Hacking
Download as PPTX, PDF0 likes555 views
This document discusses hacking and cracking. It defines hacking as unauthorized attempts to bypass security systems or networks, and distinguishes between ethical ("white hat") hackers and criminal ("black hat") hackers. It describes common hacking techniques like phishing and pretexting. The document also provides examples of famous hackers and notes that most hacking targets social media sites. It recommends security measures like antivirus software and firewalls to prevent hacking.
1 of 27
Downloaded 19 times























Recommended
Hacking



Hackingsatwinderkaurbajwa
╠²
The document thanks the teacher for allowing the students to do a presentation on hacking. It then provides definitions for different types of hackers such as hackers, crackers, and phreaks. It describes hackers as those who bypass security without permission, crackers as those who destroy systems, and phreaks as those who work with frequencies for confidential information. It also discusses common hacker languages and provides examples of famous and Indian hackers as well as random facts about hacking. Finally, it suggests preventive measures like using antivirus software.Hacking & Attack vector



Hacking & Attack vectorSmit Shah
╠²
In this slide given the information about different type of hacking & different type of attacking vector...Ethical hacking



Ethical hackingManish Mudhliyar
╠²
In this slides i have mentioned some hacking tricks which are interesting to know.. You will able to know how the sites are blocked, how to get rid of them.You will also able to crack the passwords...And some useful tricks related to facebook and mobile hacking.. i hope,You will like it...But one thing ,the tricks are old...But what i think is Old is Gold. :pEthical Hacking



Ethical HackingPallavi Sonone
╠²
This document discusses various techniques used in ethical hacking such as password cracking, Trojans, phishing, and social engineering. It covers related topics like IP addresses, torrent blocking, cookies, spoofing, denial of service (DoS) attacks, and steganography. The document provides definitions and examples of these terms. It also lists some best security practices for protecting systems and data, such as using a firewall, antivirus software, strong passwords, and encryption.Learn awesome hacking tricks



Learn awesome hacking tricksSudhanshu Mishra
╠²
This document provides instructions for various computer-related tasks, some of which could enable harmful behavior. It discusses bypassing security measures, hiding and deleting drives, creating viruses, and cracking software, among other topics. The document warns users not to attempt certain instructions on their own computers due to risk of damage. It also contains links promoting harmful content.Watering Hole Attacks Case Study and Analysis_SecurityXploded_Meet_june14



Watering Hole Attacks Case Study and Analysis_SecurityXploded_Meet_june14securityxploded
╠²
Presented by Monnappa in our quarterly system security meet. visit: http://www.securitytrainings.net for more information.ETHICAL HACKING



ETHICAL HACKINGNAWAZ KHAN
╠²
This document discusses various hacking techniques, including hacking Airtel mobile internet using a proxy server, cracking passwords using tools like Cain & Abel and John the Ripper, installing keylogger software to steal Facebook login credentials, and creating a fake Facebook login page using the Backtrack 5 operating system to phish user passwords. The author argues that the Backtrack method is most effective as it allows anonymous hacking without installing anything on the victim's computer. The document concludes by warning readers not to attempt hacking and only discusses these techniques for educational purposes.Hacker&cracker



Hacker&crackerPat Ninlawan
╠²
The document discusses the differences between hackers and crackers. It defines hackers as individuals who use their technical skills to experiment with computer systems, often to identify vulnerabilities, whereas crackers break into systems illegally with malicious intent. It provides examples of different types of hackers like white hat and black hat hackers. It also gives examples of cracking techniques like password sniffing, spoofing, and exploiting vulnerabilities in websites. The document notes that while hacking can be done for fun or challenge, cracking involves illegal activities for malicious purposes.Notes to The Ten Commandments of Online Security and Privacy



Notes to The Ten Commandments of Online Security and PrivacyJonathan Bacon
╠²
These are the notes for the slideshow offered as a JCCCRA TechTalk on Thursday, November 30, 2018. See the slideshow that is also available at www.slideshare.net/jbaconHackers 22



Hackers 22Mahmoud Saeed
╠²
Hackers can be classified as white hats, black hats, or grey hats based on their intentions and actions. White hats aim to improve security, black hats hack illegally for personal gain, and grey hats operate in the middle. Companies like Microsoft hire white hat hackers to find weaknesses in their systems. However, some hackers attack for criminal reasons, like the North Korean-backed hackers who attacked Sony Pictures in retaliation for The Interview film, or the black hat group Lizard Squad that claimed attacks on Microsoft and Sony gaming networks over Christmas.Hacker !



