Frequency Based Detection Of Task Switches
Download as ppt, pdf2 likes531 views
The document discusses a frequency-based detection method for task switches in user interactions, focusing on window manipulation patterns as indicators of task switching. A study involving six participants demonstrated varying accuracy in switch detection based on user behavior, with insights into the effects of instant messaging on detection rates. The software aims to minimize privacy concerns while efficiently tracking task transitions without needing to identify specific tasks.
1 of 17
Downloaded 15 times
![Frequency-based detection of task switches Rahul Nair Yahoo! Research Berkeley [email_address] Steve Voida & Elizabeth Mynatt Georgia Institute of Technology {svoida, mynatt}@cc.gatech.edu](https://image.slidesharecdn.com/frequency-based-detection-of-task-switches4656/85/Frequency-Based-Detection-Of-Task-Switches-1-320.jpg)


![Frequency-based detection of task switches Rahul Nair Yahoo! Research Berkeley [email_address] Steve Voida & Elizabeth Mynatt Georgia Institute of Technology {svoida, mynatt}@cc.gatech.edu](https://image.slidesharecdn.com/frequency-based-detection-of-task-switches4656/85/Frequency-Based-Detection-Of-Task-Switches-5-320.jpg)








![Questions? Rahul Nair [email_address] www.rahulnair.net](https://image.slidesharecdn.com/frequency-based-detection-of-task-switches4656/85/Frequency-Based-Detection-Of-Task-Switches-16-320.jpg)
Ad
Recommended
CASA: Context Aware Scalable Authentication, at SOUPS 2013
CASA: Context Aware Scalable Authentication, at SOUPS 2013Jason Hong
╠²
The document discusses CASA (context-aware scalable authentication), a framework designed to enhance user authentication by adapting to various contexts through active and passive factors. It presents findings from multiple field studies that examine user preferences for different authentication schemes based on location, ultimately concluding that users favor a customizable system that balances security with usability. The proposed naive Bayes model effectively combines these factors, enhancing security while reducing user annoyance associated with traditional authentication methods.Getting to Flow in Software Development (ASWEC 2014 Keynote)
Getting to Flow in Software Development (ASWEC 2014 Keynote)Gail Murphy
╠²
The document discusses the concept of 'flow' in software development, emphasizing the importance of tools and interfaces that enable developers to work without interruptions and distractions. It outlines techniques for improving flow through task context, recommendations, dialog, and summarization, while identifying mismatches in information spaces and cognitive overload. The ultimate goal is to create programming environments that enhance productivity and enjoyment in software development.CASA: Context-Aware Scalable Authentication, at SOUPS 2013
CASA: Context-Aware Scalable Authentication, at SOUPS 2013Jason Hong
╠²
The document discusses the CASA (Context-Aware Scalable Authentication) framework designed to enhance user authentication by adjusting security measures based on contextual factors. Through a series of field studies, it evaluates the usability and security of varying authentication schemes across different environments, notably home and workplace. Results suggest that users prefer the system that minimizes the need for constant authentication, while still maintaining appropriate security levels, showing a balance between usability and security.Complexity 2
Complexity 2David Maynard, MBA, PMP
╠²
The document discusses the complexity of project management, emphasizing the need for appropriate tools and processes based on project complexity. It introduces a model designed to evaluate project complexity using various dimensions and factors, along with an interface for users to input data and adapt the model. Future enhancements are suggested for security, user interface, and the model's ability to learn from user input.Towards Task Analysis Tool Support
Towards Task Analysis Tool SupportSuzanne Kieffer
╠²
The document discusses a task analysis framework aimed at improving data collection efficiency in a work environment through a tool called 'tempest.' It details the methodology used to assess user tasks, their complexities, and the potential errors during execution, comparing traditional face-to-face techniques with tool-assisted methods. The findings highlight increased analyst efficiency and product accuracy, suggesting a need for adaptable tools that support real-time monitoring and response traceability.Bug or Feature? Covert Impairments to Human Computer Interaction
Bug or Feature? Covert Impairments to Human Computer Interactionivaderivader
╠²
