Hash pre
0 likes656 views
A hash table maps keys to values by applying a hash function to the keys, which then indexes into an array of buckets or slots. There are two main types: open-addressing hash tables, where keys are stored directly in the array slots, and separate chaining, where each slot contains a linked list of key-value entries. Some example applications include databases, symbol tables for compilers, and network processing algorithms.
1 of 18
Downloaded 18 times












Ad
Recommended
Hashing
HashingLavanyaJ28
Ã˝
Hashing is a technique that maps large amounts of data to smaller data structures using a hashing function. A hash function takes inputs of any size and maps them to a fixed-size table called a hash table. To handle collisions where two keys map to the same slot, separate chaining uses linked lists attached to each slot while open addressing resolves collisions by probing to the next slot using techniques like linear probing, quadratic probing, or double hashing. As the hash table fills up, rehashing may be needed to recalculate hashcodes and move entries to a larger table.Indexing
Indexingmyrajendra
Ã˝
Indexes are data structures that improve the speed of data retrieval from a database table by organizing records to allow for faster searches. They work by sorting records on indexed fields and storing field values and pointers to records, allowing for binary searches rather than linear searches through the entire table. While indexes improve search performance, they require additional storage and slower writes. Indexes should be created on fields commonly used for searching that have high cardinality (uniqueness) to maximize performance gains from their use.Ch17 Hashing
Ch17 Hashingleminhvuong
Ã˝
The document discusses hashing and hash tables. It defines hashing as a technique where the location of an element in a collection is determined by a hashing function of the element's value. Collisions can occur if multiple elements map to the same location. Common techniques for resolving collisions include chaining and open addressing. The Java Collections API provides several implementations of hash tables like HashMap and HashSet.Intro To TSQL - Unit 5
Intro To TSQL - Unit 5iccma
Ã˝
This document provides guidance on naming and structuring tables and columns in a SQL database. It discusses best practices for naming tables and columns with up to 30 characters and avoiding spaces. It also covers the different data types that can be used as well as considerations for determining the appropriate data type based on the type and range of data. User defined data types can be created to enforce consistency. The document also discusses identity columns, creating tables, and other table properties and limitations.Unit viii searching and hashing
Unit viii searching and hashing Tribhuvan University
Ã˝
Unit – VIII discusses searching and hashing techniques. It describes linear and binary searching algorithms. Linear search has O(n) time complexity while binary search has O(log n) time complexity for sorted arrays. Hashing is also introduced as a technique to allow O(1) access time by mapping keys to array indices via a hash function. Separate chaining and open addressing like linear probing and quadratic probing are described as methods to handle collisions during hashing.Data indexing presentation
Data indexing presentationgmbmanikandan
Ã˝
The document discusses data indexing, which is a data structure added to files to provide faster data access. Indexing reduces the number of blocks a database management system must check when performing operations like reading, modifying, updating, and deleting data. An index contains a search key and pointer, where the search key is used to look up records and the pointer contains the address of stored data. Common indexing techniques include ordered/primary indexes that access sorted data and hash indexes that uniformly distribute data across buckets. When choosing an indexing technique, factors like access type, time, space overhead are considered. B-trees are commonly used indexing data structures that can grow and shrink dynamically with root, branch and leaf nodes.4.4 hashing02
4.4 hashing02Krish_ver2
Ã˝
The document outlines various data structures and algorithms for implementing dictionaries and hash tables, including:
- Separate chaining, which handles collisions by storing elements that hash to the same value in a linked list. Find, insert, and delete take average time of O(1).
- Open addressing techniques like linear probing and quadratic probing, which handle collisions by probing to alternate locations until an empty slot is found. These have faster search but slower inserts and deletes.
- Double hashing, which uses a second hash function to determine probe distances when collisions occur, reducing clustering compared to linear probing.Overview of Storage and Indexing ...