Hacker !Mahmoud Saeed
╠²
Hackers are computer programmers with advanced skills in computer and information security. Some hackers illegally break into systems, while others are hired by companies to test security vulnerabilities. The document discusses different types of hackers and their motivations, as well as hacking techniques like using Trojan horses. It provides examples of high-profile hacks, such as the Sony Pictures hack believed to be conducted by North Korea, and hacks done by the black hat hacking group Lizard Squad against websites like Facebook and gaming networks.Hacker !



Hacker !Mahmoud Saeed
╠²
Hackers can be classified into three main types: white hat hackers who hack to find security vulnerabilities, black hat hackers who hack with malicious intent, and grey hat hackers whose intentions are unclear. The document discusses different hacking techniques like using Trojan horses to gain access to systems. It provides examples of hacking incidents like the Sony Pictures hack believed to be done by North Korea in response to a movie, and attacks on gaming networks by the hacking group Lizard Squad over Christmas to demonstrate security weaknesses in large companies like Microsoft and Sony.Dark side presentation lwhippedtc515



Dark side presentation lwhippedtc515lisawhipp
╠²
The document discusses both the positive and negative aspects of internet usage. Positively, it recommends using up-to-date antivirus software, firewalls, and HTTPS for secure online purchases. Negatively, it warns of issues like spam costing billions, computer viruses infecting millions of devices, and identity theft. It also discusses the dangers of phishing scams, spyware secretly recording keystrokes, and employers legally monitoring employee internet usage. Overall, the document provides an overview of internet threats like viruses and malware, as well as tips for safeguarding devices and personal information online.Web defacement



Web defacementstudent
╠²
This document provides definitions and information related to hacking and web defacement. It defines hacking as unauthorized use of computer and network resources. A hacker is described as an expert programmer who breaks security, while a cracker breaks in with malicious intent. Web defacement is when a hacker compromises a web server and changes the visual appearance or data on a page. Types of hacking discussed include password, email, site, banking and network hacking. The effects of hacking and methods to prevent hacking like software updates, firewalls, and antivirus software are also summarized.Basic Introduction to hacking



Basic Introduction to hackingSainath Volam
╠²
This document discusses what hacking is and provides information on different types of hackers and hacking techniques. It defines hackers as people who examine computer systems very closely, and distinguishes between white hat, gray hat, and black hat hackers. It also outlines common hacking methods like keylogging, sniffing, and SQL injection. The document then explains why hackers hack and what they typically do after gaining access such as installing backdoors. It concludes with tips on how to protect systems against hackers through patching, encryption, firewalls and backups.Cybercrime (Computer Hacking)



Cybercrime (Computer Hacking)Michael Asres
╠²
This presentation deals with the past, present and future implications of cybercrime with respect to computer hacking.Hacking and cracking



Hacking and crackingDeepak kumar
╠²
This document discusses hacking and cracking. It defines hacking as unauthorized attempts to bypass security mechanisms of information systems or networks, while cracking specifically refers to destroying things. It outlines different types of hackers (white hat, black hat, grey hat) and hacking techniques (pretexting, phishing). Preventative measures like antivirus software and firewalls are recommended. Examples of cracking include bypassing BIOS passwords by trying default passwords or hardware resets, and breaking Windows logon passwords by deleting password files or crashing the password program.Hacking And EthicalHacking By Satish



