History Days 1 3
- 1. 9 th Grade Computer Science Rotation Mr. Fedder/Mr. Crowley
- 2. Why Learn About Computers?
- 3. ŌĆ£ IŌĆÖm not a techieŌĆØ
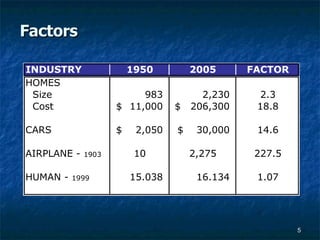
- 4. True/False: 1950ŌĆÖs vs. 2005 Homes are 20 times more expensive. Cars are 15 times more expensive. Computers are 100,000 times more powerful. The development and innovation of computing technology has resulted in the greatest cultural revolution in the history of mankind. You will use computers in some form for the rest of your life.
- 5. Factors
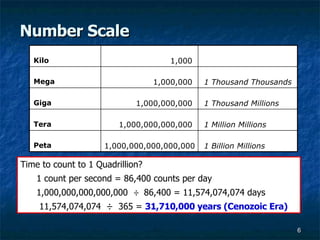
- 6. Number Scale Time to count to 1 Quadrillion? 1 count per second = 86,400 counts per day 1,000,000,000,000,000 ├Ę 86,400 = 11,574,074,074 days 11,574,074,074 ├Ę 365 = 31,710,000 years (Cenozoic Era) Kilo Mega Giga Tera Peta 1 Billion Millions 1,000,000,000,000,000 QUADRILLION 1 Million Millions 1,000,000,000,000 TRILLION 1 Thousand Millions 1,000,000,000 BILLION 1 Thousand Thousands 1,000,000 MILLION ╠² 1,000 THOUSAND
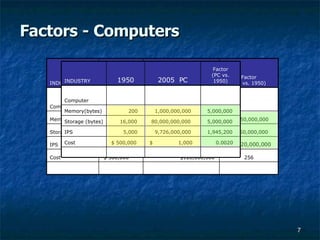
- 7. Factors - Computers ╠² ╠² ╠² ╠² 256 $128,000,000 $ 500,000 Cost 56,120,000,000 280,600,000,000 5,000 IPS 250,000,000 4,000,000,000,000 16,000 Storage (bytes) 10,250,000,000 4,000,000,000,000 200 Memory(bytes) ╠² ╠² ╠² Computer ╠² ╠² ╠² ╠² Factor (SC vs. 1950) 2007 Supercomputer 1950 INDUSTRY ╠² ╠² ╠² ╠² 0.0020 $ 1,000 $ 500,000 Cost 1,945,200 9,726,000,000 5,000 IPS 5,000,000 80,000,000,000 16,000 Storage (bytes) 5,000,000 1,000,000,000 200 Memory(bytes) ╠² ╠² ╠² Computer ╠² ╠² ╠² ╠² Factor (PC vs. 1950) 2005 PC 1950 INDUSTRY
- 8. IBM Blue Gene - Supercomputer
- 9. True/False: 1950 vs. 2005 Homes are 20 times more expensive. Cars are 15 times more expensive. Computers are 100,000 times more powerful. The development and innovation of computing technology has resulted in the greatest cultural revolution in the history of mankind. You will use computers in some form for the rest of your life.
- 10. Malicious Software Spyware Viruses Hardware Software
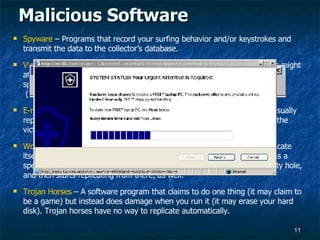
- 11. Malicious Software Spyware ŌĆō Programs that record your surfing behavior and/or keystrokes and transmit the data to the collectorŌĆÖs database. Viruses - Programs that piggyback on real programs. For example, a virus might attach itself to a program such as a spreadsheet program. Each time the spreadsheet program runs, the virus runs too where it can reproduce (by attaching to other programs) or wreak system havoc. E-mail Viruses ŌĆō An E-mail virus is transmitted via e-mail messages and usually replicates automatically by mailing a copy of itself to dozens of people in the victim's e-mail address book. Worms - Software that use computer networks and security holes to replicate itself. A copy of the worm scans the network for another machine that has a specific security hole. It copies itself to the new machine using the security hole, and then starts replicating from there, as well. Trojan Horses ŌĆō A software program that claims to do one thing (it may claim to be a game) but instead does damage when you run it (it may erase your hard disk). Trojan horses have no way to replicate automatically.
