Group 6
Download as pptx, pdf1 like269 views
The document discusses encryption and decryption techniques. It introduces symmetric-key cryptography, where the sender and receiver share a single key, and public-key cryptography, which avoids the problem of secure key exchange. It then discusses the Data Encryption Standard (DES) algorithm, which transforms 64-bit blocks of data using a complex computation controlled by a 64-bit key. DES applies initial and final permutations to the data and uses a cipher function and key schedule for the encryption.
1 of 12
Download to read offline








Ad
Recommended
Criptography
CriptographySajan Sahu
╠²
This document provides an overview of cryptography. It discusses traditional cryptography techniques like the Caesar cipher and shift ciphers. It also explains symmetric and asymmetric key cryptography, giving examples like DES, RSA, and their uses. Cryptographic services like authentication, data integrity, non-repudiation, and confidentiality are mentioned. The document notes how cryptography is widely used today in network security, banking transactions, and military communications.Cryptography
Cryptographyresearch30
╠²
Cryptography is used to protect information by encrypting messages into an unreadable cipher text format. Modern cryptography uses either secret key cryptography, which uses a single key for encryption and decryption, or public key cryptography, which uses two mathematically related keys with one key to encrypt and the other to decrypt. The purpose of cryptography and security is to defend against hackers, industrial espionage, and to secure e-commerce, bank accounts, intellectual property, and avoid liability.Public key Cryptography & RSA
Public key Cryptography & RSAAmit Debnath
╠²
Public-key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts them, allowing secure communication without secretly exchanging keys. It was a major advance in cryptography and enables applications like encryption for security and digital signatures for authentication. The RSA algorithm is an example of public-key cryptography that revolutionized encryption by using this two-key system.Cryptography
CryptographySagar Janagonda
╠²
This document discusses cryptography and its various aspects. Cryptography is the science of securing communication and information. It involves encryption to encode data into an unreadable format and decryption to decode it. There are different types of cryptography like symmetric key, public key, and hash functions. Symmetric key uses a single key for encryption and decryption while public key uses different keys. Hash functions create a unique digest from data but the data cannot be recovered from the digest. Cryptography provides security features like authentication, privacy, integrity and non-repudiation. Keys are numerical values used in encryption algorithms. The document outlines advantages like privacy and disadvantages like the time needed for encryption and decryption.Cryptography
Cryptographyherrberk
╠²
This document discusses the science of encryption through three main topics: the purpose and history of cryptography, modern cryptography techniques, and password security. It describes cryptography as the science of secure communications and its goals of authentication, privacy, integrity, and non-repudiation. The history of cryptography is divided into ancient uses and electro-mechanical machines of World War II. Modern techniques discussed are secret key cryptography, hash functions, and public key cryptography. It emphasizes the importance of strong, unique passwords for security.Caesar cipher
Caesar cipherTechnical Hub
╠²
The project titled 'Caesar Cipher' explores various cipher codes, guiding users from basic to advanced encryption techniques. It emphasizes the importance of cryptography for secure communications and data protection, illustrating three stages: ancient ciphers, polyalphabetic ciphers, and creation of a custom cipher algorithm. The culmination of the project includes a website to access these ciphers and promote the benefits of cryptography in enhancing security.Cryptography
Cryptography žŻžŁ┘䞦┘ģ ž¦┘åžĄž¦ž▒┘ē
╠²
Cryptography is the practice of hiding information and involves techniques like secret key cryptography, public key cryptography, and hash functions. New trends in cryptography include elliptic curve cryptography, which uses points on elliptic curves to securely exchange keys, quantum cryptography which uses quantum effects for secure communication, and pairing based cryptography which pairs elements of groups to construct hybrid cryptosystems. The document discusses different encryption techniques, their drawbacks, and the need for new techniques that are more secure against attacks.Cryptography basices
Cryptography basicesSiddique Ibrahim
╠²
Cryptography is the practice and study of techniques for secure communication in the presence of third parties. It involves encrypting plaintext messages into ciphertext that can only be decrypted by authorized parties. There are two main categories of cryptography: symmetric key cryptography which uses the same key for encryption and decryption, and asymmetric key cryptography which uses separate public and private keys. Network security relies heavily on cryptography to protect data transmission over the internet.Information Security Cryptography ( L01- introduction )
Information Security Cryptography ( L01- introduction )Anas Rock
╠²
The document serves as an introduction to cryptography, detailing its historical context, definitions, and key goals such as confidentiality, integrity, and availability. It explains the processes of encryption and decryption and highlights the importance of cryptographic keys, distinguishing between public and private keys. The document sets the stage for further discussion on types of encryption in subsequent sections.Encryption presentation final
Encryption presentation finaladrigee12
╠²
The document provides an overview of encryption, including what it is, why it is used, and how it works. Encryption is the process of encoding information to protect it, while decryption is decoding the information. There are two main types of encryption: asymmetric encryption which uses public and private keys, and symmetric encryption which uses a shared key. Encryption is used to secure important data like health records, credit cards, and student information from being stolen or read without permission. It allows senders to encode plain text into ciphertext using a key.Advanced cryptography and implementation
Advanced cryptography and implementationAkash Jadhav
╠²
