Google Hacking for Cryptographic Secrets
- 1. Outline Google Hacking Cryptographic Secrets Automatic Tools Countermeasures Google Code Search Conclusion Google Hacking for Cryptographic Secrets Emin ˙ Islam Tatlı tatli@th.informatik.uni-mannheim.de Department of Computer Science, University of Mannheim NEC Research-Heidelberg, 10 November 2006 ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 2. Outline Google Hacking Cryptographic Secrets Automatic Tools Countermeasures Google Code Search Conclusion Outline 1 Google Hacking 2 Cryptographic Secrets 3 Automatic Tools 4 Countermeasures 5 Google Code Search ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 3. Outline Google Hacking Cryptographic Secrets Motivation Automatic Tools Advanced Search Parameters Countermeasures Examples of Google Hacking Google Code Search Conclusion Motivation Google has the index size over 20 billion entries try to search -"fgkdfgjisdfgjsiod" Hackers use google to search vulnerabilities called Google Hacking vulnerable servers, ’¼üles and applications, ’¼üles containing usernames-passwords, sensitive directories, online devices, etc. Google Hacking Database [1] ŌćÆ 1468 entries in 14 groups (by October 2006) What about Cryptographic Secrets? In this talk, we ’¼ünd out cryptographic secrets with google ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 4. Outline Google Hacking Cryptographic Secrets Motivation Automatic Tools Advanced Search Parameters Countermeasures Examples of Google Hacking Google Code Search Conclusion Advanced Search Parameters [all]inurl [all]intext [all]intitle site ext, ’¼ületype symbols: - . * | ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
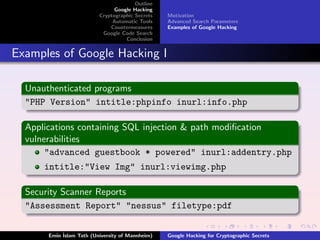
- 5. Outline Google Hacking Cryptographic Secrets Motivation Automatic Tools Advanced Search Parameters Countermeasures Examples of Google Hacking Google Code Search Conclusion Examples of Google Hacking I Unauthenticated programs "PHP Version" intitle:phpinfo inurl:info.php Applications containing SQL injection & path modi’¼ücation vulnerabilities "advanced guestbook * powered" inurl:addentry.php intitle:"View Img" inurl:viewimg.php Security Scanner Reports "Assessment Report" "nessus" filetype:pdf ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
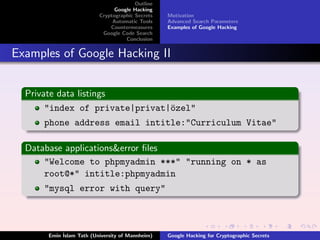
- 6. Outline Google Hacking Cryptographic Secrets Motivation Automatic Tools Advanced Search Parameters Countermeasures Examples of Google Hacking Google Code Search Conclusion Examples of Google Hacking II Private data listings "index of private|privat|┬©zel" o phone address email intitle:"Curriculum Vitae" Database applications&error ’¼üles "Welcome to phpmyadmin ***" "running on * as root@*" intitle:phpmyadmin "mysql error with query" ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 7. Outline Google Hacking Cryptographic Secrets Motivation Automatic Tools Advanced Search Parameters Countermeasures Examples of Google Hacking Google Code Search Conclusion Examples of Google Hacking III Online Devices inurl:"hp/device/this.LCDispatcher" intitle:liveapplet inurl:LvAppl "Please wait....." intitle:"SWW link" ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 8. Outline Hashed Passwords Google Hacking Secret Keys Cryptographic Secrets Public Keys Automatic Tools Private Keys Countermeasures Encrypted Messages Google Code Search Signed Messages Conclusion Cryptographic Secrets 1 Hashed Passwords 2 Secret Keys 3 Public Keys 4 Private Keys 5 Encrypted Messages 6 Signed Messages ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 9. Outline Hashed Passwords Google Hacking Secret Keys Cryptographic Secrets