Hacking TESLA Model3 - NFC Relay Revisited
- 1. Hacking TESLA Model 3 -- NFC Relay Revisited
- 2. ČĂ °˛ Č« ¸ü Ľň µĄ Who We Are . INGEEK is a Vehicle CyberSecurity company based in Shanghai, China . Members: @Kevin2600; Yuchao Zhang; Ming Wu; Yan Bo; Tony Zhou .. . Focus on research, evaluation, and defense for Smart Car Cyber Security . Notable Achievements . 2020 Tesla Model 3 NFC Keyfob system research . 2018 After-Market Digital Keyfob system (DEFCON 26) . 2017 CarSRC (China First Car Security Response Center Focused on Vehicles)
- 4. NFC (Near Field Communication) Operation Mode: Passive Operation Range: 5-10 cm Operation Freqs: 13.56MHz Data Format: NDEF (NFC Data Exchange Format)
- 5. NFC Applications NFC technology is widely developed E-wallets; Loyalty cards; Libraries; Payments; Passports Access control; Car-keys; Bus; Train; Ski-pass; Museum tickets ...
- 6. BYD-DiLink NFC for Automotive NIO ES8 BYD-DiLink
- 8. Tesla -- Computer on Wheels
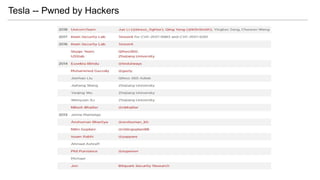
- 9. Tesla -- Pwned by Hackers
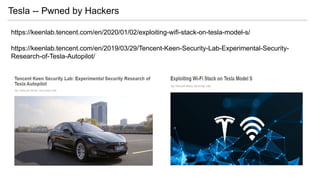
- 10. Tesla -- Pwned by Hackers https://keenlab.tencent.com/en/2020/01/02/exploiting-wifi-stack-on-tesla-model-s/ https://keenlab.tencent.com/en/2019/03/29/Tencent-Keen-Security-Lab-Experimental-Security- Research-of-Tesla-Autopilot/
- 11. Tesla -- Pwned by Hackers https://www.zerodayinitiative.com/blog/2019/3/22/pwn2own-vancouver-2019-wrapping-up-and- rolling-out https://www.esat.kuleuven.be/cosic/fast-furious-and-insecure-passive-keyless-entry-and-start-in- modern-supercars/
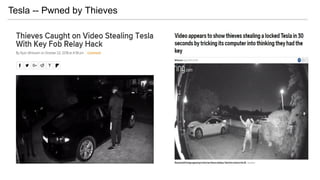
- 12. Tesla -- Pwned by Thieves
- 14. Research Procedures 1. Reconnaissance a. The potential attack scenarios (BrainStorming) b. The architecture of target (RTFM: Internal Mechanism) 2. Design attack plans to achieve the goal a. Get the gears ready & hands dirty b. Implementing the actual attack plans 3. Trophy or Nothing a. Testing with the target (if Success --> Trophy ) b. Testing with the target (If Failed --> TryHarder --> Repeat)
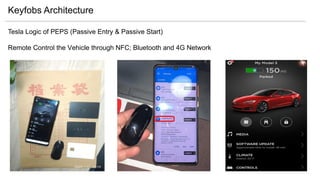
- 15. Keyfobs Architecture Tesla Logic of PEPS (Passive Entry & Passive Start) Remote Control the Vehicle through NFC; Bluetooth and 4G Network
- 16. Keyfob Internal
- 17. Keyfob Internal
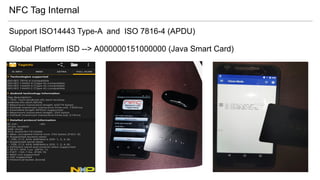
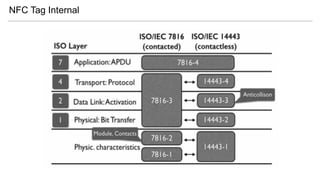
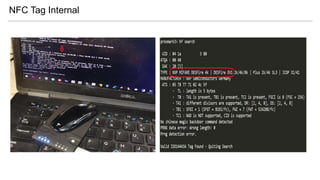