Overview of Storage and Indexing ...Javed Khan
Ã˝
The document provides an overview of storage and indexing techniques in advanced database management systems, explaining the types of indexing such as primary, secondary, and clustering indexes. It details indexing variations like dense and sparse indexing, as well as multi-level indexing, static and dynamic hashing methods. Additionally, it covers operations related to hashing, including insertion, search, deletion, and how to handle bucket overflows.Database index
Database indexRiteshkiit
Ã˝
This document discusses database indexing. It provides information on the benefits of indexes, how to create indexes, common misconceptions about indexing, and rules for determining when and how to create indexes. Key points include that indexes improve performance of queries by enabling faster data retrieval and synchronization; indexes should be created on columns frequently filtered in WHERE and JOIN clauses; and the order of columns in an index matters for its effectiveness.Quick And Dirty Databases
Quick And Dirty Databasescwarren
Ã˝
This document provides an overview of databases and SQL. It discusses how data is organized in databases using tables, records, and fields. It then covers designing a relational database by creating entity relationship diagrams (ERDs) which show entities, attributes, and relationships. The document outlines the process of normalizing a database to remove duplication. It also introduces SQL for manipulating data by defining concepts like selecting, updating, deleting, and inserting data using commands targeted at specific tables and rows.Indexing techniques
Indexing techniquesHuda Alameen
Ã˝
Indexing techniques allow for faster data retrieval from a database table. Indexes are data structures that copy and sort one or more columns from a table. This allows for both rapid random lookups and efficient retrieval of ordered records. There are two main types of indexes: clustered and non-clustered. A clustered index orders the physical row data by the index keys, while a non-clustered index separately maintains the sorted index keys and pointers to the physical rows. Different databases support various index implementations like B-trees, bitmaps, hashes, and more to provide rapid access to data.Data Structure
Data StructureHarshGupta663
Ã˝
This presentation covers data structures including arrays, linked lists, and stacks. It discusses array types (one and multi-dimensional), linked list types (singly, doubly, circular), and common operations for each. Stack operations like push, pop, peek and applications for infix, prefix, postfix notation conversion are also explained with examples. Code snippets are provided for array traversal, insertion, deletion as well as linked list creation, insertion, deletion and traversal.Data storage and indexing
Data storage and indexingpradeepa velmurugan
Ã˝
1) Databases organize and store data efficiently using a storage hierarchy including cache, main memory, magnetic disks, optical disks, and tapes. Magnetic disks are commonly used secondary storage.
2) Indexing and file structures like B+ trees are data structures that allow efficient retrieval of records from database files based on indexed attributes. B+ trees in particular provide fast traversal and searching through a balanced tree structure.
3) RAID (Redundant Array of Independent Disks) uses multiple disks together to provide increased performance, redundancy, or both through techniques like disk striping and mirroring.Apex collection patterns
Apex collection patternsSathishkumar Periyasamy
Ã˝
This document discusses Apex collection design patterns in Salesforce. It defines collections as objects that can hold references to other objects or sObjects. The main types of collections are Lists, Sets, and Maps. Lists store elements in order and allow duplicates, Sets store unique elements in any order, and Maps store key-value pairs with unique keys. The document provides examples of using each collection type with sObjects and primitive data. It also presents two patterns for mapping contacts to accounts using collections, with one taking fewer script lines to execute.Optimizing Data Accessin Sq Lserver2005
Optimizing Data Accessin Sq Lserver2005rainynovember12
Ã˝
The document discusses various techniques for optimizing SQL Server performance, including handling index fragmentation, optimizing files and partitioning tables, effective use of SQL Profiler and Performance Monitor, a methodology for performance troubleshooting, and a 10 step process for performance optimization. Some key points covered are determining and resolving index fragmentation, partitioning tables across multiple file groups, capturing traces with SQL Profiler and Performance Monitor counters to diagnose issues, and ensuring proper indexing through query execution plans and the SQL Server tuning advisor.Html tables
Html tablesSikandar Pandit
Ã˝
This document provides an overview of HTML tables, including how to define the basic table structure using <table>, <tr>, <th>, and <td> tags. It also describes how to style tables by adding borders, padding, alignment, and captions. Advanced features like colspan, rowspan, and styling individual tables are also covered.Rdbms terminology
Rdbms terminologyHarish Gyanani
Ã˝
A database is a collection of tables containing related data. A table is like a spreadsheet with rows and columns. Columns contain the same kind of data for each row, like a postcode. A row contains all the related data for one record, like a subscription. Primary keys uniquely identify each row, while foreign keys link tables together by matching values. Indexes help locate data faster, and referential integrity ensures foreign keys always point to existing rows.What is Link list? explained with animations
What is Link list? explained with animationsPratikNaik41
Ã˝
