How to do hydra-Ethical hacking
0 likes2,018 views
The document discusses how to perform a brute-force attack using the Hydra tool on Gmail accounts. It explains the requirements, process, and settings needed to configure the attack, including the use of a password list. The document also highlights security measures that prevent brute-force attacks from succeeding easily.
1 of 9


Recommended
Password Cracking
Password CrackingRahul Sharma
╠²
The document explains the concepts of password hashing in Windows systems, detailing the differences between LM and NTLM hashes. It highlights the security vulnerabilities of LM hashes, the implementation of NTLM hashes using the MD4 algorithm, and the significance of salting in preventing rainbow table attacks. Additionally, it discusses various types of brute force attacks and provides examples of real-world password cracking incidents.How to Hack Snapchat Account
How to Hack Snapchat AccountJanim Kione
╠²
The document discusses a discovered vulnerability in Snapchat's security system that can be exploited to hack accounts. It claims that the system can successfully hack 96.87% of passwords by obtaining hashes from Snapchat's server and performing a dictionary attack. The document includes a link to a website providing more information on the hacking process.Hackers secrets
Hackers secretsTengku Maulana
╠²
A hacker can potentially gain access to an unprotected system in under 15 seconds by exploiting security flaws. The document outlines how to check if a system is vulnerable by using command line tools to view the system's IP address and network configuration. It finds that if the system has a hex code of <20>, it indicates file and printer sharing is enabled, allowing hackers easy access. The guide aims to educate users on vulnerabilities so they can better protect themselves from online threats.Hack Snapchat Account
Hack Snapchat Accountjack ordert
╠²
This document describes how to hack into Snapchat accounts by exploiting a vulnerability in Snapchat's security system. It claims to be able to hack 96.87% of passwords by obtaining hashes from the Snapchat server and running a dictionary attack on them. The document promotes a website that supposedly provides the means to hack Snapchat accounts.Spyware
Spywareguest6fde72
╠²
This document defines spyware and discusses methods used for passive spyware tracking, specifically web beacons and cookies. It demonstrates how a web beacon can be used to deposit a cookie and track browsing activity without consent. The document concludes that browser settings can prevent cookie deposit and users should be cautious about what they download or open online.Password craking techniques
Password craking techniques žŻžŁ┘䞦┘ģ ž¦┘åžĄž¦ž▒┘ē
╠²
The document discusses various techniques for cracking passwords, including dictionary attacks, brute force attacks, and exploiting weaknesses in password hashing algorithms. Default passwords, social engineering through phishing emails, and the use of tools like Cain and Abel, John the Ripper, and THC Hydra are also covered as effective cracking methods. Common password mistakes that can enable cracking are also listed.Password cracking and brute force tools
Password cracking and brute force toolszeus7856
╠²
The document discusses password cracking and brute force tools, outlining various methods and tools used to gain unauthorized access to systems or recover forgotten passwords. It details common cracking techniques such as brute force attacks, social engineering, and phishing, along with specific tools like Brutus, RainbowCrack, and Cain & Abel. Emphasis is placed on the importance of complex passwords to counteract these attacks and the various methods employed by hackers to acquire sensitive information.Password hacking
Password hackingMr. FM
╠²
This document provides instructions on how to hack passwords and create an FTP server on a PC. It discusses techniques like hashing, guessing, using default passwords, brute force attacks, and phishing to hack passwords. It also describes how to crack Windows passwords using tools like Cain and Abel. Additionally, it outlines the steps to obtain a static IP address, install and configure an FTP server software, and set up user accounts on the server.Ethical hacking for Business or Management.pptx
Ethical hacking for Business or Management.pptxFarhanaMariyam1
╠²
The document discusses ethical hacking and password cracking techniques. It begins with an introduction to ethical hacking and defines it as testing systems for security purposes with authorization. It then covers various password cracking techniques like dictionary attacks, brute force attacks, default passwords, and social engineering. Specific tools mentioned that can be used for password cracking include Cain and Abel, John the Ripper, THC Hydra, and rainbow tables. Common password mistakes are also listed. The document provides information on ethical hacking and analyzing various methods for cracking passwords.Password hacking
Password hackingAbhay pal
╠²
1) Password cracking is the process of recovering secret passwords through various techniques like hashing, guessing using dictionaries, using default passwords, brute force, and phishing.
2) Common password cracking techniques include exploiting weak hashing algorithms, guessing using common words and personal details, using default passwords for applications, trying all possible character combinations through brute force, and tricking users into revealing passwords through phishing.