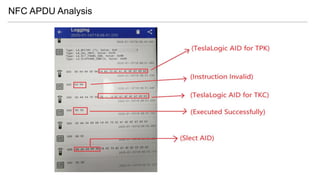
- 18. NFC Tag Internal Support ISO14443 Type-A and ISO 7816-4 (APDU) Global Platform ISD --> A000000151000000 (Java Smart Card)
- 19. NFC Tag Internal
- 20. NFC Tag Internal
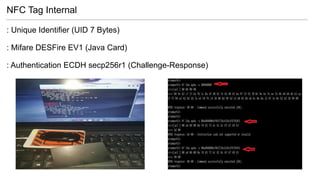
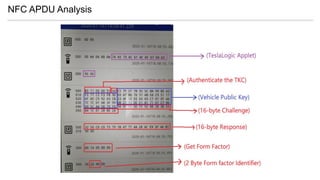
- 21. NFC Tag Internal : Unique Identifier (UID 7 Bytes) : Mifare DESFire EV1 (Java Card) : Authentication ECDH secp256r1 (Challenge-Response)
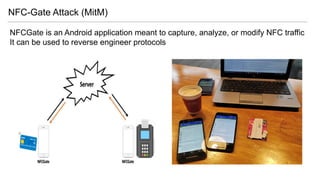
- 23. NFC-Gate Attack (MitM) NFCGate is an Android application meant to capture, analyze, or modify NFC traffic It can be used to reverse engineer protocols
- 24. NFC Relay Demo (NFCGate)
- 25. Tesla Relay Attempt (1st )
- 31. Relay Attack Timing Issue . Payment terminal POS is not required to stop transactions if it takes longer . TESLA has more restrictions on timing. it will be timeout, if it didn't respond the correct answer to AID on time
- 32. Tesla Relay Attempt (2nd)
- 33. Tesla Relay Attempt (3rd)
- 34. NFC Relay Demo (USB: www.youtube.com/watch?v=_6m-htNlz80)
- 35. All Your data are Belong to us ..
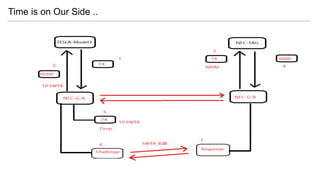
- 37. Time is on Our Side ..
- 38. NFC Relay Demo (WIFI: www.youtube.com/watch?v=kQWg-Ywv3S4)
- 39. I Want To See Further ..
- 40. NFC Relay Demo (Long-Range: www.youtube.com/watch?v=VYKsfgox-bs)
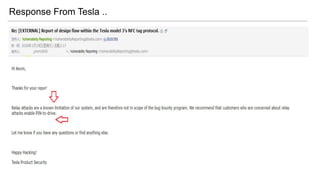
- 41. Response From Tesla ..
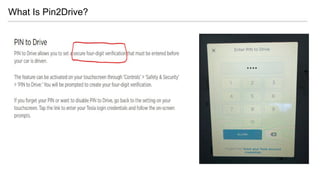
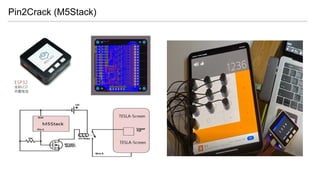
- 42. . The goods can be stolen or put in (SPYCam or GPS-Tracker) . PIN2Drive for protecting from relay attack is a debatable solution . We are able to open the door, the risk is still there (CVE-2020-15912) What We Thought ..
- 44. What Could Possibly Go Wrong
- 46. There Is a Catch..
- 48. . Security by Obscurity is not going to work . 100% Security Does Not exist, even in Vehicles . Products need to be fully tested before going on the market Summary
- 49. . NFCGate (https://github.com/nfcgate) . @slawekja (A Practical guide to hacking NFC/RFID) . @herrmann1001 (https://github.com/RfidResearchGroup/proxmark3) . Lennert Wouters (https://tches.iacr.org/index.php/TCHES/article/view/8289) . Robert Quattlebaum (https://gist.github.com/darconeous/tesla-key-card-protocol) . Salvador Mendoza (https://salmg.net/2018/12/01/intro-to-nfc-payment-relay-attacks/) References
- 50. THANK YOU