Hacking And EthicalHacking By SatishNugala Sathesh Chowdary
╠²
This document discusses hacking and different types of hackers. It defines hackers as people who build things and crackers as people who break things. There are three main types of hackers: white-hat hackers who find vulnerabilities to strengthen security, black-hat hackers who hack systems secretly or to steal information, and grey-hat hackers who are in between. The document also provides the "hackers language" which substitutes numbers and symbols for letters to disguise communications, and recommends steps like using antivirus software and being careful about personal details online to help prevent hacking.Hacking



Hackingvkradhika
╠²
The document discusses different types of hacking including website, email, network, password, online banking, and computer hacking. It describes various hackers like white hat, black hat, and grey hat hackers and provides examples of famous hackers such as Kevin Mitnick and Kevin Poulsen. The document concludes with tips to prevent hacking which include using strong passwords, installing antivirus software, avoiding disclosure of personal details, employing ethical hackers, and other internet safety practices.Ethical hacking by chandra prakash upadhyay



Ethical hacking by chandra prakash upadhyayChandra Prakash
╠²
This document provides an overview of hacking, including definitions of different types of hackers (e.g. black hat, white hat, grey hat hackers), why and how hackers hack systems, hacking languages/techniques, ethical hacking and the skills required of ethical hackers, and steps to take after being hacked. It discusses the history of hacking terminology, examples of past hacks, and profiles notable hackers from each category.Hacking



HackingAsma Khan
╠²
Hacking is the process of attempting to gain or successfully gaining unauthorized access to computer resources.
In this presentation types of hacking, types of hackers, process of hacking, advantages of hacking and disvantages are illustrated. End User Security Awareness - Information Security



End User Security Awareness - Information SecurityWorldTrade3
╠²
User awareness and security practices are important due to the risks posed by poor security knowledge and attacks from anywhere in the world via the internet. The top vulnerabilities exploited by cyber criminals include web browsers, IM clients, web applications, and excessive user rights. Maintaining updated anti-virus software, using strong and unique passwords, avoiding suspicious emails and attachments, and practicing good cyber hygiene can help protect users from common security risks. Organizations should implement defense in depth with multiple layers of security to address technical, personnel, and operational issues.UserSecurityAwarenessUniversityTemplate.ppt



UserSecurityAwarenessUniversityTemplate.pptDiveshK4
╠²
User awareness and security practices are important to prevent attacks and vulnerabilities. Poor security can lead to identity theft, monetary theft, and legal issues. The top vulnerabilities according to SANS.org are web browsers, IM clients, web applications, and excessive user rights. Various types of malware like viruses, worms, Trojan horses, and botnets pose threats. Social engineering is another risk. Users should practice secure behaviors like strong passwords, antivirus software, and firewalls to protect themselves and their organizations.Windows Hacking



Windows HackingMayur Sutariya
╠²
This document discusses different types of hackers and methods of hacking passwords. It defines white hat and black hat hackers, with white hats using their skills constructively and ethically to find security vulnerabilities, while black hats use their skills illegally and destructively. The document also discusses crackers/attackers who hack with malicious intent, phreaks who hack phone networks, and script kiddies who exploit known vulnerabilities without technical skills. It provides examples of password cracking tools and methods like Cain & Abel, LCP, password dumping, and using Windows repair mode. It notes the importance of security awareness and prevention.IT security awareness



IT security awarenessDr. Ramkumar Lakshminarayanan
╠²
This document discusses various cybersecurity risks and best practices. It describes how attackers can compromise computers through vulnerabilities in web browsers, applications, and weak user access rights. Common cyber attacks like viruses, worms, Trojans, and botnets are also explained. The document recommends implementing security measures like firewalls, antivirus software, and strong passwords to help defend against these threats. Regular software updates and awareness of social engineering tactics are also emphasized as important aspects of cybersecurity defense.Hacking Presentation v2 By Raffi 



