Format String
- 2. Who am I? ? ID : bananaapple ? WÐĢŋÆÏĩ : ―ŧÍĻīóWŲYđĪÏĩ ? Äęž : īóČýÉýīóËÄ ? ÄŋĮ°é Bamboofox ÖÐĩÄŌŧT
- 3. Outline ? Dangerous Function ? Function call ? Format string ? Example ? Strategy ? Practice
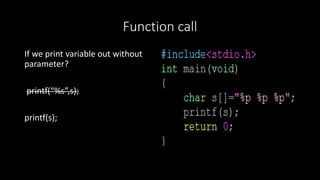
- 5. Function call If we print variable out without parameter? printf(Ą°%sĄą,s); printf(s);
- 7. Format string ? Function doesnĄŊt know how many parameter it has. ? As result, function will take the value on the stack as parameters. ? As this way we could leak any address above the stack. ? How about the address below the stack? ? We have make our own arguments and use it ? How? ? The buffer will above the stack pointer ? Calculate the offset and point to the buffer
- 8. Format string ? %x : Unsigned hexadecimal integer ? %s : String of characters ? %p : Pointer address ? %n : The number of characters written so far is stored in the pointed location ? %(num)c : Print num characters ? %(num)$x : dump numth parameter Ex : %100$x : dump 100th dword
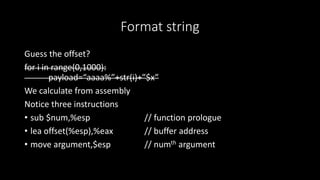
- 9. Format string Guess the offset? for i in range(0,1000): payload=Ą°aaaa%Ąą+str(i)+Ąą$xĄą We calculate from assembly Notice three instructions ? sub $num,%esp // function prologue ? lea offset(%esp),%eax // buffer address ? move argument,$esp // numth argument
- 10. Example
- 11. Example
- 12. Example
- 13. Example ? %n %n : dword : 4 bytes %hn : word : 2 bytes %hhn: byte : 1 bytes ? Try to write value 0x6a686664 to 0x08045566 0x64 to 0x08045566 0x66 to 0x08045567 0x68 to 0x08045568 0x6a to 0x08045569
- 14. Example Try to write value 0x6a686664 to 0x08045566 Payload will look like this x66x55x04x08x67x55x04x08 // 8 characters x68x55x04x08x69x55x04x08 // 8 characters %84c%4$hhn %2c%5$hhn %2c%6$hhn %2c%7$hhn
- 15. Strategy With this skill you can do ? Read / write any position if map permission is allowed ? GOT hijacking ? Write variable value ? Leak libc base address and calculate offset to get another function address ? Leak libc version ? Leak stack address
- 16. Practice ? fmt1 http://secprog.cs.nctu.edu.tw/problems/12 ? fmt2 http://secprog.cs.nctu.edu.tw/problems/13 ? Monkey1 http://train.cs.nctu.edu.tw/problems/2 ? Monkey2 http://train.cs.nctu.edu.tw/problems/3
- 17. Reference ? http://www.cis.syr.edu/~wedu/Teaching/cis643/LectureNotes_New/F ormat_String.pdf ? Almost by experience ( practice hard, and use gdb to test )