The document discusses a technical presentation on advanced cryptography and its implementation. It provides an overview of cryptography, including its history and basic concepts such as encryption, decryption, and cryptanalysis. Examples of cryptography applications discussed include ATM cards, credit cards, e-mail, and lottery tickets. Cryptography and network security
Cryptography and network securityMahipesh Satija
╠²
The document discusses various algorithms and techniques in cryptography and network security, highlighting the importance of secure communication in the presence of adversaries. It presents a range of methods including the Tiny algorithm, image and audio steganography, the Rijndael algorithm, and a hybrid port knocking system to enhance security. The proposal aims to combine these techniques to mitigate individual weaknesses and improve the overall security of file sharing.Encryption
EncryptionSyed Taimoor Hussain Shah
╠²
The document outlines types of encryption, specifically symmetric and asymmetric encryption, along with their uses and drawbacks. It also explains hashing, its properties, uses, and distinctions from encryption. The discussion highlights the challenges associated with each method, such as key management and security vulnerabilities.Information Security & Cryptography
Information Security & CryptographyArun ACE
╠²
This document provides an overview of information security and cryptography. It discusses objectives of security like avoiding data threats. It also covers topics like password auditing, data security, authentication, encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. It demonstrates an example of encrypting a message using RSA and decrypting the cipher text. The conclusion emphasizes the importance of information security.Cryptography ppt ,computer system security. PPT
Cryptography ppt ,computer system security. PPTARYANUNIVERSE
╠²
This document discusses cryptography and how it provides security. It defines basic cryptography terms like plain text, cipher text, encryption, and decryption. It explains how cryptography works to secure communications from both passive and active security threats. The document also categorizes different types of cryptography like symmetric and asymmetric key cryptography, and compares how each uses keys to encrypt and decrypt messages. Applications of cryptography are listed as well.Cryptography
CryptographyVicky Kamboj
╠²
Secret writing refers to cryptography and steganography. Cryptography involves encrypting messages so only authorized users can read them, while steganography hides information within other files or mediums. Common cryptographic techniques include symmetric and asymmetric encryption methods. Symmetric encryption uses a shared key between sender and receiver, while asymmetric encryption uses public and private key pairs. Steganography hides information by embedding it within images or other files.Cryptography
CryptographyVishalya Dulam
╠²
This document provides an overview of cryptography techniques. It discusses modern cryptography methods like DES and DSA, how cryptography is used in applications like VPNs and secure web browsing. It also summarizes Windows authentication methods used in operating systems from Windows NT to Windows Server 2012, and the Kerberos authentication protocol.Cryptography
CryptographySandip kumar
╠²
This document discusses cryptography and some of its key concepts. It defines cryptography as the science of secret writing and describes how it can be used to securely transmit messages and protect information. It then summarizes some common issues in cryptography like confidentiality, authentication, and integrity. It also defines important cryptography terms like plaintext, ciphertext, ciphers, keys, symmetric and asymmetric algorithms. Specific algorithms like DES, AES, RSA are also outlined at a high level.Overview of cryptography
Overview of cryptographyRoshan Chaudhary
╠²
This document provides an overview of cryptography. It discusses that cryptography is the practice of secure communication in the presence of others. The purpose of cryptography is to defend against hackers and industrial espionage while securing e-commerce, bank accounts, intellectual property, and avoiding liability. Cryptography provides authentication, privacy, integrity, and non-repudiation. Encryption converts plain text to cipher text using a key while decryption converts cipher text to plain text. Common cryptographic algorithms are secret key cryptography, public key cryptography, and hash functions. Secret key cryptography uses a private key for encryption while public key cryptography uses a public key exchanged over an insecure channel. Hash functions produce a checksum of data. AES encryption is now commonly used andCryptography by Durlab Kumbhakar
Cryptography by Durlab KumbhakarDurlove Kumbhakar
╠²
Cryptography is the practice of hiding information to store or communicate it in a secure way. It allows for confidentiality, integrity, and authentication of messages. There are two main types: symmetric key cryptography which uses a single key for encryption and decryption, and asymmetric key cryptography which uses different public and private keys. Popular symmetric algorithms include AES and DES, while RSA is an example of an asymmetric algorithm. The seminar discussed the components, processes, and applications of cryptography as well as examples of algorithms and common attacks.Symmetric & Asymmetric Cryptography
Symmetric & Asymmetric Cryptographychauhankapil
╠²
This document summarizes symmetric and asymmetric cryptography. Symmetric cryptography involves both parties agreeing on an encryption algorithm and key beforehand to encrypt and decrypt messages. Asymmetric cryptography uses public and private key pairs, where the public key encrypts messages and the private key decrypts them, allowing encryption without pre-sharing keys. It also discusses digital signatures, where messages are signed with a private key and verified with the corresponding public key. Common attacks on public-key cryptography like man-in-the-middle attacks are addressed. The document is intended for a computer science course on cryptography fundamentals and security mechanisms.Basic Cryptography unit 4 CSS
Basic Cryptography unit 4 CSSDr. SURBHI SAROHA
╠²
The document discusses various topics related to public key cryptography including:
1) Public key cryptography uses key pairs (public/private keys) to encrypt and decrypt messages securely. Private keys are kept secret while public keys can be openly distributed.
2) RSA is a commonly used public key cryptosystem that uses large prime numbers to encrypt data. It is considered secure if a large enough key is used.