The document explains data structures, particularly focusing on linked lists, defined as a way to organize data in a non-contiguous manner using pointers. It contrasts linked lists with arrays, highlighting advantages such as dynamic sizing and easier insertion and deletion of nodes. The document also includes a C++ implementation demonstrating basic linked list operations like creation, insertion, deletion, and counting nodes.Aaa ped-6-Data manipulation: Data Files, and Data Cleaning & Preparation
Aaa ped-6-Data manipulation: Data Files, and Data Cleaning & PreparationAminaRepo
Ã˝
The document outlines essential techniques for data manipulation using Python and pandas, covering data file reading/writing, missing data handling, data transformation, and string manipulation. It provides methods for interacting with various data formats, as well as strategies for filtering and replacing missing values. Additionally, it discusses the importance of handling duplicates, renaming indexes, and utilizing libraries for database interaction and web APIs.Hash table in java
Hash table in javasiriindian
Ã˝
Hashtable is a legacy implementation of a map or key-value pairs in Java. It uses a hash table to store keys and values, where the key is used to find the corresponding value. Hashtable does not allow null keys or values. It is synchronized, which makes it slower than newer implementations like HashMap. Hashtable uses separate chaining to handle collisions when multiple keys hash to the same bucket.Intro to tsql unit 5
Intro to tsql unit 5Syed Asrarali
Ã˝
This document provides guidance on best practices for naming tables and columns in a SQL database, selecting appropriate data types, and creating tables. It discusses:
- Naming conventions for tables and columns
- Data type considerations and available exact numeric, approximate numeric, money, datetime, character, and binary data types
- User defined data types that can be created to enforce consistency
- Identity columns that automatically provide sequential values for new rows
- How to create tables using CREATE TABLE and specifying column properties and constraintsLearn Data Structures With Myassignmenthelp.Net
Learn Data Structures With Myassignmenthelp.NetSteve Johnson
Ã˝
This document discusses data structures and algorithms. It defines data structures as a way to organize data in computer memory and algorithms as systematic methods for solving problems. It states that data structures and algorithms work together, with the data structure chosen to allow easy operation by the algorithm. Examples of commonly used data structures like stacks, queues, arrays and linked lists are provided along with their applications. Classification of linear and non-linear as well as homogeneous and non-homogeneous data structures is also covered.File Organization in Database
File Organization in DatabaseA. S. M. Shafi
Ã˝
File organization refers to the logical relationships and access methods for records within a file. There are several common file organization methods including sequential, heap, hash, clustered, and B+ tree. Sequential organization stores records sequentially in the order they are inserted. Heap organization inserts records into available data blocks without order. Hash organization uses a hash function to map records to storage locations. Clustered organization stores related records together. B+ tree organization stores records at leaf nodes and uses intermediate nodes as pointers to improve access performance.Chapter 12 ds
Chapter 12 dsHanif Durad
Ã˝
This document provides an overview of hash tables and collision resolution techniques for hash tables. It discusses separate chaining and open addressing as the two broad approaches for resolving collisions in hash tables. For separate chaining, items with the same hash are stored in linked lists. For open addressing, techniques like linear probing, quadratic probing and double hashing use arrays to resolve collisions by probing to different index locations. The document outlines common hashing functions, applications of hash tables, and situations where hash tables may not be suitable. It also includes examples and pseudocode.hashing in data strutures advanced in languae java
hashing in data strutures advanced in languae javaishasharma835109
Ã˝
Hashing is a technique that maps values to a fixed-size key to uniquely identify elements, facilitating efficient data storage and retrieval. It utilizes hash functions to produce a hash code which acts as an index in a hash table for quick operations like insertion, deletion, and searching, ideally in constant time O(1). However, issues like collisions, where different keys generate the same hash value, require resolution strategies such as separate chaining and open addressing methods.Lec12-Hash-Tables-27122022-125641pm.pptx
Lec12-Hash-Tables-27122022-125641pm.pptxIqraHanif27
Ã˝
The document provides an overview of hashing in computer science, explaining the method of hashing for efficient data storage and retrieval using hash functions and hash tables. It discusses various aspects of hashing including advantages, applications, collision resolution methods (such as separate chaining and linear probing), and the impact of load factors on performance. Additionally, examples of hash functions and their implementations are presented to illustrate the concepts.Data Structures-Topic-Hashing, Collision
Data Structures-Topic-Hashing, Collisionsailaja156145
Ã˝
Hashing,Types of Hashing,Collision,Resolution Techniquesunit-1-dsa-hashing-2022_compressed-1-converted.pptx
unit-1-dsa-hashing-2022_compressed-1-converted.pptxBabaShaikh3
Ã˝
1. Hashing is a technique that is used to map keys to values in a hash table using a hash function. It allows for fast lookup, insertion, and deletion of key-value pairs.
2. A hash table stores key-value pairs in an array. When looking up a value by its key, the hash function is applied to the key to get the index in the array where the value should be stored. Collisions can occur if two keys map to the same index.