3) IP spoofing involves modifying the source IP address field in the IP packet header to disguise the identity of the sender or impersonate another system and exploit weaknesses in the connection-oriented TCP protocol.Gamifying Ethical hacking for education.pptx
Gamifying Ethical hacking for education.pptxyg5ptrdvbg
╠²
The document discusses ethical hacking as a practice focused on securing systems rather than maliciously exploiting them. It differentiates between ethical hackers and malicious hackers, emphasizing that ethical hacking is performed legally with permission for the betterment of technology. Additionally, it covers various password cracking techniques and the importance of using strong passwords to prevent unauthorized access.Brute force
Brute forcePrajwal Panchmahalkar
╠²
A brute force attack is a trial-and-error method to decrypt encrypted data like passwords by exhaustively checking all possible combinations without using any intelligent strategies. It is always successful eventually but can require billions of years for systems with long keys. Tools like Brutus and THC-Hydra are used to perform brute force attacks against network services to guess passwords stored in dictionaries. Session IDs, files/directories, credit card information, and password retrieval questions are also potential targets of brute force attacks. While processing intensive, brute force does not require much setup but can take a very long time.Brute Forcing
Brute Forcingn|u - The Open Security Community
╠²
A brute force attack is a trial-and-error method to decrypt encrypted data like passwords by exhaustively checking all possible combinations without using any intelligent strategies. It is always successful eventually but can require billions of years for systems with long keys. Tools like Brutus and THC-Hydra are used to perform brute force attacks against network services to guess passwords stored in dictionaries. Session IDs, files/directories, credit card information, and password retrieval questions are also potential targets of brute force attacks. While processing intensive, brute force does not require much setup but can take a very long time.Unit-4 Cybercrimes-II Mobile and Wireless Devices.ppt
Unit-4 Cybercrimes-II Mobile and Wireless Devices.pptajajkhan16
╠²
Unit-4 Cybercrimes-II Mobile and Wireless DevicesPreventions of Email Hacking
Preventions of Email HackingUsman Khan
╠²
The document presents a comprehensive overview of email hacking, outlining key hacking methods such as phishing attacks, key logging, and brute forcing. It also details several prevention strategies including careful email examination, using antivirus and encryption tools, and implementing strong password requirements. The conclusion emphasizes the importance of secondary email recovery options and maintaining email confidentiality.Password Attack
Password Attack Sina Manavi
╠²
The document outlines a hacking methodology focused on password attacks, featuring various techniques such as brute force, dictionary, and phishing attacks. It includes practical demonstrations and tools for password cracking, along with guidance on secure password practices and password hardening techniques. Additionally, it touches on the importance of password policy and the implementation of biometric technologies to enhance security.How to choose a password thatŌĆÖs hard to crack
How to choose a password thatŌĆÖs hard to crackKlaus Drosch
╠²
This document provides guidelines for creating strong passwords to enhance online security. Key recommendations include using long, complex passwords that include a mix of characters, avoiding personal information, never reusing passwords, and utilizing tools like password managers and two-factor authentication. It also outlines common hacking techniques such as brute force attacks, dictionary attacks, and phishing, highlighting the importance of password management and vigilance.Ethical hacking
Ethical hackingUnited Group Of Institution
╠²
This document discusses the concept of ethical hacking. It defines ethical hacking as testing systems for security purposes, while distinguishing it from criminal hacking. It describes different types of hackers like white hat and black hat hackers. The document then covers various hacking techniques like email hacking through phishing and keyloggers, hacking Windows systems by exploiting the SAM database, and use of trojans for remote access or data theft. Prevention methods are also highlighted for some attacks.Mobile Application Security - Broken Authentication & Management
Mobile Application Security - Broken Authentication & ManagementBarrel Software
╠²
This document discusses broken authentication and session management attacks. It defines authentication and session management, and explains the risks of broken implementations which can undermine controls and lead to privacy violations and identity theft. Several examples of attacks are described in detail, including brute force attacks, session hijacking, replay attacks, and issues with insufficient session expiration. General guidelines for prevention are outlined, such as unique user IDs, password complexity policies, secure communication, credential storage best practices, and proper logout functionality.How to hack or what is ethical hacking
How to hack or what is ethical hackingbaabtra.com - No. 1 supplier of quality freshers
╠²