Public Keys Automatic Tools Private Keys Countermeasures Encrypted Messages Google Code Search Signed Messages Conclusion Hashed Passwords Cleartext passwords ext:log inurl:password Hashed passwords in dump ’¼üles "create table" "insert into" "pass|passwd|password" (ext:sql | ext:dump | ext:dmp) intext:"password|pass|passwd" intext:"md5|sha1|crypt" (ext:sql | ext:dump | ext:dmp) ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 10. Outline Hashed Passwords Google Hacking Secret Keys Cryptographic Secrets Public Keys Automatic Tools Private Keys Countermeasures Encrypted Messages Google Code Search Signed Messages Conclusion Secret Keys Secret keys in Kerberos inurl:"kdc.conf" ext:conf inurl:"slave datatrans" OR inurl:"from master" Java keystores keystore ext:ks ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 11. Outline Hashed Passwords Google Hacking Secret Keys Cryptographic Secrets Public Keys Automatic Tools Private Keys Countermeasures Encrypted Messages Google Code Search Signed Messages Conclusion Public Keys PGP public keys "BEGIN PGP PUBLIC KEY BLOCK" (ext:txt | ext:asc | ext:key) Public keys in certi’¼ücates "Certificate:Data:Version" "BEGIN CERTIFICATE" (ext:crt | ext:asc | ext:txt) ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
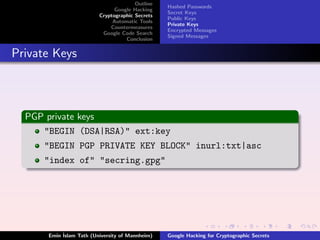
- 12. Outline Hashed Passwords Google Hacking Secret Keys Cryptographic Secrets Public Keys Automatic Tools Private Keys Countermeasures Encrypted Messages Google Code Search Signed Messages Conclusion Private Keys PGP private keys "BEGIN (DSA|RSA)" ext:key "BEGIN PGP PRIVATE KEY BLOCK" inurl:txt|asc "index of" "secring.gpg" ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 13. Outline Hashed Passwords Google Hacking Secret Keys Cryptographic Secrets Public Keys Automatic Tools Private Keys Countermeasures Encrypted Messages Google Code Search Signed Messages Conclusion Encrypted Messages PGP encrypted ’¼üles -"public|pubring|pubkey| signature|pgp|and|or|release" ext:gpg More encrypted ’¼üles -intext:"and" (ext:enc | ext:axx) XML encrypted elements "ciphervalue" ext:xml ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 14. Outline Hashed Passwords Google Hacking Secret Keys Cryptographic Secrets Public Keys Automatic Tools Private Keys Countermeasures Encrypted Messages Google Code Search Signed Messages Conclusion Signed Messages Signed emails "BEGIN PGP SIGNED MESSAGE" "From" "Date" "Subject" (ext:eml | ext:txt | ext:asc) File signatures -"and|or" "BEGIN PGP SIGNATURE" ext:asc PGP signed messages "BEGIN PGP SIGNED MESSAGE" -"From" (ext:txt | ext:asc | ext:xml) ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 15. Outline Google Hacking Gooscan Cryptographic Secrets Sitedigger Automatic Tools Goolink Countermeasures AdvancedDork Google Code Search Google Advanced Operations Toolbar Conclusion Automatic Tools 1 Gooscan 2 Sitedigger 3 Goolink 4 AdvancedDork 5 Google Advanced Operation Toolbar ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 16. Outline Google Hacking Gooscan Cryptographic Secrets Sitedigger Automatic Tools Goolink Countermeasures AdvancedDork Google Code Search Google Advanced Operations Toolbar Conclusion Gooscan [7] a Unix/Linux script to check google hacking queries against your system uses GHD [1] to execute: $ gooscan -t www.google.de -q "BEGIN (DSA|RSA) ext:key" -s de -o output.html ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 17. Outline Google Hacking Gooscan Cryptographic Secrets Sitedigger Automatic Tools Goolink Countermeasures AdvancedDork Google Code Search Google Advanced Operations Toolbar Conclusion Sitedigger [6] free from Foundstone company