3. Common collision resolution techniques include chaining, which stores multiple values at each index using linked lists, and open addressing techniques like linear probing, quadratic probing, and double hashing which search for the next available empty index.Hashing and Collision Advanced data structure and algorithm
Hashing and Collision Advanced data structure and algorithmyogoso2948
Ã˝
Hashing is a method for efficiently mapping keys to their storage addresses using hash functions, allowing for quick data retrieval in hash tables. While hash tables provide numerous benefits such as constant time complexity for operations and high performance, they also face challenges like collisions and limitations on key values. Various techniques exist for resolving collisions, including open hashing (chaining) and closed hashing, each with its own advantages and disadvantages.Hashing techniques, Hashing function,Collision detection techniques
Hashing techniques, Hashing function,Collision detection techniquesssuserec8a711
Ã˝
Hashing is a technique used to map data of arbitrary size to data of a fixed size. A hash table stores key-value pairs with the key being generated from a hash function. A good hash function uniformly distributes keys while minimizing collisions. Common hash functions include division, multiplication, and universal hashing. Collision resolution strategies like separate chaining and open addressing handle collisions by storing data in linked lists or probing for empty buckets. Hashing provides efficient average-case performance of O(1) for operations like insertion, search and deletion.More Related Content
What's hot (15)
Database index
Database indexRiteshkiit
Ã˝
This document discusses database indexing. It provides information on the benefits of indexes, how to create indexes, common misconceptions about indexing, and rules for determining when and how to create indexes. Key points include that indexes improve performance of queries by enabling faster data retrieval and synchronization; indexes should be created on columns frequently filtered in WHERE and JOIN clauses; and the order of columns in an index matters for its effectiveness.Quick And Dirty Databases
Quick And Dirty Databasescwarren
Ã˝
This document provides an overview of databases and SQL. It discusses how data is organized in databases using tables, records, and fields. It then covers designing a relational database by creating entity relationship diagrams (ERDs) which show entities, attributes, and relationships. The document outlines the process of normalizing a database to remove duplication. It also introduces SQL for manipulating data by defining concepts like selecting, updating, deleting, and inserting data using commands targeted at specific tables and rows.Indexing techniques
Indexing techniquesHuda Alameen
Ã˝
Indexing techniques allow for faster data retrieval from a database table. Indexes are data structures that copy and sort one or more columns from a table. This allows for both rapid random lookups and efficient retrieval of ordered records. There are two main types of indexes: clustered and non-clustered. A clustered index orders the physical row data by the index keys, while a non-clustered index separately maintains the sorted index keys and pointers to the physical rows. Different databases support various index implementations like B-trees, bitmaps, hashes, and more to provide rapid access to data.Data Structure
Data StructureHarshGupta663
Ã˝
This presentation covers data structures including arrays, linked lists, and stacks. It discusses array types (one and multi-dimensional), linked list types (singly, doubly, circular), and common operations for each. Stack operations like push, pop, peek and applications for infix, prefix, postfix notation conversion are also explained with examples. Code snippets are provided for array traversal, insertion, deletion as well as linked list creation, insertion, deletion and traversal.Data storage and indexing
Data storage and indexingpradeepa velmurugan
Ã˝
1) Databases organize and store data efficiently using a storage hierarchy including cache, main memory, magnetic disks, optical disks, and tapes. Magnetic disks are commonly used secondary storage.
2) Indexing and file structures like B+ trees are data structures that allow efficient retrieval of records from database files based on indexed attributes. B+ trees in particular provide fast traversal and searching through a balanced tree structure.
3) RAID (Redundant Array of Independent Disks) uses multiple disks together to provide increased performance, redundancy, or both through techniques like disk striping and mirroring.Apex collection patterns
Apex collection patternsSathishkumar Periyasamy
Ã˝
This document discusses Apex collection design patterns in Salesforce. It defines collections as objects that can hold references to other objects or sObjects. The main types of collections are Lists, Sets, and Maps. Lists store elements in order and allow duplicates, Sets store unique elements in any order, and Maps store key-value pairs with unique keys. The document provides examples of using each collection type with sObjects and primitive data. It also presents two patterns for mapping contacts to accounts using collections, with one taking fewer script lines to execute.Optimizing Data Accessin Sq Lserver2005
Optimizing Data Accessin Sq Lserver2005rainynovember12
Ã˝
The document discusses various techniques for optimizing SQL Server performance, including handling index fragmentation, optimizing files and partitioning tables, effective use of SQL Profiler and Performance Monitor, a methodology for performance troubleshooting, and a 10 step process for performance optimization. Some key points covered are determining and resolving index fragmentation, partitioning tables across multiple file groups, capturing traces with SQL Profiler and Performance Monitor counters to diagnose issues, and ensuring proper indexing through query execution plans and the SQL Server tuning advisor.Html tables
Html tablesSikandar Pandit
Ã˝
This document provides an overview of HTML tables, including how to define the basic table structure using <table>, <tr>, <th>, and <td> tags. It also describes how to style tables by adding borders, padding, alignment, and captions. Advanced features like colspan, rowspan, and styling individual tables are also covered.Rdbms terminology
