Ethicalhacking
Download as pptx, pdf0 likes213 views
Ethical hacking provides security benefits to banks and financial institutions by preventing website defacement through evolving techniques that think like criminals. However, it depends on trustworthy ethical hackers who can be expensive to hire professionally. Usage has been increasing over time according to data.
1 of 13
Download to read offline












Recommended
Ethical hacking By- NAGENDRA SAINI
Ethical hacking By- NAGENDRA SAININagendra Saini
╠²
Ethical hacking provides security benefits to banks and financial institutions by preventing website defacement through an evolving technique that requires thinking like a thief to catch one, though it depends on the trustworthiness of the ethical hacker and hiring professionals can be expensive.ETHICAL HACKING PPT
ETHICAL HACKING PPTSweta Leena Panda
╠²
Ethical hacking provides security benefits to banks and financial institutions by preventing website defacement through evolving techniques that think like criminals. However, it depends on trustworthy ethical hackers who can be expensive to hire professionally.EthicalHacking_AakashTakale
EthicalHacking_AakashTakaleAakash Takale
╠²
The document discusses ethical hacking, which involves using the same tools and techniques as hackers but legally and with permission in order to discover vulnerabilities and better secure systems. It defines ethical hacking and the different types of hackers, including black hat, white hat, and grey hat. It describes what ethical hackers do, which is think like hackers to find vulnerabilities from an intruder's perspective. The document also lists required skills for ethical hackers and discusses advantages like providing security versus disadvantages like trust issues. It concludes that regular ethical hacking is needed since no system is completely secure.World health day_2008_15_vulnerability
World health day_2008_15_vulnerabilityravi rajpurohit
╠²
This chapter discusses what makes individuals and populations vulnerable to the health effects of climate change. It defines vulnerability as the degree to which a system is susceptible to and unable to cope with adverse climate impacts. Vulnerability is determined by the characteristics, magnitude and rate of climate change, a population's sensitivity, and its adaptive capacity. Vulnerable groups include the elderly, women, urban residents, and those in nursing homes. Actions can be taken to reduce future health vulnerabilities from climate change.New professional accountability
New professional accountabilityravi rajpurohit
╠²
This document discusses the topic of professional accountability, ethics, and the image of a profession. It is presented by Rajendra Singh, a civil engineering student. The document defines professional accountability as taking responsibility and following through on commitments. It explains that accountability cannot be delegated like responsibility can. Professional accountability comes from being accountable to employers, customers, and the work performed. Maintaining professional accountability involves providing a valuable service, having a defined role, undergoing substantial training, and taking responsibility towards clients, organizations, colleagues, and oneself. The document stresses that professionals must follow ethical conduct as defined for their profession.Jaca05heatw
Jaca05heatwravi rajpurohit
╠²
This document discusses definitions of heat waves and methods for determining heat wave thresholds. It analyzes temperature and mortality data from Zaragoza and Huesca, Spain from 1951-2004. A multi-step process is used to define a threshold temperature T1 based on identifying temperature percentiles associated with mortality excesses across time periods. T1 thresholds increase along summer months from 1975-2002 but remain constant when expressed as percentiles. The defined T1 thresholds generally perform better than an alternative definition for identifying periods of elevated mortality risk.EARTHQUAKE AND TSUNAMI
EARTHQUAKE AND TSUNAMIravi rajpurohit
╠²
This document discusses the 2011 earthquake and tsunami that struck Japan. It began with definitions of disaster and descriptions of different types of natural and man-made disasters. It then provides details of the March 11, 2011 Tohoku earthquake off the coast of Japan that triggered massive tsunami waves up to 133 feet high, causing over 15,000 deaths. The tsunami damaged over 125,000 buildings and caused radiation contamination from affected nuclear power plants, resulting in long-term environmental damage. The response efforts included search and rescue operations, food and medical aid, shelter, and rebuilding infrastructure.10.15 -saudamini_das
10.15 -saudamini_dasravi rajpurohit
╠²
This document summarizes a study on the effectiveness of an awareness program in reducing deaths from heat waves in India. The study found that districts that participated in the Disaster Risk Management (DRM) program's intensive awareness campaign on heat wave dos and don'ts experienced fewer heat wave deaths compared to districts without the program, even during severe heat waves. A difference-in-differences analysis estimated the awareness campaign averted around 170 deaths in the DRM districts. Additionally, the use of multiple media outlets and grassroots programs together in the DRM districts was found to further reduce deaths compared to either approach alone. However, the results require validation with more detailed mortality, awareness exposure, and heat wave response data.Ethics1
Ethics1ravi rajpurohit
╠²
This document discusses ethics and is about a student with roll number 41 studying civil engineering under guidance from Maa'm Ruma Bhaduriya. It covers meta ethics, normative ethics, and applied ethics. It also lists providing care, education, safety, and a good environment.2002 indian heat wave
