How to convert pdf to ppt without software
•
3 likes•620 views
How to convert pdf to ppt without software,convert pdf to ppt,pdf to ppt without software,How to convert pdf to ppt
1 of 10
Download to read offline



Recommended
How to convert word doc to pdf



How to convert word doc to pdfJohn Piquero
Ěý
This document provides instructions for converting a Microsoft Word document to a PDF file format. It explains that PDF files have greater data integrity and cannot be easily modified, unlike Word documents. The steps include going to a website called doc2pdf.net, browsing to select the Word file to convert, clicking "Open" and "Convert document", and then the file will be converted to a PDF format.3 Alternates to Whiteout PDF



3 Alternates to Whiteout PDFDeftPDF
Ěý
Have you ever had that moment when you had a typographical error and you need to edit your PDF? well if you don't have Adobe Acrobat, there are other ways you can remove that error. Here are the ways you can do so with our hacks.
Tool link: https://deftpdf.com/pdf-editor
How to Convert PPT into PDF file format Online



How to Convert PPT into PDF file format OnlineCharmainne Alonzo
Ěý
The document describes the steps to convert a file to PDF format using the online tool Doc2pdf.net. It explains that the tool allows users to easily convert documents to PDF with just one click and have the converted file emailed to their email address. It then lists the step-by-step process of using Doc2pdf.net, which involves opening the website, selecting a file to convert, providing an email, and receiving the converted PDF file via email.How to convert a file to Portable Document format (PDF)?



How to convert a file to Portable Document format (PDF)?jessecadelina
Ěý
The document provides instructions for converting documents from Microsoft Word and PowerPoint to PDF format. It directs users to visit doc2pdf.net where they can browse and select the file to convert, choose the PDF format, and click "convert document" to complete the process. The instructions aim to simplify converting files to PDF.The life of era - a vb6 program



The life of era - a vb6 programMark John Lado, MIT
Ěý
Create a data from Visual Basic and print an output to MS Word.
Written and Designed by
Mark John P. Lado
What is MS Word 



What is MS Word TarandeepSingh143
Ěý
MS Word is a word processing program that allows users to create and edit documents. It functions similarly to other word processors like WordPerfect but with additional features. Users can open MS Word from the desktop or start menu to create new blank documents or choose from templates. The document provided information and instructions on various MS Word features, including inserting pictures, hyperlinks, cross-references, setting page layout options, using the references tab, mail merge, track changes for review, different view options, functions of the home tab, converting to PDF, and protecting documents with passwords.Document.docx.docx



Document.docx.docxBhavani Testone
Ěý
This document tests the compatibility of opening a Word document created with formatting and elements like headings, images, tables, etc. in other applications on different devices. It contains text formatted with styles, colors, fonts and embedded images, tables, and a drawing to check if the formatting and elements remain intact when opened in other applications like Pages, Excel, or Numbers. The document also tests if a table of contents and page numbers generated in Word carry over when the file is opened in other apps.Sw2w10



Sw2w10s1170158
Ěý
High-speed dial-up providers speed up connections by using acceleration servers with broadband connections to quickly find requested web pages and compress files before transferring them. Compression works best for text files but cannot change encrypted files. Acceleration servers filter requests and cache frequently accessed content to load web pages and connect users to high-speed dial-up systems faster than traditional dial-up. Understanding how high-speed dial-up works helps extend the life of dial-up Internet and provides an alternative for users with slow connection speeds.Best fit topology - lo1 part iv



Best fit topology - lo1 part ivAbenezer Abiti
Ěý
Ethernet is a LAN technology that transmits data at speeds between 1 Mbps to 1 Gbps. It operates at the physical and data link layers of the OSI model. The original Ethernet specification from 1980 defined the standards, while current specifications are developed by IEEE 802.3. Ethernet evolves through standards like 10BaseT, 10Base2, 10Base5, 10BaseFL, 100BaseVG, 100BaseX, which provide faster speeds and use different cable types like twisted pair, coaxial, and fiber optic cables. Ethernet frames data into packets with fields for destination/source addresses, type, and error checking.Best fit topology - lo1 part iii



Best fit topology - lo1 part iiiAbenezer Abiti
Ěý
The document discusses various network connectivity devices including network interface cards (NICs), repeaters, hubs, bridges, and switches. It provides details on the functions and operations of each device. NICs receive and transmit data to and from the network, converting electrical signals to data packets. Repeaters and hubs extend network reach but do not filter or prioritize traffic. Bridges split a network into segments and filter traffic by MAC address. Switches learn MAC addresses to selectively transmit frames to destination ports, improving network efficiency over hubs.Best fit topology - LO1 part II