This document discusses ethical hacking. It begins by defining hacking and distinguishing between black hat, white hat, and grey hat hackers. White hat hackers, also known as ethical hackers, hack systems with permission to identify vulnerabilities. The document outlines the different phases of ethical hacking including footprinting, scanning, enumeration, gaining access, and maintaining access. It provides examples of tools used in each phase and types of attacks like social engineering and SQL injection. The document emphasizes that for hacking to be ethical, hackers must have permission and respect privacy. It concludes by discussing how organizations can prevent hacking by closing vulnerabilities identified through ethical hacking activities.BS CS 5 week 6 lecture 2.pptx
BS CS 5 week 6 lecture 2.pptxwhoiam36
╠²
Hacking involves gaining unauthorized access to computer systems or modifying systems for unauthorized purposes. There are several types of hacking, including website hacking, network hacking, password hacking, software hacking, ethical hacking, email hacking, and computer hacking. Website hacking involves taking control of a website from its owner. Network hacking involves gathering information about a network domain, IP address, and ports. Password hacking is attempting to recover passwords through brute force or dictionary attacks. Software hacking modifies software to change its functionality. Ethical hacking tests system security by finding weaknesses. Email hacking accesses email accounts without authorization. Computer hacking involves unauthorized viewing, creation, editing or deletion of files.Introduction of hacking and cracking
Introduction of hacking and crackingHarshil Barot
╠²
The document provides an introduction to hacking and cracking, describing what hacking and cracking are, different types of hackers (high-level and low-level), and the difference between hackers and crackers. It also discusses common hacking techniques like password attacks, spoofing, and sniffing. The document is intended to educate about hacking and related cybersecurity topics.Personal Internet Security System
Personal Internet Security SystemMatthew Bricker
╠²
The document outlines the importance of password security and internet safety, detailing how passwords are stored as encrypted hashes and the methods used by password crackers. It advises using complex passwords, not sharing personal information, and implementing robust network security measures, including firewalls and secure Wi-Fi protocols. Additionally, it highlights the risks of weak passwords and unsecured networks that can lead to unauthorized access and data breaches.Yours Advance Security Hood (Yash)
Yours Advance Security Hood (Yash)IOSR Journals
╠²
The document proposes a new security method called Yours Advanced Security Hood (YASH) to prevent password cracking through brute force and dictionary attacks. YASH uses a two-level security approach:
1. It tracks the number of incorrect login attempts and activates a virtual machine crosschecking (VMC) process if the attempt threshold is exceeded, preventing the password from being matched to attempted passwords.
2. It allows the true user to initiate an unauthorised access control (UAC) using their mobile phone to signal that no attempts should be matched, protecting the account until the user deactivates UAC.
3. The system can then detect the true user by their ability to deactivate UAC through theirpassword cracking and Key logger
password cracking and Key loggerPatel Mit
╠²
This document discusses password cracking and keyloggers. It defines passwords and describes different types of password attacks like dictionary attacks and brute force attacks. It also lists popular password cracking tools. The document also defines keyloggers and discusses how they can be used legitimately for monitoring or illegally to steal sensitive information. It provides examples of hardware and software keyloggers and describes some methods of preventing keylogger infections like using antivirus software and alternative keyboards.AN INNOVATIVE PATTERN BASED PASSWORD METHOD USING TIME VARIABLE WITH ARITHMET...
AN INNOVATIVE PATTERN BASED PASSWORD METHOD USING TIME VARIABLE WITH ARITHMET...ijistjournal
╠²
The document presents an innovative password security method that uses a combination of user-selected patterns based on time variables and arithmetic operations to create dynamic passwords. This approach aims to protect against various password attacks, including brute-force, dictionary, phishing, and shoulder surfing. The proposed scheme enhances security by requiring the server to generate the same password dynamically for authentication, thus minimizing the risks associated with static passwords.Password Storage Explained
Password Storage Explainedjeetendra mandal
╠²
Bcrypt is a hashing function that hashes passwords with a salt and cost parameter to encrypt passwords stored in a database. The salt is randomly generated for each password, meaning the same password will hash to different values. Both the salt and cost are stored with the hashed password. Hackers may pre-compute hashes from word lists to crack hashed passwords, so proper salting is important.Cyber Security(Password Cracking Presentation).pptx
Cyber Security(Password Cracking Presentation).pptxVASUOFFICIAL
╠²
Password cracking involves techniques to gain unauthorized access to accounts by guessing passwords. Common techniques include brute force attacks that try all possible combinations, dictionary attacks that use common password lists, and rainbow tables that reverse cryptographic hashes. Defenses include using strong, unique passwords, avoiding phishing scams, and implementing multi-factor authentication.Rapid Prototyping for XR: Lecture 1 Introduction to Prototyping
Rapid Prototyping for XR: Lecture 1 Introduction to PrototypingMark Billinghurst
╠²
Lecture 1 of a course on Rapid Prototyping for XR taught by Mark Billinghurst at Oulu University on June 9th, 2025. This lecture presents an Introduction to Prototyping. (Continuous Integration and Continuous Deployment/Delivery) is a fundamental ...
