Hades
Download as pptx, pdf1 like302 views
This document describes Hades, a Hadoop-based framework for detecting peer-to-peer botnets. Hades uses a distributed data collection architecture to gather data from multiple locations within a network. It then applies a host-aggregation approach, extracting statistical features per host from all network communications. These features are stored and analyzed using Hadoop ecosystem tools like HDFS, Hive, and Mahout. The features help distinguish botnets from benign P2P applications with high true positive rates and low false positive rates in testing.
1 of 8
Download to read offline





Ad
Recommended
DEEPSEC 2013: Malware Datamining And Attribution
DEEPSEC 2013: Malware Datamining And AttributionMichael Boman
╠²
The document outlines a malware attribution project by Michael Boman focusing on the analysis and tracking of malicious software using metadata extraction and collection. It details the steps involved, such as gathering malware samples, extracting and storing metadata, and analyzing collected data to identify malware behavior and development environments. Boman also discusses future goals, including expanding analysis scope, automation, and addressing big data challenges.Performing Network & Security Analytics with Hadoop
Performing Network & Security Analytics with HadoopDataWorks Summit
╠²
The document discusses using Hadoop for network and security analytics. It describes how Hadoop allows analyzing large amounts of network traffic data to detect malicious or abnormal activity that would be difficult to find through traditional means. Specifically, Hadoop enables running sophisticated algorithms over vast datasets and combining multiple analytic passes and tools like clustering and machine learning. The author provides an example workflow for detecting a polymorphic botnet and explains how their system leverages different tools like Hadoop, a streaming analysis engine, and a relational database to break problems into pieces and get results faster than any single tool could achieve.Open source network forensics and advanced pcap analysis
Open source network forensics and advanced pcap analysisGTKlondike
╠²
The document discusses network forensics, emphasizing the analysis of packet captures (pcap) to investigate security incidents and anomalies. It outlines methodologies for pcap analysis, including pattern matching and identifying triggering events, and details two scenarios involving malware detection and denial of service attacks. The author provides resources for further reading and tools used in network analysis, aiming to bridge the gap between basic knowledge and practical application in cybersecurity.Apache metron - An Introduction
Apache metron - An IntroductionBaban Gaigole
╠²
Apache Metron is a cyber security application framework designed for organizations to ingest, process, and store diverse security data feeds in real-time for anomaly detection. It features advanced analytics capabilities, including data enrichment, full-packet capture, and a user-friendly interface for monitoring network traffic and machine logs. Key advantages include real-time alerting and the ability to automate the detection of up to 90% of malicious activities, thereby reducing the need for human intervention.Forensic Analysis - Empower Tech Days 2013
Forensic Analysis - Empower Tech Days 2013Islam Azeddine Mennouchi
╠²
This document provides an agenda for a two-day course on network monitoring and forensics. Day one will cover network forensics, including an introduction to forensic data types like PCAP (full packet capture) and flow data. It will discuss what these data types look like, how to interpret them, and how to obtain them. Day two will recap PCAP and flow data, then cover working with logs and alerts, including how to consolidate these sources and use SIEM tools. It will conclude by discussing how to implement a network monitoring solution. The goal is to provide students with an understanding of network forensic data gathering and concepts needed for network forensics investigations.Kademlia introduction
Kademlia introductionPriyab Satoshi
╠²
Kademlia is a distributed hash table for decentralized peer-to-peer networks designed in 2002. It specifies the structure of the network and exchange of information through node lookups. Each node is identified by a unique ID used to locate values through the Kademlia algorithm. The system is designed to efficiently locate values and nodes through parallel requests to close nodes in the network using a binary tree structure and distance calculation between node IDs. Kademlia has been widely implemented in applications like file sharing, messaging, and blockchain networks due its scalability and fault tolerance.Peer to peer Paradigms
Peer to peer Paradigmshassan ahmed
╠²
The document provides an overview of peer-to-peer paradigms and several related concepts:
- Peer-to-peer networks allow for direct exchange of resources between nodes without centralized control. Nodes act as both clients and servers.
- Examples of peer-to-peer systems include BitTorrent, Skype, and social networking apps. Systems can be pure peer-to-peer or hybrid with some centralized elements.