Best fit topology - LO1 part IIAbenezer Abiti
Ěý
This document discusses different types of transmission media used in computer networks, including guided and unguided media. It focuses on the three primary types of cables used to build local area networks (LANs): coaxial cable, twisted-pair cable, and fiber optic cable. For each cable type, the document describes the cable construction, common varieties used in networking, maximum data transmission speeds, and typical applications. Twisted-pair cable is highlighted as the most common medium in modern LANs.Best fit topology - LO1 part I



Best fit topology - LO1 part IAbenezer Abiti
Ěý
This document provides information on network topologies. It begins by defining key terms like computer networks and networking. It then covers different types of network topologies including physical topologies like bus, star, ring, mesh and hybrid and logical topologies like broadcast and token passing. For each topology, it discusses the basic structure, how communication works, advantages and disadvantages. The document also covers other network concepts like the difference between LAN, MAN, WAN, protocols, and factors to consider when choosing a topology.Build internet infrastructure LO1



Build internet infrastructure LO1Abenezer Abiti
Ěý
This document provides information about planning and designing internet infrastructure. It defines internet infrastructure as the collection of hardware and software that enables internet operations, including transmission lines, routing equipment, DNS, email servers, databases, and other critical components. The key components of internet infrastructure are data centers, networks, computer equipment, storage services, and server applications. Common transmission media for internet infrastructure are coaxial cable, twisted pair cable, and fiber optic cable.How to convert pdf to excel without software 



How to convert pdf to excel without software Abenezer Abiti
Ěý
How to convert pdf to excel without software,convert pdf to excel without software,pdf to excel,pdf to excel without software,How to convert pdf to excel without software PPTPlan and organize work 



Plan and organize work Abenezer Abiti
Ěý
This document provides information on planning and organizing work. It defines key terms like plan, work, objectives, and resources. It describes setting objectives by linking them to organizational aims and making them measurable. It explains breaking work down into subtasks and prioritizing them. The document also covers allocating resources to tasks and creating a time schedule by listing activities with intended start and finish dates.File management 



File management Abenezer Abiti
Ěý
This document provides information about file management in Windows XP. It defines key concepts like files, folders, storage media, and computers. It explains common rules for naming files and folders and how to locate information based on file paths. It also describes how to use Windows Explorer to display, search for, select, create, rename, move, and delete files and folders. The document emphasizes that proper file management is important for storing, reusing, and sharing information on a computer.Introduction to windows xp



Introduction to windows xpAbenezer Abiti
Ěý
The document provides an introduction to the basics of Windows XP, including:
- The desktop contains the Start button, icons, taskbar, and notification area for running programs.
- Files and folders are organized in windows; common window elements include the title bar, menu bar, and buttons for minimizing, maximizing, and closing.
- Data is stored on storage devices like hard disks and USB drives, organized in a file structure with folders that can contain subfolders.Ethiopian Music Theory 



Ethiopian Music Theory Abenezer Abiti
Ěý
The document discusses music scales and their components. It defines a scale as a collection of notes grouped together based on musical relationships. It explains that major and minor scales typically consist of seven notes and are octave-repeating patterns. It provides examples of major scales using sharps and flats. It also discusses the chromatic scale, diatonic major scales, diatonic natural minor scales, and melodic minor scales. It provides the intervals, steps, and formulas that define each type of scale.Introduction to power point 2007 docx



Introduction to power point 2007 docxAbenezer Abiti
Ěý
The document provides an introduction and instructions for using Microsoft PowerPoint. It is divided into two main sections. Section 1 defines PowerPoint and discusses terminology and tips for creating effective presentations. Section 2 provides a step-by-step exercise to create a sample PowerPoint presentation on making a peanut butter and jelly sandwich, demonstrating how to add slides, text, images, colors and other formatting. The exercise covers starting PowerPoint, adding and formatting slides, saving the presentation, and viewing slide shows. The overall document aims to familiarize users with PowerPoint's basic features and interface.Ms access 2007 pptx



Ms access 2007 pptxAbenezer Abiti
Ěý
This document provides an introduction to Microsoft Access 2007, including:
1) Databases are used to organize related information into tables, queries, forms, and reports. Tables store the core data, while queries find and retrieve data, forms provide interfaces to view and edit data, and reports analyze and present data.
2) Proper database design includes determining the database purpose and intended uses, defining relevant tables and their fields, identifying primary keys to connect tables, and determining relationships between tables.
3) The core components of an Access database are tables, which organize data into rows and columns. Fields define the columns and have properties like data type and size that determine how data is stored and displayed.Ms excel 2007 pptx



