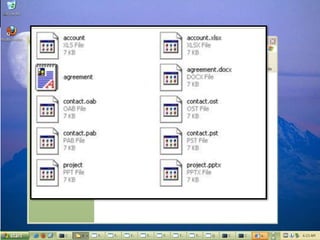
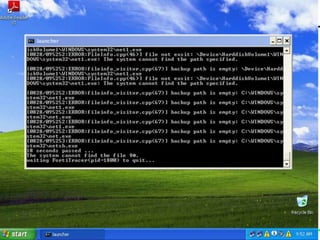
Honeypot Spotted
- 2. ABOUT ME ? @Sh1n0g1 ? Security Researcher of Macnica Networks Corp. ? Malware Simulator Developer
- 3. Malware Simulators ? Backdoor Simulator ®C ShinoBOT ®C ShinoBOT.ps1 ? APT Simulator ®C ShinoBOT Suite ? Ransomware Simulator ®C ShinoLocker ? ICS Malware Simulator ®C ShinoICS (not published yet) https://shinosec.com
- 4. QUESTION? ? How do the honeypots, malware analysis systems, sandboxes look like from the attacker's point of view?
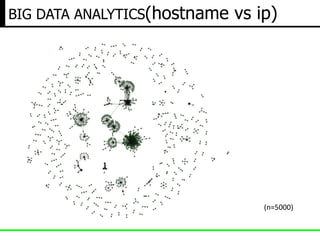
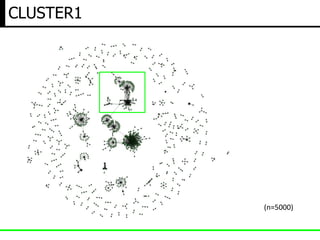
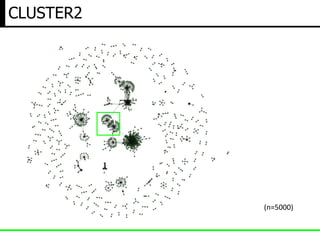
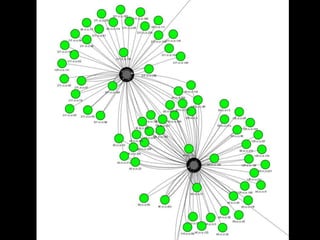
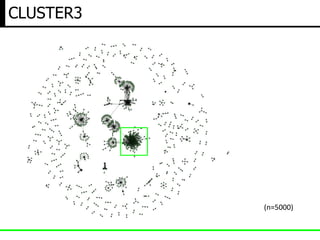
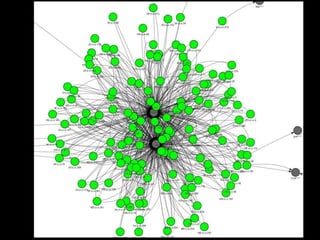
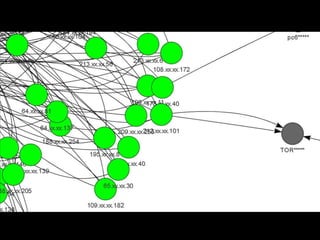
- 10. BIG DATA ANALYTICS(hostname vs ip) (n=5000)
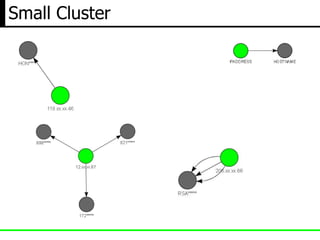
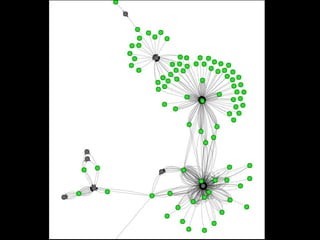
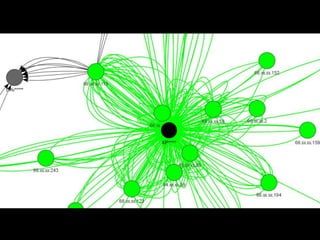
- 11. Small Cluster
- 20. "TO BE SPOTTED" does matter? ? Yes ? The attacker will create next malware which avoids to be run on the honeypots/malware analytics system/sandboxes
- 21. CONCLUSION ? Make your Honey pot "human-y" ®P dirty ? Make your Honey pot "random" ? Use an IP address which does not related with you ®C Cloud service should be good