- Distributed hash tables (DHTs) like Chord and Kademlia provide structured peer-to-peer networks through algorithms that determine how keys are mapped to nodes.Hadoop / Spark on Malware Expression
Hadoop / Spark on Malware ExpressionMapR Technologies
╠²
The document discusses the challenges of detecting Advanced Persistent Threats (APTs) in IT environments, emphasizing the increasing sophistication of malware and the inadequacy of traditional detection methods such as antivirus software. It explores the potential of big data and technologies like Hadoop and Spark for automating malware detection and reducing false positives through advanced analysis techniques. Additionally, it highlights various detection phases and suggests leveraging threat intelligence with big data for improved cybersecurity strategies.Apache metron meetup presentation at capital one
Apache metron meetup presentation at capital onegvetticaden
╠²
Apache Metron is an open source security data analytics platform designed to ingest, process, and analyze large volumes of security and network data in real-time. The presentation introduces Apache Metron, discusses its architecture and key capabilities, and outlines a code lab agenda to add a new data source (Squid proxy logs) to the platform. The code lab will demonstrate how to parse, enrich, and correlate the new data with threat intelligence feeds to enable real-time detection and alerting.Scaling DDS to Millions of Computers and Devices
Scaling DDS to Millions of Computers and DevicesRick Warren
╠²
The document discusses scaling the Data Distribution Service (DDS) to manage large numbers of computers and devices through hierarchical composition and multi-path data routing. It emphasizes the need for efficient data filtering and management of discovery data to ensure effective communication among numerous publishers and subscribers. Recommendations for algorithmic improvements and protocol enhancements, such as instance-level interest filtering and scalable discovery services, are also presented to accommodate rapidly growing network demands. SFBay Area Solr Meetup - July 15th: Integrating Hadoop and Solr
SFBay Area Solr Meetup - July 15th: Integrating Hadoop and SolrLucidworks (Archived)
╠²
The document discusses integrating Hadoop and Solr to enable fast, ad-hoc search across structured and unstructured big data stored in Hadoop. It provides examples of how Hadoop can be used for large-scale storage and processing while Solr is used for real-time querying and search. Specifically, it describes how the Lucidworks HDFS connector can process documents from HDFS and index them into SolrCloud for search, and how log data can be ingested from Flume into HDFS for archiving and extracted fields can be indexed into Solr in real-time for search and analytics dashboards.Chicago Solr Meetup - June 10th: This Ain't Your Parents' Search Engine
Chicago Solr Meetup - June 10th: This Ain't Your Parents' Search EngineLucidworks (Archived)
╠²
The document discusses how search has evolved beyond traditional keyword search to include more complex tasks like recommendations, classifications, and analytics using distributed technologies like Hadoop. It provides an overview of new capabilities in Lucene/Solr like reduced memory usage, pluggable codecs, and spatial search upgrades. LucidWorks offers products like Solr and SiLK that integrate with Hadoop and provide search and analytics capabilities across distributed data.Python for Data Science
Python for Data ScienceHarri H├żm├żl├żinen
╠²
This document presents a comprehensive overview of using Python for data science, highlighting tools and techniques for data harvesting, cleansing, analysis, and visualization. It emphasizes the importance of ethical considerations when dealing with data and discusses various Python libraries suitable for different tasks, such as Scrapy, Numpy, and NetworkX. The latter part focuses on data publishing and sharing, advocating for the open data movement and providing examples of data formats and sources.Large Scale Processing of Unstructured Text
Large Scale Processing of Unstructured TextDataWorks Summit
╠²
The document discusses large-scale natural language processing (NLP) techniques and the importance of managing vast amounts of textual data. It covers various NLP tools and methodologies including Apache OpenNLP and Apache Flink, detailing processes like tokenization, part-of-speech tagging, and name entity recognition. The presentation also touches on future developments in deep learning frameworks that can enhance NLP capabilities.Building a Real-Time News Search Engine: Presented by Ramkumar Aiyengar, Bloo...
Building a Real-Time News Search Engine: Presented by Ramkumar Aiyengar, Bloo...Lucidworks
╠²
The document discusses the challenges of building a news search engine at Bloomberg L.P. It describes how Bloomberg uses Apache Solr/Lucene to index millions of news stories and handle complex search queries from customers. Some key challenges discussed include optimizing searches over huge numbers of documents and metadata fields, handling arbitrarily complex queries, and developing an alerting system to notify users of new matching results. The system has been scaled up to include thousands of Solr cores distributed across data centers to efficiently search and retrieve news content.Hadoop for Bioinformatics: Building a Scalable Variant Store
Hadoop for Bioinformatics: Building a Scalable Variant StoreUri Laserson
╠²