3) Digital signatures authenticate messages by encrypting a hash of the message with the sender's private key, allowing verification with their public key.Encryption
EncryptionNitin Parbhakar
╠²
This presentation discusses various aspects of data encryption. It defines data encryption as mathematical calculations and algorithms that transform plain text into ciphertext. It then covers the main types of encryption, distinguishing between symmetric encryption which uses the same key for encryption and decryption, and asymmetric encryption which uses different public and private keys. The presentation also explains some common encryption methods like the Data Encryption Standard and public key cryptosystems.Cryptography and network security
Cryptography and network security Mathan Gopal
╠²
This document provides an overview of cryptography and network security. It discusses what cryptography is, the basic terminology used in cryptography like plaintext, ciphertext, encryption, algorithms and keys. It explains the two main types of cryptographic functions: symmetric key cryptography which uses a single shared key between sender and receiver, and asymmetric key cryptography which uses public and private key pairs. It also outlines two network security models - the model for network security and the network access security model.Cryptography
Cryptographyokolo chukwudumebi prince
╠²
The document discusses various cryptographic concepts and algorithms. It begins with basic terms in cryptography like plain text, cipher text, encryption, decryption, and keys. It then explains symmetric and asymmetric key cryptography. Specific algorithms discussed include MD5, SHA-1, SHA-256, RIPEMD-160, and crypt. Code examples are provided to demonstrate generating hashes using these algorithms.Data encryption
Data encryptionDeepam Goyal
╠²
This document discusses data encryption and digital signatures. It defines encryption as disguising information so that only those with the key can access it. There are two main types of encryption - symmetric which uses the same key for encryption and decryption, and asymmetric which uses different keys. Encryption methods include transposition, which rearranges bits or characters, and substitution, which replaces bits or characters. Popular algorithms discussed are DES, RSA, and digital signatures. Digital signatures authenticate the sender, ensure the message isn't altered, and can be used to sign documents and verify certificates from certificate authorities.Encryption/Decryption Algorithm for Devanagri Script(Affine Cipher)
Encryption/Decryption Algorithm for Devanagri Script(Affine Cipher)Swati Nagpal
╠²
The document discusses the design and implementation of an encryption/decryption scheme for Devanagari script using the affine cipher, a mathematical function that maps letters to numeric values. It outlines the encryption and decryption processes, key calculation methods, and provides algorithms for implementation along with time and space complexity analysis. The conclusion emphasizes the uniqueness of the affine cipher's key determination based on character unicodes.Encryption And Decryption
Encryption And DecryptionNA
╠²
This document discusses encryption and decryption. It was developed by four students and submitted to their professor. The document introduces encryption as converting plaintext to ciphertext and decryption as converting ciphertext back to plaintext. It explains that encryption uses a key to scramble the plaintext and decryption uses the same key to unscramble the ciphertext to retrieve the original plaintext. The document also briefly mentions the feasibility study, methodology, purpose of providing security, and system requirements for the encryption/decryption software.Results presentation 4 q13_2013_eng_vfinal
Results presentation 4 q13_2013_eng_vfinalLPS Brasil - Consultoria de Im├│veis S.A.
╠²
The document provides an overview of LPS Brasil's 2013/4Q13 presentation. It summarizes the following key points:
1) LPS Brasil had its best year ever in 2013 with total transactions of R$19.9 billion, including a record R$14.9 billion in the primary market.
2) Net revenue reached R$503.8 million, up 22% from 2012. Adjusted EBITDA was R$171.9 million, the best result achieved by the company.
3) CrediPronto! originated a volume of R$2 billion in mortgages, up 34% from 2012. Its mortgage loan portfolio reached R$4 billion, increasing 45FT Partners Research: Transaction Security - At the Nexus of E-Commerce, Paym...
FT Partners Research: Transaction Security - At the Nexus of E-Commerce, Paym...FT Partners / Financial Technology Partners
╠²
The document discusses the growing demand for transaction security solutions due to the rise of e-commerce and mobile payments, which have increased the prevalence of card-not-present (CNP) fraud. It highlights various authentication and fraud prevention technologies while detailing the financial implications for merchants and the complexity of the evolving payment ecosystem. Furthermore, it cites increased private equity interest and anticipated M&A activity in the transaction security sector, indicating it as a rapidly expanding area within financial technology.More Related Content
What's hot (20)
Information Security Cryptography ( L01- introduction )
Information Security Cryptography ( L01- introduction )Anas Rock
╠²
The document serves as an introduction to cryptography, detailing its historical context, definitions, and key goals such as confidentiality, integrity, and availability. It explains the processes of encryption and decryption and highlights the importance of cryptographic keys, distinguishing between public and private keys. The document sets the stage for further discussion on types of encryption in subsequent sections.Encryption presentation final
Encryption presentation finaladrigee12
╠²
The document provides an overview of encryption, including what it is, why it is used, and how it works. Encryption is the process of encoding information to protect it, while decryption is decoding the information. There are two main types of encryption: asymmetric encryption which uses public and private keys, and symmetric encryption which uses a shared key. Encryption is used to secure important data like health records, credit cards, and student information from being stolen or read without permission. It allows senders to encode plain text into ciphertext using a key.Advanced cryptography and implementation
Advanced cryptography and implementationAkash Jadhav
╠²
