Excel tutorial on students record
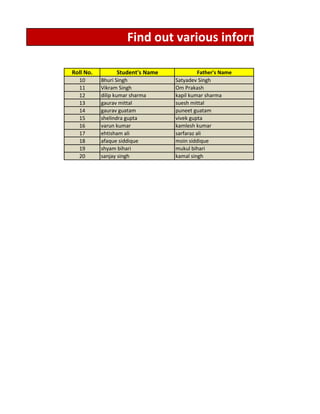
- 1. Find out various informations from Roll No. Student's Name Father's Name 10 Bhuri Singh Satyadev Singh 11 Vikram Singh Om Prakash 12 dilip kumar sharma kapil kumar sharma 13 gaurav mittal suesh mittal 14 gaurav guatam puneet guatam 15 shelindra gupta vivek gupta 16 varun kumar kamlesh kumar 17 ehtisham ali sarfaraz ali 18 afaque siddique moin siddique 19 shyam bihari mukul bihari 20 sanjay singh kamal singh
- 2. nformations from a students record ? Last Degree Address BCA Nagla Barhan Biruni BCA Lawyers colony khandari agra BCA Mau khandari bye pass agra BCA trans yammuna colony agra BSC hing ki madi agra BCA azad nagar khandari agra BSC d-block kamla nagar delhi bca 48 naseerabad khandari agra bba 59 e2 naseerabad colony khandari agra bca nagla jhori barhan agra BCA minakshi cenima aligarh
- 4. Roll No. Student's Name Father's Name Last Degree 10 Bhuri Singh Satyadev Singh BCA 11 Vikram Singh Om Prakash BCA 12 dilip kumar sharma kapil kumar sharma BCA 13 gaurav mittal suesh mittal BCA 14 gaurav guatam puneet guatam BSC 15 shelindra gupta vivek gupta BCA 16 varun kumar kamlesh kumar BSC 17 ehtisham ali sarfaraz ali bca 18 afaque siddique moin siddique bba 19 shyam bihari mukul bihari bca 20 sanjay singh kamal singh BCA Ques. 1 We have to find out the address of student having R Sol. 1 Result ---------> Assign. 1 Find out the last degree of "varun Kumar" Assign. 2 Find out the fathers name of "gaurav guatam"
- 5. Address Nagla Barhan Biruni Lawyers colony khandari agra Mau khandari bye pass agra trans yammuna colony agra hing ki madi agra azad nagar khandari agra d-block kamla nagar delhi 48 naseerabad khandari agra 59 e2 naseerabad colony khandari agra nagla jhori barhan agra minakshi cenima aligarh of student having Roll.No. 17 ? Formula applied here ! 48 naseerabad khandari agra Formula used ----> =vlookup(17,a2:e12,5) Here 17 is the roll number we have to look for. a2:e12 is the data range for which we have to find the information 5 is the coloumn from which we want to retreive the result n Kumar" urav guatam"
- 6. Roll No. Student's Name Father's Name Last Degree 10 Bhuri Singh Satyadev Singh BCA 11 Vikram Singh Om Prakash BCA 12 dilip kumar sharma kapil kumar sharma BCA 13 gaurav mittal suesh mittal BCA 14 gaurav guatam puneet guatam BSC 15 shelindra gupta vivek gupta BCA 16 varun kumar kamlesh kumar BSC 17 ehtisham ali sarfaraz ali bca 18 afaque siddique moin siddique bba 19 shyam bihari mukul bihari bca 20 sanjay singh kamal singh BCA Ques. 1 Determine how many students have done BCA or BS Formula applied here ! Sol. 1 Result --------------------------> 8 Formula used -----> =countif(d2:d12,"BCA" Here d2:d12 is the range where we have to f BCA is the text which we have to find NOTE : whenever you have to find any text Assign. 1 Find out how many students have done BSC
- 7. Address Nagla Barhan Biruni Lawyers colony khandari agra Mau khandari bye pass agra trans yammuna colony agra hing ki madi agra azad nagar khandari agra d-block kamla nagar delhi 48 naseerabad khandari agra 59 e2 naseerabad colony khandari agra nagla jhori barhan agra minakshi cenima aligarh have done BCA or BSC etc Formula applied here ! students have done BCA ula used -----> =countif(d2:d12,"BCA") d2:d12 is the range where we have to find the result the text which we have to find : whenever you have to find any text enclose it in double quotes as "BCA" ve done BSC
- 8. Roll No. Student's Name Father's Name Last Degree 10 Bhuri Singh Satyadev Singh BCA 11 Vikram Singh Om Prakash BCA 12 dilip kumar sharma kapil kumar sharma BCA 13 gaurav mittal suesh mittal BCA 14 gaurav guatam puneet guatam BSC 15 shelindra gupta vivek gupta BCA 16 varun kumar kamlesh kumar BSC 17 ehtisham ali sarfaraz ali bca 18 afaque siddique moin siddique bba 19 shyam bihari mukul bihari bca 20 sanjay singh kamal singh BCA Ques. 1 Plot a graph showing how many students are enrolled in which course,also find out whic 9 Sol.1 Degree No. of Students 8 BCA 8 7 BSC 2 No.Of Students 6 BBA 1 5 4 Formula applied here ! 3 2 1 0 Formula applied here ! Study revieles that most of the students have their last degree as Assin. 1 Solve the above question again by ploting a pie chart and finding out the course having t
- 9. Address Nagla Barhan Biruni Lawyers colony khandari agra Mau khandari bye pass agra trans yammuna colony agra hing ki madi agra azad nagar khandari agra d-block kamla nagar delhi 48 naseerabad khandari agra 59 e2 naseerabad colony khandari agra nagla jhori barhan agra minakshi cenima aligarh which course,also find out which course has maximum students ? BCA BSC BBA Last Degree BCA finding out the course having the minimum number of students ?