This document provides a framework for analyzing covert impairments to human-computer interaction. It defines covert impairments as modifications to user input that are intentionally hidden from the user and decrease task performance. The document categorizes covert impairments based on their modality, impairment type, intent, reaction, and goal. It discusses ethical considerations and detection/prevention of both malevolent and benevolent covert impairments. The document aims to systematically study this issue and highlights examples of covert impairments currently used in applications like cybersecurity and cognitive science research.Dan Mallinger, Data Science Practice Manager, Think Big Analytics at MLconf NYC
Dan Mallinger, Data Science Practice Manager, Think Big Analytics at MLconf NYCMLconf
╠²
The document discusses the importance of effective communication in analytics and the challenges faced by data scientists in explaining complex models. It emphasizes that better communication leads to understanding and trust in data-driven decisions, especially in regulated environments. The author shares insights on overcoming barriers to model explanation and the significance of model robustness and sensitivity analysis.The Resting Brain
The Resting BrainDDB515
╠²
This document discusses research on the neural basis of mind wandering and its relationship to ongoing behavior and executive function. It examines how mind wandering is associated with the default network in the brain and recruitment of this network decreases with external task demands. It also looks at how probing subjects during a sustained attention task can provide information about levels of mind wandering and meta-awareness and recruitment of the executive network. The research found that mind wandering is strongest when there is less meta-awareness and that higher executive recruitment may indicate multitasking, attempting to return to the task, or conflict detection related to mind wandering.Final Report_213110090
Final Report_213110090Arvind Singh Rathod
╠²
The document provides details about an internship at Digital Endpoint. It summarizes the intern's work automating tests for Digital Endpoint's main product, KnowIT, using the Robot Framework. The intern learned about Robot Framework, designed test suites to automate features of KnowIT and Flexispy, including application usage, file activity, key logs, and more. The internship helped the individual gain experience in professional work environments and skills with test automation, Robot Framework, and tools like Selenium and Java.How Testing A Monitoring Rule Led to A Microsoft Bounty
How Testing A Monitoring Rule Led to A Microsoft BountyTristan Bennett
╠²
The document describes how the author tested a network monitoring rule they created by simulating suspicious activities on their system to determine if the rule could accurately detect these events. Through extensive testing of different tools, commands, and techniques, the author was able to improve the rule's detection capabilities and gain a deeper understanding of how Windows logs and responds to such activities. This led Microsoft to award the author a bounty for discovering a vulnerability their original rule was missing.Sharing Motion Information with Close Family and Friends
Sharing Motion Information with Close Family and Friendsbentley79
╠²
The document discusses the Motion Presence application, designed to facilitate sharing motion information among close friends and family to enhance social awareness and availability. It highlights findings from a field study where participants could infer details about each other's locations and activities, leading to improved communication and coordination. Participants expressed minimal privacy concerns and a desire for more detailed motion information, underlining the potential benefits of such technology in everyday interactions.Making Effective, Useful Software Development Tools
Making Effective, Useful Software Development ToolsGail Murphy
╠²
The document discusses making effective software development tools for humans. It presents examples of tools that either successfully or unsuccessfully bridge the mismatch between how developers work and how tools are designed. The Whyline debugging tool reduces debugging time by directly supporting developers' inquisitive nature. Mylyn improves productivity by leveraging how developers work in tasks and use episodic memory. In contrast, defect prediction tools showed no behavioral change when flags were added to code reviews, failing to bridge theory and practice. Overall, the document argues tools should be designed around how humans work, not just computers.ObserveIT whitepaper: "Log Blindspots" > generare i Log in automatico per un ...