(Continuous Integration and Continuous Deployment/Delivery) is a fundamental ...ketan09101
╠²
(Continuous Integration and Continuous Deployment/Delivery) is a fundamental practice in DevOps that streamlines software development and deployment.More Related Content
Similar to How to do hydra-Ethical hacking (20)
Ethical hacking for Business or Management.pptx
Ethical hacking for Business or Management.pptxFarhanaMariyam1
╠²
The document discusses ethical hacking and password cracking techniques. It begins with an introduction to ethical hacking and defines it as testing systems for security purposes with authorization. It then covers various password cracking techniques like dictionary attacks, brute force attacks, default passwords, and social engineering. Specific tools mentioned that can be used for password cracking include Cain and Abel, John the Ripper, THC Hydra, and rainbow tables. Common password mistakes are also listed. The document provides information on ethical hacking and analyzing various methods for cracking passwords.Password hacking
Password hackingAbhay pal
╠²
1) Password cracking is the process of recovering secret passwords through various techniques like hashing, guessing using dictionaries, using default passwords, brute force, and phishing.
2) Common password cracking techniques include exploiting weak hashing algorithms, guessing using common words and personal details, using default passwords for applications, trying all possible character combinations through brute force, and tricking users into revealing passwords through phishing.
3) IP spoofing involves modifying the source IP address field in the IP packet header to disguise the identity of the sender or impersonate another system and exploit weaknesses in the connection-oriented TCP protocol.Gamifying Ethical hacking for education.pptx
Gamifying Ethical hacking for education.pptxyg5ptrdvbg
╠²
The document discusses ethical hacking as a practice focused on securing systems rather than maliciously exploiting them. It differentiates between ethical hackers and malicious hackers, emphasizing that ethical hacking is performed legally with permission for the betterment of technology. Additionally, it covers various password cracking techniques and the importance of using strong passwords to prevent unauthorized access.Brute force
Brute forcePrajwal Panchmahalkar
╠²
A brute force attack is a trial-and-error method to decrypt encrypted data like passwords by exhaustively checking all possible combinations without using any intelligent strategies. It is always successful eventually but can require billions of years for systems with long keys. Tools like Brutus and THC-Hydra are used to perform brute force attacks against network services to guess passwords stored in dictionaries. Session IDs, files/directories, credit card information, and password retrieval questions are also potential targets of brute force attacks. While processing intensive, brute force does not require much setup but can take a very long time.Brute Forcing
Brute Forcingn|u - The Open Security Community
╠²
A brute force attack is a trial-and-error method to decrypt encrypted data like passwords by exhaustively checking all possible combinations without using any intelligent strategies. It is always successful eventually but can require billions of years for systems with long keys. Tools like Brutus and THC-Hydra are used to perform brute force attacks against network services to guess passwords stored in dictionaries. Session IDs, files/directories, credit card information, and password retrieval questions are also potential targets of brute force attacks. While processing intensive, brute force does not require much setup but can take a very long time.Unit-4 Cybercrimes-II Mobile and Wireless Devices.ppt
Unit-4 Cybercrimes-II Mobile and Wireless Devices.pptajajkhan16
╠²
Unit-4 Cybercrimes-II Mobile and Wireless DevicesPreventions of Email Hacking
Preventions of Email HackingUsman Khan
╠²
The document presents a comprehensive overview of email hacking, outlining key hacking methods such as phishing attacks, key logging, and brute forcing. It also details several prevention strategies including careful email examination, using antivirus and encryption tools, and implementing strong password requirements. The conclusion emphasizes the importance of secondary email recovery options and maintaining email confidentiality.Password Attack
Password Attack Sina Manavi
╠²
The document outlines a hacking methodology focused on password attacks, featuring various techniques such as brute force, dictionary, and phishing attacks. It includes practical demonstrations and tools for password cracking, along with guidance on secure password practices and password hardening techniques. Additionally, it touches on the importance of password policy and the implementation of biometric technologies to enhance security.How to choose a password thatŌĆÖs hard to crack
How to choose a password thatŌĆÖs hard to crackKlaus Drosch
╠²
This document provides guidelines for creating strong passwords to enhance online security. Key recommendations include using long, complex passwords that include a mix of characters, avoiding personal information, never reusing passwords, and utilizing tools like password managers and two-factor authentication. It also outlines common hacking techniques such as brute force attacks, dictionary attacks, and phishing, highlighting the importance of password management and vigilance.Ethical hacking
Ethical hackingUnited Group Of Institution
╠²