Ms excel 2007 pptxAbenezer Abiti
Ěý
This document provides an introduction to Microsoft Excel and how to perform common tasks in Excel. It explains that Excel is a spreadsheet program where data is organized into columns and rows within a grid. It then outlines several reasons for using Excel, such as to analyze data, write formulas to perform calculations, pivot data, and present information visually in charts. The document proceeds to describe various methods for opening, creating, and saving Excel files. It also provides instructions for common formatting and editing tasks like naming and adding worksheets, adjusting cell sizes, entering data, working with formulas and functions, sorting and filtering data, and basic formatting options.Ms word 2007 pptx



Ms word 2007 pptxAbenezer Abiti
Ěý
Microsoft Word is a word processing program that allows users to type, edit, and save documents. The document provides an introduction to MS Word 2007, describing its purpose and main components. It explains that Word 2007 introduced the ribbon interface which organizes commands into tabs and groups, replacing the traditional menus and toolbars. It also outlines the main tabs in the ribbon, including the Home, Insert, and Page Layout tabs, describing the functions of each group within the tabs.Operate personal computer 



Operate personal computer Abenezer Abiti
Ěý
This document provides information about operating a personal computer. It discusses starting the computer by checking peripheral connections and power input. It defines peripheral devices as those connected but not core to the computer, like input devices (mouse, keyboard), output devices (monitor, printer) and storage devices. It details starting the learning process to operate the computer and applications, including navigating the desktop environment, organizing files and folders, printing, and using word processing.Determine best fit topology



Determine best fit topologyAbenezer Abiti
Ěý
This document provides information on determining the best network topology. It describes the key types of network topologies including bus, star, ring, mesh, hybrid and tree. For each topology, it outlines the basic design, how communication works, advantages and disadvantages. The document is intended to help identify the appropriate topology based on factors like equipment, growth needs, management approach and more.Identify and resolve network problems



Identify and resolve network problemsAbenezer Abiti
Ěý
This document discusses network monitoring tools and techniques. It defines network monitoring as the process of collecting network activity statistics to inform management decisions. Regular monitoring is needed to troubleshoot problems, identify slow or failing components, and notify administrators of outages. Common diagnostic tools discussed include Ping, Traceroute, Ipconfig and Netstat which can test connectivity and determine device availability. The document also outlines some network monitoring platforms and utilities that can perform specialized tasks like protocol analysis, connectivity testing and log analysis.Configure and administer server



Configure and administer serverAbenezer Abiti
Ěý
The document discusses configuring and administering servers. It defines network operating systems and their characteristics. A network OS is software that runs on a server and enables it to manage networking functions. It also defines servers and their roles in providing services and resources to users. The document outlines learning outcomes related to confirming server specifications, verifying compatibility and interoperability, and configuring and testing servers.Configure and administer server



Configure and administer serverAbenezer Abiti
Ěý
The document discusses configuring and administering servers. It defines network operating systems and their characteristics. A network OS is software that runs on a server and enables it to manage networking functions. It also defines servers and their roles in providing services and resources to users. The document outlines learning outcomes related to confirming server specifications, verifying compatibility and interoperability, and configuring and testing servers.Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan
Ěý
This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG (coming 2025)
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at art_morgan@att.net.
100% human made.THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
Ěý
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.The Constructor's Digital Transformation Playbook: Reducing Risk With Technology



The Constructor's Digital Transformation Playbook: Reducing Risk With TechnologyAggregage
Ěý
https://www.professionalconstructorcentral.com/frs/27678427/the-constructor-s-digital-transformation-playbook--reducing-risk-with-technology
Reduce risk and boost efficiency with digital transformation in construction. Join us to explore how AI, automation, and data-driven insights can improve project safety and streamline operations.More Related Content
More from Abenezer Abiti (19)
Best fit topology - lo1 part iv



Best fit topology - lo1 part ivAbenezer Abiti
Ěý
Ethernet is a LAN technology that transmits data at speeds between 1 Mbps to 1 Gbps. It operates at the physical and data link layers of the OSI model. The original Ethernet specification from 1980 defined the standards, while current specifications are developed by IEEE 802.3. Ethernet evolves through standards like 10BaseT, 10Base2, 10Base5, 10BaseFL, 100BaseVG, 100BaseX, which provide faster speeds and use different cable types like twisted pair, coaxial, and fiber optic cables. Ethernet frames data into packets with fields for destination/source addresses, type, and error checking.Best fit topology - lo1 part iii