ObserveIT whitepaper: "Log Blindspots" > generare i Log in automatico per un ...Clever Consulting
╠²
The whitepaper discusses significant blindspots in system logs that fail to capture critical security events, highlighting that well-established log management tools can miss key actions. It provides examples of common system activities on both Windows and Linux platforms that lack adequate logging, ultimately advocating for user activity monitoring solutions like ObserveIT to fill these gaps. The document emphasizes that traditional audit reports may overlook critical user actions, necessitating enhanced monitoring to ensure comprehensive security and compliance.IT 510 Module Two Case Study You are employed in the co.docx
IT 510 Module Two Case Study You are employed in the co.docxvrickens
╠²
The document outlines a case study at Urcovered, Inc., where management has identified a mobile application as a potential enhancement to customer service in claims management. A dedicated committee is formed to analyze both the benefits and drawbacks of implementing the application, emphasizing the necessity to maintain personal connections between case managers and customers. The analysis will support a go/no go decision for the project, with criteria set to address consumer needs, technical integration, and resource allocation.Business Effectiveness Assignment 2 Report
Business Effectiveness Assignment 2 ReportMohammed Zohaib Munnee
╠²
This software called TempBuddy is used by recruitment agency Verve to manage temporary staffing. Employees create profiles providing availability and personal details. When work is available, employees are notified and can accept shifts, receiving job details. The software automatically tracks check-ins, timesheets, and messaging between the agency and employees, providing security and efficient scheduling. Key benefits include real-time staff visibility, fast booking of shifts, digital timesheets, and geo-location check-ins for accurate scheduling and payment. Tests of features like messaging, scheduling, and timesheet generation confirmed the software meets requirements for usability and managing staff assignments.Engage 2013 - Interaction Process Automation
Engage 2013 - Interaction Process AutomationAvtex
╠²
The document discusses the challenges faced by organizations due to inefficient processes, such as manual handling and lack of visibility, leading to delays and errors. It highlights the importance of Interaction Process Automation (IPA) to streamline operations, ensuring efficient task management, real-time monitoring, and improved communication. By integrating processes and using automated workflows, businesses can enhance efficiency, reduce training time, and provide better customer service.Programmer Information Needs After Memory Failure
Programmer Information Needs After Memory FailureChris Parnin
╠²
The document discusses memory theories and cognitive neuroscience as they relate to programmers' abilities to recall information after interruptions. It emphasizes the importance of different memory types, like associative and episodic memory, and offers insights into tools and strategies for enhancing memory retention in programming tasks. Memory deficiencies and the effectiveness of memory cues in recovering from interruptions are also explored.Exploratory Testing in Practice
Exploratory Testing in PracticeElisabeth Hendrickson
╠²
Exploratory testing is a systematic approach to discovering risks by rigorously analyzing and testing a system through heuristics and testing techniques. It involves simultaneously learning about the target system while designing and immediately executing tests, using feedback from previous experiments to inform new tests. Exploratory testing focuses on discovering things you can vary and uses models, heuristics, time-boxed sessions, and charters to structure the exploration and focus on important areas.Aspect-Oriented Instrumentation for Capturing Task- Based Event Traces
Aspect-Oriented Instrumentation for Capturing Task- Based Event TracesIDES Editor
╠²
This paper discusses an aspect-oriented approach to capture task-based event traces for usability evaluation, addressing the challenge of collecting contextual information alongside user interface event data. It presents a proof-of-concept tool designed to enhance the interpretation of event traces by enabling developers to capture relevant information about user interactions with applications. The authors highlight the necessity of contextual data for effectively identifying tasks and task sequences from user actions.Resouce.pptx
Resouce.pptxRajivSharma63156
╠²
Anviam Solutions provides web design, software development, and IT services. They enhance user experiences through creative and collaborative work. Their time tracking application aims to provide comprehensive time tracking for employees, clients, projects, and tasks with seamless clock-in/out, location tracking, and note taking abilities. The implementation plan focuses on ideating solutions, co-creating customized approaches, and providing personalized implementation support.Changing rules 1_stopcheating_slideshare
Changing rules 1_stopcheating_slideshareSOASTA
╠²
The webinar discusses the evolution of performance testing in cloud environments, emphasizing the importance of realistic simulations over traditional methods that often relied on flawed extrapolations and modifications. It critiques common pitfalls such as modifying think time, extrapolating capacity incorrectly, and poorly modeling user flows, advocating for methods that accurately reflect real user behavior. The presentation highlights that better testing strategies can uncover critical performance issues, ultimately leading to more reliable production environments.Group6 presentation
Group6 presentationSteven Nava
╠²
The document outlines a proposal for an RFID card time entry and resource access solution. It describes the old paper-based system and proposes a new RFID badge system that provides more flexibility and simplifies processes like time tracking and access management. The new system would use RFID badges for secure building access and time tracking through badge swipes that are logged. This allows for easy reporting, access removal for terminated employees, and time calculations. The proposal discusses stakeholders, requirements, costs, benefits, and project methodology to implement the new RFID badge system.Synerion - Comprehensive Workforce Management Solutions
Synerion - Comprehensive Workforce Management SolutionsSynerionNA
╠²
The document provides a brief history and overview of trends in workforce management. It discusses how early time clocks from the 20th century tracked employee hours and pay using paper timecards. Today, there are many automated options like web entry, badge readers, and biometric systems like fingerprint scanning. Recent trends include using workforce management systems for broader functions beyond timekeeping, increased self-service capabilities, and strategic workforce planning across organizations.History & Trends in Workforce Management
History & Trends in Workforce ManagementSynerion North America Inc.