The document discusses the application of the Hadoop ecosystem in genomics, highlighting its evolution from GoogleŌĆÖs infrastructure to an open-source platform at Yahoo!, known as Apache Hadoop. It emphasizes the advantages of Hadoop, such as fault tolerance, scalability, and effective data processing for large genomic datasets, while addressing challenges in bioinformatics, like data access and computational efficiency. Recommendations for future development include adopting Hadoop for data centralization, improving consent models, and promoting open-source methodologies to enhance reproducibility.The Internet
The InternetConorW
╠²
The document discusses key concepts relating to how the Internet works. It defines the Internet as a global network of interconnected computer networks that use standard protocols to share information. It describes how IP addresses identify devices connected to the Internet and how domain names make addresses easier for humans to use, with domain name servers translating names to IP addresses. It also explains how data is broken into packets and sent over networks, with routers selecting the best path to direct packets to their destination while allowing for rerouting if issues arise.Hades_poster_Comad
Hades_poster_ComadPratik Narang
╠²
This document presents Hades, a Hadoop-based framework for detecting peer-to-peer (P2P) botnets in an enterprise network. Hades uses a host-aggregation approach that analyzes behavioral metrics for each P2P host, such as destination hosts contacted and data transfer volume, to distinguish between benign and infected hosts. It proposes a distributed data collection architecture to monitor internal network traffic within a local area network, as opposed to just analyzing external traffic at a backbone router. The framework collects packet data, extracts host-based features using Hive, and evaluates models built with Mahout to detect P2P botnets.A Dynamic Botnet Detection Model based on Behavior Analysis
A Dynamic Botnet Detection Model based on Behavior Analysisidescitation
╠²
The document presents a dynamic botnet detection model based on behavior analysis. The proposed model detects P2P botnets in three phases: (1) identifying P2P nodes using an in-out degree algorithm, (2) clustering suspicious P2P nodes using k-means clustering, and (3) detecting botnets based on the stability of network flows between clustered P2P nodes. Experimental results show the approach can detect botnets with high accuracy by analyzing network traffic at the packet level to measure node connectivity and flow stability over time.Literature survey on peer to peer botnets
Literature survey on peer to peer botnetsAcad
╠²
This document summarizes a literature study on peer-to-peer botnets presented at the International Conference on Recent Innovations in Science, Engineering and Technology (ICRISET-18) on May 18-19, 2018. It discusses the evolution of botnets from centralized command and control structures to decentralized peer-to-peer architectures to avoid detection. The paper then reviews various approaches for detecting P2P botnets, including signature-based, traffic analysis, behavior analysis, graph analysis, and data mining techniques. It concludes that no single technique can effectively detect the evolving botnets and that a collaborative detection framework is needed, with future work developing a model to analyze current botnets and a generic detection framework.Guarding Against Large-Scale Scrabble In Social Network
Guarding Against Large-Scale Scrabble In Social NetworkEditor IJCATR
╠²
The document discusses a botnet detection system designed to identify and mitigate large-scale threats posed by stealthy P2P botnets in social networks. It utilizes statistical analysis and anomaly-based detection techniques to differentiate between legitimate P2P traffic and malicious botnet activities. The proposed system aims to enhance the security of online environments by profiling P2P applications and reducing the visibility of bot-related malicious behaviors.Botnet detection using ensemble classifiers of network flow
Botnet detection using ensemble classifiers of network flow IJECEIAES
╠²
This document summarizes a research paper that proposes using ensemble classifier algorithms to detect botnet traffic from normal network traffic. The paper experiments with bagging, boosting, and random forest classifiers to compare their ability to accurately classify network flows as either botnet or normal traffic. The models are trained and evaluated using the CTU-13 dataset, which contains labeled botnet and normal traffic data. Feature selection is performed to identify the most important attributes for classification, finding source IP, destination IP, start time, duration, protocol, protocol state, number of packets, and total bytes to be the top features. 10-fold cross validation is used to evaluate the performance of the proposed botnet detection models.A Taxonomy of Botnet Detection Approaches
A Taxonomy of Botnet Detection ApproachesFabrizio Farinacci
╠²
This document provides a taxonomy for classifying approaches to detecting botnets. It discusses categorizing detection approaches based on 6 dimensions: (1) the type of botnet being detected such as IRC-based or P2P, (2) what aspect of the botnet is being tracked such as the C&C channel or bot activities, (3) the source of features such as the host or network traffic, (4) how features are extracted such as through passive or active means, (5) how features are correlated such as vertically or horizontally, and (6) the detection algorithm used such as statistical classification or cluster analysis. The document also discusses challenges in detecting botnets given their evolving architectures and activities, and potential futureDetecting Victim Systems In Client Networks Using Coarse Grained Botnet Algor...