The document discusses a technical presentation on advanced cryptography and its implementation. It provides an overview of cryptography, including its history and basic concepts such as encryption, decryption, and cryptanalysis. Examples of cryptography applications discussed include ATM cards, credit cards, e-mail, and lottery tickets. Cryptography and network security
Cryptography and network securityMahipesh Satija
╠²
The document discusses various algorithms and techniques in cryptography and network security, highlighting the importance of secure communication in the presence of adversaries. It presents a range of methods including the Tiny algorithm, image and audio steganography, the Rijndael algorithm, and a hybrid port knocking system to enhance security. The proposal aims to combine these techniques to mitigate individual weaknesses and improve the overall security of file sharing.Encryption
EncryptionSyed Taimoor Hussain Shah
╠²
The document outlines types of encryption, specifically symmetric and asymmetric encryption, along with their uses and drawbacks. It also explains hashing, its properties, uses, and distinctions from encryption. The discussion highlights the challenges associated with each method, such as key management and security vulnerabilities.Information Security & Cryptography
Information Security & CryptographyArun ACE
╠²
This document provides an overview of information security and cryptography. It discusses objectives of security like avoiding data threats. It also covers topics like password auditing, data security, authentication, encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. It demonstrates an example of encrypting a message using RSA and decrypting the cipher text. The conclusion emphasizes the importance of information security.Cryptography ppt ,computer system security. PPT
Cryptography ppt ,computer system security. PPTARYANUNIVERSE
╠²
This document discusses cryptography and how it provides security. It defines basic cryptography terms like plain text, cipher text, encryption, and decryption. It explains how cryptography works to secure communications from both passive and active security threats. The document also categorizes different types of cryptography like symmetric and asymmetric key cryptography, and compares how each uses keys to encrypt and decrypt messages. Applications of cryptography are listed as well.Cryptography
CryptographyVicky Kamboj
╠²
Secret writing refers to cryptography and steganography. Cryptography involves encrypting messages so only authorized users can read them, while steganography hides information within other files or mediums. Common cryptographic techniques include symmetric and asymmetric encryption methods. Symmetric encryption uses a shared key between sender and receiver, while asymmetric encryption uses public and private key pairs. Steganography hides information by embedding it within images or other files.Cryptography
CryptographyVishalya Dulam
╠²
This document provides an overview of cryptography techniques. It discusses modern cryptography methods like DES and DSA, how cryptography is used in applications like VPNs and secure web browsing. It also summarizes Windows authentication methods used in operating systems from Windows NT to Windows Server 2012, and the Kerberos authentication protocol.Cryptography
CryptographySandip kumar
╠²
This document discusses cryptography and some of its key concepts. It defines cryptography as the science of secret writing and describes how it can be used to securely transmit messages and protect information. It then summarizes some common issues in cryptography like confidentiality, authentication, and integrity. It also defines important cryptography terms like plaintext, ciphertext, ciphers, keys, symmetric and asymmetric algorithms. Specific algorithms like DES, AES, RSA are also outlined at a high level.Overview of cryptography
Overview of cryptographyRoshan Chaudhary
╠²
This document provides an overview of cryptography. It discusses that cryptography is the practice of secure communication in the presence of others. The purpose of cryptography is to defend against hackers and industrial espionage while securing e-commerce, bank accounts, intellectual property, and avoiding liability. Cryptography provides authentication, privacy, integrity, and non-repudiation. Encryption converts plain text to cipher text using a key while decryption converts cipher text to plain text. Common cryptographic algorithms are secret key cryptography, public key cryptography, and hash functions. Secret key cryptography uses a private key for encryption while public key cryptography uses a public key exchanged over an insecure channel. Hash functions produce a checksum of data. AES encryption is now commonly used andCryptography by Durlab Kumbhakar
Cryptography by Durlab KumbhakarDurlove Kumbhakar
╠²
Cryptography is the practice of hiding information to store or communicate it in a secure way. It allows for confidentiality, integrity, and authentication of messages. There are two main types: symmetric key cryptography which uses a single key for encryption and decryption, and asymmetric key cryptography which uses different public and private keys. Popular symmetric algorithms include AES and DES, while RSA is an example of an asymmetric algorithm. The seminar discussed the components, processes, and applications of cryptography as well as examples of algorithms and common attacks.Symmetric & Asymmetric Cryptography
Symmetric & Asymmetric Cryptographychauhankapil
╠²
This document summarizes symmetric and asymmetric cryptography. Symmetric cryptography involves both parties agreeing on an encryption algorithm and key beforehand to encrypt and decrypt messages. Asymmetric cryptography uses public and private key pairs, where the public key encrypts messages and the private key decrypts them, allowing encryption without pre-sharing keys. It also discusses digital signatures, where messages are signed with a private key and verified with the corresponding public key. Common attacks on public-key cryptography like man-in-the-middle attacks are addressed. The document is intended for a computer science course on cryptography fundamentals and security mechanisms.Basic Cryptography unit 4 CSS
Basic Cryptography unit 4 CSSDr. SURBHI SAROHA
╠²
The document discusses various topics related to public key cryptography including:
1) Public key cryptography uses key pairs (public/private keys) to encrypt and decrypt messages securely. Private keys are kept secret while public keys can be openly distributed.
2) RSA is a commonly used public key cryptosystem that uses large prime numbers to encrypt data. It is considered secure if a large enough key is used.