Best fit topology - lo1 part iiiAbenezer Abiti
Ěý
The document discusses various network connectivity devices including network interface cards (NICs), repeaters, hubs, bridges, and switches. It provides details on the functions and operations of each device. NICs receive and transmit data to and from the network, converting electrical signals to data packets. Repeaters and hubs extend network reach but do not filter or prioritize traffic. Bridges split a network into segments and filter traffic by MAC address. Switches learn MAC addresses to selectively transmit frames to destination ports, improving network efficiency over hubs.Best fit topology - LO1 part II



Best fit topology - LO1 part IIAbenezer Abiti
Ěý
This document discusses different types of transmission media used in computer networks, including guided and unguided media. It focuses on the three primary types of cables used to build local area networks (LANs): coaxial cable, twisted-pair cable, and fiber optic cable. For each cable type, the document describes the cable construction, common varieties used in networking, maximum data transmission speeds, and typical applications. Twisted-pair cable is highlighted as the most common medium in modern LANs.Best fit topology - LO1 part I



Best fit topology - LO1 part IAbenezer Abiti
Ěý
This document provides information on network topologies. It begins by defining key terms like computer networks and networking. It then covers different types of network topologies including physical topologies like bus, star, ring, mesh and hybrid and logical topologies like broadcast and token passing. For each topology, it discusses the basic structure, how communication works, advantages and disadvantages. The document also covers other network concepts like the difference between LAN, MAN, WAN, protocols, and factors to consider when choosing a topology.Build internet infrastructure LO1



Build internet infrastructure LO1Abenezer Abiti
Ěý
This document provides information about planning and designing internet infrastructure. It defines internet infrastructure as the collection of hardware and software that enables internet operations, including transmission lines, routing equipment, DNS, email servers, databases, and other critical components. The key components of internet infrastructure are data centers, networks, computer equipment, storage services, and server applications. Common transmission media for internet infrastructure are coaxial cable, twisted pair cable, and fiber optic cable.How to convert pdf to excel without software 



How to convert pdf to excel without software Abenezer Abiti
Ěý
How to convert pdf to excel without software,convert pdf to excel without software,pdf to excel,pdf to excel without software,How to convert pdf to excel without software PPTPlan and organize work 



Plan and organize work Abenezer Abiti
Ěý
This document provides information on planning and organizing work. It defines key terms like plan, work, objectives, and resources. It describes setting objectives by linking them to organizational aims and making them measurable. It explains breaking work down into subtasks and prioritizing them. The document also covers allocating resources to tasks and creating a time schedule by listing activities with intended start and finish dates.File management 



File management Abenezer Abiti
Ěý
This document provides information about file management in Windows XP. It defines key concepts like files, folders, storage media, and computers. It explains common rules for naming files and folders and how to locate information based on file paths. It also describes how to use Windows Explorer to display, search for, select, create, rename, move, and delete files and folders. The document emphasizes that proper file management is important for storing, reusing, and sharing information on a computer.Introduction to windows xp



Introduction to windows xpAbenezer Abiti
Ěý
The document provides an introduction to the basics of Windows XP, including:
- The desktop contains the Start button, icons, taskbar, and notification area for running programs.
- Files and folders are organized in windows; common window elements include the title bar, menu bar, and buttons for minimizing, maximizing, and closing.
- Data is stored on storage devices like hard disks and USB drives, organized in a file structure with folders that can contain subfolders.Ethiopian Music Theory 



Ethiopian Music Theory Abenezer Abiti
Ěý
The document discusses music scales and their components. It defines a scale as a collection of notes grouped together based on musical relationships. It explains that major and minor scales typically consist of seven notes and are octave-repeating patterns. It provides examples of major scales using sharps and flats. It also discusses the chromatic scale, diatonic major scales, diatonic natural minor scales, and melodic minor scales. It provides the intervals, steps, and formulas that define each type of scale.Introduction to power point 2007 docx



Introduction to power point 2007 docxAbenezer Abiti
Ěý
The document provides an introduction and instructions for using Microsoft PowerPoint. It is divided into two main sections. Section 1 defines PowerPoint and discusses terminology and tips for creating effective presentations. Section 2 provides a step-by-step exercise to create a sample PowerPoint presentation on making a peanut butter and jelly sandwich, demonstrating how to add slides, text, images, colors and other formatting. The exercise covers starting PowerPoint, adding and formatting slides, saving the presentation, and viewing slide shows. The overall document aims to familiarize users with PowerPoint's basic features and interface.Ms access 2007 pptx