Rdbms terminologyHarish Gyanani
Ã˝
A database is a collection of tables containing related data. A table is like a spreadsheet with rows and columns. Columns contain the same kind of data for each row, like a postcode. A row contains all the related data for one record, like a subscription. Primary keys uniquely identify each row, while foreign keys link tables together by matching values. Indexes help locate data faster, and referential integrity ensures foreign keys always point to existing rows.What is Link list? explained with animations
What is Link list? explained with animationsPratikNaik41
Ã˝
The document explains data structures, particularly focusing on linked lists, defined as a way to organize data in a non-contiguous manner using pointers. It contrasts linked lists with arrays, highlighting advantages such as dynamic sizing and easier insertion and deletion of nodes. The document also includes a C++ implementation demonstrating basic linked list operations like creation, insertion, deletion, and counting nodes.Aaa ped-6-Data manipulation: Data Files, and Data Cleaning & Preparation
Aaa ped-6-Data manipulation: Data Files, and Data Cleaning & PreparationAminaRepo
Ã˝
The document outlines essential techniques for data manipulation using Python and pandas, covering data file reading/writing, missing data handling, data transformation, and string manipulation. It provides methods for interacting with various data formats, as well as strategies for filtering and replacing missing values. Additionally, it discusses the importance of handling duplicates, renaming indexes, and utilizing libraries for database interaction and web APIs.Hash table in java
Hash table in javasiriindian
Ã˝
Hashtable is a legacy implementation of a map or key-value pairs in Java. It uses a hash table to store keys and values, where the key is used to find the corresponding value. Hashtable does not allow null keys or values. It is synchronized, which makes it slower than newer implementations like HashMap. Hashtable uses separate chaining to handle collisions when multiple keys hash to the same bucket.Intro to tsql unit 5
Intro to tsql unit 5Syed Asrarali
Ã˝
This document provides guidance on best practices for naming tables and columns in a SQL database, selecting appropriate data types, and creating tables. It discusses:
- Naming conventions for tables and columns
- Data type considerations and available exact numeric, approximate numeric, money, datetime, character, and binary data types
- User defined data types that can be created to enforce consistency
- Identity columns that automatically provide sequential values for new rows
- How to create tables using CREATE TABLE and specifying column properties and constraintsLearn Data Structures With Myassignmenthelp.Net
Learn Data Structures With Myassignmenthelp.NetSteve Johnson
Ã˝
This document discusses data structures and algorithms. It defines data structures as a way to organize data in computer memory and algorithms as systematic methods for solving problems. It states that data structures and algorithms work together, with the data structure chosen to allow easy operation by the algorithm. Examples of commonly used data structures like stacks, queues, arrays and linked lists are provided along with their applications. Classification of linear and non-linear as well as homogeneous and non-homogeneous data structures is also covered.File Organization in Database
File Organization in DatabaseA. S. M. Shafi
Ã˝
File organization refers to the logical relationships and access methods for records within a file. There are several common file organization methods including sequential, heap, hash, clustered, and B+ tree. Sequential organization stores records sequentially in the order they are inserted. Heap organization inserts records into available data blocks without order. Hash organization uses a hash function to map records to storage locations. Clustered organization stores related records together. B+ tree organization stores records at leaf nodes and uses intermediate nodes as pointers to improve access performance.Similar to Hash pre (20)
Chapter 12 ds
Chapter 12 dsHanif Durad
Ã˝
This document provides an overview of hash tables and collision resolution techniques for hash tables. It discusses separate chaining and open addressing as the two broad approaches for resolving collisions in hash tables. For separate chaining, items with the same hash are stored in linked lists. For open addressing, techniques like linear probing, quadratic probing and double hashing use arrays to resolve collisions by probing to different index locations. The document outlines common hashing functions, applications of hash tables, and situations where hash tables may not be suitable. It also includes examples and pseudocode.hashing in data strutures advanced in languae java
hashing in data strutures advanced in languae javaishasharma835109
Ã˝
Hashing is a technique that maps values to a fixed-size key to uniquely identify elements, facilitating efficient data storage and retrieval. It utilizes hash functions to produce a hash code which acts as an index in a hash table for quick operations like insertion, deletion, and searching, ideally in constant time O(1). However, issues like collisions, where different keys generate the same hash value, require resolution strategies such as separate chaining and open addressing methods.Lec12-Hash-Tables-27122022-125641pm.pptx
Lec12-Hash-Tables-27122022-125641pm.pptxIqraHanif27
Ã˝
The document provides an overview of hashing in computer science, explaining the method of hashing for efficient data storage and retrieval using hash functions and hash tables. It discusses various aspects of hashing including advantages, applications, collision resolution methods (such as separate chaining and linear probing), and the impact of load factors on performance. Additionally, examples of hash functions and their implementations are presented to illustrate the concepts.Data Structures-Topic-Hashing, Collision
Data Structures-Topic-Hashing, Collisionsailaja156145
Ã˝
Hashing,Types of Hashing,Collision,Resolution Techniquesunit-1-dsa-hashing-2022_compressed-1-converted.pptx
unit-1-dsa-hashing-2022_compressed-1-converted.pptxBabaShaikh3
Ã˝
1. Hashing is a technique that is used to map keys to values in a hash table using a hash function. It allows for fast lookup, insertion, and deletion of key-value pairs.