3) Digital signatures authenticate messages by encrypting a hash of the message with the sender's private key, allowing verification with their public key.Encryption
EncryptionNitin Parbhakar
╠²
This presentation discusses various aspects of data encryption. It defines data encryption as mathematical calculations and algorithms that transform plain text into ciphertext. It then covers the main types of encryption, distinguishing between symmetric encryption which uses the same key for encryption and decryption, and asymmetric encryption which uses different public and private keys. The presentation also explains some common encryption methods like the Data Encryption Standard and public key cryptosystems.Cryptography and network security
Cryptography and network security Mathan Gopal
╠²
This document provides an overview of cryptography and network security. It discusses what cryptography is, the basic terminology used in cryptography like plaintext, ciphertext, encryption, algorithms and keys. It explains the two main types of cryptographic functions: symmetric key cryptography which uses a single shared key between sender and receiver, and asymmetric key cryptography which uses public and private key pairs. It also outlines two network security models - the model for network security and the network access security model.Cryptography
Cryptographyokolo chukwudumebi prince
╠²
The document discusses various cryptographic concepts and algorithms. It begins with basic terms in cryptography like plain text, cipher text, encryption, decryption, and keys. It then explains symmetric and asymmetric key cryptography. Specific algorithms discussed include MD5, SHA-1, SHA-256, RIPEMD-160, and crypt. Code examples are provided to demonstrate generating hashes using these algorithms.Data encryption
Data encryptionDeepam Goyal
╠²
This document discusses data encryption and digital signatures. It defines encryption as disguising information so that only those with the key can access it. There are two main types of encryption - symmetric which uses the same key for encryption and decryption, and asymmetric which uses different keys. Encryption methods include transposition, which rearranges bits or characters, and substitution, which replaces bits or characters. Popular algorithms discussed are DES, RSA, and digital signatures. Digital signatures authenticate the sender, ensure the message isn't altered, and can be used to sign documents and verify certificates from certificate authorities.Encryption/Decryption Algorithm for Devanagri Script(Affine Cipher)
Encryption/Decryption Algorithm for Devanagri Script(Affine Cipher)Swati Nagpal
╠²
The document discusses the design and implementation of an encryption/decryption scheme for Devanagari script using the affine cipher, a mathematical function that maps letters to numeric values. It outlines the encryption and decryption processes, key calculation methods, and provides algorithms for implementation along with time and space complexity analysis. The conclusion emphasizes the uniqueness of the affine cipher's key determination based on character unicodes.Encryption And Decryption
Encryption And DecryptionNA
╠²
This document discusses encryption and decryption. It was developed by four students and submitted to their professor. The document introduces encryption as converting plaintext to ciphertext and decryption as converting ciphertext back to plaintext. It explains that encryption uses a key to scramble the plaintext and decryption uses the same key to unscramble the ciphertext to retrieve the original plaintext. The document also briefly mentions the feasibility study, methodology, purpose of providing security, and system requirements for the encryption/decryption software.Viewers also liked (8)
Results presentation 4 q13_2013_eng_vfinal
Results presentation 4 q13_2013_eng_vfinalLPS Brasil - Consultoria de Im├│veis S.A.
╠²
The document provides an overview of LPS Brasil's 2013/4Q13 presentation. It summarizes the following key points:
1) LPS Brasil had its best year ever in 2013 with total transactions of R$19.9 billion, including a record R$14.9 billion in the primary market.
2) Net revenue reached R$503.8 million, up 22% from 2012. Adjusted EBITDA was R$171.9 million, the best result achieved by the company.
3) CrediPronto! originated a volume of R$2 billion in mortgages, up 34% from 2012. Its mortgage loan portfolio reached R$4 billion, increasing 45FT Partners Research: Transaction Security - At the Nexus of E-Commerce, Paym...
FT Partners Research: Transaction Security - At the Nexus of E-Commerce, Paym...FT Partners / Financial Technology Partners
╠²
The document discusses the growing demand for transaction security solutions due to the rise of e-commerce and mobile payments, which have increased the prevalence of card-not-present (CNP) fraud. It highlights various authentication and fraud prevention technologies while detailing the financial implications for merchants and the complexity of the evolving payment ecosystem. Furthermore, it cites increased private equity interest and anticipated M&A activity in the transaction security sector, indicating it as a rapidly expanding area within financial technology.Secure electronic transaction (set)
Secure electronic transaction (set)Agn─Ś Chomentauskait─Ś
╠²
SET was developed by Visa and MasterCard to securely transmit credit and debit card information over the internet. It uses public key encryption and digital certificates to authenticate parties and encrypt transactions for confidentiality. All parties must have digital certificates and information is only shared when necessary to protect privacy. SET supports common transaction types and uses technologies like 3DES, RSA signatures, and SHA-1 hashing to provide security.Network security for E-Commerce
Network security for E-CommerceHem Pokhrel
╠²
The document outlines network security concepts in the context of e-commerce, focusing on trends and common practices for protecting data and communication. It discusses various types of security attacks, including client/server security, data and transaction security, and several preventive measures such as encryption, firewalls, and biometric systems. Additionally, it highlights the importance of risk management and the evaluation of security vulnerabilities in electronic commerce environments.Ec2009 ch10 e commerce security
Ec2009 ch10 e commerce securityNuth Otanasap
╠²
The document discusses security issues and threats related to e-commerce. It describes common security practices for organizations of different sizes and summarizes key learning objectives around e-commerce security. Specific topics covered include brute force credit card attacks, security requirements, types of threats and attacks (e.g. denial of service, malware), common mistakes in managing security risks, and methods for securing e-commerce communications and networks.Classical Encryption Techniques in Network Security
Classical Encryption Techniques in Network Securitybabak danyal
╠²
The document provides an overview of classical encryption techniques, including: symmetric ciphers that use the same key for encryption and decryption (such as the Caesar cipher, monoalphabetic ciphers like the Playfair cipher, and polyalphabetic ciphers like the Vigen├©re cipher) as well as transposition techniques that rearrange plaintext; rotor machines like the Enigma that implemented complex polyalphabetic substitution; and steganography that hides messages within other files or messages. The goal is to introduce basic concepts and terminology of encryption to prepare for studying modern cryptography.Cryptography and Encryptions,Network Security,Caesar Cipher
Cryptography and Encryptions,Network Security,Caesar CipherGopal Sakarkar
╠²
The document discusses network security concepts including:
1. Four principles of security are defined: confidentiality, authentication, integrity, and non-repudiation.
2. Security attacks are classified into two categories: passive attacks and active attacks. Common examples like traffic analysis and message modification are described.