Hacking Presentation v2 By Raffi Shawon Raffi
╠²
Shawon Raffi is presenting on the topic of hacking. He explains that hacking has negative connotations but can actually be used for positive purposes like security testing and finding vulnerabilities. There are different types of hackers, including black hat hackers who perform criminal acts and white hat hackers who work in cybersecurity. The presentation then covers the history of hacking, definitions, famous hackers, countries with many hackers, and tips for protecting against hackers. It aims to provide an overview of hacking and clear up misconceptions, while emphasizing the importance of ethical hacking for security.Information security awareness



Information security awarenessCAS
╠²
The document discusses various cybersecurity risks and best practices for protection. It notes that the internet allows attackers to strike from anywhere in the world. Poor security practices can enable identity theft, monetary theft, and legal issues. According to SANS.org, the top vulnerabilities are web browsers, IM clients, web applications, and excessive user rights. The document provides tips for protecting computers and data, such as using secure passwords, updating software, and practicing safe online behaviors. It also outlines common cyber attacks like viruses, worms, trojans, and social engineering and recommends defenses such as antivirus software, firewalls, and regular software updates.Information Security - A Discussion



Information Security - A DiscussionKaushik Patra
╠²
A presentation to discuss information securities and responsibilities of individual to keep it safe. This specific presentation was contributed by many people. Each of the different area has its own author. I have planned and coordinated with them to compile it into a group presentation.Hacking



Hackingakam bajalan
╠²
This document provides an overview of hacking, including its history, definitions, types, and advice. It discusses how hacking began at MIT in the 1960s, defines it as attempting to gain unauthorized access to computer systems, and identifies different types such as website, network, and password hacking. The document also provides tips on securing data and accounts, such as using unique, complex passwords and ensuring online transactions use HTTPS. Both advantages like testing security and disadvantages like privacy harm are outlined.More Related Content
What's hot (8)
Notes to The Ten Commandments of Online Security and Privacy



Notes to The Ten Commandments of Online Security and PrivacyJonathan Bacon
╠²
These are the notes for the slideshow offered as a JCCCRA TechTalk on Thursday, November 30, 2018. See the slideshow that is also available at www.slideshare.net/jbaconHackers 22



Hackers 22Mahmoud Saeed
╠²
Hackers can be classified as white hats, black hats, or grey hats based on their intentions and actions. White hats aim to improve security, black hats hack illegally for personal gain, and grey hats operate in the middle. Companies like Microsoft hire white hat hackers to find weaknesses in their systems. However, some hackers attack for criminal reasons, like the North Korean-backed hackers who attacked Sony Pictures in retaliation for The Interview film, or the black hat group Lizard Squad that claimed attacks on Microsoft and Sony gaming networks over Christmas.Hacker !



Hacker !Mahmoud Saeed
╠²
Hackers are computer programmers with advanced skills in computer and information security. Some hackers illegally break into systems, while others are hired by companies to test security vulnerabilities. The document discusses different types of hackers and their motivations, as well as hacking techniques like using Trojan horses. It provides examples of high-profile hacks, such as the Sony Pictures hack believed to be conducted by North Korea, and hacks done by the black hat hacking group Lizard Squad against websites like Facebook and gaming networks.Hacker !



Hacker !Mahmoud Saeed
╠²
Hackers can be classified into three main types: white hat hackers who hack to find security vulnerabilities, black hat hackers who hack with malicious intent, and grey hat hackers whose intentions are unclear. The document discusses different hacking techniques like using Trojan horses to gain access to systems. It provides examples of hacking incidents like the Sony Pictures hack believed to be done by North Korea in response to a movie, and attacks on gaming networks by the hacking group Lizard Squad over Christmas to demonstrate security weaknesses in large companies like Microsoft and Sony.Dark side presentation lwhippedtc515



Dark side presentation lwhippedtc515lisawhipp
╠²
The document discusses both the positive and negative aspects of internet usage. Positively, it recommends using up-to-date antivirus software, firewalls, and HTTPS for secure online purchases. Negatively, it warns of issues like spam costing billions, computer viruses infecting millions of devices, and identity theft. It also discusses the dangers of phishing scams, spyware secretly recording keystrokes, and employers legally monitoring employee internet usage. Overall, the document provides an overview of internet threats like viruses and malware, as well as tips for safeguarding devices and personal information online.Web defacement