╠²
Early time clocks from the early 20th century tracked employee hours by having them punch time cards that recorded their entry and exit times. Over time, timekeeping evolved to include automated data collection using technologies like web entry, badge readers, and biometric systems like fingerprint scanning. Modern workforce management systems now provide strategic workforce planning capabilities and are used across entire organizations and offsite workers to optimize scheduling and labor costs.Computational Behaviour Modelling for the Internet of Things
Computational Behaviour Modelling for the Internet of ThingsFahim Kawsar
╠²
This document discusses computational behavior modeling for the Internet of Things. It begins by posing questions about the future of connected devices and apps. The author then discusses using sensors, learning, and actions to create useful IoT devices like a smart thermostat. However, many current IoT devices are dismissed as solving no real problems. The document outlines using wireless networks and wearables to understand human context and behavior through large datasets of user activity traces and applying machine learning. Challenges are discussed around privacy and participation guarantees. Applications include people analytics, productivity management, and space management to quantify enterprises. The future may include contextual automation through multi-modal sensing and deep learning on devices, networks, and infrastructure to better understand environments and activities.Building Intelligent Workplace Limits and Challenges RIGA COMM 2023
Building Intelligent Workplace Limits and Challenges RIGA COMM 2023 Muntis Rudzitis
╠²
The presentation by Muntis Rudzitis explores the implementation of machine learning and AI in creating intelligent workplaces to optimize workflow and task execution. It emphasizes the challenges in understanding task similarity and developing analytics to improve productivity through knowledge reuse. Key lessons include the importance of structuring data, the influence of context on task similarity, and the need for better local models.Resumption strategies
Resumption strategiesChris Parnin
╠²
This document discusses research on interrupted programming tasks. It finds that programming work is highly fragmented, with most tasks interrupted and taking twice as long to complete. When resuming an interrupted task, programmers often have to navigate to multiple locations before continuing work, resulting in resumption lags of 10-30 minutes. Common resumption strategies include returning to the last edit location, navigating to locations to trigger memory, and examining errors, tests or version history. However, these strategies are often insufficient on their own due to the limited cues available to programmers. The research aims to understand these challenges and how tools could better support task resumption.Supporting document management in complex multitask environments
Supporting document management in complex multitask environmentsSamuel Driessen
╠²
The document discusses the persistent use of paper in modern workplaces despite the push for digital solutions, highlighting paper's unique advantages in supporting knowledge work, task management, and collaboration. It outlines three research stages that explore how paper facilitates task management, switching, and context representation, revealing challenges such as information overload and the need for effective document management systems. The findings suggest improvements for digital systems by incorporating insights from how paper is utilized, aiming to enhance user experience in multitasking environments.Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
╠²
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.Mastering AI Workflows with FME by Mark Do╠łring
Mastering AI Workflows with FME by Mark Do╠łringSafe Software
╠²
Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FMEŌĆÖs powerful tools for training, optimization, and seamless integrationMore Related Content
Similar to Frequency Based Detection Of Task Switches (20)
Final Report_213110090
Final Report_213110090Arvind Singh Rathod
╠²
The document provides details about an internship at Digital Endpoint. It summarizes the intern's work automating tests for Digital Endpoint's main product, KnowIT, using the Robot Framework. The intern learned about Robot Framework, designed test suites to automate features of KnowIT and Flexispy, including application usage, file activity, key logs, and more. The internship helped the individual gain experience in professional work environments and skills with test automation, Robot Framework, and tools like Selenium and Java.How Testing A Monitoring Rule Led to A Microsoft Bounty