2002 indian heat waveravi rajpurohit
╠²
The 2002 Indian heat wave in South India killed over 1,000 people, most in Andhra Pradesh. Temperatures rose as high as 45-50 degrees Celsius. It caused major drought, health impacts like heat strokes, effects on agriculture and animals, and issues for energy infrastructure and railways. Treatment for heat stroke involves cooling the body and giving oral rehydration solutions, with hospitalization if needed. Prevention tips include staying hydrated, avoiding dehydrating substances, and not leaving people or pets in closed vehicles.Stess management
Stess managementravi rajpurohit
╠²
Stress can be caused by sudden changes in the environment, emotional factors, or situations we feel unprepared for. Stress affects individuals differently based on how we interpret situations, the resources we draw on, and our existing skills and resources. The effects of stress include physical symptoms like sweating, back pain, and muscle issues as well as behavioral changes like nail biting, sleep problems, anger, substance abuse, and social withdrawal. To overcome stress, the document recommends exercising, balancing responsibilities, avoiding drugs and alcohol, eating nutritious foods, spending time with friends and family, and maintaining a supportive environment.General elections
General electionsravi rajpurohit
╠²
The 2014 Indian general election was the longest in history, taking place over 9 phases from April to May 2014. Over 814 million people were eligible to vote, choosing members of parliament for the Lok Sabha. Key events included Narendra Modi being selected as the BJP's prime ministerial candidate and leading their campaign on a platform of development. The election also saw rise of the Aam Aadmi Party and Arvind Kejriwal challenging Modi in Varanasi. Voter turnout exceeded 2009 levels.English project
English projectravi rajpurohit
╠²
Literacy rates in rural India are significantly lower than in urban areas due to lack of educational infrastructure and resources. Only 61% of Indians are literate, with large disparities between states, genders, and rural/urban populations. Several government schemes aim to improve literacy, but progress remains slow. NGOs are also working to boost education access for underprivileged groups. To fully develop, India must prioritize achieving universal literacy through improved implementation and funding of literacy programs.Communication skills
Communication skillsravi rajpurohit
╠²
The document contains information about Gourav Sharma, a second semester Computer Science student at Government College of Engineering & Technology with roll number 29. It discusses various aspects of communication such as senders and receivers, messages, channels, feedback, and blocks. It also covers topics like effective communication, the distribution of communication skills among reading, writing, speaking and listening. Some key aspects of communication covered are being an active listener, effective presenter, quick thinker, and win-win negotiator. The document also discusses nonverbal behaviors, constructive communication, and overcoming communication barriers.Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
╠²
The SQLExecutor is one of FMEŌĆÖs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation ŌĆōValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019
╠²
A presentation at Internetware 2025.Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
╠²
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.OpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM
╠²
penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
╠²
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.UserCon Belgium: Honey, VMware increased my bill
UserCon Belgium: Honey, VMware increased my billstijn40
╠²
VMwareŌĆÖs pricing changes have forced organizations to rethink their datacenter cost management strategies. While FinOps is commonly associated with cloud environments, the FinOps Foundation has recently expanded its framework to include ScopesŌĆöand Datacenter is now officially part of the equation. In this session, weŌĆÖll map the FinOps Framework to a VMware-based datacenter, focusing on cost visibility, optimization, and automation. YouŌĆÖll learn how to track costs more effectively, rightsize workloads, optimize licensing, and drive efficiencyŌĆöall without migrating to the cloud. WeŌĆÖll also explore how to align IT teams, finance, and leadership around cost-aware decision-making for on-prem environments. If your VMware bill keeps increasing and you need a new approach to cost management, this session is for you!Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
╠²
Securing Account Lifecycles in the Age of DeepfakesCoordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the Same10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash
╠²
10 Key Challenges for AI within the EU Data Protection FrameworkQuantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu
╠²
Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowQuantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
╠²
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.More Related Content
More from ravi rajpurohit (6)
Ethics1
Ethics1ravi rajpurohit
╠²
This document discusses ethics and is about a student with roll number 41 studying civil engineering under guidance from Maa'm Ruma Bhaduriya. It covers meta ethics, normative ethics, and applied ethics. It also lists providing care, education, safety, and a good environment.2002 indian heat wave
2002 indian heat waveravi rajpurohit
╠²
The 2002 Indian heat wave in South India killed over 1,000 people, most in Andhra Pradesh. Temperatures rose as high as 45-50 degrees Celsius. It caused major drought, health impacts like heat strokes, effects on agriculture and animals, and issues for energy infrastructure and railways. Treatment for heat stroke involves cooling the body and giving oral rehydration solutions, with hospitalization if needed. Prevention tips include staying hydrated, avoiding dehydrating substances, and not leaving people or pets in closed vehicles.Stess management