Web defacementstudent
╠²
This document provides definitions and information related to hacking and web defacement. It defines hacking as unauthorized use of computer and network resources. A hacker is described as an expert programmer who breaks security, while a cracker breaks in with malicious intent. Web defacement is when a hacker compromises a web server and changes the visual appearance or data on a page. Types of hacking discussed include password, email, site, banking and network hacking. The effects of hacking and methods to prevent hacking like software updates, firewalls, and antivirus software are also summarized.Basic Introduction to hacking



Basic Introduction to hackingSainath Volam
╠²
This document discusses what hacking is and provides information on different types of hackers and hacking techniques. It defines hackers as people who examine computer systems very closely, and distinguishes between white hat, gray hat, and black hat hackers. It also outlines common hacking methods like keylogging, sniffing, and SQL injection. The document then explains why hackers hack and what they typically do after gaining access such as installing backdoors. It concludes with tips on how to protect systems against hackers through patching, encryption, firewalls and backups.Cybercrime (Computer Hacking)



Cybercrime (Computer Hacking)Michael Asres
╠²
This presentation deals with the past, present and future implications of cybercrime with respect to computer hacking.Similar to Hacking (20)
Hacking and cracking



Hacking and crackingDeepak kumar
╠²
This document discusses hacking and cracking. It defines hacking as unauthorized attempts to bypass security mechanisms of information systems or networks, while cracking specifically refers to destroying things. It outlines different types of hackers (white hat, black hat, grey hat) and hacking techniques (pretexting, phishing). Preventative measures like antivirus software and firewalls are recommended. Examples of cracking include bypassing BIOS passwords by trying default passwords or hardware resets, and breaking Windows logon passwords by deleting password files or crashing the password program.Hacking And EthicalHacking By Satish



Hacking And EthicalHacking By SatishNugala Sathesh Chowdary
╠²
This document discusses hacking and different types of hackers. It defines hackers as people who build things and crackers as people who break things. There are three main types of hackers: white-hat hackers who find vulnerabilities to strengthen security, black-hat hackers who hack systems secretly or to steal information, and grey-hat hackers who are in between. The document also provides the "hackers language" which substitutes numbers and symbols for letters to disguise communications, and recommends steps like using antivirus software and being careful about personal details online to help prevent hacking.Hacking



Hackingvkradhika
╠²
The document discusses different types of hacking including website, email, network, password, online banking, and computer hacking. It describes various hackers like white hat, black hat, and grey hat hackers and provides examples of famous hackers such as Kevin Mitnick and Kevin Poulsen. The document concludes with tips to prevent hacking which include using strong passwords, installing antivirus software, avoiding disclosure of personal details, employing ethical hackers, and other internet safety practices.Ethical hacking by chandra prakash upadhyay



Ethical hacking by chandra prakash upadhyayChandra Prakash
╠²
This document provides an overview of hacking, including definitions of different types of hackers (e.g. black hat, white hat, grey hat hackers), why and how hackers hack systems, hacking languages/techniques, ethical hacking and the skills required of ethical hackers, and steps to take after being hacked. It discusses the history of hacking terminology, examples of past hacks, and profiles notable hackers from each category.Hacking



HackingAsma Khan
╠²
Hacking is the process of attempting to gain or successfully gaining unauthorized access to computer resources.
In this presentation types of hacking, types of hackers, process of hacking, advantages of hacking and disvantages are illustrated. End User Security Awareness - Information Security



End User Security Awareness - Information SecurityWorldTrade3
╠²
User awareness and security practices are important due to the risks posed by poor security knowledge and attacks from anywhere in the world via the internet. The top vulnerabilities exploited by cyber criminals include web browsers, IM clients, web applications, and excessive user rights. Maintaining updated anti-virus software, using strong and unique passwords, avoiding suspicious emails and attachments, and practicing good cyber hygiene can help protect users from common security risks. Organizations should implement defense in depth with multiple layers of security to address technical, personnel, and operational issues.UserSecurityAwarenessUniversityTemplate.ppt