Detecting Victim Systems In Client Networks Using Coarse Grained Botnet Algor...IRJET Journal
╠²
This document presents a proposed system for detecting victim systems in client networks using a coarse-grained botnet algorithm. The system uses a two-stage approach: 1) the primary stage detects and collects network anomalies related to botnets; 2) the second stage identifies bots and blocks them from entering the receiver end, identifying bot sender IP addresses. The system implements a scanner to identify bot files, scanning incoming files in both the sender and receiver ends if protection mode is enabled. This avoids intrusions and blocks unauthorized users from accessing the application. The proposed system can help avoid botnet infections spreading in client networks.Towards botnet detection through features using network traffic classification
Towards botnet detection through features using network traffic classificationIJERA Editor
╠²
The paper presents a model for detecting botnets through network traffic classification, highlighting that botnets pose significant threats by facilitating malicious activities such as data theft and DDoS attacks. It evaluates various methods for feature selection to enhance detection accuracy, achieving an impressive 99.85% accuracy with a low false positive rate of 0.145% using a random committee classifier. Future work aims to extend the model by incorporating additional features to identify specific bot families.A Survey of HTTP Botnet Detection
A Survey of HTTP Botnet DetectionIRJET Journal
╠²
This document summarizes research on detecting HTTP botnets. It provides an abstract describing botnets and the challenges of detecting HTTP-based botnet communications. It then summarizes 5 research papers on HTTP botnet detection techniques. Each paper is summarized including the methodology used. Methodologies discussed include using neural networks, data mining algorithms like Apriori, density-based clustering algorithms, and machine learning classifiers like decision trees. The document concludes that both signature-based and behavior-based techniques can be used to detect HTTP botnets by focusing on interrupting stages of the botnet lifecycle.Feature selection for detection of peer to-peer botnet traffic
Feature selection for detection of peer to-peer botnet trafficPratik Narang
╠²
This document summarizes research conducted on feature selection techniques for detecting peer-to-peer botnet traffic. Three feature selection algorithms - Correlation-based Feature Selection, Consistency-based Subset Evaluation, and Principal Component Analysis - were evaluated on traffic data containing benign, P2P, and botnet flows. Features were extracted from network flows and used to build classification models with Naive Bayes, Bayes Network, and C4.5 algorithms. Evaluation showed CFS and CSE improved accuracy over using all features, while PCA provided the fastest model building time with only minor accuracy reductions. The research aims to develop an efficient, close to real-time botnet detection tool.DETECTION OF PEER-TO-PEER BOTNETS USING GRAPH MINING
DETECTION OF PEER-TO-PEER BOTNETS USING GRAPH MININGIJCNCJournal
╠²
The document summarizes previous research on detecting peer-to-peer (P2P) botnets using various techniques including machine learning, graph mining, flow-based analysis, and anomaly detection. It describes a proposed method that uses graph mining on a network communication graph constructed from network flow data to detect botnet nodes. The method applies three graph mining techniques individually and then uses an ensemble algorithm to combine the results, achieving 99.99% accuracy, 94.29% precision, and 98.02% recall on a test dataset, outperforming existing methods.Detection of Peer-to-Peer Botnets using Graph Mining
Detection of Peer-to-Peer Botnets using Graph MiningIJCNCJournal
╠²
The document presents a method for detecting peer-to-peer (P2P) botnets using graph mining techniques applied to network flow data. It employs three graph-mining methods combined through an ensemble algorithm, achieving accuracy rates of 99.99%, precision of 94.29%, and recall of 98.02%, surpassing existing detection methods. The results are validated using both synthetic and publicly available datasets.Machine Learning Based Botnet Detection
Machine Learning Based Botnet Detectionbutest
╠²
This document summarizes a machine learning approach for botnet detection using binary classification and analysis of IRC logs. It discusses using n-gram features extracted from binary executables to train supervised learning classifiers like Naive Bayes, SVM, kNN, and decision trees to classify binaries as benign or botnet. It also discusses obtaining labeled IRC logs for botnet communication and using them to detect botnet activity, but notes data limitations. The goal is to use machine learning for early detection of botnet binaries and monitoring of IRC channels to disrupt botnets.More Related Content
What's hot (9)
Apache metron meetup presentation at capital one
Apache metron meetup presentation at capital onegvetticaden
╠²
Apache Metron is an open source security data analytics platform designed to ingest, process, and analyze large volumes of security and network data in real-time. The presentation introduces Apache Metron, discusses its architecture and key capabilities, and outlines a code lab agenda to add a new data source (Squid proxy logs) to the platform. The code lab will demonstrate how to parse, enrich, and correlate the new data with threat intelligence feeds to enable real-time detection and alerting.Scaling DDS to Millions of Computers and Devices
Scaling DDS to Millions of Computers and DevicesRick Warren