Ms access 2007 pptxAbenezer Abiti
Ěý
This document provides an introduction to Microsoft Access 2007, including:
1) Databases are used to organize related information into tables, queries, forms, and reports. Tables store the core data, while queries find and retrieve data, forms provide interfaces to view and edit data, and reports analyze and present data.
2) Proper database design includes determining the database purpose and intended uses, defining relevant tables and their fields, identifying primary keys to connect tables, and determining relationships between tables.
3) The core components of an Access database are tables, which organize data into rows and columns. Fields define the columns and have properties like data type and size that determine how data is stored and displayed.Ms excel 2007 pptx



Ms excel 2007 pptxAbenezer Abiti
Ěý
This document provides an introduction to Microsoft Excel and how to perform common tasks in Excel. It explains that Excel is a spreadsheet program where data is organized into columns and rows within a grid. It then outlines several reasons for using Excel, such as to analyze data, write formulas to perform calculations, pivot data, and present information visually in charts. The document proceeds to describe various methods for opening, creating, and saving Excel files. It also provides instructions for common formatting and editing tasks like naming and adding worksheets, adjusting cell sizes, entering data, working with formulas and functions, sorting and filtering data, and basic formatting options.Ms word 2007 pptx



Ms word 2007 pptxAbenezer Abiti
Ěý
Microsoft Word is a word processing program that allows users to type, edit, and save documents. The document provides an introduction to MS Word 2007, describing its purpose and main components. It explains that Word 2007 introduced the ribbon interface which organizes commands into tabs and groups, replacing the traditional menus and toolbars. It also outlines the main tabs in the ribbon, including the Home, Insert, and Page Layout tabs, describing the functions of each group within the tabs.Operate personal computer 



Operate personal computer Abenezer Abiti
Ěý
This document provides information about operating a personal computer. It discusses starting the computer by checking peripheral connections and power input. It defines peripheral devices as those connected but not core to the computer, like input devices (mouse, keyboard), output devices (monitor, printer) and storage devices. It details starting the learning process to operate the computer and applications, including navigating the desktop environment, organizing files and folders, printing, and using word processing.Determine best fit topology



Determine best fit topologyAbenezer Abiti
Ěý
This document provides information on determining the best network topology. It describes the key types of network topologies including bus, star, ring, mesh, hybrid and tree. For each topology, it outlines the basic design, how communication works, advantages and disadvantages. The document is intended to help identify the appropriate topology based on factors like equipment, growth needs, management approach and more.Identify and resolve network problems



Identify and resolve network problemsAbenezer Abiti
Ěý
This document discusses network monitoring tools and techniques. It defines network monitoring as the process of collecting network activity statistics to inform management decisions. Regular monitoring is needed to troubleshoot problems, identify slow or failing components, and notify administrators of outages. Common diagnostic tools discussed include Ping, Traceroute, Ipconfig and Netstat which can test connectivity and determine device availability. The document also outlines some network monitoring platforms and utilities that can perform specialized tasks like protocol analysis, connectivity testing and log analysis.Configure and administer server



Configure and administer serverAbenezer Abiti
Ěý
The document discusses configuring and administering servers. It defines network operating systems and their characteristics. A network OS is software that runs on a server and enables it to manage networking functions. It also defines servers and their roles in providing services and resources to users. The document outlines learning outcomes related to confirming server specifications, verifying compatibility and interoperability, and configuring and testing servers.Configure and administer server



Configure and administer serverAbenezer Abiti
Ěý
The document discusses configuring and administering servers. It defines network operating systems and their characteristics. A network OS is software that runs on a server and enables it to manage networking functions. It also defines servers and their roles in providing services and resources to users. The document outlines learning outcomes related to confirming server specifications, verifying compatibility and interoperability, and configuring and testing servers.Recently uploaded (20)
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan
Ěý
This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG (coming 2025)
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at art_morgan@att.net.
100% human made.THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
Ěý
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.The Constructor's Digital Transformation Playbook: Reducing Risk With Technology



The Constructor's Digital Transformation Playbook: Reducing Risk With TechnologyAggregage
Ěý
https://www.professionalconstructorcentral.com/frs/27678427/the-constructor-s-digital-transformation-playbook--reducing-risk-with-technology
Reduce risk and boost efficiency with digital transformation in construction. Join us to explore how AI, automation, and data-driven insights can improve project safety and streamline operations.What's New? ThousandEyes Product Features and Highlights



What's New? ThousandEyes Product Features and HighlightsThousandEyes
Ěý
Presented by Jonathan ZarkowerAI Trends and Fun Demos – Sotheby’s Rehoboth Presentation



AI Trends and Fun Demos – Sotheby’s Rehoboth PresentationEthan Holland
Ěý
Ethan B. Holland explores the impact of artificial intelligence on real estate and digital transformation. Covering key AI trends such as multimodal AI, agency, co-pilots, and AI-powered computer usage, the document highlights how emerging technologies are reshaping industries. It includes real-world demonstrations of AI in action, from automated real estate insights to AI-generated voice and video applications. With expertise in digital transformation, Ethan shares insights from his work optimizing workflows with AI tools, automation, and large language models. This presentation is essential for professionals seeking to understand AI’s role in business, automation, and real estate.
Revolutionizing Field Service: How LLMs Are Powering Smarter Knowledge Access...