UserSecurityAwarenessUniversityTemplate.pptDiveshK4
╠²
User awareness and security practices are important to prevent attacks and vulnerabilities. Poor security can lead to identity theft, monetary theft, and legal issues. The top vulnerabilities according to SANS.org are web browsers, IM clients, web applications, and excessive user rights. Various types of malware like viruses, worms, Trojan horses, and botnets pose threats. Social engineering is another risk. Users should practice secure behaviors like strong passwords, antivirus software, and firewalls to protect themselves and their organizations.Windows Hacking



Windows HackingMayur Sutariya
╠²
This document discusses different types of hackers and methods of hacking passwords. It defines white hat and black hat hackers, with white hats using their skills constructively and ethically to find security vulnerabilities, while black hats use their skills illegally and destructively. The document also discusses crackers/attackers who hack with malicious intent, phreaks who hack phone networks, and script kiddies who exploit known vulnerabilities without technical skills. It provides examples of password cracking tools and methods like Cain & Abel, LCP, password dumping, and using Windows repair mode. It notes the importance of security awareness and prevention.IT security awareness



IT security awarenessDr. Ramkumar Lakshminarayanan
╠²
This document discusses various cybersecurity risks and best practices. It describes how attackers can compromise computers through vulnerabilities in web browsers, applications, and weak user access rights. Common cyber attacks like viruses, worms, Trojans, and botnets are also explained. The document recommends implementing security measures like firewalls, antivirus software, and strong passwords to help defend against these threats. Regular software updates and awareness of social engineering tactics are also emphasized as important aspects of cybersecurity defense.Hacking Presentation v2 By Raffi 



Hacking Presentation v2 By Raffi Shawon Raffi
╠²
Shawon Raffi is presenting on the topic of hacking. He explains that hacking has negative connotations but can actually be used for positive purposes like security testing and finding vulnerabilities. There are different types of hackers, including black hat hackers who perform criminal acts and white hat hackers who work in cybersecurity. The presentation then covers the history of hacking, definitions, famous hackers, countries with many hackers, and tips for protecting against hackers. It aims to provide an overview of hacking and clear up misconceptions, while emphasizing the importance of ethical hacking for security.Information security awareness



Information security awarenessCAS
╠²
The document discusses various cybersecurity risks and best practices for protection. It notes that the internet allows attackers to strike from anywhere in the world. Poor security practices can enable identity theft, monetary theft, and legal issues. According to SANS.org, the top vulnerabilities are web browsers, IM clients, web applications, and excessive user rights. The document provides tips for protecting computers and data, such as using secure passwords, updating software, and practicing safe online behaviors. It also outlines common cyber attacks like viruses, worms, trojans, and social engineering and recommends defenses such as antivirus software, firewalls, and regular software updates.Information Security - A Discussion



Information Security - A DiscussionKaushik Patra
╠²
A presentation to discuss information securities and responsibilities of individual to keep it safe. This specific presentation was contributed by many people. Each of the different area has its own author. I have planned and coordinated with them to compile it into a group presentation.Hacking



Hackingakam bajalan
╠²
This document provides an overview of hacking, including its history, definitions, types, and advice. It discusses how hacking began at MIT in the 1960s, defines it as attempting to gain unauthorized access to computer systems, and identifies different types such as website, network, and password hacking. The document also provides tips on securing data and accounts, such as using unique, complex passwords and ensuring online transactions use HTTPS. Both advantages like testing security and disadvantages like privacy harm are outlined.Hacking



HackingVirus
╠²
Hacking has been around for more than a century. In the 1870s, several teenagers were flung off the country's brand new phone system by enraged authorities. Here's a peek at how busy hackers have been in the past 35 years.Ethical hacking