╠²
The document discusses scaling the Data Distribution Service (DDS) to manage large numbers of computers and devices through hierarchical composition and multi-path data routing. It emphasizes the need for efficient data filtering and management of discovery data to ensure effective communication among numerous publishers and subscribers. Recommendations for algorithmic improvements and protocol enhancements, such as instance-level interest filtering and scalable discovery services, are also presented to accommodate rapidly growing network demands. SFBay Area Solr Meetup - July 15th: Integrating Hadoop and Solr
SFBay Area Solr Meetup - July 15th: Integrating Hadoop and SolrLucidworks (Archived)
╠²
The document discusses integrating Hadoop and Solr to enable fast, ad-hoc search across structured and unstructured big data stored in Hadoop. It provides examples of how Hadoop can be used for large-scale storage and processing while Solr is used for real-time querying and search. Specifically, it describes how the Lucidworks HDFS connector can process documents from HDFS and index them into SolrCloud for search, and how log data can be ingested from Flume into HDFS for archiving and extracted fields can be indexed into Solr in real-time for search and analytics dashboards.Chicago Solr Meetup - June 10th: This Ain't Your Parents' Search Engine
Chicago Solr Meetup - June 10th: This Ain't Your Parents' Search EngineLucidworks (Archived)
╠²
The document discusses how search has evolved beyond traditional keyword search to include more complex tasks like recommendations, classifications, and analytics using distributed technologies like Hadoop. It provides an overview of new capabilities in Lucene/Solr like reduced memory usage, pluggable codecs, and spatial search upgrades. LucidWorks offers products like Solr and SiLK that integrate with Hadoop and provide search and analytics capabilities across distributed data.Python for Data Science
Python for Data ScienceHarri H├żm├żl├żinen
╠²
This document presents a comprehensive overview of using Python for data science, highlighting tools and techniques for data harvesting, cleansing, analysis, and visualization. It emphasizes the importance of ethical considerations when dealing with data and discusses various Python libraries suitable for different tasks, such as Scrapy, Numpy, and NetworkX. The latter part focuses on data publishing and sharing, advocating for the open data movement and providing examples of data formats and sources.Large Scale Processing of Unstructured Text
Large Scale Processing of Unstructured TextDataWorks Summit
╠²
The document discusses large-scale natural language processing (NLP) techniques and the importance of managing vast amounts of textual data. It covers various NLP tools and methodologies including Apache OpenNLP and Apache Flink, detailing processes like tokenization, part-of-speech tagging, and name entity recognition. The presentation also touches on future developments in deep learning frameworks that can enhance NLP capabilities.Building a Real-Time News Search Engine: Presented by Ramkumar Aiyengar, Bloo...
Building a Real-Time News Search Engine: Presented by Ramkumar Aiyengar, Bloo...Lucidworks
╠²
The document discusses the challenges of building a news search engine at Bloomberg L.P. It describes how Bloomberg uses Apache Solr/Lucene to index millions of news stories and handle complex search queries from customers. Some key challenges discussed include optimizing searches over huge numbers of documents and metadata fields, handling arbitrarily complex queries, and developing an alerting system to notify users of new matching results. The system has been scaled up to include thousands of Solr cores distributed across data centers to efficiently search and retrieve news content.Hadoop for Bioinformatics: Building a Scalable Variant Store
Hadoop for Bioinformatics: Building a Scalable Variant StoreUri Laserson
╠²
The document discusses the application of the Hadoop ecosystem in genomics, highlighting its evolution from GoogleŌĆÖs infrastructure to an open-source platform at Yahoo!, known as Apache Hadoop. It emphasizes the advantages of Hadoop, such as fault tolerance, scalability, and effective data processing for large genomic datasets, while addressing challenges in bioinformatics, like data access and computational efficiency. Recommendations for future development include adopting Hadoop for data centralization, improving consent models, and promoting open-source methodologies to enhance reproducibility.The Internet
The InternetConorW
╠²
The document discusses key concepts relating to how the Internet works. It defines the Internet as a global network of interconnected computer networks that use standard protocols to share information. It describes how IP addresses identify devices connected to the Internet and how domain names make addresses easier for humans to use, with domain name servers translating names to IP addresses. It also explains how data is broken into packets and sent over networks, with routers selecting the best path to direct packets to their destination while allowing for rerouting if issues arise.Similar to Hades (20)
Hades_poster_Comad
Hades_poster_ComadPratik Narang
╠²
This document presents Hades, a Hadoop-based framework for detecting peer-to-peer (P2P) botnets in an enterprise network. Hades uses a host-aggregation approach that analyzes behavioral metrics for each P2P host, such as destination hosts contacted and data transfer volume, to distinguish between benign and infected hosts. It proposes a distributed data collection architecture to monitor internal network traffic within a local area network, as opposed to just analyzing external traffic at a backbone router. The framework collects packet data, extracts host-based features using Hive, and evaluates models built with Mahout to detect P2P botnets.A Dynamic Botnet Detection Model based on Behavior Analysis
