HTML5 Messaging (Post Message)
- 1. HTML5 Messaging (postMessage) By - Parth Jhankharia Date - 14/5/2020
- 2. ~$whoami â—Ź Security Analyst â—Ź Twitter @Aee_Parth
- 3. postMessage-Overview â—Ź Working â—Ź Exploitation â—Ź Remediation â—Ź References
- 4. postMessage Supported Browsers From:- https://caniuse.com/#search=postMessage
- 5. postMessage? ● Controlled mechanism to circumvent SOP. ● Dispatches “Message Event”. ● Type (Always “message”). ● Data (User Supplied). ● Origin (Origin of the window calling). ● Source (window Calling).
- 6. Same Origin Policy â—Ź Port â—Ź Protocol â—Ź Host
- 11. postMessage? ● Syntax window.postMessage(message, targetOrigin [, ports]) ● Example window.postMessage(“msg-here”, “*”)
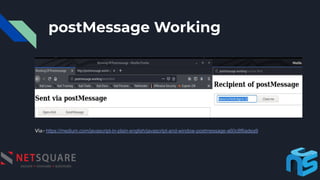
- 13. postMessage Demo
- 14. postMessage Attacks â—Ź XSS â—Ź Information leakage.
- 15. postMessage Xss ● No origin validation on the target. ● Attacker crafts a malicious page having an xss payload ● Sending the payload from attacker’s domain. ● XSS’ed.
- 18. So How Do We Fix It?
- 19. So How Do We Fix It?
- 20. So How Do We Fix It? â—Ź You have to check the origin.
- 21. So How Do We Fix It? â—Ź You HAVE to check the origin.
- 22. So How Do We Fix It? â—Ź You HAVE to check the origin. â—Ź CORRECTLY
- 26. Reference â—Ź /LukasKlein1/attacking-and-defending-html5-p ostmessage-in-mobile-websites â—Ź /mitchbox/ltiframe-communication-in-javascript â—Ź https://github.com/shurmajee/postmessage-vulnerability-demo â—Ź https://medium.com/javascript-in-plain-english/javascript-and-window-po stmessage-a60c8f6adea9 â—Ź https://www.cs.utexas.edu/~shmat/shmat_ndss13postman.pdf
- 27. Resources â—Ź /danwrong/building-anywhere-for-txjs â—Ź /tomasperezv/sandboxed-platform â—Ź https://public-firing-range.appspot.com/dom/index.html â—Ź /peterlubbers/html5-realtime-and-connectivity â—Ź https://www.youtube.com/watch?v=FTeE3OrTNoA&t=862s
- 28. More Resources
- 30. Thank You!











![postMessage?
â—Ź Syntax
window.postMessage(message, targetOrigin [, ports])
â—Ź Example
window.postMessage(“msg-here”, “*”)](https://image.slidesharecdn.com/html5messagingpostmessage-200514095855/85/HTML5-Messaging-Post-Message-11-320.jpg)