Ethical hackingdjkhatri
╠²
Hacking can refer to authorized or unauthorized attempts to bypass security mechanisms. A hacker is someone who takes advantage of security weaknesses in a system. There are different types of hackers - white hat hackers help identify weaknesses, black hat hackers break into systems to steal information or cause damage, and grey hat hackers fall between white and black hats. Ethical hacking involves company engineers hacking their own systems to improve security. Famous hackers include Stephen Wozniak, Tsutomu Shimomura, Kevin Mitnick, and Kevin Poulsen. Social media sites are a common target for hacking. Installing antivirus software, avoiding personal information disclosure, and frequent scans can help prevent hacking.Ethical hacking



Ethical hackingdjkhatri
╠²
Hacking can refer to authorized or unauthorized attempts to bypass security mechanisms. A hacker is someone who takes advantage of security weaknesses in a system. There are different types of hackers - white hat hackers help identify weaknesses, black hat hackers break into systems to steal information or cause damage, and grey hat hackers fall between white and black hats. Ethical hacking involves company engineers hacking their own systems to improve security. Famous hackers include Wozniac, Shimomura, Mitnick, and Poulsen. Social media sites are often targets of hacking. Installing antivirus software, avoiding personal information disclosure, and frequent scans can help prevent hacking.Hacking and Hackers



Hacking and HackersFarwa Ansari
╠²
This presentation provided information on communication skills and hackers. It began with an introduction to the topic of hackers, defining what a hacker is and discussing different types of hackers such as black hat, white hat, grey hat, and script kiddie hackers. The presentation then discussed famous hackers like Albert Gonzalez, Jonathan James, Ian Murphy, and John Draper. It provided details on some of their hacking activities. The presentation concluded with tips on how to prevent hacking, including keeping software and operating systems updated, using firewalls and antivirus software, avoiding suspicious websites and emails, and having strong passwords.E security and payment 2013-1



E security and payment 2013-1Abdelfatah hegazy
╠²
The presentation discusses internet security threats and e-payment systems. It covers topics such as current internet security issues, statistics on internet usage, industry responses to security threats, available security tools, common types of attackers like hackers and their techniques, and types of attacks like viruses and denial of service attacks. It also discusses ensuring security for e-businesses and different e-payment types. Maintaining data security, privacy, system reliability and integrity are important concerns for any organization conducting business online.HACKING