A Dynamic Botnet Detection Model based on Behavior Analysisidescitation
╠²
The document presents a dynamic botnet detection model based on behavior analysis. The proposed model detects P2P botnets in three phases: (1) identifying P2P nodes using an in-out degree algorithm, (2) clustering suspicious P2P nodes using k-means clustering, and (3) detecting botnets based on the stability of network flows between clustered P2P nodes. Experimental results show the approach can detect botnets with high accuracy by analyzing network traffic at the packet level to measure node connectivity and flow stability over time.Literature survey on peer to peer botnets
Literature survey on peer to peer botnetsAcad
╠²
This document summarizes a literature study on peer-to-peer botnets presented at the International Conference on Recent Innovations in Science, Engineering and Technology (ICRISET-18) on May 18-19, 2018. It discusses the evolution of botnets from centralized command and control structures to decentralized peer-to-peer architectures to avoid detection. The paper then reviews various approaches for detecting P2P botnets, including signature-based, traffic analysis, behavior analysis, graph analysis, and data mining techniques. It concludes that no single technique can effectively detect the evolving botnets and that a collaborative detection framework is needed, with future work developing a model to analyze current botnets and a generic detection framework.Guarding Against Large-Scale Scrabble In Social Network
Guarding Against Large-Scale Scrabble In Social NetworkEditor IJCATR
╠²
The document discusses a botnet detection system designed to identify and mitigate large-scale threats posed by stealthy P2P botnets in social networks. It utilizes statistical analysis and anomaly-based detection techniques to differentiate between legitimate P2P traffic and malicious botnet activities. The proposed system aims to enhance the security of online environments by profiling P2P applications and reducing the visibility of bot-related malicious behaviors.Botnet detection using ensemble classifiers of network flow
Botnet detection using ensemble classifiers of network flow IJECEIAES
╠²
This document summarizes a research paper that proposes using ensemble classifier algorithms to detect botnet traffic from normal network traffic. The paper experiments with bagging, boosting, and random forest classifiers to compare their ability to accurately classify network flows as either botnet or normal traffic. The models are trained and evaluated using the CTU-13 dataset, which contains labeled botnet and normal traffic data. Feature selection is performed to identify the most important attributes for classification, finding source IP, destination IP, start time, duration, protocol, protocol state, number of packets, and total bytes to be the top features. 10-fold cross validation is used to evaluate the performance of the proposed botnet detection models.A Taxonomy of Botnet Detection Approaches
A Taxonomy of Botnet Detection ApproachesFabrizio Farinacci
╠²
This document provides a taxonomy for classifying approaches to detecting botnets. It discusses categorizing detection approaches based on 6 dimensions: (1) the type of botnet being detected such as IRC-based or P2P, (2) what aspect of the botnet is being tracked such as the C&C channel or bot activities, (3) the source of features such as the host or network traffic, (4) how features are extracted such as through passive or active means, (5) how features are correlated such as vertically or horizontally, and (6) the detection algorithm used such as statistical classification or cluster analysis. The document also discusses challenges in detecting botnets given their evolving architectures and activities, and potential futureDetecting Victim Systems In Client Networks Using Coarse Grained Botnet Algor...
Detecting Victim Systems In Client Networks Using Coarse Grained Botnet Algor...IRJET Journal
╠²
This document presents a proposed system for detecting victim systems in client networks using a coarse-grained botnet algorithm. The system uses a two-stage approach: 1) the primary stage detects and collects network anomalies related to botnets; 2) the second stage identifies bots and blocks them from entering the receiver end, identifying bot sender IP addresses. The system implements a scanner to identify bot files, scanning incoming files in both the sender and receiver ends if protection mode is enabled. This avoids intrusions and blocks unauthorized users from accessing the application. The proposed system can help avoid botnet infections spreading in client networks.Towards botnet detection through features using network traffic classification
Towards botnet detection through features using network traffic classificationIJERA Editor
╠²
The paper presents a model for detecting botnets through network traffic classification, highlighting that botnets pose significant threats by facilitating malicious activities such as data theft and DDoS attacks. It evaluates various methods for feature selection to enhance detection accuracy, achieving an impressive 99.85% accuracy with a low false positive rate of 0.145% using a random committee classifier. Future work aims to extend the model by incorporating additional features to identify specific bot families.A Survey of HTTP Botnet Detection
A Survey of HTTP Botnet DetectionIRJET Journal
╠²
