IA 124 Lecture 01 2022 -23-1.pdf hahahah
- 1. IA 124: INTRODUCTION TO IT SECURITY LECTURE 01 SECURITY CONCEPTS 1 3/24/2023
- 2. INTRODUCTION ŌØ¢What is a Security? 2 What do you think?
- 3. WHAT IS SECURITY? ŌØ¢Security: A state of well-being of information and infrastructure in which the possibility of theft, tempering, and disruption of information and services is kept low or tolerable. ŌØ¢ ŌĆ£SecurityŌĆØ is the quality or state of being secure--to be free from danger. 3 3/24/2023
- 4. Specialized Areas of Security 3/24/2023 4 ŌØ¢Physical security: Protect the physical items, objects, or areas of an organization from unauthorized access and misuse. ŌØ¢Personal security: Protect the individual or group of individuals who are authorized to access the organization and its operations. ŌØ¢Communications security: Protect an organizationŌĆÖs communications media, technology, and content.
- 5. Specialized Areas of Security 3/24/2023 5 ŌØ¢Network Security: Protect the network and the network-accessible resources from unauthorized access, consistent and continuous monitoring and measurement of its effectiveness. ŌØ¢Data security: Data security is the means of ensuring that data is kept safe from corruption and that access to it is suitably controlled.
- 6. Computer Security 3/24/2023 6 ŌØ¢ŌĆ£ŌĆ”.Protection of computers hardware, software, data, information and other related computer devices, from theft, corruption, or natural disaster destructionŌĆ”.ŌĆØ. ŌØ¢Computer security is concern with protecting a computer systemŌĆÖs information assets, as well as the computer systems themselves. Ō£ōAsset = item of value Ō£ōAssets include: Hardware, Software, Data
- 7. The Vulnerability ŌĆō Threat ŌĆō Control Paradigm ŌØ¢ A major goal of information security as a discipline and as a profession is to protect valuable assets ŌØ¢ To study methods of asset protection, we use vulnerability ŌĆō threat ŌĆō control framework: ŌØ¢ Vulnerability Ō£ō Is a weakness in an information system or its components that might be exploited to compromise the security of the system. Ō£ō Attack is the deliberate act that exploits vulnerability. Is the actual attempt to violate security. ŌØ¢ Threat Ō£ō A set of circumstances or events that has the potential to course loss or harm an information system by destroying it, disclosing the information stored on the system, adversely modifying data, or making the system unavailable. ŌØ¢ Control Ō£ō An action, device, procedure, or technique that eliminates or reduces a vulnerability Ō£ō Also called a countermeasure 3/24/2023 7
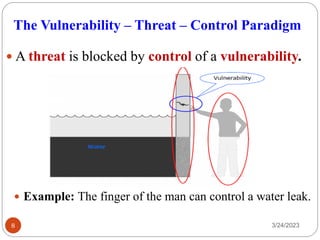
- 8. The Vulnerability ŌĆō Threat ŌĆō Control Paradigm ’éŚ A threat is blocked by control of a vulnerability. 3/24/2023 8 ’éŚ Example: The finger of the man can control a water leak.
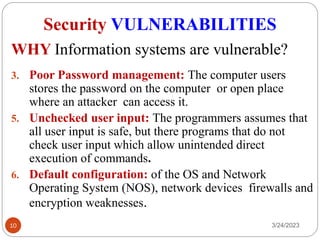
- 9. Security VULNERABILITIES 3/24/2023 9 1. Poor system management: If managers at all levels don't make security, their number one priority, then the threats to an information system is easily to become real. 2. Familiarity: Using common, well-known code, software, operating systems, and/or hardware increases the probability an attacker to have the tools or knowledge to exploit the weakness. 3. Poor System Design: If the System Analyst did not consider the security aspect, during system design process then creates a loop hole for an attacker to damage a system. WHY Information systems are vulnerable?
- 10. Security VULNERABILITIES 3/24/2023 10 3. Poor Password management: The computer users stores the password on the computer or open place where an attacker can access it. 5. Unchecked user input: The programmers assumes that all user input is safe, but there programs that do not check user input which allow unintended direct execution of commands. 6. Default configuration: of the OS and Network Operating System (NOS), network devices firewalls and encryption weaknesses. WHY Information systems are vulnerable?