supports both GHD and FoundstoneŌĆÖs own hacking database for a given host, all entries in the database are queried ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 18. Outline Google Hacking Gooscan Cryptographic Secrets Sitedigger Automatic Tools Goolink Countermeasures AdvancedDork Google Code Search Google Advanced Operations Toolbar Conclusion Goolink [5] Goolink queries Google for a particular chosen search from GHD ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 19. Outline Google Hacking Gooscan Cryptographic Secrets Sitedigger Automatic Tools Goolink Countermeasures AdvancedDork Google Code Search Google Advanced Operations Toolbar Conclusion AdvancedDork [2] not speci’¼üc to google hacking a Firefox extension for google searches ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 20. Outline Google Hacking Gooscan Cryptographic Secrets Sitedigger Automatic Tools Goolink Countermeasures AdvancedDork Google Code Search Google Advanced Operations Toolbar Conclusion Google Advanced Operations Toolbar [3] a Firefox extension provides a shortcut of GoogleŌĆÖs advanced search functions ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 21. Outline Google Hacking Cryptographic Secrets Automatic Tools Countermeasures Google Code Search Conclusion Security Countermeasures 1 Use automatic tools to check your system 2 Use Robot Exclusion Standart (robots.txt) 3 Install and manage Google Honeypot [4] ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 22. Outline Google Hacking Cryptographic Secrets Automatic Tools Countermeasures Google Code Search Conclusion Google Code Search search keywords within source ’¼üles (www.google.com/codesearch) ’¼ünd application bugs (e.g. sql injection, xss injection, bu’¼Ćer over’¼éows, etc.) in the source ’¼üles ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 23. Outline Google Hacking Cryptographic Secrets Automatic Tools Countermeasures Google Code Search Conclusion Conclusion Cryptography requires secrets to be kept secret Google indexes your secrets and makes public Take the required security countermeasures and protect your secrets ˙ Emin Islam Tatlı (University of Mannheim) Google Hacking for Cryptographic Secrets
- 24. Outline Google Hacking Cryptographic Secrets Automatic Tools Countermeasures Google Code Search Conclusion References I Google Hacking Database. http://johnny.ihackstu’¼Ć.com AdvancedDork- A Firefox extension for google searches. http://johnny.ihackstu’¼Ć.com Google Advanced Operation Toolbar. https://addons.mozilla.org/’¼ürefox/1258/ Google Hack Honeypot Project. http://ghh.sourceforge.net Goolink- Security Scanner. www.ghacks.net/2005/11/23/goolink-scanner-beta-preview/ ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets
- 25. Outline Google Hacking Cryptographic Secrets Automatic Tools Countermeasures Google Code Search Conclusion References II SiteDigger v2.0 - Information Gathering Tool. http://www.foundstone.com Gooscan - Google Security Scanner. http://johnny.ihackstu’¼Ć.com ╦Ö Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets



![Outline
Google Hacking
Cryptographic Secrets Motivation
Automatic Tools Advanced Search Parameters
Countermeasures Examples of Google Hacking
Google Code Search
Conclusion
Motivation
Google has the index size over 20 billion entries
try to search -"fgkdfgjisdfgjsiod"
Hackers use google to search vulnerabilities
called Google Hacking
vulnerable servers, ’¼üles and applications, ’¼üles containing
usernames-passwords, sensitive directories, online devices, etc.
Google Hacking Database [1] ŌćÆ 1468 entries in 14 groups (by
October 2006)
What about Cryptographic Secrets?