- 12. Malicious Software: Deal with it! Spyware Pay attention to what you click. DonŌĆÖt click on ŌĆ£too good to be trueŌĆØ ads. Google it! Check for hoaxes. Get Anti-Spyware software (2) Ad-Aware CounterSpy SpyBot
- 13. Viruses DonŌĆÖt click on executables ! DonŌĆÖt open suspicious eMail. Install Anti-Virus Software Malicious Software How to Deal? AVG Anti-Virus Anti-Vir
- 14. Executable File Extensions MDE - Microsoft Access MDE Database MSC - Microsoft Common Console Document MSI - Windows Installer Package MSP - Windows Installer Patch MST - Visual Test Source File OCX - ActiveX Objects PCD - Photo CD Image PIF - Shortcut to MS-DOS Program POT - PowerPoint Templates PPT - PowerPoint Files REG - Registration Entries SCR - Screen Saver SCT - Windows Script Component SHB - Document Shortcut File SYS - System Config/Driver URL - Internet Shortcut VB - VBScript File VBE - VBScript Encoded Script File VBS - VBScript Script File WSH - Windows Scripting Host Settings File XL* - Excel Files and Templates File types that should be considered suspicious when received in email and should not be opened unless you requested or expected the attachment: MDE - Microsoft Access MDE Database MSC - Microsoft Common Console Document MSI - Windows Installer Package MSP - Windows Installer Patch MST - Visual Test Source File OCX - ActiveX Objects PCD - Photo CD Image PIF - Shortcut to MS-DOS Program POT - PowerPoint Templates PPT - PowerPoint Files REG - Registration Entries SCR - Screen Saver SCT - Windows Script Component SHB - Document Shortcut File SYS - System Config/Driver URL - Internet Shortcut VB - VBScript File VBE - VBScript Encoded Script File VBS - VBScript Script File WSH - Windows Scripting Host Settings File XL* - Excel Files and Templates ADE - Microsoft Access Project Extension ADP - Microsoft Access Project BAS - Visual Basic Class Module BAT - Batch File CHM - Compiled HTML Help File CMD - Windows NT Command Script COM - MS-DOS Application CPL - Control Panel Extension CRT - Security Certificate DLL - Dynamic Link Library DO* - Word Documents and Templates EXE - Application HLP - Windows Help File HTA - HTML Applications INF - Setup Information File INS - Internet Communication Settings ISP - Internet Communication Settings JS - JScript File JSE - JScript Encoded Script File LNK - Shortcut MDB - Microsoft Access Application ADE - Microsoft Access Project Extension ADP - Microsoft Access Project BAS - Visual Basic Class Module BAT - Batch File CHM - Compiled HTML Help File CMD - Windows NT Command Script COM - MS-DOS Application CPL - Control Panel Extension CRT - Security Certificate DLL - Dynamic Link Library DO* - Word Documents and Templates EXE - Application HLP - Windows Help File HTA - HTML Applications INF - Setup Information File INS - Internet Communication Settings ISP - Internet Communication Settings JS - JScript File JSE - JScript Encoded Script File LNK - Shortcut MDB - Microsoft Access Application MDE - Microsoft Access MDE Database MSC - Microsoft Common Console Document MSI - Windows Installer Package MSP - Windows Installer Patch MST - Visual Test Source File OCX - ActiveX Objects PCD - Photo CD Image PIF - Shortcut to MS-DOS Program POT - PowerPoint Templates PPT - PowerPoint Files REG - Registration Entries SCR - Screen Saver SCT - Windows Script Component SHB - Document Shortcut File SYS - System Config/Driver URL - Internet Shortcut VB - VBScript File VBE - VBScript Encoded Script File VBS - VBScript Script File WSH - Windows Scripting Host Settings File XL* - Excel Files and Templates ADE - Microsoft Access Project Extension ADP - Microsoft Access Project BAS - Visual Basic Class Module BAT - Batch File CHM - Compiled HTML Help File CMD - Windows NT Command Script COM - MS-DOS Application CPL - Control Panel Extension CRT - Security Certificate DLL - Dynamic Link Library DO* - Word Documents and Templates EXE - Application HLP - Windows Help File HTA - HTML Applications INF - Setup Information File INS - Internet Communication Settings ISP - Internet Communication Settings JS - JScript File JSE - JScript Encoded Script File LNK - Shortcut MDB - Microsoft Access Application
- 15. Phishing Threat
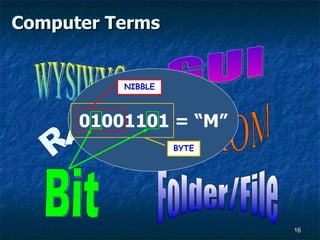
- 16. Computer Terms WYSIWYG GUI RAM CD-ROM Bit Folder/File 01001101 = ŌĆ£MŌĆØ BYTE NIBBLE
- 17. Terms Mega Giga Tera Nano ENIAC IBM DEC Apple RFID Hardware Software CPU Disk/Hard Drive Batch Processing Timesharing MIPS/FLOPS Kilo GUI
- 18. 1.1 History of Computers Nanocomputer CPU Memory Board
- 19. 1.1 History of Computers ŌĆō 1940ŌĆÖs 1941 1949
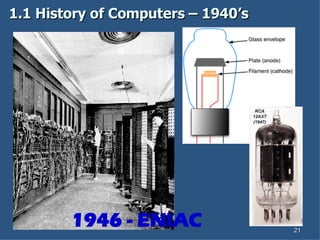
- 20. 1.1 History of Computers ŌĆō 1940ŌĆÖs 1800 square feet, 30 tons and consumed 160 kilowatts of electrical power. 1000 times faster than any other calculating machine to date. Performed 5,000 additions (5 KIPS), 357 multiplications or 38 divisions (FLOPS) Programming ENIAC entailed flipping switches and moving plug cords. Developed by John Mauchley and J. Presper Eckert 18 months and $500,000 tax dollars to build. Military Uses: Calculate trajectories Design hydrogen bomb Weather prediction Wind-tunnel design. 17,468 vacuum tubes, 70,000 resistors, 10,000 capacitors, 1,500 relays, 6,000 manual switches and 5 million soldered joints. 1946 - ENIAC ENIAC ENIAC
- 21. 1.1 History of Computers ŌĆō 1940ŌĆÖs 1946 - ENIAC
- 22. 1.1 History of Computers ŌĆō 1940ŌĆÖs 1945 - Vannevar Bush ŌĆ£ As we May Think ŌĆØ Bush calls for a new relationship between ŌĆ£ thinking man and the sum of our knowledgeŌĆ£. Proposes ŌĆ£ MemexŌĆØ - a machine that stores vast amounts of information, where users could: Create information trails Use Links b/n related texts and illustrations Store data and use for future reference.