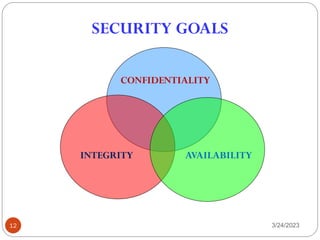
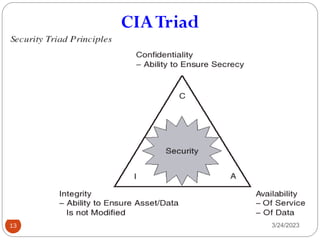
- 11. Threats and C-I-A ŌØ¢Threats can apply to the confidentiality, integrity, or availability (C-I-A) of a system ŌØ¢Confidentiality: Assurance that the information is accessible only to those authorized to have access. ŌØ¢Integrity: The trustworthiness of data of resources in terms of preventing improper and unauthorized changes. ŌØ¢Availability: Assurance that the systems are accessible when required by the authorized users. 3/24/2023 11 ’éŚ C-I-A = The security Triad ’éŚ C-I-A = The Goals/Objectives of Information Security
- 14. Additional Pillars of Information Security ŌØ¢Aside from C-I-A, authentication, nonreputiation, and auditability are also desirable system properties ŌØ¢Authentication: The ability of a system to confirm the identity of a sender. ŌØ¢Nonrepudiation: The ability of a system to confirm that a sender cannot convincingly deny having sent a message. ŌØ¢Auditability: The ability of a system to trace all actions related to a given asset. Ō£ōDetermine who did what and when in order to ensure that responsible parties are held account. 3/24/2023 14
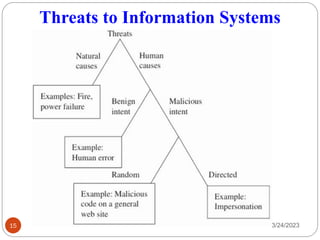
- 15. Threats to Information Systems 3/24/2023 15
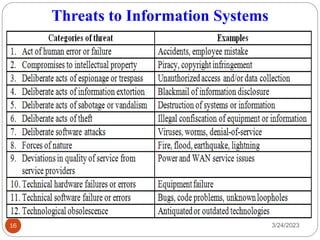
- 16. Threats to Information Systems 3/24/2023 16
- 17. Threats to Information Systems 3/24/2023 17 ŌØ¢Includes acts done without malicious intent ŌØ¢Caused by: Ō£ōInexperience Ō£ōImproper training Ō£ōIncorrect assumptions Ō£ōOther circumstances ŌØ¢Employees are greatest threats to information security Ō£ōThey are closest to the organizational data Example: Acts of Human Error or Failure
- 18. Threats to Information Systems 3/24/2023 18 ŌØ¢Employee mistakes can easily lead to the following: Ō£ōRevelation of classified data Ō£ōEntry of erroneous data Ō£ōAccidental deletion or modification of data Ō£ōStorage of data in unprotected areas Ō£ōFailure to protect information Example: Acts of Human Error or Failure ŌØ¢Many of these threats can be prevented with controls Ō£ōControl: Is an action, procedure or technique that removes or reduces the vulnerabilities.
- 19. 3/24/2023 19
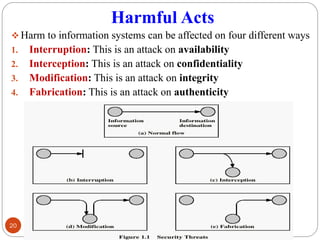
- 20. Harmful Acts ŌØ¢ Harm to information systems can be affected on four different ways 1. Interruption: This is an attack on availability 2. Interception: This is an attack on confidentiality 3. Modification: This is an attack on integrity 4. Fabrication: This is an attack on authenticity 20
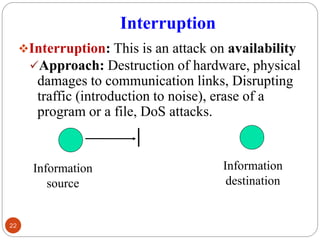
- 22. Interruption ŌØ¢Interruption: This is an attack on availability Ō£ōApproach: Destruction of hardware, physical damages to communication links, Disrupting traffic (introduction to noise), erase of a program or a file, DoS attacks. 22 Information source Information destination
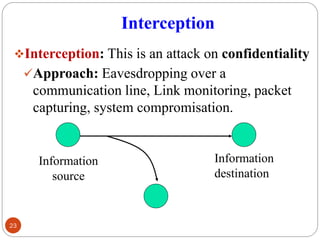
- 23. Interception ŌØ¢Interception: This is an attack on confidentiality Ō£ōApproach: Eavesdropping over a communication line, Link monitoring, packet capturing, system compromisation. 23 Information source Information destination
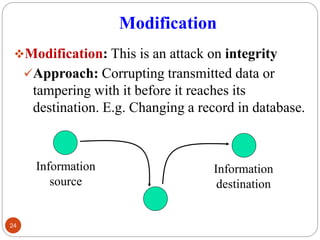
- 24. Modification ŌØ¢Modification: This is an attack on integrity Ō£ōApproach: Corrupting transmitted data or tampering with it before it reaches its destination. E.g. Changing a record in database. 24 Information source Information destination
- 25. Fabrication ŌØ¢Fabrication: This is an attack on authenticity Ō£ōApproach: Faking data as if it were created by a legitimate and authentic party. E.g. Adding a new record to a database, insertion of new network packet. 25 Information source Information destination
- 26. Types of attackers ŌØ¢Amateurs Ō£ōOpportunistic attackers Ō¢¬ Use a password that he or she found Ō¢¬ Script kiddies ŌØ¢Hackers: Non-malicious ŌØ¢Crackers: Malicious Ō£ōCareer criminals Ō£ōOrganized crime syndicates Ō£ōCyber terrorists Ō£ōState-supported spies and information warriors 3/24/2023 26
- 27. Method ŌĆō Opportunity - Motive ’éŚ Attackers need MOM ŌØ¢Method Ō£ōSkills, knowledge, tools, etc. with which to attempt an attack ŌØ¢Opportunity Ō£ōTime and access to attempt an attack ŌØ¢Motive Ō£ōA reason to attempt an attack 3/24/2023 27
- 28. Method of Defense ’éŚ Six approaches to defense of computing systems 1. Prevent attack ’éŚ Block attack / close vulnerability 2. Deter attack ’éŚ Make attack harder (if we canŌĆÖt make it impossible) 3. Deflect attack ’éŚ Make another target more attractive than this target 4. Mitigate attack ’éŚ Make the impact of an attack less severe 5. Detect attack ’éŚ during or after 6. Recover from attack 3/24/2023 28
- 29. Importance of Computer Security 3/24/2023 29 1. To protect organization's valuable resources, such as information, hardware, and software, through the selection of appropriate techniques. 2. Security helps the organization's mission of protecting its. ŌØ¢ Physical and financial resources. ŌØ¢ Gaining reputation and legal position from employees, and customers trust.