This document summarizes research on detecting HTTP botnets. It provides an abstract describing botnets and the challenges of detecting HTTP-based botnet communications. It then summarizes 5 research papers on HTTP botnet detection techniques. Each paper is summarized including the methodology used. Methodologies discussed include using neural networks, data mining algorithms like Apriori, density-based clustering algorithms, and machine learning classifiers like decision trees. The document concludes that both signature-based and behavior-based techniques can be used to detect HTTP botnets by focusing on interrupting stages of the botnet lifecycle.Feature selection for detection of peer to-peer botnet traffic
Feature selection for detection of peer to-peer botnet trafficPratik Narang
╠²
This document summarizes research conducted on feature selection techniques for detecting peer-to-peer botnet traffic. Three feature selection algorithms - Correlation-based Feature Selection, Consistency-based Subset Evaluation, and Principal Component Analysis - were evaluated on traffic data containing benign, P2P, and botnet flows. Features were extracted from network flows and used to build classification models with Naive Bayes, Bayes Network, and C4.5 algorithms. Evaluation showed CFS and CSE improved accuracy over using all features, while PCA provided the fastest model building time with only minor accuracy reductions. The research aims to develop an efficient, close to real-time botnet detection tool.DETECTION OF PEER-TO-PEER BOTNETS USING GRAPH MINING
DETECTION OF PEER-TO-PEER BOTNETS USING GRAPH MININGIJCNCJournal
╠²
The document summarizes previous research on detecting peer-to-peer (P2P) botnets using various techniques including machine learning, graph mining, flow-based analysis, and anomaly detection. It describes a proposed method that uses graph mining on a network communication graph constructed from network flow data to detect botnet nodes. The method applies three graph mining techniques individually and then uses an ensemble algorithm to combine the results, achieving 99.99% accuracy, 94.29% precision, and 98.02% recall on a test dataset, outperforming existing methods.Detection of Peer-to-Peer Botnets using Graph Mining
Detection of Peer-to-Peer Botnets using Graph MiningIJCNCJournal
╠²
The document presents a method for detecting peer-to-peer (P2P) botnets using graph mining techniques applied to network flow data. It employs three graph-mining methods combined through an ensemble algorithm, achieving accuracy rates of 99.99%, precision of 94.29%, and recall of 98.02%, surpassing existing detection methods. The results are validated using both synthetic and publicly available datasets.Machine Learning Based Botnet Detection
Machine Learning Based Botnet Detectionbutest
╠²
This document summarizes a machine learning approach for botnet detection using binary classification and analysis of IRC logs. It discusses using n-gram features extracted from binary executables to train supervised learning classifiers like Naive Bayes, SVM, kNN, and decision trees to classify binaries as benign or botnet. It also discusses obtaining labeled IRC logs for botnet communication and using them to detect botnet activity, but notes data limitations. The goal is to use machine learning for early detection of botnet binaries and monitoring of IRC channels to disrupt botnets.Bot net detection by using ssl encryption
Bot net detection by using ssl encryptionAcad
╠²
The document discusses botnet detection using SSL encryption. It begins with an abstract discussing how botnets spread through distributed denial of service attacks and control large numbers of computers. The authors propose checking SSL traffic and features to detect malicious connections. It then discusses how botnets use peer-to-peer networks and protocols like HTTP and IRC, making detection challenging. The document outlines a framework for detecting P2P botnets using host-based and network-based methods. It describes applying the Apriori algorithm to find frequent itemsets in network data to identify systems likely to be infected. In conclusion, the authors present a detection system that can identify malicious connections over SSL and propose a graphical tool to detect future infected systems through data mining.Detection of Botnets using Honeypots and P2P Botnets
Detection of Botnets using Honeypots and P2P BotnetsCSCJournals
╠²
This document discusses a proposed method for using honeypots and peer-to-peer (P2P) botnets to detect botnets. It begins by introducing the concepts of botnets, honeypots, and P2P botnets. The proposed method has three steps: 1) launching bots into a network to infect honeypots, 2) constructing a P2P botnet to detect and remove infected honeypots, and 3) using the remaining uninfected honeypots to detect the original bots. Simulation results show the number of detected botnets increases as more uninfected honeypots are used. The document concludes by discussing limitations of honeypot detection and the ongoing challenge of detecting botnets.Machine-learning Approaches for P2P Botnet Detection
using Signal-processing...
Machine-learning Approaches for P2P Botnet Detection
using Signal-processing...Pratik Narang
╠²
This document describes a machine learning approach for detecting peer-to-peer (P2P) botnets using signal processing techniques. It proposes extracting features based on discrete Fourier transforms and Shannon's entropy in addition to regular network behavior features. These features are used to build detection models using supervised machine learning algorithms. The approach treats the communication between each pair of nodes as a signal and aims to uncover hidden patterns in botnet command and control traffic by analyzing it in the frequency domain rather than just the time domain. Evaluation using real botnet and benign traffic datasets showed the models could accurately detect storms, waledac and zeus P2P botnets.An Efficient Framework for Detection & Classification of IoT BotNet.pptx