2. A hash table stores key-value pairs in an array. When looking up a value by its key, the hash function is applied to the key to get the index in the array where the value should be stored. Collisions can occur if two keys map to the same index.
3. Common collision resolution techniques include chaining, which stores multiple values at each index using linked lists, and open addressing techniques like linear probing, quadratic probing, and double hashing which search for the next available empty index.Hashing and Collision Advanced data structure and algorithm
Hashing and Collision Advanced data structure and algorithmyogoso2948
Ã˝
Hashing is a method for efficiently mapping keys to their storage addresses using hash functions, allowing for quick data retrieval in hash tables. While hash tables provide numerous benefits such as constant time complexity for operations and high performance, they also face challenges like collisions and limitations on key values. Various techniques exist for resolving collisions, including open hashing (chaining) and closed hashing, each with its own advantages and disadvantages.Hashing techniques, Hashing function,Collision detection techniques
Hashing techniques, Hashing function,Collision detection techniquesssuserec8a711
Ã˝
Hashing is a technique used to map data of arbitrary size to data of a fixed size. A hash table stores key-value pairs with the key being generated from a hash function. A good hash function uniformly distributes keys while minimizing collisions. Common hash functions include division, multiplication, and universal hashing. Collision resolution strategies like separate chaining and open addressing handle collisions by storing data in linked lists or probing for empty buckets. Hashing provides efficient average-case performance of O(1) for operations like insertion, search and deletion.unit-1-data structure and algorithms-hashing-2024-1 (1).pptx
unit-1-data structure and algorithms-hashing-2024-1 (1).pptxpritimalkhede
Ã˝
The document is a lecture note on hashing prepared by Professor Anand N. Gharu, covering key concepts such as hash tables, hash functions, collision resolution strategies, and operations related to hash tables. It explains various hashing methods, benefits and disadvantages of using hash tables, their applications, and characteristics of hash functions. The content also includes examples and techniques for handling collisions, particularly through open and closed addressing.Hashing
HashingDawood Faheem Abbasi
Ã˝
The document provides an overview of hashing and its application in data structures, particularly in the context of searching methods like linear search, binary search, and hashing. It explains the concept of hash tables, the operations involved, various hash functions, and techniques for collision resolution. Additionally, it discusses the characteristics of good hash functions and their use in applications such as file management and cryptography.08 Hash Tables
08 Hash TablesAndres Mendez-Vazquez
Ã˝
The document provides a comprehensive analysis of hash tables, covering basic data structures, hash table concepts, hashing methods, and their performance. It discusses challenges like collisions and strategies such as chaining and open addressing to resolve them. The text also emphasizes the importance of selecting effective hash functions to ensure efficient data storage and retrieval.Hashing Technique In Data Structures
Hashing Technique In Data StructuresSHAKOOR AB
Ã˝
This document discusses different searching methods like sequential, binary, and hashing. It defines searching as finding an element within a list. Sequential search searches lists sequentially until the element is found or the end is reached, with efficiency of O(n) in worst case. Binary search works on sorted arrays by eliminating half of remaining elements at each step, with efficiency of O(log n). Hashing maps keys to table positions using a hash function, allowing searches, inserts and deletes in O(1) time on average. Good hash functions uniformly distribute keys and generate different hashes for similar keys.Algorithms notes tutorials duniya
Algorithms notes tutorials duniyaTutorialsDuniya.com
Ã˝
This document provides information about dictionaries and hash tables. It defines dictionaries as dynamic sets that support operations like insertion, deletion, and searching. Hash tables are described as an efficient implementation of dictionaries that map keys to array positions using a hash function. The document discusses hash functions, collisions, open and closed addressing techniques to handle collisions, and qualities of good hash functions.Hashing And Hashing Tables
Hashing And Hashing TablesChinmaya M. N
Ã˝
Hashing is a technique to uniquely identify objects by assigning them keys via a hash function. This allows objects to be easily stored and retrieved from a hash table data structure. Collisions, where two objects have the same hash value, are resolved through techniques like separate chaining, linear probing, and double hashing. Hashing provides fast lookup times of O(1) and is widely used to implement caches, databases, associative arrays, and object storage in many programming languages.asdfew.pptx
asdfew.pptxhunterkurosaki
Ã˝