3. Network security is important to prevent billions of dollars in losses each year from security breaches and theft of sensitive data.Security in E-commerce
Security in E-commercem8817
╠²
The document discusses security threats and solutions for e-commerce. It outlines various threats like human error, espionage, hacking and fraud. It then describes goals of network security like confidentiality, integrity and authentication. Further, it explains encryption techniques like symmetric algorithms (DES, 3DES, AES), asymmetric algorithms and digital signatures to secure e-commerce transactions and communication channels. Key requirements for e-commerce security are also highlighted such as message privacy, integrity, authentication and non-repudiation of transactions.FT Partners Research: Transaction Security - At the Nexus of E-Commerce, Paym...
FT Partners Research: Transaction Security - At the Nexus of E-Commerce, Paym...FT Partners / Financial Technology Partners
╠²
Ad
Similar to Group 6 (20)
Cryptography ppt
Cryptography pptAnubhav Sokhal
╠²
This document discusses cryptography, which is the science of secure communication. It covers the basics of cryptography including its objectives, components, terminology, types, and advantages. Specifically, it explains how cryptography ensures confidentiality, integrity, and authentication of information. It also discusses symmetric and asymmetric encryption methods. Symmetric encryption uses a shared key for encryption and decryption while asymmetric encryption uses public and private key pairs. The document highlights how cryptography provides secure communication methods and is important for both military and everyday applications.Vtu network security(10 ec832) unit 2 notes..
Vtu network security(10 ec832) unit 2 notes..Jayanth Dwijesh H P
╠²
The document discusses symmetric cryptography, focusing on techniques such as substitution and transposition, along with standards like the Data Encryption Standard (DES) and AES. It details the components of symmetric cipher systems, cryptographic principles, and the vulnerabilities to attacks like cryptanalysis and brute-force. Additionally, it summarizes various cipher techniques including Caesar, monoalphabetic, Playfair, and Hill ciphers, highlighting their operational mechanisms and security strengths.A REVIEW STUDY OF CRYPTOGRAPHY TECHNIQUES
A REVIEW STUDY OF CRYPTOGRAPHY TECHNIQUESValerie Felton
╠²
This document reviews and summarizes various cryptography techniques. It discusses how cryptography provides security for data transmission by converting plain text into cipher text using encryption and back using decryption. The two main types of cryptography discussed are symmetric key cryptography which uses a single secret key for both encryption and decryption, and asymmetric key cryptography which uses public/private key pairs. Specific techniques covered include DES, 3DES, AES, and RSA.CRYPTOGRAPHY-PAYAL CHOPRA.ppt
CRYPTOGRAPHY-PAYAL CHOPRA.pptPayalChopra9
╠²
This document provides an overview of cryptography. Cryptography is the practice of hiding information to ensure confidentiality, integrity, and authentication. There are two main types: secret key cryptography which uses a single key for encryption and decryption, and public key cryptography which uses separate public and private keys. Popular cryptographic algorithms include RSA and hash functions. Cryptography aims to provide security against common attacks such as ciphertext-only attacks.Network security and cryptography
Network security and cryptographyPavithra renu
╠²
This document discusses network security and cryptography. It begins by defining a network and some common network threats. It then discusses network security goals like avoiding denial of service attacks. The document outlines different cryptography techniques like symmetric and asymmetric key cryptography. Symmetric cryptography uses a shared key while asymmetric uses public and private keys. Specific algorithms like RSA and DES are described. The document proposes combining numerals and alphabets in encryption to increase security. It concludes cryptography can securely hide and transmit data through encryption and decryption.A Survey on Generation and Evolution of Various Cryptographic Techniques
A Survey on Generation and Evolution of Various Cryptographic TechniquesIRJET Journal
╠²
This document summarizes previous research that has surveyed and compared various symmetric key cryptographic techniques. Several studies analyzed the performance of algorithms like DES, 3DES, AES, Blowfish, RC4 in terms of encryption/decryption time, memory usage, power consumption, throughput, and security against attacks. Most found that Blowfish had among the best performance overall, being fast and requiring few resources while maintaining strong security. AES generally required more processing power and time than alternatives like DES or RC4. The performance of algorithms could also vary based on file/data type, size, and the computing platform or operating system used.PresentationonCRYPTOGRvvvvvvvvvvvAPHYppt.ppt
PresentationonCRYPTOGRvvvvvvvvvvvAPHYppt.pptkushal37073
╠²
The document presents an overview of cryptography, highlighting its importance for secure communications on the internet. It details the purpose, types (including secret key and public key cryptography), processes, algorithms, and potential attacks on cryptographic systems. The conclusion emphasizes the use of different algorithms based on security requirements for rapid or secret message transmission.A Survey on Cryptographic Techniques for Network Security.pdf
A Survey on Cryptographic Techniques for Network Security.pdfYasmine Anino
╠²
This document summarizes and compares several cryptographic techniques for network security, including AES, 3DES, Blowfish, and DES. It provides an overview of each algorithm, including key sizes and block sizes. AES is identified as providing better performance and security compared to other algorithms like 3DES and DES. The document also reviews related literature on encrypting data for network security and enhancing encryption methods. It concludes that AES is a better encryption algorithm than alternatives like 3DES and DES due to its performance and security against attacks like brute force.Introduction to Cryptography CYB 303.pptx