How Testing A Monitoring Rule Led to A Microsoft BountyTristan Bennett
╠²
The document describes how the author tested a network monitoring rule they created by simulating suspicious activities on their system to determine if the rule could accurately detect these events. Through extensive testing of different tools, commands, and techniques, the author was able to improve the rule's detection capabilities and gain a deeper understanding of how Windows logs and responds to such activities. This led Microsoft to award the author a bounty for discovering a vulnerability their original rule was missing.Sharing Motion Information with Close Family and Friends
Sharing Motion Information with Close Family and Friendsbentley79
╠²
The document discusses the Motion Presence application, designed to facilitate sharing motion information among close friends and family to enhance social awareness and availability. It highlights findings from a field study where participants could infer details about each other's locations and activities, leading to improved communication and coordination. Participants expressed minimal privacy concerns and a desire for more detailed motion information, underlining the potential benefits of such technology in everyday interactions.Making Effective, Useful Software Development Tools
Making Effective, Useful Software Development ToolsGail Murphy
╠²
The document discusses making effective software development tools for humans. It presents examples of tools that either successfully or unsuccessfully bridge the mismatch between how developers work and how tools are designed. The Whyline debugging tool reduces debugging time by directly supporting developers' inquisitive nature. Mylyn improves productivity by leveraging how developers work in tasks and use episodic memory. In contrast, defect prediction tools showed no behavioral change when flags were added to code reviews, failing to bridge theory and practice. Overall, the document argues tools should be designed around how humans work, not just computers.ObserveIT whitepaper: "Log Blindspots" > generare i Log in automatico per un ...
ObserveIT whitepaper: "Log Blindspots" > generare i Log in automatico per un ...Clever Consulting
╠²
The whitepaper discusses significant blindspots in system logs that fail to capture critical security events, highlighting that well-established log management tools can miss key actions. It provides examples of common system activities on both Windows and Linux platforms that lack adequate logging, ultimately advocating for user activity monitoring solutions like ObserveIT to fill these gaps. The document emphasizes that traditional audit reports may overlook critical user actions, necessitating enhanced monitoring to ensure comprehensive security and compliance.IT 510 Module Two Case Study You are employed in the co.docx
IT 510 Module Two Case Study You are employed in the co.docxvrickens
╠²
The document outlines a case study at Urcovered, Inc., where management has identified a mobile application as a potential enhancement to customer service in claims management. A dedicated committee is formed to analyze both the benefits and drawbacks of implementing the application, emphasizing the necessity to maintain personal connections between case managers and customers. The analysis will support a go/no go decision for the project, with criteria set to address consumer needs, technical integration, and resource allocation.Business Effectiveness Assignment 2 Report
Business Effectiveness Assignment 2 ReportMohammed Zohaib Munnee
╠²
This software called TempBuddy is used by recruitment agency Verve to manage temporary staffing. Employees create profiles providing availability and personal details. When work is available, employees are notified and can accept shifts, receiving job details. The software automatically tracks check-ins, timesheets, and messaging between the agency and employees, providing security and efficient scheduling. Key benefits include real-time staff visibility, fast booking of shifts, digital timesheets, and geo-location check-ins for accurate scheduling and payment. Tests of features like messaging, scheduling, and timesheet generation confirmed the software meets requirements for usability and managing staff assignments.Engage 2013 - Interaction Process Automation
Engage 2013 - Interaction Process AutomationAvtex
╠²