Stess managementravi rajpurohit
╠²
Stress can be caused by sudden changes in the environment, emotional factors, or situations we feel unprepared for. Stress affects individuals differently based on how we interpret situations, the resources we draw on, and our existing skills and resources. The effects of stress include physical symptoms like sweating, back pain, and muscle issues as well as behavioral changes like nail biting, sleep problems, anger, substance abuse, and social withdrawal. To overcome stress, the document recommends exercising, balancing responsibilities, avoiding drugs and alcohol, eating nutritious foods, spending time with friends and family, and maintaining a supportive environment.General elections
General electionsravi rajpurohit
╠²
The 2014 Indian general election was the longest in history, taking place over 9 phases from April to May 2014. Over 814 million people were eligible to vote, choosing members of parliament for the Lok Sabha. Key events included Narendra Modi being selected as the BJP's prime ministerial candidate and leading their campaign on a platform of development. The election also saw rise of the Aam Aadmi Party and Arvind Kejriwal challenging Modi in Varanasi. Voter turnout exceeded 2009 levels.English project
English projectravi rajpurohit
╠²
Literacy rates in rural India are significantly lower than in urban areas due to lack of educational infrastructure and resources. Only 61% of Indians are literate, with large disparities between states, genders, and rural/urban populations. Several government schemes aim to improve literacy, but progress remains slow. NGOs are also working to boost education access for underprivileged groups. To fully develop, India must prioritize achieving universal literacy through improved implementation and funding of literacy programs.Communication skills
Communication skillsravi rajpurohit
╠²
The document contains information about Gourav Sharma, a second semester Computer Science student at Government College of Engineering & Technology with roll number 29. It discusses various aspects of communication such as senders and receivers, messages, channels, feedback, and blocks. It also covers topics like effective communication, the distribution of communication skills among reading, writing, speaking and listening. Some key aspects of communication covered are being an active listener, effective presenter, quick thinker, and win-win negotiator. The document also discusses nonverbal behaviors, constructive communication, and overcoming communication barriers.Recently uploaded (20)
Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
╠²
The SQLExecutor is one of FMEŌĆÖs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation ŌĆōValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019
╠²
A presentation at Internetware 2025.Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
╠²
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.OpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM
╠²
penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
╠²
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.UserCon Belgium: Honey, VMware increased my bill
UserCon Belgium: Honey, VMware increased my billstijn40
╠²
VMwareŌĆÖs pricing changes have forced organizations to rethink their datacenter cost management strategies. While FinOps is commonly associated with cloud environments, the FinOps Foundation has recently expanded its framework to include ScopesŌĆöand Datacenter is now officially part of the equation. In this session, weŌĆÖll map the FinOps Framework to a VMware-based datacenter, focusing on cost visibility, optimization, and automation. YouŌĆÖll learn how to track costs more effectively, rightsize workloads, optimize licensing, and drive efficiencyŌĆöall without migrating to the cloud. WeŌĆÖll also explore how to align IT teams, finance, and leadership around cost-aware decision-making for on-prem environments. If your VMware bill keeps increasing and you need a new approach to cost management, this session is for you!Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
╠²
Securing Account Lifecycles in the Age of DeepfakesCoordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the Same10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash
╠²
10 Key Challenges for AI within the EU Data Protection FrameworkQuantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu
╠²
Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowQuantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
╠²
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
╠²
║▌║▌▀Ż deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 20252025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata
╠²
The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
¤æŗ Introducing Data Contracts: An agreement between data producers and consumers
¤ōØ Data Contracts key components: Understanding a contract and its purpose
¤¦æŌĆŹ¤Ä© Writing your first contract: How to create your own contracts in OpenMetadata
¤”Š An OpenMetadata MCP Server update!
Ō×Ģ And More!OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic
╠²
Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
Ethicalhacking
- 8. .
- 9. Advantages ’é¦ Provides security to banking and financial establishments ’é¦ Prevents website defacements ’é¦ An evolving technique ’é¦ To catch a thief you have to think like a thief Disadvantages ’é¦ All depends upon the trustworthiness of the ethical hacker ’é¦ Hiring professionals is expensive. .
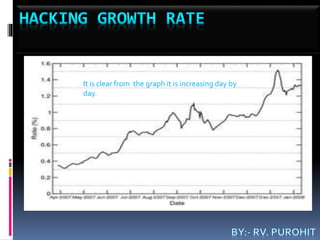
- 12. It is clear from the graph it is increasing day by day.