Introduction to Cryptography CYB 303.pptxAbolarinwa
╠²
The document provides an overview of cryptography, detailing its fundamental components such as ciphers, key exchange mechanisms, and the concepts of symmetric and public key cryptography. It discusses methods for symmetric key distribution, key agreement through algorithms like Diffie-Hellman, and introduces public key cryptography utilizing RSA and elliptic curve cryptography for secure communications. Additionally, it addresses digital signatures, hashing, non-repudiation, and the role of digital certificates in ensuring the authenticity of public keys.PresentationonCRYPTOGRAPHYppt.ppt
PresentationonCRYPTOGRAPHYppt.pptPrabhatMishraAbvp
╠²
This document provides an overview of cryptography. It begins with defining cryptography as the practice of hiding information and discusses its purposes, including authentication, privacy, integrity, and non-repudiation. It then describes the basic architecture and types of cryptography, including secret key cryptography, public key cryptography, and hash functions. The document outlines the process of cryptography and different algorithm types, including public/private key cryptography and hash functions. It concludes by discussing different types of attacks on cryptography and thanking the audience.Presentationon ON THE TOPIC CRYPTOGRAPHY
Presentationon ON THE TOPIC CRYPTOGRAPHYBARATH800940
╠²
This document provides an overview of cryptography. It begins with defining cryptography as the practice of hiding information and discusses its purposes, including authentication, privacy, integrity, and non-repudiation. It then describes the basic architecture and types of cryptography, including secret key cryptography, public key cryptography, and hash functions. The document outlines the process of cryptography and different algorithm types, including public/private key cryptography and hash functions. It concludes by discussing different types of attacks on cryptography and thanking the audience.PresentationonCRYPTOGRAPHYppt.ppt
PresentationonCRYPTOGRAPHYppt.pptvinitajain703
╠²
This document provides an overview of cryptography. It begins with defining cryptography as the practice of hiding information and discusses its purposes, including authentication, privacy, integrity, and non-repudiation. It then describes the basic architecture and types of cryptography, including secret key cryptography, public key cryptography, and hash functions. The document outlines the process of cryptography and different algorithm types, including public/private key cryptography and hash functions. It concludes by discussing different types of attacks on cryptography and thanking the audience.Pairing Based Elliptic Curve Cryptosystem for Message Authentication
Pairing Based Elliptic Curve Cryptosystem for Message AuthenticationIJTET Journal
╠²
This document summarizes a research paper on using elliptic curve cryptography for message authentication. It begins with an introduction to elliptic curve cryptography and how it can provide equivalent security to other public key encryption methods but with smaller key sizes. It then describes the proposed methodology which includes generating an ECC key pair, encrypting a message with the public key, transmitting the encrypted message, and decrypting it with the private key. The results show a message being encrypted and decrypted correctly using this ECC process. It concludes that ECC can provide an efficient method for authentication in systems like vehicular networks due to its lower computation and communication overhead compared to other encryption methods.CISSP Certification Security Engineering-Part2
CISSP Certification Security Engineering-Part2Hamed Moghaddam
╠²
The document discusses the principles and components of cryptography, emphasizing its importance in data protection through encryption and decryption processes. Key concepts include types of ciphers, symmetric and asymmetric algorithms, digital signatures, and the role of public key infrastructure (PKI) in managing and validating cryptographic identities. It also outlines security measures such as confidentiality, integrity, authentication, and non-repudiation in cryptographic systems.PresentationonCRYPTOGRAPHYppt.ppt - Read-Only - Compatibility Mode.ppt
PresentationonCRYPTOGRAPHYppt.ppt - Read-Only - Compatibility Mode.pptso6281019
╠²
This document provides an overview of cryptography. It defines cryptography as the practice of hiding information and discusses its purposes, including authentication, privacy, integrity, and non-repudiation. The document outlines the basic architecture of cryptography, including secret key cryptography, public key cryptography, hash functions, and types of cryptographic attacks. It describes the processes of public/private key cryptography and different types of cryptographic algorithms.Analysis of Cryptography Techniques
Analysis of Cryptography Techniqueseditor1knowledgecuddle
╠²
The document reviews various cryptography techniques used for securing confidential information during digital communication, highlighting the importance of data protection for sensitive information such as banking transactions. It categorizes cryptography into symmetric and asymmetric techniques, discussing RSA, Diffie-Hellman, DSA, and ECC, and provides examples of their applications, performance analysis, and security implications. Additionally, the paper emphasizes the need for effective encryption methods to prevent unauthorized access and ensure data integrity.Cryptography ppt
Cryptography pptOECLIB Odisha Electronics Control Library
╠²