The document discusses the challenges faced by organizations due to inefficient processes, such as manual handling and lack of visibility, leading to delays and errors. It highlights the importance of Interaction Process Automation (IPA) to streamline operations, ensuring efficient task management, real-time monitoring, and improved communication. By integrating processes and using automated workflows, businesses can enhance efficiency, reduce training time, and provide better customer service.Programmer Information Needs After Memory Failure
Programmer Information Needs After Memory FailureChris Parnin
╠²
The document discusses memory theories and cognitive neuroscience as they relate to programmers' abilities to recall information after interruptions. It emphasizes the importance of different memory types, like associative and episodic memory, and offers insights into tools and strategies for enhancing memory retention in programming tasks. Memory deficiencies and the effectiveness of memory cues in recovering from interruptions are also explored.Exploratory Testing in Practice
Exploratory Testing in PracticeElisabeth Hendrickson
╠²
Exploratory testing is a systematic approach to discovering risks by rigorously analyzing and testing a system through heuristics and testing techniques. It involves simultaneously learning about the target system while designing and immediately executing tests, using feedback from previous experiments to inform new tests. Exploratory testing focuses on discovering things you can vary and uses models, heuristics, time-boxed sessions, and charters to structure the exploration and focus on important areas.Aspect-Oriented Instrumentation for Capturing Task- Based Event Traces
Aspect-Oriented Instrumentation for Capturing Task- Based Event TracesIDES Editor
╠²
This paper discusses an aspect-oriented approach to capture task-based event traces for usability evaluation, addressing the challenge of collecting contextual information alongside user interface event data. It presents a proof-of-concept tool designed to enhance the interpretation of event traces by enabling developers to capture relevant information about user interactions with applications. The authors highlight the necessity of contextual data for effectively identifying tasks and task sequences from user actions.Resouce.pptx
Resouce.pptxRajivSharma63156
╠²
Anviam Solutions provides web design, software development, and IT services. They enhance user experiences through creative and collaborative work. Their time tracking application aims to provide comprehensive time tracking for employees, clients, projects, and tasks with seamless clock-in/out, location tracking, and note taking abilities. The implementation plan focuses on ideating solutions, co-creating customized approaches, and providing personalized implementation support.Changing rules 1_stopcheating_slideshare
Changing rules 1_stopcheating_slideshareSOASTA
╠²
The webinar discusses the evolution of performance testing in cloud environments, emphasizing the importance of realistic simulations over traditional methods that often relied on flawed extrapolations and modifications. It critiques common pitfalls such as modifying think time, extrapolating capacity incorrectly, and poorly modeling user flows, advocating for methods that accurately reflect real user behavior. The presentation highlights that better testing strategies can uncover critical performance issues, ultimately leading to more reliable production environments.Group6 presentation
Group6 presentationSteven Nava
╠²
The document outlines a proposal for an RFID card time entry and resource access solution. It describes the old paper-based system and proposes a new RFID badge system that provides more flexibility and simplifies processes like time tracking and access management. The new system would use RFID badges for secure building access and time tracking through badge swipes that are logged. This allows for easy reporting, access removal for terminated employees, and time calculations. The proposal discusses stakeholders, requirements, costs, benefits, and project methodology to implement the new RFID badge system.Synerion - Comprehensive Workforce Management Solutions
Synerion - Comprehensive Workforce Management SolutionsSynerionNA
╠²
The document provides a brief history and overview of trends in workforce management. It discusses how early time clocks from the 20th century tracked employee hours and pay using paper timecards. Today, there are many automated options like web entry, badge readers, and biometric systems like fingerprint scanning. Recent trends include using workforce management systems for broader functions beyond timekeeping, increased self-service capabilities, and strategic workforce planning across organizations.History & Trends in Workforce Management
History & Trends in Workforce ManagementSynerion North America Inc.