In this talk, we ’¼ünd out cryptographic secrets with google
˙
Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets](https://image.slidesharecdn.com/ghackcryptopresentationnec-121212160006-phpapp02/85/Google-Hacking-for-Cryptographic-Secrets-3-320.jpg)
![Outline
Google Hacking
Cryptographic Secrets Motivation
Automatic Tools Advanced Search Parameters
Countermeasures Examples of Google Hacking
Google Code Search
Conclusion
Advanced Search Parameters
[all]inurl
[all]intext
[all]intitle
site
ext, ’¼ületype
symbols: - . * |
˙
Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets](https://image.slidesharecdn.com/ghackcryptopresentationnec-121212160006-phpapp02/85/Google-Hacking-for-Cryptographic-Secrets-4-320.jpg)








![Outline
Google Hacking Gooscan
Cryptographic Secrets Sitedigger
Automatic Tools Goolink
Countermeasures AdvancedDork
Google Code Search Google Advanced Operations Toolbar
Conclusion
Gooscan [7]
a Unix/Linux script to check google hacking queries against
your system
uses GHD [1]
to execute:
$ gooscan -t www.google.de -q "BEGIN (DSA|RSA)
ext:key" -s de -o output.html
˙
Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets](https://image.slidesharecdn.com/ghackcryptopresentationnec-121212160006-phpapp02/85/Google-Hacking-for-Cryptographic-Secrets-16-320.jpg)
![Outline
Google Hacking Gooscan
Cryptographic Secrets Sitedigger
Automatic Tools Goolink
Countermeasures AdvancedDork
Google Code Search Google Advanced Operations Toolbar
Conclusion
Sitedigger [6]
free from Foundstone
company
supports both GHD and
FoundstoneŌĆÖs own hacking
database
for a given host, all entries in
the database are queried
˙
Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets](https://image.slidesharecdn.com/ghackcryptopresentationnec-121212160006-phpapp02/85/Google-Hacking-for-Cryptographic-Secrets-17-320.jpg)
![Outline
Google Hacking Gooscan
Cryptographic Secrets Sitedigger
Automatic Tools Goolink
Countermeasures AdvancedDork
Google Code Search Google Advanced Operations Toolbar
Conclusion
Goolink [5]
Goolink queries Google for a
particular chosen search from
GHD
˙
Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets](https://image.slidesharecdn.com/ghackcryptopresentationnec-121212160006-phpapp02/85/Google-Hacking-for-Cryptographic-Secrets-18-320.jpg)
![Outline
Google Hacking Gooscan
Cryptographic Secrets Sitedigger
Automatic Tools Goolink
Countermeasures AdvancedDork
Google Code Search Google Advanced Operations Toolbar
Conclusion
AdvancedDork [2]
not speci’¼üc to google
hacking
a Firefox extension for google
searches
˙
Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets](https://image.slidesharecdn.com/ghackcryptopresentationnec-121212160006-phpapp02/85/Google-Hacking-for-Cryptographic-Secrets-19-320.jpg)
![Outline
Google Hacking Gooscan
Cryptographic Secrets Sitedigger
Automatic Tools Goolink
Countermeasures AdvancedDork
Google Code Search Google Advanced Operations Toolbar
Conclusion
Google Advanced Operations Toolbar [3]
a Firefox extension
provides a shortcut of GoogleŌĆÖs advanced search functions
˙
Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets](https://image.slidesharecdn.com/ghackcryptopresentationnec-121212160006-phpapp02/85/Google-Hacking-for-Cryptographic-Secrets-20-320.jpg)
![Outline
Google Hacking
Cryptographic Secrets
Automatic Tools
Countermeasures
Google Code Search
Conclusion
Security Countermeasures
1 Use automatic tools to check your system
2 Use Robot Exclusion Standart (robots.txt)
3 Install and manage Google Honeypot [4]
˙
Emin Islam Tatl─▒ (University of Mannheim) Google Hacking for Cryptographic Secrets](https://image.slidesharecdn.com/ghackcryptopresentationnec-121212160006-phpapp02/85/Google-Hacking-for-Cryptographic-Secrets-21-320.jpg)