A hash table is a data structure that uses a hash function to map keys to unique indices in an underlying array. Collisions occur when two keys hash to the same index and must be resolved. Open addressing resolves collisions by probing through alternative array locations until an empty slot is found. Double hashing is an open addressing collision resolution technique that uses a secondary hash of the key as an offset when probing for the next index. Hash tables provide efficient lookup, insertion and deletion of key-value pairs and are used widely in applications like databases, caching and cryptography.Hashing notes data structures (HASHING AND HASH FUNCTIONS)
Hashing notes data structures (HASHING AND HASH FUNCTIONS)Kuntal Bhowmick
Ã˝
The document explains the structure and function of hash tables, highlighting how data is stored and retrieved using hash functions that generate a hash key from a given key. It discusses various types of hash functions including division, mid square, multiplicative, digit folding, and digit analysis, and addresses the collision problems that arise when multiple records map to the same bucket, along with corresponding resolution techniques such as chaining and open addressing. Additionally, it covers advanced techniques like quadratic probing and double hashing for collision resolution and introduces the concept of rehashing when the table size needs to be adjusted.Hashing in Data Structure and analysis of Algorithms
Hashing in Data Structure and analysis of AlgorithmsKavitaSingh962656
Ã˝
The document explains hashing as a mathematical concept used extensively in discrete mathematics, focusing on hash functions and hash tables for efficient data storage and retrieval. It details the components of hashing, methods for defining hash functions, and strategies for collision resolution, including separate chaining and open addressing techniques. Additionally, the document outlines various applications of hashing, such as in compilers and online spelling checkers.Data Structures and Agorithm: DS 24 Hash Tables.pptx
Data Structures and Agorithm: DS 24 Hash Tables.pptxRashidFaridChishti
Ã˝
The document discusses hash tables, a data structure that enables fast data retrieval through calculated index numbers derived from keys. It explains the use of ASCII values in generating indices and methods for handling collisions, such as separate chaining and open addressing. Hash tables are widely utilized for various applications, including database indexing, compilers, and password authentication due to their efficiency in insertion, deletion, and retrieval operations.Hash based inventory system
Hash based inventory systemDADITIRUMALATARUN
Ã˝
The document describes a hash-based inventory system that uses hashing algorithms to create a list of inventory parts and quantities sold. The system has three modules: constructing a hash table, searching for inventory items by generating hash codes, and generating reports of parts and quantities. It discusses hash tables, hashing functions, and basic hash table operations like search, insert, and delete. The document also provides examples of hash functions and how they map strings to indexes in a hash table to enable fast retrieval of data.Presentation.pptx
Presentation.pptxAgonySingh
Ã˝
The document discusses hashing techniques and collision resolution methods for hash tables. It covers:
- Hashing maps keys of variable length to smaller fixed-length values using a hash function. Hash tables use hashing to efficiently store and retrieve key-value pairs.
- Collisions occur when two keys hash to the same value. Common collision resolution methods are separate chaining, where each slot points to a linked list, and open addressing techniques like linear probing and double hashing.
- Bucket hashing groups hash table slots into buckets to improve performance. Records are hashed to buckets and stored sequentially within buckets or in an overflow bucket if a bucket is full. This reduces disk accesses when the hash table is storedAd
Hash pre
- 1. Tafelia Technical university TTU
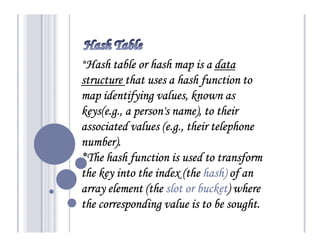
- 2. *Hash table or hash map is a data structure that uses a hash function to map identifying values, known as keys(e.g., a person's name), to their associated values (e.g., their telephone number). *The hash function is used to transform hash) the key into the index (the hash) of an array element (the slot or bucket) where bucket) the corresponding value is to be sought.
- 4. Ideally, the hash function should map each possible key to a unique slot index, but this ideal is rarely achievable in practice (unless the hash keys are fixed .
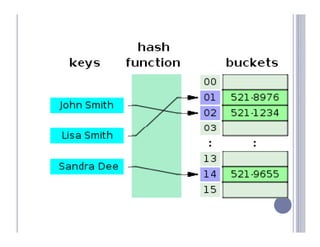
- 5. HASH TABLE TYPES There are two types of Hash Tables: Open-addressed Hash Tables and Separate- Open- Separate- Tables. Chained Hash Tables An Open-addressed Hash Table is a one-dimensional array indexed by Open- integer values that are computed by an index function called a hash function function. A Separate-Chained Hash Table is a one-dimensional array of linked lists indexed by Separate- integer values that are computed by an index function called a hash function function. Hash tables are sometimes referred to as scatter tables tables.”chain”. Typical hash table operations are: Initialization. — Initialization. — Insertion. Insertion. — Searching Deletion. — Deletion.