An Efficient Framework for Detection & Classification of IoT BotNet.pptxSandeep Maurya
╠²
This dissertation develops an efficient framework for the detection and classification of IoT botnet traffic, particularly analyzing the byob botnet. It includes the creation of a new dataset named ri_bot, evaluated against existing datasets using various machine learning models, achieving significant detection accuracies. Future work aims to implement hybrid models incorporating both static and dynamic analyses to improve detection capabilities against evolving threats.A Botnet Detecting Infrastructure
Using a Beneficial Botnet
A Botnet Detecting Infrastructure
Using a Beneficial BotnetTakashi Yamanoue
╠²
The document presents a beneficial botnet framework aimed at detecting malicious peer-to-peer botnets by utilizing a network of agent and analyzing bots to monitor and analyze communication within local area networks. It discusses the evolution and challenges posed by malicious botnets, particularly those employing decentralized communication techniques. Experimental results demonstrate the beneficial botnet's capability to identify and respond to potential threats while highlighting the need for improvements in speed and security.A review botnet detection and suppression in clouds
A review botnet detection and suppression in cloudsAlexander Decker
╠²
This document provides a summary of a journal article that reviews techniques for detecting and suppressing botnets in cloud computing environments. It discusses how botnets pose a security threat and how cloud environments provide botmasters rich computing resources to deploy attacks. The document reviews literature on various botnet detection techniques including network-based, host-based, and those using intrusion detection system data. It also discusses an active analysis technique using honeypots and honeynets, and a passive analysis technique using darknets. Finally, it introduces a distributed botnet suppression system for clouds and a collaborative network security system to automatically detect and process botnet traffic across networks.Performance evaluation of botnet detection using machine learning techniques
Performance evaluation of botnet detection using machine learning techniquesIJECEIAES
╠²
This document investigates the performance evaluation of botnet detection using machine learning techniques, specifically focusing on the CTU-13 dataset which comprises real botnet traffic data. It evaluates various machine learning models, including decision trees, regression models, naive Bayes, and neural networks, assessing their accuracy and ability to minimize false positives in detecting botnet traffic. The results indicate high detection rates for the proposed methods, suggesting their potential application in real-world cybersecurity scenarios.Ad
Hades
- 1. BITS Pilani Hyderabad Campus Hades: A Hadoop-based Framework for Detection of Peer-to-Peer Botnets Pratik Narang, Abhishek Thakur, Chittaranjan Hota
- 2. P2P: uses & misuses
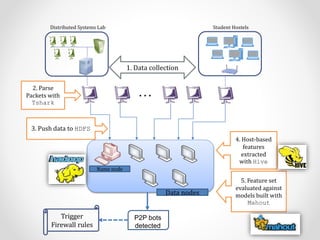
- 3. Approach & Contributions ŌĆó Hades: o ŌĆśHost-aggregation based detection systemŌĆÖ for P2P botnets o is a system for distinguishing Peer-to-Peer (P2P) botnets from benign P2P applications ŌĆó We propose a distributed data collection architecture wherein data collectors are distributed at multiple locations inside a network and sit close to the nodes (say at an Access switch or a Wi-fi APs) o This allows inside-to-inside communication view ŌĆō can be vital for detecting P2P botnets inside a network which communicate to each other over LAN. ŌĆó Hades adopts a Host-aggregation based approach which obtains statistical features per host for all P2P hosts involved in network communications. o No signatures or Deep Packet inspection (DPI) required ŌĆó Built on top of the Hadoop ecosystem, Hades is scalable by design.
- 4. ŌĆ” Data nodes P2P bots detected Name node 2. Parse Packets with Tshark 5. Feature set evaluated against models built with Mahout 4. Host-based features extracted with Hive 3. Push data to HDFS 1. Data collection Trigger Firewall rules Distributed Systems Lab Student Hostels
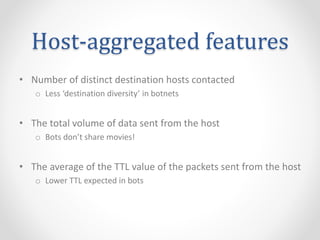
- 5. Host-aggregated features ŌĆó Number of distinct destination hosts contacted o Less ŌĆśdestination diversityŌĆÖ in botnets ŌĆó The total volume of data sent from the host o Bots donŌĆÖt share movies! ŌĆó The average of the TTL value of the packets sent from the host o Lower TTL expected in bots
- 6. Host-based approach Parsed Packet data stored with Hive: CREATE EXTERNAL TABLE packet_data ( timestamp DECIMAL, ip_source STRING, ip_destination STRING, ttl INT, proto INT, payload INT ) ROW FORMAT DELIMITED FIELDS TERMINATED BY ŌĆś,ŌĆÖ LOCATION ŌĆś/user/hdfs/PacketDumpŌĆÖ; CREATE TABLE host_data ( host STRING, destinations DECIMAL, avg_ttl DECIMAL, volume BIGINT ) ROW FORMAT DELIMITED FIELDS TERMINATED BY ŌĆś,ŌĆÖ LINES TERMINATED BY ŌĆśnŌĆÖ STORED AS TEXTFILE; INSERT INTO TABLE host_data SELECT ip_source, COUNT(DISTINCT ip_destination), AVG(ttl), SUM(payload) FROM packet_data GROUP BY ip_source;
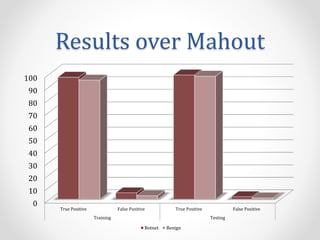
- 7. Results over Mahout 0 10 20 30 40 50 60 70 80 90 100 True Positive False Positive True Positive False Positive Training Testing Botnet Benign
Editor's Notes
- #4: Hades defines our ETL logic
