Fighting telecom fraud. Explaining SMS SS7 fraud
- 1. Fighting Telecom Fraud. Explaining SMS SS7 Fraud Source:https://www.gsma.com/newsroom/wp-content/uploads//IR.70-v4.0.pdf Martyn Sukys, 2016 Malta
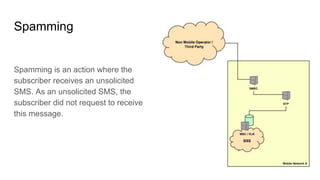
- 3. Spamming Spamming is an action where the subscriber receives an unsolicited SMS. As an unsolicited SMS, the subscriber did not request to receive this message.
- 4. Flooding The act of flooding is when a large number of messages are sent to one or more destinations. These messages may be either valid or invalid. The value or parameter used to define flooding is the extraordinary number of messages sent.
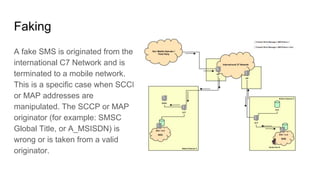
- 5. Faking A fake SMS is originated from the international C7 Network and is terminated to a mobile network. This is a specific case when SCCP or MAP addresses are manipulated. The SCCP or MAP originator (for example: SMSC Global Title, or A_MSISDN) is wrong or is taken from a valid originator.
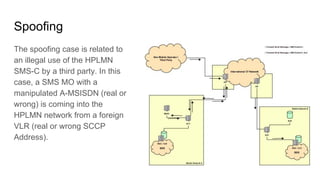
- 6. Spoofing The spoofing case is related to an illegal use of the HPLMN SMS-C by a third party. In this case, a SMS MO with a manipulated A-MSISDN (real or wrong) is coming into the HPLMN network from a foreign VLR (real or wrong SCCP Address).
- 7. GT Scanning The GT scanning is the fact to send SMS MO to all Global Title address from one mobile operator in order to find unsecured SMS-C (SMS-C that are not controlling the A number).
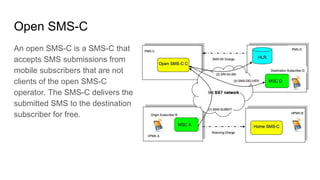
- 8. Open SMS-C An open SMS-C is a SMS-C that accepts SMS submissions from mobile subscribers that are not clients of the open SMS-C operator. The SMS-C delivers the submitted SMS to the destination subscriber for free.
- 9. Operators are aware of the risks Operators take measures to reduce the risk of threat exploitation. They succeed in reducing subscriber and network data leakage. In 2016, all analyzed networks used SMS Home Routing, and every third network had signaling traffic filtering and blocking enabled. Existing solutions are not sufficient Despite additional protection measures, all the networks were prone to vulnerabilities caused by occasional incorrect setup of equipment or faults in SS7 network architecture that cannot be eliminated using existing tools. Only a comprehensive approach that combines security analysis, network setup maintenance, regular monitoring of signaling traffic, and timely detection of illegitimate activities can ensure a higher level of protection against criminals.