This document discusses the concept of ethical hacking. It defines ethical hacking as testing systems for security purposes, while distinguishing it from criminal hacking. It describes different types of hackers like white hat and black hat hackers. The document then covers various hacking techniques like email hacking through phishing and keyloggers, hacking Windows systems by exploiting the SAM database, and use of trojans for remote access or data theft. Prevention methods are also highlighted for some attacks.Mobile Application Security - Broken Authentication & Management
Mobile Application Security - Broken Authentication & ManagementBarrel Software
╠²
This document discusses broken authentication and session management attacks. It defines authentication and session management, and explains the risks of broken implementations which can undermine controls and lead to privacy violations and identity theft. Several examples of attacks are described in detail, including brute force attacks, session hijacking, replay attacks, and issues with insufficient session expiration. General guidelines for prevention are outlined, such as unique user IDs, password complexity policies, secure communication, credential storage best practices, and proper logout functionality.How to hack or what is ethical hacking
How to hack or what is ethical hackingbaabtra.com - No. 1 supplier of quality freshers
╠²
This document discusses ethical hacking. It begins by defining hacking and distinguishing between black hat, white hat, and grey hat hackers. White hat hackers, also known as ethical hackers, hack systems with permission to identify vulnerabilities. The document outlines the different phases of ethical hacking including footprinting, scanning, enumeration, gaining access, and maintaining access. It provides examples of tools used in each phase and types of attacks like social engineering and SQL injection. The document emphasizes that for hacking to be ethical, hackers must have permission and respect privacy. It concludes by discussing how organizations can prevent hacking by closing vulnerabilities identified through ethical hacking activities.BS CS 5 week 6 lecture 2.pptx
BS CS 5 week 6 lecture 2.pptxwhoiam36
╠²
Hacking involves gaining unauthorized access to computer systems or modifying systems for unauthorized purposes. There are several types of hacking, including website hacking, network hacking, password hacking, software hacking, ethical hacking, email hacking, and computer hacking. Website hacking involves taking control of a website from its owner. Network hacking involves gathering information about a network domain, IP address, and ports. Password hacking is attempting to recover passwords through brute force or dictionary attacks. Software hacking modifies software to change its functionality. Ethical hacking tests system security by finding weaknesses. Email hacking accesses email accounts without authorization. Computer hacking involves unauthorized viewing, creation, editing or deletion of files.Introduction of hacking and cracking
Introduction of hacking and crackingHarshil Barot
╠²
The document provides an introduction to hacking and cracking, describing what hacking and cracking are, different types of hackers (high-level and low-level), and the difference between hackers and crackers. It also discusses common hacking techniques like password attacks, spoofing, and sniffing. The document is intended to educate about hacking and related cybersecurity topics.Personal Internet Security System
Personal Internet Security SystemMatthew Bricker
╠²
The document outlines the importance of password security and internet safety, detailing how passwords are stored as encrypted hashes and the methods used by password crackers. It advises using complex passwords, not sharing personal information, and implementing robust network security measures, including firewalls and secure Wi-Fi protocols. Additionally, it highlights the risks of weak passwords and unsecured networks that can lead to unauthorized access and data breaches.Yours Advance Security Hood (Yash)
Yours Advance Security Hood (Yash)IOSR Journals
╠²
The document proposes a new security method called Yours Advanced Security Hood (YASH) to prevent password cracking through brute force and dictionary attacks. YASH uses a two-level security approach:
1. It tracks the number of incorrect login attempts and activates a virtual machine crosschecking (VMC) process if the attempt threshold is exceeded, preventing the password from being matched to attempted passwords.
2. It allows the true user to initiate an unauthorised access control (UAC) using their mobile phone to signal that no attempts should be matched, protecting the account until the user deactivates UAC.
3. The system can then detect the true user by their ability to deactivate UAC through theirpassword cracking and Key logger
password cracking and Key loggerPatel Mit
╠²
This document discusses password cracking and keyloggers. It defines passwords and describes different types of password attacks like dictionary attacks and brute force attacks. It also lists popular password cracking tools. The document also defines keyloggers and discusses how they can be used legitimately for monitoring or illegally to steal sensitive information. It provides examples of hardware and software keyloggers and describes some methods of preventing keylogger infections like using antivirus software and alternative keyboards.AN INNOVATIVE PATTERN BASED PASSWORD METHOD USING TIME VARIABLE WITH ARITHMET...