Revolutionizing Field Service: How LLMs Are Powering Smarter Knowledge Access...Earley Information Science
Ěý
Revolutionizing Field Service with LLM-Powered Knowledge Management
Field service technicians need instant access to accurate repair information, but outdated knowledge systems often create frustrating delays. Large Language Models (LLMs) are changing the game—enhancing knowledge retrieval, streamlining troubleshooting, and reducing technician dependency on senior staff.
In this webinar, Seth Earley and industry experts Sanjay Mehta, and Heather Eisenbraun explore how LLMs and Retrieval-Augmented Generation (RAG) are transforming field service operations. Discover how AI-powered knowledge management is improving efficiency, reducing downtime, and elevating service quality.
LLMs for Instant Knowledge Retrieval – How AI-driven search dramatically cuts troubleshooting time.
Structured Data & AI – Why high-quality, organized knowledge is essential for LLM success.
Real-World Implementation – Lessons from deploying LLM-powered knowledge tools in field service.
Business Impact – How AI reduces service delays, optimizes workflows, and enhances technician productivity.
Empower your field service teams with AI-driven knowledge access. Watch the webinar to see how LLMs are revolutionizing service efficiency.Benchmark Testing Demystified: Your Roadmap to Peak Performance



Benchmark Testing Demystified: Your Roadmap to Peak PerformanceShubham Joshi
Ěý
Benchmark testing is the cornerstone of understanding your system’s performance, and this guide breaks it down step-by-step. Learn how to design tests that simulate real-world conditions, measure key performance metrics, and interpret results effectively. This comprehensive roadmap covers everything from selecting the right tools to creating repeatable tests that help identify bottlenecks and optimize resource usage. Whether you're dealing with web applications, mobile apps, or enterprise software, this guide offers practical tips and real-life examples to ensure your system runs at peak efficiency.Mastering ChatGPT & LLMs for Practical Applications: Tips, Tricks, and Use Cases



Mastering ChatGPT & LLMs for Practical Applications: Tips, Tricks, and Use CasesSanjay Willie
Ěý
Our latest session with Astiostech covered how to unlock the full potential of ChatGPT and LLMs for real-world use!
âś… Key Takeaways:
🔹 Effective Prompting: Crafting context-specific, high-quality prompts for optimal AI responses.
🔹 Advanced ChatGPT Features: Managing system prompts, conversation memory, and file uploads.
🔹 Optimizing AI Outputs: Refining responses, handling large texts, and knowing when fine-tuning is needed.
🔹 Competitive Insights: Exploring how ChatGPT compares with other AI tools.
🔹 Business & Content Use Cases: From summarization to SEO, sales, and audience targeting.
đź’ˇ The session provided hands-on strategies to make AI a powerful tool for content creation, decision-making, and business growth.
🚀 Are you using AI effectively in your workflow? Let’s discuss how it can improve efficiency and creativity!
#AI #ChatGPT #PromptEngineering #ArtificialIntelligence #LLM #Productivity #Astiostech"Building Trust: Strengthening Your Software Supply Chain Security", Serhii V...



"Building Trust: Strengthening Your Software Supply Chain Security", Serhii V...Fwdays
Ěý
The talk focuses on developing and integrating automation tools to enhance Supply Chain security. It addresses reproducible security practices with tools like Renovate and Wiz, as well as GitLab and JFrog Artifactory, to enforce consistent security scans seamlessly within existing workflows.
We will cover centralized artifact management for improved oversight and consistency. Furthermore, we will discuss the seamless integration of security scans into deployment tooling, featuring automatic deployment blocks for vulnerabilities and a controlled override option for flexibility.
The talk also examines tactics to keep the source code secure and up to date. We will explore the integration of runtime monitoring systems with detection capabilities and SLAs to manage and resolve issues on time.What is Blockchain and How Can Blockchain Consulting Help Businesses.pdf



What is Blockchain and How Can Blockchain Consulting Help Businesses.pdf Yodaplus Technologies Private Limited
Ěý
This is a comprehensive guide explaining how blockchain technology works, its key features, and real-world applications in industries like finance, supply chain, and retail. Learn about different blockchain networks (public, private, and consortium) and the challenges businesses face in adopting blockchain. Discover how blockchain consulting can help businesses implement secure, transparent, and efficient solutions, reducing risks and optimizing operations. This guide is ideal for businesses exploring blockchain adoption and seeking expert guidance.Getting Started with AWS - Enterprise Landing Zone for Terraform Learning & D...