- 30. Importance of Computer Security 3/24/2023 30 3. Preserving, Integrity, Confidentiality and Availability of information system resources that includes. ŌØ¢ OrganizationŌĆÖs data. ŌØ¢ CustomerŌĆÖs information. ŌØ¢ OrganizationŌĆÖs hardware and software etc. 4. To protect the organizationsŌĆÖ information from criminal, natural hazards and other threats.
- 31. Importance of Computer Security 3/24/2023 31 5. To protect the organization from hackers, crackers and terrorists. ŌØ¢ Hacker: Intelligent individual with excellent computer skills, with the ability to create and explore or exploits weaknesses in computer systems and network. ŌØ¢ Cracker: System intruder/destroyer who Breaching security on software or systems. ŌØ¢ Virus: Is a program that reproduces its own code by attaching itself to other executable files in such a way that the virus code is executed when the infected executable file is executed. Ō£ō Is a program designed and to cause problems to computers or computer network systems.
- 32. SECURITY MEASURES 3/24/2023 32 ŌØ¢The following measures can be used to protect your computer from security threats and attacks: 1. Locking your computer with a password. 2. Installing Anti-Virus software and ensure it is up- to-date. 3. Using up-to-date software (operating systems and user applications) 4. Logging off or shutting down your computer when going away. Protecting Computers
- 33. SECURITY MEASURES 3/24/2023 33 5. Make a backup of your important documents and data. 6. Protect your files with passwords 7. Before clicking on any e-mail attachment, make sure that the attachment is scanned even if you know the source. 8. Before using media given to you by someone else, scan it to remove viruses Protecting ComputersŌĆ”
- 34. SECURITY MEASURES 3/24/2023 34 ŌØ¢The following measures can be used to protect your network from security threats and attacks 1. Firewalls: A firewall defines a single choke point of control and monitoring that keeps unauthorized users out of the protected network. 2. Intrusion Detection System (IDS) Protecting Computers Networks
- 35. SYMPTOMS OF INFECTED COMPUTER 3/24/2023 35 ŌØ¢It is difficult to prove if your computer has been affected with a virus. However, one can suspects that a computer is infected with a virus, by considering some primary indicators that are; 1. The computer runs slower than usual. 2. The computer stops responding, or it locks up frequently. 3. The computer crashes, and then it restarts every few minutes. 4. Your computer has much less memory or hard drive space is unavailable.
- 36. SYMPTOMS OF INFECTED COMPUTERŌĆ” 3/24/2023 36 5. Applications programs on the computers do not work correctly. 6. Disks or flash disk drives are inaccessible. 7. You cannot print soft copy to hardcopy correctly or PC prints bogus information. 8. You see unusual error messages. 9. There is a double extension on an attachment that you recently opened, such as a .jpg, .gif, or .exe. extension. 10. An antivirus program is disabled for no reason and sometimes it cannot be restarted.
- 37. SYMPTOMS OF INFECTED COMPUTERŌĆ” 3/24/2023 37 11. An antivirus program cannot be installed on the computer, or the antivirus program will not run. 12. New icons appear on the desktop that you did not put there, or the icons are not associated with any recently installed programs. 13. There are error messages popping out on a regular basis. 14. Your files and folders are getting deleted automatically. 15. Abnormal sound.
- 38. 38 IA 124 LECTURE 01 END 3/24/2023
























































![GEOGRAPHY-Study Material [ Class 10th] .pdf](https://cdn.slidesharecdn.com/ss_thumbnails/geography-studymaterial-250613053858-319e1b53-thumbnail.jpg?width=560&fit=bounds)

