AN INNOVATIVE PATTERN BASED PASSWORD METHOD USING TIME VARIABLE WITH ARITHMET...ijistjournal
╠²
The document presents an innovative password security method that uses a combination of user-selected patterns based on time variables and arithmetic operations to create dynamic passwords. This approach aims to protect against various password attacks, including brute-force, dictionary, phishing, and shoulder surfing. The proposed scheme enhances security by requiring the server to generate the same password dynamically for authentication, thus minimizing the risks associated with static passwords.Password Storage Explained
Password Storage Explainedjeetendra mandal
╠²
Bcrypt is a hashing function that hashes passwords with a salt and cost parameter to encrypt passwords stored in a database. The salt is randomly generated for each password, meaning the same password will hash to different values. Both the salt and cost are stored with the hashed password. Hackers may pre-compute hashes from word lists to crack hashed passwords, so proper salting is important.Cyber Security(Password Cracking Presentation).pptx
Cyber Security(Password Cracking Presentation).pptxVASUOFFICIAL
╠²
Password cracking involves techniques to gain unauthorized access to accounts by guessing passwords. Common techniques include brute force attacks that try all possible combinations, dictionary attacks that use common password lists, and rainbow tables that reverse cryptographic hashes. Defenses include using strong, unique passwords, avoiding phishing scams, and implementing multi-factor authentication.Recently uploaded (20)
Rapid Prototyping for XR: Lecture 1 Introduction to Prototyping
Rapid Prototyping for XR: Lecture 1 Introduction to PrototypingMark Billinghurst
╠²
Lecture 1 of a course on Rapid Prototyping for XR taught by Mark Billinghurst at Oulu University on June 9th, 2025. This lecture presents an Introduction to Prototyping. (Continuous Integration and Continuous Deployment/Delivery) is a fundamental ...
(Continuous Integration and Continuous Deployment/Delivery) is a fundamental ...ketan09101
╠²
(Continuous Integration and Continuous Deployment/Delivery) is a fundamental practice in DevOps that streamlines software development and deployment.International Journal of Advanced Information Technology (IJAIT)
International Journal of Advanced Information Technology (IJAIT)ijait
╠²
International journal of advanced Information technology (IJAIT) is a bi monthly open access peer-
reviewed journal, will act as a major forum for the presentation of innovative ideas, approaches,
developments, and research projects in the area advanced information technology applications and
services. It will also serve to facilitate the exchange of information between researchers and industry
professionals to discuss the latest issues and advancement in the area of advanced IT. Core areas of
advanced IT and multi-disciplinary and its applications will be covered during the conferences.Cadastral Maps
Cadastral MapsGoogle
╠²
Preparation of cadastral maps based by Engineer Dungo Tizazu from Dire Dawa University Introduction to Natural Language Processing - Stages in NLP Pipeline, Challen...
Introduction to Natural Language Processing - Stages in NLP Pipeline, Challen...resming1
╠²
Lecture delivered in 2021. This gives an introduction to Natural Language Processing. It describes the use cases of NLP in daily life. It discusses the stages in NLP Pipeline. It highlights the challenges involved covering the different levels of ambiguity that could arise. It also gives a brief note on the present scenario with the latest language models, tools and frameworks/libraries for NLP.May 2025: Top 10 Read Articles in Data Mining & Knowledge Management Process
May 2025: Top 10 Read Articles in Data Mining & Knowledge Management ProcessIJDKP
╠²
Data mining and knowledge discovery in databases have been attracting a significant amount of research, industry, and media attention of late. There is an urgent need for a new generation of computational theories and tools to assist researchers in extracting useful information from the rapidly growing volumes of digital data.
This Journal provides a forum for researchers who address this issue and to present their work in a peer-reviewed open access forum. Authors are solicited to contribute to the Journal by submitting articles that illustrate research results, projects, surveying works and industrial experiences that describe significant advances in the following areas, but are not limited to these topics only.Deep Learning for Image Processing on 16 June 2025 MITS.pptx
Deep Learning for Image Processing on 16 June 2025 MITS.pptxresming1
╠²
This covers how image processing or the field of computer vision has advanced with the advent of neural network architectures ranging from LeNet to Vision transformers. It covers how deep neural network architectures have developed step-by-step from the popular CNNs to ViTs. CNNs and its variants along with their features are described. Vision transformers are introduced and compared with CNNs. It also shows how an image is processed to be given as input to the vision transformer. It give the applications of computer vision.Generative AI & Scientific Research : Catalyst for Innovation, Ethics & Impact
Generative AI & Scientific Research : Catalyst for Innovation, Ethics & ImpactAlqualsaDIResearchGr
╠²
Invited keynote at the Artificial Intelligence Symposium on AI-powered Research Innovation, taking place at ENSEM (L'├ēcole Nationale Sup├®rieure d'├ēlectricit├® et de M├®canique), Casablanca on June 21, 2025. IŌĆÖll be giving a keynote titled: "Generative AI & Scientific Research: Catalyst for Innovation, Ethics & Impact". Looking forward to engaging with researchers and doctoral students on how Generative AI is reshaping the future of science, from discovery to governance ŌĆö with both opportunities and responsibilities in focus.
