstanding solution for automating browser tasks, the integration of WebdriverIO (WDIO) with Selenium and JavaScript marks a significant advancement in automation testing. WDIO enhances the testing process by offering a robust interface that improves test creation, execution, and management. This amalgamation capitalizes on the strengths of both tools, leveraging SeleniumŌĆÖs broad browser support and WDIOŌĆÖs modern, efficient approach to test automation. As automation testing becomes increasingly vital for faster development cycles and superior software releases, WDIO emerges as a versatile framework, particularly potent when paired with JavaScript, making it a preferred choice for contemporary testing teams.9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
╠²
Securing Account Lifecycles in the Age of DeepfakesOWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic
╠²
Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2
╠²
ū×ū©ūøū¢ ūóūÖūæūĢūōūÖūØ ū¬ūóū®ūÖūÖū¬ūÖ ūæūóū£ 3/4/5 ū”ūÖū©ūÖūØ, ūóūō 22 ūöūŚū£ūżūĢū¬ ūøū£ūÖūØ ūóūØ ūøū£ ūÉūżū®ū©ūĢūÖūĢū¬ ūöūóūÖūæūĢūō ūöūōū©ūĢū®ūĢū¬.╠²ūæūóū£ ū®ūśūŚ ūóūæūĢūōūö ūÆūōūĢū£ ūĢū×ūŚū®ūæ ūĀūĢūŚ ūĢū¦ū£ ū£ūöūżūóū£ūö ūæū®ūżūö ūöūóūæū©ūÖū¬/ū©ūĢūĪūÖū¬/ūÉūĀūÆū£ūÖū¬/ūĪūżū©ūōūÖū¬/ūóū©ūæūÖū¬ ūĢūóūĢūō..
ū×ūĪūĢūÆū£ ū£ūæū”ūó ūżūóūĢū£ūĢū¬ ūóūÖūæūĢūō ū®ūĢūĀūĢū¬ ūöū×ū¬ūÉūÖū×ūĢū¬ ū£ūóūĀūżūÖūØ ū®ūĢūĀūÖūØ: ū¦ūÖūōūĢūŚ ūÉūĀūøūÖ, ūÉūĢūżū¦ūÖ, ūĀūÖūĪūĢū©, ūĢūøū©ūĪūĢūØ ūÉūĀūøūÖ.Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash
╠²
Lessons Learned from Developing Secure AI WorkflowsAI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software
╠²
In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike.Ad
Encryption: Fact and Fiction
- 1. Dr. V. Kumar Murty CTO, Perfect Cloud Corp. www.perfectcloud.io
- 2. BIOGRAPHY: DR. V. KUMAR MURTY ! ŌĆó CTO, PerfectCloud.io ŌĆó Professor and Chair, Department of Mathematics, University of Toronto ŌĆó Director, GANITA Labs, University of Toronto ŌĆó Ph.D. Harvard University ŌĆó Fellow of the Royal Society of Canada ŌĆó Foreign Fellow of the National Academy of Sciences (India) ŌĆó 100+ papers, 5 books and 2 patents in Information Security CTO, PerfectCloud.io PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 3. SOME ATTRIBUTES OF DATA ŌĆó Confiden;ality ŌĆó Privacy ŌĆó Iden;ty ŌĆó Reliability (Data Integrity) ŌĆó Trust PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
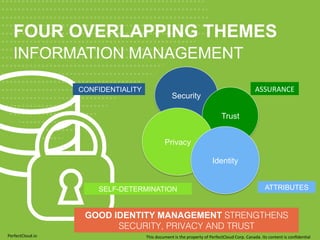
- 4. FOUR OVERLAPPING THEMES INFORMATION MANAGEMENT Security Trust Privacy Identity CONFIDENTIALITY SELF-DETERMINATION ASSURANCE ATTRIBUTES GOOD IDENTITY MANAGEMENT STRENGTHENS SECURITY, PRIVACY AND TRUST! PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 5. PROVISIONING TOOLS ŌĆó Confiden;ality: Encryp;on ŌĆó Privacy: Access Control ŌĆó Iden;ty: IDM ŌĆó Reliability: Digital fingerprints ŌĆó Trust: Digital signatures PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 6. ENCRYPTION ŌĆó Secret wri;ng ŌĆó Symmetric and Asymmetric ŌĆó Plaintext + Secret Key is transformed to Ciphertext ŌĆó Decryp;on: Ciphertext + Secret Key is transformed to Plaintext ŌĆó Our confidence in the security is based on the key being secret ŌĆó Transforma;on = Algorithm: many kinds PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 7. SOME ALGORITHMS ŌĆó Symmetric: ŌĆó AES ŌĆó Blowfish ŌĆó Asymmetric: ŌĆó RSA ŌĆó ECC ŌĆó HEC PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 8. SYMMETRIC ENCRYPTION ŌĆó Used for bulk encryp;on ŌĆó High speed algorithms ŌĆó Requires a shared secret (key) ŌĆó Challenge is in key management PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 9. AES ŌĆó ŌĆ£Government grade encryp;onŌĆØ is a meaningless term ŌĆó Research