HACKINGShubham Agrawal
╠²
Hacking refers to attempting to gain unauthorized access to computer systems or networks. There are different types of hackers, including white hat hackers who test security systems to help organizations, black hat hackers who access systems maliciously, and gray hat hackers whose activities fall between white and black. Common types of hacking include website, email, network, password, and computer hacking through techniques like sniffing passwords, spoofing addresses, cracking encryption, brute force guessing, and exploiting poor web application coding. Organizations can help prevent hacking by employing ethical hackers to test security, not exposing passwords to untrusted sites, closing internet access when not in use, and having basic internet knowledge.Hacking
- 2. Objectives of Hacking and Cracking ’éŚ What is Hacking? ’éŚ Difference between Hacking and cracking ’éŚ Types of Hackers ’éŚ Types of Hacking Techniques ’éŚ Preventive measures ’éŚ Some Cracking Examples
- 3. HACKING ’éŚ Authorized or Unauthorize attempts to bypass the security mechanisms of an information systems or network ’éŚ In simple words Hacking means finding out weaknesses in a computer or computer network
- 5. Why do people hack ? ’éŚ To make security stronger (Ethical hacking) ’éŚ Just for fun ’éŚ Steal important information ’éŚ Destroy enemyŌĆÖs computer network ’éŚ For Fame
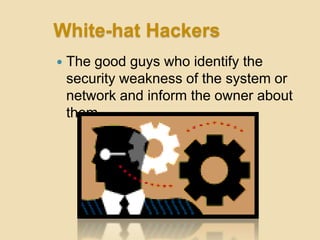
- 7. White-hat Hackers ’éŚ The good guys who identify the security weakness of the system or network and inform the owner about them
- 8. Black Hat Hackers A black hat is the villain or bad guy, who crash into victimŌƤs security to steal information and destroy the victims security network.
- 9. Grey hat Hackers A grey hat, in the hacking community, refers to a skilled hacker who is somewhere in between white and black hat hackers
- 11. ’āśPretexting: Pretexting is the act of been that u r not to release information (e.g. date of birth, Social Security Number, last bill amt.) ’āśPhishing: Phishing is an e-mail fraud method in which the perpetrator sends out email in an attempt to gather personal and financial information from recipients. Phishers attempt to fraudulently acquire sensitive information, such as usernames, passwords and credit card details .Ebay and PayPal are two of the most targeted companies, and online banks are also common targets
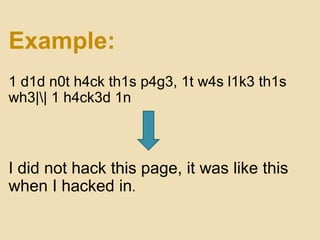
- 12. Language of hackers - Leet 1 -> i or l 3 -> e 4 -> a 7 -> t 9 -> g 0 -> o $ -> s | -> i or l || -> n |/| -> m s -> z z -> s f -> ph ph -> f x -> ck ck -> x
- 13. Example: 1 d1d n0t h4ck th1s p4g3, 1t w4s l1k3 th1s wh3|| 1 h4ck3d 1n I did not hack this page, it was like this when I hacked in.
- 14. World famous hackers ’éŚ Stephen Wozniac ’éŚ Tsutomu Shimomura
- 15. ’éŚ Kevin Mitnick ’éŚ Kevin Poulsen
- 16. Random Fact !!!! ’éŚ The average age group of hackers are aged between 14-24 yrs. ŌĆ”
- 17. Did you know ? ’éŚSocial networking sites like ŌĆ×FACEBOOKŌƤ, ŌƤGMAILŌƤ, ŌƤYAHOOŌĆØ comprised of 60% of direct or indirect hacking incidents.
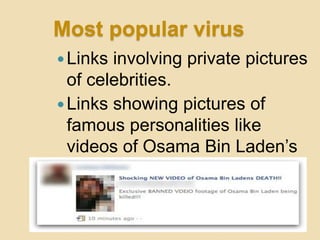
- 18. Most popular virus ’éŚLinks involving private pictures of celebrities. ’éŚLinks showing pictures of famous personalities like videos of Osama Bin LadenŌƤs killing.
- 19. Another popular scam Facebook lottery scam.
- 21. Preventive measures ’éŚ Install a strong anti-virus with full security from internet, removal memory etc. ’éŚ Avoid disclosing personal details like phone number, credit card details to strangers. ’éŚ A good firewall (Sygate personal) ’éŚ A good spy ware / Trojan buster. ’éŚ Use of genuine software
- 22. How to become Hacker ’éŚ The best approach is to gain as much knowledge about stuff as you can. ’éŚ Good command over C / C++ / Perl will definitely help. ’éŚ But above all you need a good logical brain
- 23. Some Examples of Cracking ’éŚWindows Cracking 1) Windows Logon password Breaking
- 24. Window log on password breaking ’éŚ To hack windows login password, reboot and wait for the message: When we see the boot menu on the screen, press F2 or F12 before ŌĆ£Starting Windows 9xŌĆ”ŌĆØ . The boot menu will come up. Select option to boot into DOS . C:>cd windows ’éŚ C:windows>ren *.pwl *.xyz // RENAME Or delete them by typing ’éŚ C:windows>del *.pwl *.xyz //DELETE
- 25. Easy and Simple approach On many computers a series of keystrokes may crash the password program. keep pressing ESC 15 to 20 times . This will result in the crashing of the password program and the computer will continue booting . BY BOOTING We can break into a computer by using live tools like conboot live cd which are readly available on internet .The live cd can be used to make a bootable pen drive and then we can break into any computer.