#AI hashtag#GenerativeAI #ScientificResearch #Innovation #Ethics #Keynote #AIinScience #GAI #ResearchInnovation #Casablanca
1. Thinking, Creative Thinking, Innovation
2. Societies Evolution from 1.0 to 5.0
3. AI - 3P Approach, Use Cases & Innovation
4. GAI & Creativity
5. TrustWorthy AI
6. Guidelines on The Responsible use of GAI In ResearchIntroduction to Python Programming Language
Introduction to Python Programming Languagemerlinjohnsy
╠²
This PPT covers features, applications, variable, data types and statements in PythonProposal for folders structure division in projects.pdf
Proposal for folders structure division in projects.pdfMohamed Ahmed
╠²
Proposal for folders structure division in projectsRapid Prototyping for XR: Lecture 5 - Cross Platform Development
Rapid Prototyping for XR: Lecture 5 - Cross Platform DevelopmentMark Billinghurst
╠²
This is lecture 5 in the course about Rapid Prototyping for XR, taught by Mark Billinghurst. This lecture is about Cross Platform Development.Rapid Prototyping for XR: Lecture 4 - High Level Prototyping.
Rapid Prototyping for XR: Lecture 4 - High Level Prototyping.Mark Billinghurst
╠²
This is lecture 4 in the course on Rapid Prototyping for XR, taught by Mark Billinghurst on June 11th, 2025. This lecture is about High Level Prototyping.Stay Safe Women Security Android App Project Report.pdf
Stay Safe Women Security Android App Project Report.pdfKamal Acharya
╠²
WomenŌĆÖs security is a critical issue in todayŌĆÖs world and itŌĆÖs very much needed for every individual
to be acting over such an issue. This document describes a GPS based ŌĆ£Women Security System''
that provides the combination of GPS devices as well as provide alerts and messages with an
emergency button trigger whenever somebody is in trouble They might not have so much time, all
that they have to do is generate a distress emergency signal by shaking up their phone. Our system
provides a realizable, cost effective solution to problem detection. Nowdays due to recently
happened cases such as rape by drivers or colleagues, burglary etc., women security, especially
women security has become the foremost priority of the world. System uses the Global Positioning
System (GPS) technology to find out the location of women. The information of women's position
provided by the device can be viewed on Google maps using Internet or specialized software. The
companies are looking for-ward to the security problem and require a system that will efficiently
evaluate the problem of women security working in night shifts, traveling alone. We focus on the
proposed model that can be used to deal with the security issue of women using GPS based tracking
systems.Rapid Prototyping for XR: Lecture 2 - Low Fidelity Prototyping.
Rapid Prototyping for XR: Lecture 2 - Low Fidelity Prototyping.Mark Billinghurst
╠²
This is lecture 2 on the Rapid Prototyping for XR course taught by Mark Billingurst on June 10th 2025. This lecture is about Low Fidelity Prototyping.Generative AI & Scientific Research : Catalyst for Innovation, Ethics & Impact
Generative AI & Scientific Research : Catalyst for Innovation, Ethics & ImpactAlqualsaDIResearchGr
╠²
How to do hydra-Ethical hacking
- 1. How to do Hydra (Brute force Attack) to hack any E-mail Password POSTED ON 22:58 BY VIV EK Brute-force attack A password attack that does not attempt to decrypt any information, but continue to try different passwords. For example, a brute-force attack may have a dictionary of all words or a listing of commonly used passwords. To gain access to an account using a brute-force attack, a program tries all available words it has to gain access to the account. Another type of brute-force attack is a program that runs through all letters or letters and numbers until it gets a match. Although a brute-force attack may be able to gain access to an account eventually, these attacks can take several hours, minutes or Hour to run. The amount of time it takes to complete these attacks is dependent on how complicated the password is and how well the attacker knows the target. To help prevent brute-force attacks many systems will only allow a user to make a mistake in entering their username or password three or four times. If the user exceeds these attempts, the system will either lock them out of the system or prevent any future attempts for a set amount of time.