╠²
Early time clocks from the early 20th century tracked employee hours by having them punch time cards that recorded their entry and exit times. Over time, timekeeping evolved to include automated data collection using technologies like web entry, badge readers, and biometric systems like fingerprint scanning. Modern workforce management systems now provide strategic workforce planning capabilities and are used across entire organizations and offsite workers to optimize scheduling and labor costs.Computational Behaviour Modelling for the Internet of Things
Computational Behaviour Modelling for the Internet of ThingsFahim Kawsar
╠²
This document discusses computational behavior modeling for the Internet of Things. It begins by posing questions about the future of connected devices and apps. The author then discusses using sensors, learning, and actions to create useful IoT devices like a smart thermostat. However, many current IoT devices are dismissed as solving no real problems. The document outlines using wireless networks and wearables to understand human context and behavior through large datasets of user activity traces and applying machine learning. Challenges are discussed around privacy and participation guarantees. Applications include people analytics, productivity management, and space management to quantify enterprises. The future may include contextual automation through multi-modal sensing and deep learning on devices, networks, and infrastructure to better understand environments and activities.Building Intelligent Workplace Limits and Challenges RIGA COMM 2023
Building Intelligent Workplace Limits and Challenges RIGA COMM 2023 Muntis Rudzitis
╠²
The presentation by Muntis Rudzitis explores the implementation of machine learning and AI in creating intelligent workplaces to optimize workflow and task execution. It emphasizes the challenges in understanding task similarity and developing analytics to improve productivity through knowledge reuse. Key lessons include the importance of structuring data, the influence of context on task similarity, and the need for better local models.Resumption strategies
Resumption strategiesChris Parnin
╠²
This document discusses research on interrupted programming tasks. It finds that programming work is highly fragmented, with most tasks interrupted and taking twice as long to complete. When resuming an interrupted task, programmers often have to navigate to multiple locations before continuing work, resulting in resumption lags of 10-30 minutes. Common resumption strategies include returning to the last edit location, navigating to locations to trigger memory, and examining errors, tests or version history. However, these strategies are often insufficient on their own due to the limited cues available to programmers. The research aims to understand these challenges and how tools could better support task resumption.Supporting document management in complex multitask environments
Supporting document management in complex multitask environmentsSamuel Driessen
╠²
The document discusses the persistent use of paper in modern workplaces despite the push for digital solutions, highlighting paper's unique advantages in supporting knowledge work, task management, and collaboration. It outlines three research stages that explore how paper facilitates task management, switching, and context representation, revealing challenges such as information overload and the need for effective document management systems. The findings suggest improvements for digital systems by incorporating insights from how paper is utilized, aiming to enhance user experience in multitasking environments.Recently uploaded (20)
Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
╠²
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.Mastering AI Workflows with FME by Mark Do╠łring
Mastering AI Workflows with FME by Mark Do╠łringSafe Software
╠²
Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FMEŌĆÖs powerful tools for training, optimization, and seamless integration2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata
╠²
The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
¤æŗ Introducing Data Contracts: An agreement between data producers and consumers
¤ōØ Data Contracts key components: Understanding a contract and its purpose
¤¦æŌĆŹ¤Ä© Writing your first contract: How to create your own contracts in OpenMetadata
¤”Š An OpenMetadata MCP Server update!
Ō×Ģ And More!AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc
╠²
AI VIDEO MAGAZINE - r/aivideo community newsletter ŌĆō Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens
╠²
Hi, IŌĆÖm Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as IŌĆÖve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobsŌĆ” WeŌĆÖll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is ŌĆ£Fifth ElementŌĆØ. It wowed me with futuristic predictions when I was a kid and IŌĆÖm impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldnŌĆÖt be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we donŌĆÖt know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didnŌĆÖt steal jobsŌĆöthey transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic
╠²
Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle."How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
╠²
The SQLExecutor is one of FMEŌĆÖs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation ŌĆōValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik
╠²
A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.Salesforce Summer '25 Release Frenchgathering.pptx.pdf
Salesforce Summer '25 Release Frenchgathering.pptx.pdfyosra Saidani
╠²
Salesforce Summer '25 Release Frenchgathering.pptx.pdfA Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash
╠²
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and PrivacyGenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowOpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM
╠²
penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.AI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software
╠²
In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike.Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software
╠²
Managing airport and airspace data is no small task, especially when youŌĆÖre expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts ŌĆō all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results ŌĆō streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FMEŌĆÖs AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too.Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019
╠²
A presentation at Internetware 2025.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
Ad
Frequency Based Detection Of Task Switches
- 1. Frequency-based detection of task switches Rahul Nair Yahoo! Research Berkeley [email_address] Steve Voida & Elizabeth Mynatt Georgia Institute of Technology {svoida, mynatt}@cc.gatech.edu
- 2. A Question How did you know that this talk was beginning?