Getting Started with AWS - Enterprise Landing Zone for Terraform Learning & D...Chris Wahl
Ěý
Recording: https://youtu.be/PASG0NTKUQA?si=1Ih7O9z0Lk0IzX9n
Welcome innovators! In this comprehensive tutorial, you will learn how to get started with AWS Cloud and Terraform to build an enterprise-like landing zone for a secure, low-cost environment to develop with Terraform. We'll guide you through setting up AWS Control Tower, Identity and Access Management, and creating a sandbox account, ensuring you have a safe and controlled area for learning and development. You'll also learn about budget management, single sign-on setup, and using AWS organizations for policy management. Plus, dive deep into Terraform basics, including setting up state management, migrating local state to remote state, and making resource modifications using your new infrastructure as code skills. Perfect for beginners looking to master AWS and Terraform essentials!Understanding & Utilizing SharePoint Advanced Management



Understanding & Utilizing SharePoint Advanced ManagementDrew Madelung
Ěý
Drew Madelung is a Cloud Solutions Architect and a Microsoft MVP for Office Apps and Services. He helps organizations realize what is possible with Microsoft 365 & Azure, onboard them in a secure and compliant way, and drive sustained adoption for those solutions. He is experienced in a range of technologies but specializes in the collaboration and teamwork workspaces such as Microsoft Teams, SharePoint, and OneDrive. He has helped deploy Microsoft 365 to multiple global companies while rolling out modern information protection and information governance technologies. He has been doing Microsoft consulting for 10+ years with a strength in security & compliance solutions.Salesforce Flow using development with Gen. AI



Salesforce Flow using development with Gen. AIJihun Jung
Ěý
This slides was shared for the event below.
This class is designed to dive deeper into Salesforce Flow, especially from an admin perspective.
Beyond the basics covered in the first session, running configurations, best practices, troubleshooting, and optimizing Flow for different use cases covered in the second session, we'll talk about how to connect Apex, LWC with Flow, and how you, as an Admin, can create features that are difficult to implement in Flow yourself with Gen AI.
Objective:
How to use development components in Flow. How to generate components that can be used in Flow through Gen. AI
Session Agenda:
1. Introduction and Recap
- Quick recap of Flow basics from previous sessions
2. Fundamentals of Salesforce Flow with Development Components (20 minutes)
-Provide foundational knowledge on incorporating development components into Flows.
-What are development components (Apex, Lightning Web Components, Invocable Actions, etc.)?
-Overview of how Flows can integrate these components.
3. Leveraging Gen AI to Obtain Flow-Ready Components (30 minutes)
-Generating Invocable Apex classes using Gen AI.
-Using AI to create Lightning Web Components for Salesforce Flows.
4. Best Practices for Combining Flows, Components, and AI (15 minutes)
-Optimizing performance: Avoiding overloading Flows with heavy logic.
-Governance and security considerations when using AI-generated code.
6. Interactive Q&AData-Driven Public Safety: Reliable Data When Every Second Counts



Data-Driven Public Safety: Reliable Data When Every Second CountsSafe Software
Ěý
When every second counts, you need access to data you can trust. In this webinar, we’ll explore how FME empowers public safety services to streamline their operations and safeguard communities. This session will showcase workflow examples that public safety teams leverage every day.
We’ll cover real-world use cases and demo workflows, including:
Automating Police Traffic Stop Compliance: Learn how the City of Fremont meets traffic stop data standards by automating QA/QC processes, generating error reports – saving over 2,800 hours annually on manual tasks.
Anonymizing Crime Data: Discover how cities protect citizen privacy while enabling transparent and trustworthy open data sharing.
Next Gen 9-1-1 Integration: Explore how Santa Clara County supports the transition to digital emergency response systems for faster, more accurate dispatching, including automated schema mapping for address standardization.
Extreme Heat Alerts: See how FME supports disaster risk management by automating the delivery of extreme heat alerts for proactive emergency response.
Our goal is to provide practical workflows and actionable steps you can implement right away. Plus, we’ll provide quick steps to find more information about our public safety subscription for Police, Fire Departments, EMS, HAZMAT teams, and more.
Whether you’re in a call center, on the ground, or managing operations, this webinar is crafted to help you leverage data to make informed, timely decisions that matter most.SB7 Mobile Ltd: Simplified & Secure Services