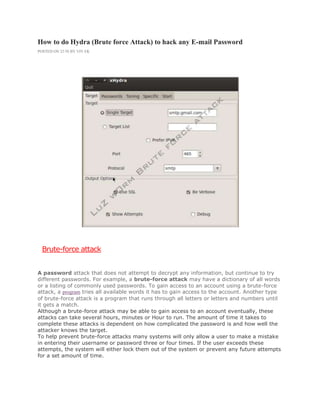
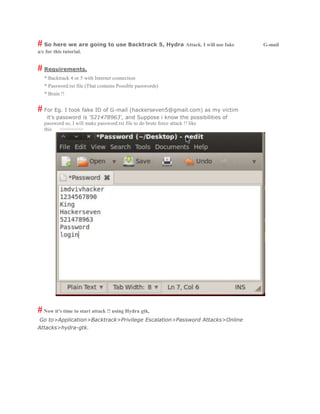
- 2. # So here we are going to use Backtrack 5, Hydra Attack. I will use fake G-mail a/c for this tutorial. # Requirements. * Backtrack 4 or 5 with Internet connection * Password.txt file (That contains Possible passwords) * Brain !! # For Eg. I took fake ID of G-mail (hackerseven5@gmail.com) as my victim it's password is '521478963', and Suppose i know the possibilities of password so, I will make password.txt file to do brute force attack !! like this >>>>>>>> #Now it's time to start attack !! using Hydra gtk, Go to>Application>Backtrack>Privilege Escalation>Password Attacks>Online Attacks>hydra-gtk.
- 3. # And it will start like this >>>>>>
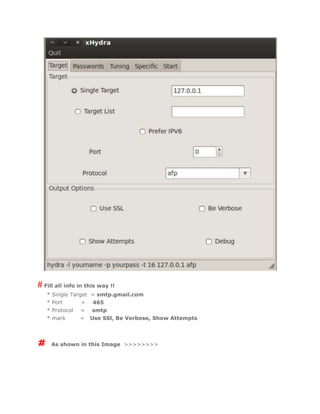
- 4. # Fill all info in this way !! * Single Target = smtp.gmail.com * Port = 465 * Protocol = smtp * mark = Use SSl, Be Verbose, Show Attempts # As shown in this Image >>>>>>>>
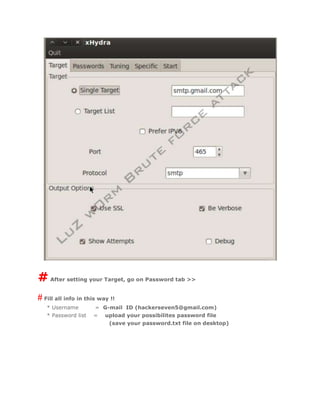
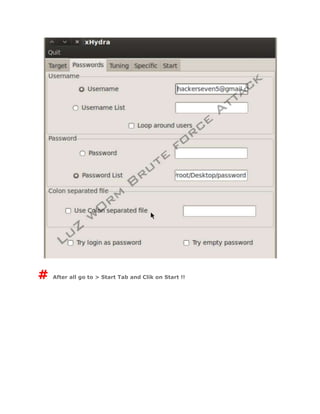
- 5. #After setting your Target, go on Password tab >> # Fill all info in this way !! * Username = G-mail ID (hackerseven5@gmail.com) * Password list = upload your possibilites password file (save your password.txt file on desktop)
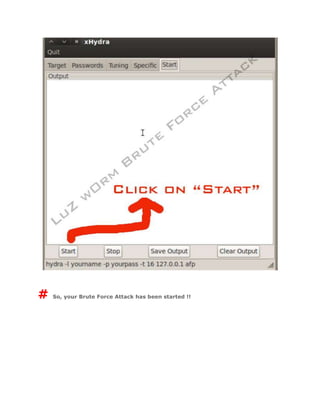
- 6. # After all go to > Start Tab and Clik on Start !!
- 7. # So, your Brute Force Attack has been started !!
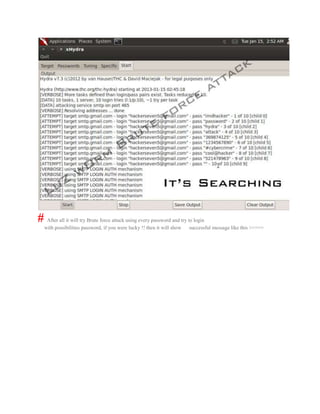
- 8. # After all it will try Brute force attack using every password and try to login with possibilities password, if you were lucky !! then it will show successful message like this >>>>>
- 9. >>>>>>>>>>>>>>>>>Viv EK<<<<<<<<<<<<<<<<<<< I no using this attack it is very hard to hack any G-mail Password, but it can help you to recover your hacked ID or forget password.