- 3. A Question How did you know that this talk was beginning? Increase in movement Fiddling with the projector New presenter looking around
- 4. A Question How did you know that this talk was beginning? Increase in movement Fiddling with the projector New presenter looking around The amount of activity in the room changed
- 5. Frequency-based detection of task switches Rahul Nair Yahoo! Research Berkeley [email_address] Steve Voida & Elizabeth Mynatt Georgia Institute of Technology {svoida, mynatt}@cc.gatech.edu
- 6. People are particular about Displays Users have a ŌĆ£working setŌĆØ of windows related to each task (Henderson 1986) There are distinct differences in window layouts for each task (Hutchins 2004) As interested in hiding windows as they are in displaying task windows (Hutchins 2004)
- 7. A frequency-based approach There is a shift in the window interaction frequencies as users ŌĆ£setupŌĆØ for each task The shift could be either an increase or decrease in the average time between interactions Rearranging windows is as significant as opening or closing them
- 8. Software design Tracks the low level window manipulation Uses a sliding window algorithm to compare current interaction speed with session average If the window average exceeds the thresholds of the session average a switch is logged Best results with a 7 interaction window and a thresholds of 0.67 and 1.5
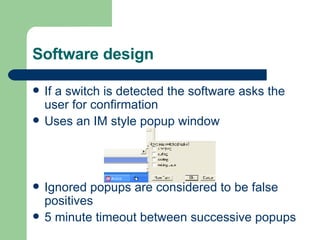
- 9. Software design If a switch is detected the software asks the user for confirmation Uses an IM style popup window Ignored popups are considered to be false positives 5 minute timeout between successive popups
- 10. Study Design 6 participants 2 Professors, 3 grad students, 1 IT professional Installed on their primary work machine 2 week study Followed by questionnaires and interviews
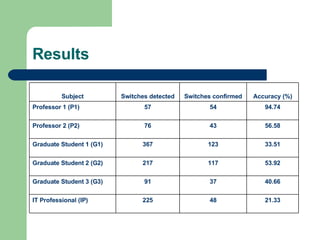
- 11. Results 21.33 48 225 IT Professional (IP) 40.66 37 91 Graduate Student 3 (G3) 53.92 117 217 Graduate Student 2 (G2) 33.51 123 367 Graduate Student 1 (G1) 56.58 43 76 Professor 2 (P2) 94.74 54 57 Professor 1 (P1) Accuracy (%) Switches confirmed Switches detected Subject
- 12. User Feedback P1 was very appreciative and said that almost all her tasks were detected P2 felt that short tasks were not always detected Rapid task switching behavior IP had the lowest accuracy but was the most enthusiastic co-opted out log files to fill out project time cards Noticed all switches but was over sensitive
- 13. The Instant Messaging (IM) Effect Some of the variance can be explained by IM usage High accuracy subjects did not use IM while low accuracy subjects were regular IM users The software detected IM usage as a task switch while the users felt that IM was not a new task Users felt that IM was a side channel of information and were irritated when it was detected as a new task
- 14. Advantages Can have extremely high accuracy Low computational cost Fewer privacy concerns since actual document and activity data is not being tagged Can spot a task switch without requiring identification of the task itself Time management applications
- 15. Future Work Integrating web browser URL information Dynamically adapting to users by adjusting window sizes, threshold values and popup timeouts Allow users to explicitly ignore windows like IM, etcŌĆ”
- 16. Questions? Rahul Nair [email_address] www.rahulnair.net
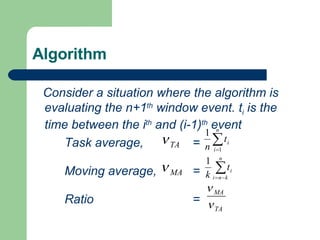
- 17. Consider a situation where the algorithm is evaluating the n+1 th window event. t i is the time between the i th and (i-1) th event Task average, = Moving average, = Ratio = Algorithm