SB7 Mobile Ltd: Simplified & Secure ServicesReuben Jasper
Ěý
SB7 Mobile Ltd is enhancing customer experience by improving support accessibility, billing transparency, and security. The company has strengthened payment authorization, simplified unsubscription, and expanded customer service channels to address common concerns.Artificial Intelligence Quick Research Guide by Arthur Morgan



Artificial Intelligence Quick Research Guide by Arthur MorganArthur Morgan
Ěý
This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG (coming 2025)
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at art_morgan@att.net.
100% human made.Webinar: LF Energy GEISA: Addressing edge interoperability at the meter



Webinar: LF Energy GEISA: Addressing edge interoperability at the meterDanBrown980551
Ěý
This webinar will introduce the Grid Edge Security and Interoperability Alliance, or GEISA, an effort within LF Energy to address application interoperability at the very edge of the utility network: meters and other distribution automation devices. Over the last decade platform manufacturers have introduced the ability to run applications on electricity meters and other edge devices. Unfortunately, while many of these efforts have been built on Linux, they haven’t been interoperable. APIs and execution environment have varied from one manufacturer to the next making it impossible for utilities to obtain applications that they can run across a fleet of different devices. For utilities that want to minimize their supply chain risk by obtaining equipment from multiple suppliers, they are forced to run and maintain multiple separate management systems. Applications available for one device may need to be ported to run on another, or they may not be available at all.
GEISA addresses this by creating a vendor neutral specification for utility edge computing environments. This webinar will discuss why GEISA is important to utilities, the specific issues GEISA will solve and the new opportunities it creates for utilities, platform vendors, and application vendors. Recipes: It's About Time | FLDC 2025.pdf



Recipes: It's About Time | FLDC 2025.pdfMartin Anderson-Clutz
Ěý
Recipes are a major leap forward for adopting Drupal and website building in general. Learn how they can also make it easier than ever to manage dates and times in your website.What is FinTech A Complete Guide to Financial Technology.pdf



What is FinTech A Complete Guide to Financial Technology.pdf Yodaplus Technologies Private Limited
Ěý
It is an in-depth exploration of how technology is transforming the financial sector. Covering the evolution of FinTech from credit cards to AI-driven banking, this guide explains key innovations such as blockchain, DeFi, AI-powered assistants, and central bank digital currencies (CBDCs). Learn how FinTech is enhancing banking, lending, and payments through automation, data analytics, and decentralized solutions. Whether you're a financial professional or just curious about the future of digital finance, this guide offers valuable insights into the rapidly evolving FinTech landscape.Revolutionizing Field Service: How LLMs Are Powering Smarter Knowledge Access...



Revolutionizing Field Service: How LLMs Are Powering Smarter Knowledge Access...Earley Information Science
Ěý
What is Blockchain and How Can Blockchain Consulting Help Businesses.pdf



What is Blockchain and How Can Blockchain Consulting Help Businesses.pdf Yodaplus Technologies Private Limited
Ěý
What is FinTech A Complete Guide to Financial Technology.pdf



What is FinTech A Complete Guide to Financial Technology.pdf Yodaplus Technologies Private Limited
Ěý
How to convert pdf to ppt without software
- 1. How to convert PDF TO PPT without Software
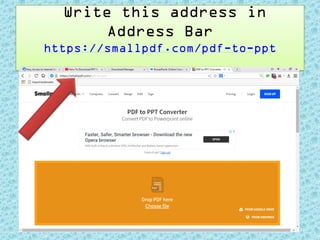
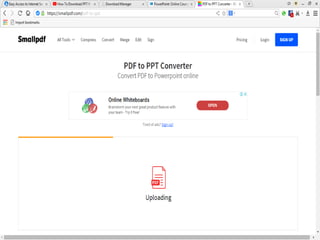
- 4. Write this address in Address Bar https://smallpdf.com/pdf-to-ppt
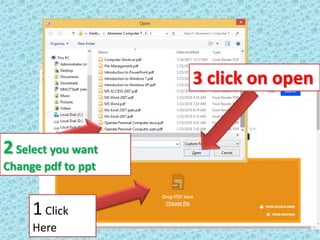
- 5. 1Click Here 2Select you want Change pdf to ppt 3 click on open
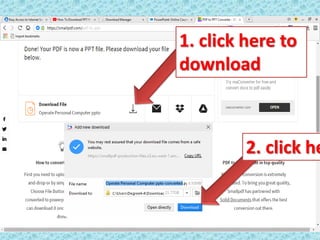
- 7. 1. click here to download 2. click he
- 10. Thank you!!