labs around the world are chipping away at this standard ŌĆó Security and speed depend on the ŌĆ£modeŌĆØ in which it is used. PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 10. ASYMMETRIC ENCRYPTION ŌĆó Does not require a shared secret (key) ŌĆó Encryp;on and Decryp;on keys are (in general) different ŌĆó Methods are mathema;cally sophis;cated ŌĆó Not suitable for bulk encryp;on PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 11. RSA ŌĆó Security depends on the difficulty of factoring large numbers ŌĆó Advances are constantly being made on this, requiring larger and larger key sizes PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its This document is the property of PerfectCloud Corp. Canada. Its conten tc oisn ctoennfit dise cno;nafil den;al
- 12. ECC ŌĆó Ellip;c curve cryptography ŌĆó Considered to be more secure and for comparable size of key: there is no index calculus known for ellip;c curves ŌĆó Included now in NIST standards PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 13. THE KEY IS THE KEY Strength (security) usually depends on several factors including: ŌĆó Size of the key ŌĆó Key management: ŌĆ£key under the doormatŌĆØ ŌĆó Security architecture is only as strong as the weakest link. PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 14. TYPICAL DEPLOYMENT ŌĆó A combina;on of both symmetric and asymmetric methods ŌĆó Security analysis will determine the size of keys needed in each part to make it equally strong throughout PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 15. THREAT MODEL ŌĆó What are we trying to protect against? ŌĆó System architecture diagram has to be analyzed for points of weakness ŌĆó Those points have to be for;fied PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 16. TECHNOLOGY IS NOT ENOUGH ŌĆó Most compromises are not of algorithms but social engineering ŌĆó Security policy is at least as important as security technology: Target ŌĆó Also electro-┬ŁŌĆÉmagne;c a[acks (more difficult to protect against). PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 17. PROTECTING DATA ŌĆó Data has two stages: ŌĆó At rest ŌĆó In transit ŌĆó It has to be secured throughout its ŌĆó lifecycle (ILM) ŌĆó Security architecture depends on ŌĆó Who is managing the data? ŌĆó Where does the data reside? ŌĆó Who has access to the data? ŌĆó Who has access to the keys to the data? ŌĆó What sort of encryption is being used? ŌĆó How is the key being managed/stored? PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 18. ENCRYPTION IN PRACTICE ŌĆó Keeping data safe is more complex in practice ŌĆó Data at rest ŌĆó Encrypted hard drives or directories ŌĆó Data in transit ŌĆó Encrypted data is usually decrypted and re-encrypted at each hop ŌĆó MITM attacks ŌĆó Security of the end devices critical PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 19. SOCIAL NETWORKS ŌĆó Leaks through informa;on voluntarily exposed on social networks ŌĆó Using Twi[er to authen;cate ŌĆó Depends on cloud-┬ŁŌĆÉbased servers PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 20. COMMON ATTACKS ŌĆó SQL Injec;on ŌĆó Malware PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 21. IDENTITY STORES ŌĆó Ac;ve Directory is encrypted: but key is stored in the same place ŌĆó No one can read your encrypted content: some devices that read EM can penetrate it PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
- 22. PERFECT CLOUD SOLUTION ŌĆó True zero knowledge ŌĆó Distributed key management ŌĆó User is in control ŌĆó Seamless and transparent provisioning and de-┬ŁŌĆÉprovisioning PerfectCloud.io This document is the property of PerfectCloud Corp. Canada. Its content is confiden;al
