Forensic
- 1. Forensic
- 2. Cyber attack ? Pdf nya bssn
- 3. Forensic analysis: ? Network Incident Response ? Email spoofing / phising / anomaly ? Network slowing down at working hour ? Local Incident Response ? PC / Laptop Forensic ? Ransom, Malware, virus ? Mobile Forensic ? stole user credential ? Phone belong to criminals ? Server Incident Response ? Webserver, mail server, voucher server
- 4. Step ? Background of when the incident happen, and what IT department do after. ? Collecting evidence ? Confirm if this computer was involved in the data breach and find traces of malicious activity if present. ? Perform disk analysis ? Perform memory analysis ? Analyse logs, registry ? Examine suspicious artefacts ? Interview with victim of incident ? Create timeline and put the leads together ? Draw conclusions ? Reporting and follow up actions ? Advise on the course of action ? Create Indicators of Compromise ? Create a report sketch ? Create recommendations of immediate actions to take
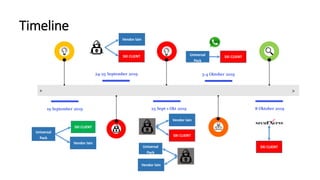
- 5. Timeline 19 September 2019 24-25 September 2019 > > 25 Sept-1 Okt 2019 3-4 Oktober 2019 8 Oktober 2019 SXI CLIENT Universal Pack SXI CLIENT Vendor lain Vendor lain SXI CLIENT Vendor lain Universal Pack Vendor lain SXI CLIENT Universal Pack SXI CLIENT
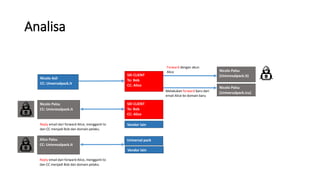
- 6. Analisa Nicolo Asli CC: Unversalpack.it SXI CLIENT To: Bob CC: Alice Nicolo Palsu (Univresalpack.it) Nicolo Palsu CC: Univresalpack.it Nicolo Palsu (Universalpack.icu) SXI CLIENT To: Bob CC: Alice Forward dengan akun Alice Reply email dari forward Alice, mengganti to dan CC menjadi Bob dan domain pelaku. Melakukan forward baru dari email Alice ke domain baru Vendor lain Alice Palsu CC: Univresalpack.it Universal pack Reply email dari forward Alice, mengganti to dan CC menjadi Bob dan domain pelaku. Vendor lain
- 7. Challenges ? Big HD and memories ? Time consuming ? Incident happen more then 3 days ? Logs retainer only for 7 days back ? The IT guys just ? shutdown the incident PC without consulting first ? Installing antivirus on the incident PC ? No SIEM available ? Very slow PC / laptop ? Everyone shared the same credentials
- 8. Cybercrime investigator ? A cybercrime investigator investigates a number of crimes that range from recovering file systems on computers that have been hacked or damaged to investigating crimes against children. ? In addition, cybercrime investigators also recover data from computers that can be used in prosecuting crimes. ? Once the necessary electronic evidence is gathered, cybercrime investigators write reports that will later be used in court. Cybercrime investigators must also testify in court.
- 9. Jobs ? Analyzing computer systems and networks following incident. ? Gathering computer and network information. ? Gathering evidence. ? Identify and recommend methods for the preservation and presentation of evidence. ? Recovering data that was either destroyed or damaged. ? Recovering password-protected/encrypted files and hidden information. ? Reconstructing cyberattacks. ? Drafting expert testimony, affidavits, and reports. ? Testifying in court.
- 10. Next ? https://www.ashemery.com/dfir.html ? https://freetraining.dfirdiva.com/dfir-ctfs-challenges ? https://or10nlabs.tech/defcon-dfir-ctf-2018/ ? https://soji256.medium.com/where-can-you-find-images-that-you- can-use-to-learn-forensics-141c6c8cdc9e ? https://aboutdfir.com/education/challenges-ctfs/ ? https://medium.com/@monliclican/defcon-dfir-ctf-2018-lessons- learned-890ef781b96c ? https://defcon2019.ctfd.io/