Gns3moi
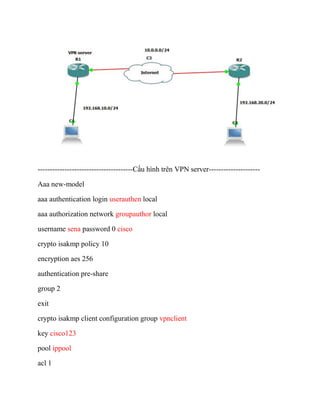
- 1. ---------------------------------------CášĨu hÃŽnh trÊn VPN server--------------------- Aaa new-model aaa authentication login userauthen local aaa authorization network groupauthor local username sena password 0 cisco crypto isakmp policy 10 encryption aes 256 authentication pre-share group 2 exit crypto isakmp client configuration group vpnclient key cisco123 pool ippool acl 1
- 2. exit crypto ipsec transform-set myset esp-3des esp-md5-hmac ex crypto dynamic-map dynmap 10 set transformâset myset reverseâroute ex crypto map clientmap client authentication list userauthen crypto map clientmap isakmp authorization list groupauthor crypto map clientmap client configuration address respond crypto map clientmap 10 ipsecâisakmp dynamic dynmap ip local pool ippool 200.0.0.10 200.0.0.20 access-list 1 permit 192.168.10.0 0.0.0.255 ip nat inside source list 1 interface s0/0/0 overload int f0/0 ip nat inside halfâduplex int s0/0/0 ip nat outside crypto map clientmap
- 3. bÊn R2 cÅĐng cášĨu hÃŽnh NAT acc 1 permit 192.168.20.0 0.0.0.255 ip nat inside sou list 1 int s1/0 over int f2/0 ip nat inside int s1/0 ip nat outside PC 2: Sauk hi cà i cisco VPN client xong bᚥn và o network enable và Äáš·t ip là 192.168.20.3/24
- 4. VÃ o VPN client cháŧn New
- 6. BášĨm save và connect -> ÄÃĄnh user váŧi pass:
- 7. Sau ÄÃģ và o status -> statictisâĶ