The document discusses cryptography, explaining its definition, purpose, architecture, and types such as secret key and public key cryptography. It outlines key aspects including authentication, privacy, integrity, and mechanisms for non-repudiation. Additionally, the document highlights various cryptographic algorithms and potential attacks, concluding that the choice of algorithm depends on the specific security needs.CS_Chapter_2Security concerns of different types of devices.pptx
CS_Chapter_2Security concerns of different types of devices.pptxhaymanottaddess2015m
╠²
The document outlines key concepts in computer security, focusing on cryptography and its techniques, such as encryption and decryption processes. It explains both symmetric (private key) and asymmetric (public key) cryptosystems, detailing the unique characteristics of each, including key management and usage. Additionally, the document discusses examples like the Caesar cipher, DES, and RSA to illustrate cryptographic principles and the significance of secure key handling.CS_Chapter_2Security concerns of different types of devices.pptx
CS_Chapter_2Security concerns of different types of devices.pptxhaymanottaddess2015m
╠²
The document discusses cryptography and encryption techniques, defining key terms such as plaintext, ciphertext, encryption, decryption, and key types including symmetric and asymmetric cryptosystems. It explains how each system operates, with examples like the Caesar cipher, DES for symmetric cryptography, and RSA for asymmetric cryptography, highlighting their applications and the significance of key management. Additionally, it covers cryptographic attacks and properties of encryption functions, demonstrating the importance of security in data transmission.A NEW PROPOSED SYMMETRIC KEY ALGORITHM FOR MODERN CRYPTOGRAPHIC
A NEW PROPOSED SYMMETRIC KEY ALGORITHM FOR MODERN CRYPTOGRAPHICijsrd.com
╠²
This document describes a new proposed symmetric key encryption algorithm. It begins with background on cryptography and then describes the new algorithm. The algorithm encrypts text by taking the ASCII value of each character, reversing the 8-bit binary representation, dividing this by a 4-digit key, and storing the remainder in the first 3 digits and quotient in the next 5 digits to form the ciphertext. It provides an example of encrypting the character 'T' using this process. The document suggests this algorithm is easy to implement and more secure than existing algorithms due to using a reversal operation during encryption.Ad
Group 6
- 2. Introduction To Basic Encryption and Decryption ’éŚ The term ŌĆśCryptographyŌĆÖ means the concept of encryption and decryption together. Cryptography is the technique in which the original ŌĆśplain textŌĆÖ message is ŌĆśencryptedŌĆÖ i.e. converted into a coded form called ŌĆścipher textŌĆÖ at the senderŌĆÖs end, which is then transmitted to the receiver.
- 3. ’éŚ The receiver then ŌĆśdecryptsŌĆÖ i.e. converts the ŌĆścipher textŌĆÖ back into the ŌĆśplain textŌĆÖ to get the original message back. ’éŚ Cryptography is also called as an art or technique to achieve the secure communication between the communicating parties by encoding the messages between them such that no 3rd party can gain anything useful out of interception.
- 4. ’éŚ Elliptic curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. Elliptic curves are also used in several integer factorization algorithms that have applications in cryptography, such as Lenstra elliptic curve factorization. ’éŚ Cryptography is one of the essential technologies used in building a secure VPN. Different applications of the same basic algorithms can provide both encryption that keeps data secret and authentication that ensures the two security peers in a VPN are who they claim to be. This chapter introduces some basic concepts in cryptography and demonstrates how they can be used in practice to provide data confidentiality. The next chapter continues this theme with a discussion of mutual authentication using cryptographic algorithms.
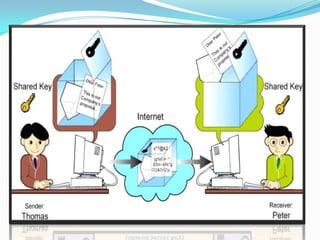
- 6. ’éŚ Symmetric-key cryptography is also known as a secret- key, single key or private key. ’éŚ An encryption system in which the sender and receiver of a message share a single, common key that is used to encrypt and decrypt the message. ’éŚ Symmetric-key systems are simpler and faster, but their main drawback is that the two parties must somehow exchange the key in a secure way. ’éŚ Public-key encryption avoids this problem because the public key can be distributed in a non-secure way, and the private key is never transmitted.
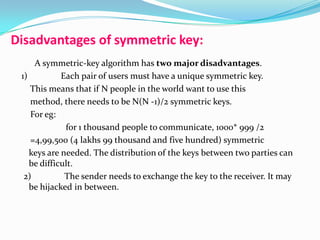
- 8. Disadvantages of symmetric key: A symmetric-key algorithm has two major disadvantages. 1) Each pair of users must have a unique symmetric key. This means that if N people in the world want to use this method, there needs to be N(N -1)/2 symmetric keys. For eg: for 1 thousand people to communicate, 1000* 999 /2 =4,99,500 (4 lakhs 99 thousand and five hundred) symmetric keys are needed. The distribution of the keys between two parties can be difficult. 2) The sender needs to exchange the key to the receiver. It may be hijacked in between.
- 9. ’éŚ Category of Standard: Computer Security. ’éŚ Explanation: The Data Encryption Standard (DES) specifies a FIPS approved cryptographic algorithm as required by FIPS 140-1. ’éŚ Qualifications. The cryptographic algorithm specified in this standard transforms a 64-bit binary value into a unique 64-bit binary value based on a 56-bit variable. Data Encryption Standard
- 10. ’éŚ The algorithm is designed to encipher and decipher blocks of data consisting of 64 bits under control of a 64-bit key ’éŚ A block to be enciphered is subjected to an initial permutation IP and then to a complex key- dependent computation and finally to a permutation which is the inverse of the initial permutation IP-1. Introduction
- 11. ’éŚ Permutation is an operation performed by a function, which moves an element at place j to the place k. ’éŚ The key-dependent computation can be simply defined in terms of a function f, called the cipher function, and a function KS, called the key schedule. ’éŚ First, a description of the computation.