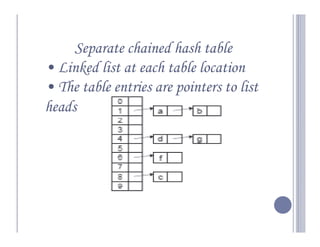
- 6. Separate chained hash table • Linked list at each table location • The table entries are pointers to list heads
- 7. There are two types of hashing : 1. Static hashing: In static hashing, the hash function maps search-key values to a fixed set of locations. 2. Dynamic hashing: In dynamic hashing a hash table can grow to handle more items. The associated hash function must change as the table grows. The load factor of a hash table is the ratio of the number of keys in the table to the size of the hash table. The higher the load factor, the slower the retrieval. With open addressing, the load factor cannot exceed 1. With chaining, the load factor often exceeds 1.
- 8. hash function f: index = f(key, arrayLength) The hash function calculates an index within the array from the data key. arrayLength is the size of the array. For assembly language or other low-level programs, a trivial hash function can often create an index with just one or two inline machine instructions
- 9. A hash function h, is a function which transforms a function, key from a set, K, into an index in a table of size n: h: K -> {0, 1, ..., n-2, n-1} {0 n- n- A key can be a number, a string, a record etc. The size of the set of keys, |K| to be relatively very |K|, large. It is possible for different keys to hash to the same array location. This situation is called collision and the colliding keys are called synonyms.
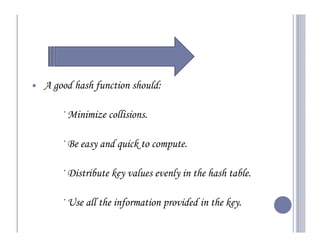
- 10. A good hash function should: — Minimize collisions. — Be easy and quick to compute. — Distribute key values evenly in the hash table. — Use all the information provided in the key.
- 12. 1. Division Remainder (using the table size as the divisor) Computes hash value from key using the % operator. Table size that is a power of 2 like 32 and 1024 should be avoided, for it leads to more collisions. Prime numbers not close to powers of 2 are better table size values. h(key) = key mod size (remainder of key divided by size) where size is the table size m
- 13. 2. Folding It involves splitting keys into two or more parts and then combining the parts to form the hash addresses. To map the key 25936715 to a range between 0 and 9999, we can: — split the number into two as 2593 and 6715 and — add these two to obtain 9308 as the hash value. Very useful if we have keys that are very large. A great advantage is ability to transform non-integer keys into integer values.
- 14. 2. Truncation or Digit/Character Extraction Works based on the distribution of digits or characters in the key. If search key is string we first convert it to integer”ASCLL” then use hash table H(“note”)=78+79+84+69
- 15. Advantages The main advantage of hash tables over other table data structures is speed. This advantage is more apparent when the number of entries is large (thousands or more.
- 16. HASH TABLE APPLICATIONS Database systems Symbol tables The tables used by compilers to maintain information tables: about symbols from a program. Data dictionaries Data structures that support adding, deleting, and dictionaries: searching for data. Although the operations of a hash table and a data dictionary are similar, other data structures may be used to implement data dictionaries. Using a hash table is particularly efficient. Network processing algorithms Hash tables are fundamental algorithms: components of several network processing algorithms and applications, including route lookup, packet classification, and network monitoring.
- 17. EXAMPLE Suppose that we want to store 10,000 students records (each with a 5-digit ID) in a given containerThe id field in this class can be used as a search key for records in the container. class StudentRecord { String name; // Student name double height; // Student height long id; // Unique id }
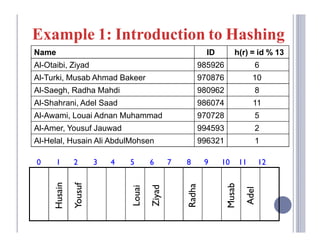
- 18. Example 1: Introduction to Hashing Name ID h(r) = id % 13 Al-Otaibi, Ziyad 985926 6 Al-Turki, Musab Ahmad Bakeer 970876 10 Al-Saegh, Radha Mahdi 980962 8 Al-Shahrani, Adel Saad 986074 11 Al-Awami, Louai Adnan Muhammad 970728 5 Al-Amer, Yousuf Jauwad 994593 2 Al-Helal, Husain Ali AbdulMohsen 996321 1 0 1 2 3 4 5 6 7 8 9 10 11 12
